Performance and Power Characterization of Cellular Networks and Mobile Application Optimizations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mobiliųjų Telefonų Modeliai, Kuriems Tinka Ši Programinė Įranga
Mobiliųjų telefonų modeliai, kuriems tinka ši programinė įranga Telefonai su BlackBerry operacinė sistema 1. Alltel BlackBerry 7250 2. Alltel BlackBerry 8703e 3. Sprint BlackBerry Curve 8530 4. Sprint BlackBerry Pearl 8130 5. Alltel BlackBerry 7130 6. Alltel BlackBerry 8703e 7. Alltel BlackBerry 8830 8. Alltel BlackBerry Curve 8330 9. Alltel BlackBerry Curve 8530 10. Alltel BlackBerry Pearl 8130 11. Alltel BlackBerry Tour 9630 12. Alltel Pearl Flip 8230 13. AT&T BlackBerry 7130c 14. AT&T BlackBerry 7290 15. AT&T BlackBerry 8520 16. AT&T BlackBerry 8700c 17. AT&T BlackBerry 8800 18. AT&T BlackBerry 8820 19. AT&T BlackBerry Bold 9000 20. AT&T BlackBerry Bold 9700 21. AT&T BlackBerry Curve 22. AT&T BlackBerry Curve 8310 23. AT&T BlackBerry Curve 8320 24. AT&T BlackBerry Curve 8900 25. AT&T BlackBerry Pearl 26. AT&T BlackBerry Pearl 8110 27. AT&T BlackBerry Pearl 8120 28. BlackBerry 5810 29. BlackBerry 5820 30. BlackBerry 6210 31. BlackBerry 6220 32. BlackBerry 6230 33. BlackBerry 6280 34. BlackBerry 6510 35. BlackBerry 6710 36. BlackBerry 6720 37. BlackBerry 6750 38. BlackBerry 7100g 39. BlackBerry 7100i 40. BlackBerry 7100r 41. BlackBerry 7100t 42. BlackBerry 7100v 43. BlackBerry 7100x 1 44. BlackBerry 7105t 45. BlackBerry 7130c 46. BlackBerry 7130e 47. BlackBerry 7130g 48. BlackBerry 7130v 49. BlackBerry 7210 50. BlackBerry 7230 51. BlackBerry 7250 52. BlackBerry 7270 53. BlackBerry 7280 54. BlackBerry 7290 55. BlackBerry 7510 56. BlackBerry 7520 57. BlackBerry 7730 58. BlackBerry 7750 59. BlackBerry 7780 60. BlackBerry 8700c 61. BlackBerry 8700f 62. BlackBerry 8700g 63. BlackBerry 8700r 64. -

Htc Kaiser User Manual Download Htc Kaiser User Manual
Htc Kaiser User Manual Download Htc Kaiser User Manual Even if anyone have any broken HTC Kaiser TyTn II laying around collecting dust im interested in these as well if i cant find the manuals ill buy the broken units for parts etc. Thanks in advance. DaveShaw HTC Kaiser alias MDA Vario III We should expect to see quite soon at T-Mobile the HTC Kaiser smartphone which will appear under the name of MDA Vario III, as the German operator will rename it. Para encontrar más libros sobre kaiser mix 2306dusb manual pdf, puede utilizar las palabras clave relacionadas : Aluminum Extrusion Die Design Kaiser, Introductory Circuit Analysis Laboratory Manual Solution Manual, Manual Practical Manual Of Vampirism Paulo Coelho, Solution Manual-instructer Manual-java Programming-pdf, CISA "manual 2012" "manual 2014", Solution Manual For Coulson And.HTC Kaiser. Jan 2, 2008 by wheaties82. Previously I had owned the 8525 and enjoyed its functionality and versatility, however the phone began giving me the white screen of death and so I was.“HTC Connection Settings” is a free app from HTC which comes pre-loaded on some of HTC’s Windows Phone 7 mobile phones and can be downloaded from the company’s “HTC Hub” app or from the Marketplace. Unfortunately, this app suddenly decided that my phone didn’t need data access anymore – talk about bad news. HTC TyTN II - user opinions and reviews. Released 2007, July 190g, 19mm thickness Microsoft Windows Mobile 6.0 Professional. HTC Kaiser HTC TyTN II HTC P4550 AT&T 8925. Rating 0 | Reply; Is there any mobile that will allow me to connect an Ipod Touch to the Internet via wifi no matter where I am if I purchase web n walk (or an alternative). -

Windows Phone 7: Implications for Digital Forensic Investigators
