Profiling Resource Usage for Mobile Applications: a Cross-Layer Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Performance and Power Characterization of Cellular Networks and Mobile Application Optimizations
Performance and Power Characterization of Cellular Networks and Mobile Application Optimizations by Junxian Huang A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in The University of Michigan 2013 Doctoral Committee: Associate Professor Z. Morley Mao, Chair Associate Professor Jason N. Flinn Associate Professor Robert Dick Technical Staff Subhabrata Sen, AT&T Labs Research c Junxian Huang 2013 All Rights Reserved To my family and my love. ii ACKNOWLEDGEMENTS I became a graduate student in the University of Michigan in the fall of 2008. Five years have passed and I would like to thank many people during this long and unique Ph.D. journey in my life. The completion of this dissertation would not be possible without anyone of them. First of all, I would like to sincerely thank my advisor, Professor Z. Morley Mao. I first met her when I was an intern in Microsoft Research Asia in 2007, wondering about my future, and she offered me much helpful advice for pursuing a Ph.D. degree in the U.S. Morley has provided me excellent and professional guidance on various research projects throughout my Ph.D. study, given her expertise in the computer networking and mobile computing, as well as delicious birthday cakes, when even I forgot my birthday myself. Moreover, she helped me gain the confidence, ability and most importantly, the enthusiasm to tackle difficult real-world problems. Her diligence and enthusiasm has set a great model for me and the experiences working with her would be my life-long treasure. -

Mobiliųjų Telefonų Modeliai, Kuriems Tinka Ši Programinė Įranga
Mobiliųjų telefonų modeliai, kuriems tinka ši programinė įranga Telefonai su BlackBerry operacinė sistema 1. Alltel BlackBerry 7250 2. Alltel BlackBerry 8703e 3. Sprint BlackBerry Curve 8530 4. Sprint BlackBerry Pearl 8130 5. Alltel BlackBerry 7130 6. Alltel BlackBerry 8703e 7. Alltel BlackBerry 8830 8. Alltel BlackBerry Curve 8330 9. Alltel BlackBerry Curve 8530 10. Alltel BlackBerry Pearl 8130 11. Alltel BlackBerry Tour 9630 12. Alltel Pearl Flip 8230 13. AT&T BlackBerry 7130c 14. AT&T BlackBerry 7290 15. AT&T BlackBerry 8520 16. AT&T BlackBerry 8700c 17. AT&T BlackBerry 8800 18. AT&T BlackBerry 8820 19. AT&T BlackBerry Bold 9000 20. AT&T BlackBerry Bold 9700 21. AT&T BlackBerry Curve 22. AT&T BlackBerry Curve 8310 23. AT&T BlackBerry Curve 8320 24. AT&T BlackBerry Curve 8900 25. AT&T BlackBerry Pearl 26. AT&T BlackBerry Pearl 8110 27. AT&T BlackBerry Pearl 8120 28. BlackBerry 5810 29. BlackBerry 5820 30. BlackBerry 6210 31. BlackBerry 6220 32. BlackBerry 6230 33. BlackBerry 6280 34. BlackBerry 6510 35. BlackBerry 6710 36. BlackBerry 6720 37. BlackBerry 6750 38. BlackBerry 7100g 39. BlackBerry 7100i 40. BlackBerry 7100r 41. BlackBerry 7100t 42. BlackBerry 7100v 43. BlackBerry 7100x 1 44. BlackBerry 7105t 45. BlackBerry 7130c 46. BlackBerry 7130e 47. BlackBerry 7130g 48. BlackBerry 7130v 49. BlackBerry 7210 50. BlackBerry 7230 51. BlackBerry 7250 52. BlackBerry 7270 53. BlackBerry 7280 54. BlackBerry 7290 55. BlackBerry 7510 56. BlackBerry 7520 57. BlackBerry 7730 58. BlackBerry 7750 59. BlackBerry 7780 60. BlackBerry 8700c 61. BlackBerry 8700f 62. BlackBerry 8700g 63. BlackBerry 8700r 64. -