Windows Phone 7 : Implications For Digital Forensic Investigators YUNG ANH LE B.E. (Manukau Institute Of Technology, NZ) A thesis submitted to the Graduate Faculty of Design and Creative Technologies AUT University in partial fulfilment of the requirements for the degree of Masters of Forensic Information Technology School of Computing and Mathematical Sciences Auckland, New Zealand 2012 ii Declaration I hereby declare that this submission is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which to a substantial extent has been accepted for the qualification of any other degree or diploma of a University or other institution of higher learning, except where due acknowledgement is made in the acknowledgements. ........................... Signature iii Acknowledgements This thesis was conducted at the Faculty of Design and Creative Technologies in the school of Computing and Mathematical Sciences at Auckland University of Technology, New Zealand. Support was received from many people throughout the duration of the thesis. Firstly I would like to thank my mother Van and my father Tai both of whom provided support and encouragement during the course of the thesis project as well as throughout my entire post graduate study. I would like to thank my thesis supervisors Mr. Petteri Kaskenpalo and Dr Brian Cusack for their exceptional support and guidance throughout the thesis project. Mr Kaskenpalo provided me with the freedom to explore research directions and choose the routes that I wanted to investigate. Mr Kaskenpalo's encouragement, excellent guidance, creative suggestions, and critical comments that have greatly contributed to this thesis. -

HTC Tytn II Manual
PDA Phone User Manual www.htc.com Please Read Before Proceeding THE BATTERY IS NOT CHARGED WHEN YOU TAKE IT OUT OF THE BOX. DO NOT REMOVE THE BATTERY PACK WHEN THE DEVICE IS CHARGING. YOUR WARRANTY IS INVALIDATED IF YOU OPEN OR TAMPER WITH THE DEVICE’S OUTER CASING. PRIVACY RESTRICTIONS Some countries require full disclosure of recorded telephone conversations, and stipulate that you must inform the person with whom you are speaking that the conversation is being recorded. Always obey the relevant laws and regulations of your country when using the recording feature of your PDA Phone. INTELLECTUAL PROPERTY RIGHT INFORMATION Copyright © 007 High Tech Computer Corp. All Rights Reserved. , , and ExtUSB are trademarks and/or service marks of High Tech Computer Corp. Microsoft, MS-DOS, Windows, Windows NT, Windows Server, Windows Mobile, Windows XP, Windows Vista, ActiveSync, Windows Mobile Device Center, Internet Explorer, MSN, Hotmail, Windows Live, Outlook, Excel, PowerPoint, Word, and Windows Media are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Bluetooth and the Bluetooth logo are trademarks owned by Bluetooth SIG, Inc. Wi-Fi is a registered trademark of the Wireless Fidelity Alliance, Inc. microSD is a trademark of SD Card Association. Java, JME and all other Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. Copyright © 007, Adobe Systems Incorporated. Copyright © 007, Macromedia Netherlands, B.V. Macromedia, Flash, Macromedia Flash, Macromedia Flash Lite and Reader are trademarks and/or registered trademarks of Macromedia Netherlands, B.V. -

Characterizing Radio Resource Allocation for 3G Networks
Characterizing Radio Resource Allocation for 3G Networks Feng Qian Zhaoguang Wang Alexandre Gerber University of Michigan University of Michigan AT&T Labs Research Z. Morley Mao Subhabrata Sen Oliver Spatscheck University of Michigan AT&T Labs Research AT&T Labs Research ABSTRACT Keywords 3G cellular data networks have recently witnessed explosive UMTS, 3G Networks, RRC state machine, Inactivity timers, growth. In this work, we focus on UMTS, one of the most Tail effects, Smartphones, Multimedia streaming popular 3G mobile communication technologies. Our work is the first to accurately infer, for any UMTS network, the state 1. INTRODUCTION machine (both transitions and timer values) that guides the 3G cellular data networks have recently witnessed rapid radio resource allocation policy through a light-weight prob- growth, especially due to the emergence of smartphones. In ing scheme. We systematically characterize the impact of this paper, we focus on the UMTS (the Universal Mobile operational state machine settings by analyzing traces col- Telecommunications System) 3G network, which is among lected from a commercial UMTS network, and pinpoint the the most popular 3G mobile communication technologies. inefficiencies caused by the interplay between smartphone As evidence of this popularity, in Q3 2008, among the 400 applications and the state machine behavior. Besides ba- million of worldwide 3G users, 300 million were UMTS sub- sic characterizations, we explore the optimal state machine scribers [1]. settings in terms of several critical -

Mobile Broadband Capacity Constraints and the Need for Optimization
Mobile Broadband Capacity Constraints And the Need for Optimization Original Release: February 16, 2010 Updated: February 24, 2010 Copyright ©2010 Rysavy Research, LLC. All rights reserved. http://www.rysavy.com Mobile Broadband Capacity Constraints Table of Contents EXECUTIVE SUMMARY ............................................................................................ 4 INTRODUCTION...................................................................................................... 6 MOBILE BROADBAND DEMAND ............................................................................... 6 BROADBAND GROWTH .................................................................................................. 6 MOBILE BROADBAND GROWTH ........................................................................................ 7 SMARTPHONES ........................................................................................................... 8 APPLICATIONS AND BANDWIDTH REQUIREMENTS ................................................................... 9 EQUATING CAPACITY WITH DEMAND ................................................................... 10 CAPACITY INTRODUCTION ............................................................................................ 10 DEMAND PROJECTION ................................................................................................ 11 OTHER REPORTS ON SPECTRUM DEMAND .......................................................................... 17 SPECTRUM DEPLOYMENT CONSIDERATIONS ....................................................... -

Power Saving Strategies for Two-Way, Real-Time Enabled
Power Saving Strategies for Two-Way, Real-Time Video-Enabled Cellular Phones Jessica Julie Tran A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering University of Washington 2010 Program Authorized to Offer Degree: Department of Electrical Engineering University of Washington Graduate School This is to certify that I have examined this copy of a master’s thesis by Jessica Julie Tran and have found that it is complete and satisfactory in all respects, and that any and all revisions required by the final examining committee have been made. Committee Members: ________________________________________________________________________ Eve A. Riskin ________________________________________________________________________ Richard E. Ladner Date:___________________________________________________________________ In presenting this thesis in partial fulfillment of the requirements for a master’s degree at the University of Washington, I agree that the Library shall make its copies freely available for inspection. I further agree that extensive copying of this thesis is allowable only for scholarly purposes, consistent with “fair use” as prescribed in the U.S. Copyright Law. Any other reproduction for any purposes or by any means shall not be allowed without my written permission. Signature ________________________ Date ____________________________ University of Washington Abstract Power Saving Strategies for Two-Way, Real-Time Video-Enabled Cellular Phones Jessica Julie Tran Co-Chairs of the Supervisory Committee: Professor Eve A. Riskin Electrical Engineering Professor Richard E. Ladner Computer Science and Engineering MobileASL provides low bandwidth and low complexity software video encoders to enable real-time video conversations on cell phones, therefore allowing people who are deaf to communicate in their native language, American Sign Language. -

Title on Localized Application-Driven Topology Control for Energy- Efficient
On localized application-driven topology control for energy- Title efficient wireless peer-to-peer file sharing Author(s) Leung, AKH; Kwok, YK Citation Ieee Transactions On Mobile Computing, 2008, v. 7 n. 1, p. 66-80 Issued Date 2008 URL http://hdl.handle.net/10722/57457 ©2008 IEEE. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for Rights resale or redistribution to servers or lists, or to reuse any copyrighted component of this work in other works must be obtained from the IEEE. 66 IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 7, NO. 1, JANUARY 2008 On Localized Application-Driven Topology Control for Energy-Efficient Wireless Peer-to-Peer File Sharing Andrew Ka-Ho Leung, Student Member, IEEE, and Yu-Kwong Kwok, Senior Member, IEEE Abstract—Wireless Peer-to-Peer (P2P) file sharing is widely envisioned as one of the major applications of ad hoc networks in the near future. This trend is largely motivated by the recent advances in high-speed wireless communication technologies and high traffic demand for P2P file sharing applications. To achieve the ambitious goal of realizing a practical wireless P2P network, we need a scalable topology control protocol to solve the neighbor discovery problem and network organization problem. Indeed, we believe that the topology control mechanism should be application driven in that we should try to achieve an efficient connectivity among mobile devices in order to better serve the file sharing application. We propose a new protocol, which consists of two components, namely, Adjacency Set Construction (ASC) and Community-Based Asynchronous Wakeup (CAW). -
E HTC Tytn II 2007-09-13
For Immediate release CSL Exclusively Launches the HTC TyTN II PDA Phone Creating a High Speed Mobile Communication Experience With CSL’s Superior Mobile Broadband Network Hong Kong, 13 September 2007 – CSL exclusively launches the new HTC TyTN II, HTC’s first PDA Phone supporting a data transmission rate of 3.6Mbps. With CSL’s superior, territory-wide HSDPA Mobile Broadband network, customers can enjoy the advantages of CSL’s comprehensive mobile services anytime, anywhere, at high speed. Enables customers to enjoy diversified mobile services with Mobile Broadband Service With the HTC TyTN II and CSL’s superior Mobile Broadband network, customers can surf the Internet, download email and a huge range of applications with faster and more stable access. CSL’s customers can enjoy a wide range of value-added services including the first-ever “DRM-free Full Song Download”, “Windows Live Messenger”, “3G Mobile TV” and video steaming, etc; and customers can use CSL’s unique “Info Easy Reader” service, to browse news and other information from major media anytime, or to have the latest headlines conveniently pushed to their handhelds at intervals, allowing them to capitalize on every business opportunity and to make the most of their leisure time.” CSL is dedicated to providing high quality mobile services. With the HTC TyTN II, customers can benefit from CSL’s extensive international data roaming service, which offers 3G and HSDPA coverage in 91 and 80 destinations, respectively, enabling customers to stay connected without any geographical constraints. Brings a new experience in mobile communication The exceptionally stylish HTC TyTN II, equipped with the most advanced Windows Mobile 6 Professional functions, which makes the HTC TyTN II work as efficiently as a mini-desktop computer, is perfectly suited to the varied needs of CSL’s professional and business customers. -
Goodlink Beta 2 Release Note
Good Mobile Messaging™ Server 5.0.4/Client 5.0.6 for Microsoft Exchange Release Notes Updated 02/09/09 Overview.......................................................................................................................................... 1 New in Good Messaging Client Version 5.0.6................................................................................. 2 New in Good Messaging Client Version 5.0.5.29............................................................................ 2 New in Good Messaging Client Version 5.0.5................................................................................. 2 New in Good Messaging Server and Client Version 5.0.4 .............................................................. 3 New in Good Messaging Server Version 5.0 .................................................................................. 4 New in Good Messaging Client Version 5.0.................................................................................... 4 End of Software Updates (ESU)...................................................................................................... 4 Issues Resolved in Client Release 5.0.6......................................................................................... 4 Good Messaging 5.0.6 Notes .......................................................................................................... 6 SR4 Known Issues – GMD....................................................................................................... 6 Issues Resolved in Client Release -
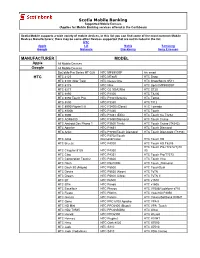
Supported Devices
Scotia Mobile Banking Supported Mobile Devices (Applies for Mobile Banking services offered in the Caribbean) Scotia Mobile supports a wide variety of mobile devices, in this list you can find some of the most common Mobile Devices Manufacturers; there may be some other Devices supported that are not included in the list. HTC Apple LG Nokia Samsung Google Motorola Blackberry Sony Ericsson MANUFACTURER MODEL Apple All Mobile Devices Google All Mobile Devices DoCoMo Pro Series HT-02A HTC MP6950SP htc smart HTC HTC 2125 HTC MTeoR HTC Snap HTC 3100 (Star Trek) HTC Nexus One HTC Snap/Sprint S511 HTC 6175 HTC Nike HTC Sprint MP6900SP HTC 6277 HTC O2 XDA2Mini HTC ST20 HTC 6850 HTC P3300 HTC T8290 HTC 6850 Touch Pro HTC P3301/Artemis HTC Tattoo HTC 8500 HTC P3350 HTC Tilt 2 HTC 8900/Pilgrim/Tilt HTC P3400i (Gene) HTC Tornado HTC 8900b HTC P3450 HTC Touch HTC 9090 HTC P3451 (Elfin) HTC Touch 3G T3232 HTC ADR6300 HTC P3490/Diamond HTC Touch Cruise HTC Android Dev Phone 1 HTC P3600 Trinity HTC Touch Cruise (T4242) HTC Apache HTC P3651 HTC Touch Diamond HTC Artist HTC P3700/Touch Diamond HTC Touch Diamond2 (T5353) HTC P3702/Touch HTC Atlas Diamond/Victor HTC Touch HD HTC Breeze HTC P4000 HTC Touch HD T8285 HTC Touch Pro (T7272/TyTn HTC Cingular 8125 HTC P4350 III) HTC Cleo HTC P4351 HTC Touch Pro/T7373 HTC Corporation Touch2 HTC P4600 HTC Touch Viva HTC Dash HTC P5310BM HTC Touch_Diamond HTC Dash 3G (Maple) HTC P5500 HTC TouchDual HTC Desire HTC P5530 (Neon) HTC TyTN HTC Dream HTC P5800 (Libra) HTC TyTN II HTC Elf HTC P6500 HTC v1510 HTC Elfin HTC -

Panasonic NCS4208 Softphone Manual
Mobile Software Phone Mobile Software Phone for Windows Mobile Devices Panasonic Softphone for Wi-Fi Mobile Device* Panasonic IP Softphone for Windows Mobile devices enables mobile workers to have Mobile Devices Windows Mobile Software for Phone anytime anywhere access to comprehensive and powerful business telephony on their Windows Mobile devices. Panasonic IP Softphone for Windows Mobile is an IP telephone client for WiFi-enabled Windows Mobile based devices. It provides transparent access to real time voice communications and productivity-enhancing Panasonic Business Telephone System features such as call set up, transfer and multiparty conference – all in the convenience of a handheld device. The IP Softphone for Windows Mobile also offers simple point and click dialing from contact directory. The IP Softphone for Windows Mobile delivers Panasonic Business Telephony features to Windows Mobile users via a highly intuitive Graphical User Interface (GUI). The software provides simplified access to common telephony functions such as setting up multi-party conference calls, transferring calls to colleagues, placing callers on hold and dropping added parties from conference calls. The software helps you manage call appearances and provides access to speed dial numbers and other personal calling features. * Note: (PDA or Mobile Phone) Anytime, Anywhere Communications. Mobile workers can connect back to your enterprise IP network wirelessly using virtual private networks (VPNs). The Panasonic IP Softphone for Windows Mobile is perfect for environments where in-building mobile communications are critical, and standard mobile coverage is either not available or not permitted - such as hospitals - and for other market segments with large, wireless enabled facilities - such as manufacturing plants, colleges or university campuses.