Htc Kaiser User Manual Download Htc Kaiser User Manual
Htc Kaiser User Manual Download Htc Kaiser User Manual Even if anyone have any broken HTC Kaiser TyTn II laying around collecting dust im interested in these as well if i cant find the manuals ill buy the broken units for parts etc. Thanks in advance. DaveShaw HTC Kaiser alias MDA Vario III We should expect to see quite soon at T-Mobile the HTC Kaiser smartphone which will appear under the name of MDA Vario III, as the German operator will rename it. Para encontrar más libros sobre kaiser mix 2306dusb manual pdf, puede utilizar las palabras clave relacionadas : Aluminum Extrusion Die Design Kaiser, Introductory Circuit Analysis Laboratory Manual Solution Manual, Manual Practical Manual Of Vampirism Paulo Coelho, Solution Manual-instructer Manual-java Programming-pdf, CISA "manual 2012" "manual 2014", Solution Manual For Coulson And.HTC Kaiser. Jan 2, 2008 by wheaties82. Previously I had owned the 8525 and enjoyed its functionality and versatility, however the phone began giving me the white screen of death and so I was.“HTC Connection Settings” is a free app from HTC which comes pre-loaded on some of HTC’s Windows Phone 7 mobile phones and can be downloaded from the company’s “HTC Hub” app or from the Marketplace. Unfortunately, this app suddenly decided that my phone didn’t need data access anymore – talk about bad news. HTC TyTN II - user opinions and reviews. Released 2007, July 190g, 19mm thickness Microsoft Windows Mobile 6.0 Professional. HTC Kaiser HTC TyTN II HTC P4550 AT&T 8925. Rating 0 | Reply; Is there any mobile that will allow me to connect an Ipod Touch to the Internet via wifi no matter where I am if I purchase web n walk (or an alternative). -
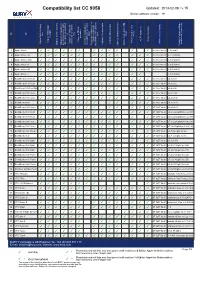
CC9058-Compatibility
Compatibility list CC 9058 Updated: 2013-02-08 / v.15 Device software version: 19 on No key level keys Card Type tags) Phone strength activation A2DP supported Phone s REDIAL Charger available / private mode with Activation Bluetooth Phone book entries: Display: GSM-signal Call lists: Missed calls Article code (Charger) connection with device Display: Battery charge Bluetooth connection to used to test/ Comments after ignition is switched Access to mobile phone Call lists: Received calls voice-dial function (voice Phone book entries: SIM Display: Service provider the last connected phone Call lists: Dialled numbers Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 3.0(7a341) 2 Apple iPhone 3G ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 4.2.1 (8a306) 3 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 4 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 5 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 6 Apple iPhone 5 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 6.1 (10b143) 7 BlackBerry 8100 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.69 8 BlackBerry 8110 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.55 9 BlackBerry 8220 Pearl Flip ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.94 10 BlackBerry 8300 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 os 5.1.342 11 BlackBerry 8310 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.180 12 BlackBerry 8800 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 -

Windows Phone 7: Implications for Digital Forensic Investigators
Windows Phone 7 : Implications For Digital Forensic Investigators YUNG ANH LE B.E. (Manukau Institute Of Technology, NZ) A thesis submitted to the Graduate Faculty of Design and Creative Technologies AUT University in partial fulfilment of the requirements for the degree of Masters of Forensic Information Technology School of Computing and Mathematical Sciences Auckland, New Zealand 2012 ii Declaration I hereby declare that this submission is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which to a substantial extent has been accepted for the qualification of any other degree or diploma of a University or other institution of higher learning, except where due acknowledgement is made in the acknowledgements. ........................... Signature iii Acknowledgements This thesis was conducted at the Faculty of Design and Creative Technologies in the school of Computing and Mathematical Sciences at Auckland University of Technology, New Zealand. Support was received from many people throughout the duration of the thesis. Firstly I would like to thank my mother Van and my father Tai both of whom provided support and encouragement during the course of the thesis project as well as throughout my entire post graduate study. I would like to thank my thesis supervisors Mr. Petteri Kaskenpalo and Dr Brian Cusack for their exceptional support and guidance throughout the thesis project. Mr Kaskenpalo provided me with the freedom to explore research directions and choose the routes that I wanted to investigate. Mr Kaskenpalo's encouragement, excellent guidance, creative suggestions, and critical comments that have greatly contributed to this thesis. -

BURY Compatibility List Generator
Compatibility list CC 9068 Updated: Device software version: Box SW: 106Display SW: 140 on No call key level keys Card SMS Type Phone strength activation conference phone name SMS / Popup between calls A2DP supported Phone s REDIAL reject waiting call Charger available / private mode with Activation Bluetooth Phone book entries: Display: GSM-signal Multiparty call: Swap E-mail read Function Messages: Download Call lists: Missed calls Article code (Charger) connection with device Multiparty call: accept / Display: Battery charge Bluetooth connection to used to test/ Comments after ignition is switched Multiparty call: merge to Required default/factory Call lists: Received calls Multiparty call: hold on 1 Messages: Receive new Phone book entries: SIM Display: Service provider the last connected phone OPP: Synch. phone book Call lists: Dialled numbers Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 3.0 (7a341) 2 Apple iPhone 3G ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 4.2.1 (8c148) 3 Apple iPhone 3GS ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 4 Apple iPhone 4 ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 5 Apple iPhone 4S ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0c.01 6.0 (10a403) 6 BlackBerry 8110 Pearl ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0b.01 v4.5.0.55 7 BlackBerry 8220 Pearl Flip ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ 07-0257-0a.01 v4.6.0.94 8 BlackBerry 8300 Curve ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ -

HTC Tytn Easy Email Setup (For Gmail E-Mail Service)
HTC TyTN Easy Email Setup (For Gmail e-mail service) Rogers makes setting up your wireless e-mail service quick and easy. Before beginning, please ensure you have everything you need to begin enjoying the time-saving benefits and convenience of sending and receiving wireless e-mail on the go. Wireless E-mail Checklist: ; E-mail-capable wireless device ; E-mail Plan ; ISP-based E-mail Address STEP 1 Insert the SIM card and the battery into your wireless device • Charge your device for 20 minutes STEP 2 Turn on your wireless device • Ensure EDGE or GPRS appears on screen (indicates device is connected to the Rogers wireless network) STEP 3 Set up your wireless e-mail service • Follow these steps for Gmail: 1. Log in to your Gmail account from your PC. 2. Select Settings at the top of any Gmail page. 3. Select the Forwarding and POP tab in the orange Mail Settings box. 4. Under POP Download, choose to Enable POP for all mail or Enable POP only for mail that arrives from now on. 5. Specify whether you want Gmail to keep a copy of messages in the Inbox when you access messages through POP. 6. Select Save Changes. Now you can auto-configure Gmail from your pocket pc: 1. On your pocket pc, press Start and scroll to Messaging. 2. Select Menu -> Tools -> New Account 3. Enter your e-mail address (i.e. [email protected]). 4. In the Auto Setup screen, wait until the status changes from Connecting to Completed and select Next. 5. -
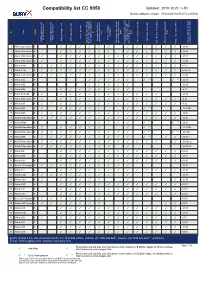
BURY Compatibility List Generator
Compatibility list CC 9050 Updated: 2010-12-21 / v.51 Device software version: APP:04.03.02/ DSW:01.02.0f/ BTS:01.47.12 (CC 9051M V06b) on No key keys Card Type tags) Profile activation service provider Phone s REDIAL A2DP from phone A2DP from device / private mode with Battery charge level Activation Bluetooth GSM-signal strength Call lists Missed calls A2DP supported start A2DP supported start connection with device Call lists Received calls Bluetooth connection to used to test/ Comments after ignition is switched Access to mobile phone Phone book entries SIM voice-dial function (voice the last connected phone Call lists Dialled numbers Phone book entries Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Nokia 2323 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 2 Nokia 2330 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 3 Nokia 2700 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 07.15 4 Nokia 2730 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.40 5 Nokia 3109c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v07.21 6 Nokia 3110c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ vp sk4.80 7 Nokia 3120 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.00 8 Nokia 3230 hf ✓ ✓ ✓ ✓ ✓ ✓ ** ✓ ** v 04.14 9 Nokia 3250 hf ✓ ✓ ✓ ✓ ✓ v 03.24 10 Nokia 3650 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 4.17 11 Nokia 3710 fold hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.80 12 Nokia 3720 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 13 Nokia 5200 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 14 Nokia 5230 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ** v 12.0.089 15 Nokia 5300 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.92 16 Nokia 5310 XpressMusic -

HTC Tytn II Manual
PDA Phone User Manual www.htc.com Please Read Before Proceeding THE BATTERY IS NOT CHARGED WHEN YOU TAKE IT OUT OF THE BOX. DO NOT REMOVE THE BATTERY PACK WHEN THE DEVICE IS CHARGING. YOUR WARRANTY IS INVALIDATED IF YOU OPEN OR TAMPER WITH THE DEVICE’S OUTER CASING. PRIVACY RESTRICTIONS Some countries require full disclosure of recorded telephone conversations, and stipulate that you must inform the person with whom you are speaking that the conversation is being recorded. Always obey the relevant laws and regulations of your country when using the recording feature of your PDA Phone. INTELLECTUAL PROPERTY RIGHT INFORMATION Copyright © 007 High Tech Computer Corp. All Rights Reserved. , , and ExtUSB are trademarks and/or service marks of High Tech Computer Corp. Microsoft, MS-DOS, Windows, Windows NT, Windows Server, Windows Mobile, Windows XP, Windows Vista, ActiveSync, Windows Mobile Device Center, Internet Explorer, MSN, Hotmail, Windows Live, Outlook, Excel, PowerPoint, Word, and Windows Media are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Bluetooth and the Bluetooth logo are trademarks owned by Bluetooth SIG, Inc. Wi-Fi is a registered trademark of the Wireless Fidelity Alliance, Inc. microSD is a trademark of SD Card Association. Java, JME and all other Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. Copyright © 007, Adobe Systems Incorporated. Copyright © 007, Macromedia Netherlands, B.V. Macromedia, Flash, Macromedia Flash, Macromedia Flash Lite and Reader are trademarks and/or registered trademarks of Macromedia Netherlands, B.V. -

Telefón S Vreckovým Počítačom HTC Tytn
Telefón s vreckovým počítačom HTC Tytn Sprievodca: Rýchle zoznámenie htc smart mobility www.htc.com Obsah 1. Súčasti balenia...........................................................................................................................................................2 2. Telefón s vreckovým počítačom.................................................................................................................................3 3. Príprava......................................................................................................................................................................5 4. Uskutočnenie hovoru..................................................................................................................................................7 5. Synchronizácia informácií programu Outlook.............................................................................................................8 6. Nastavenie emailového účtu ......................................................................................................................................9 7. Odoslanie textovej správy ..........................................................................................................................................9 8. Používanie internetu................................................................................................................................................. 10 9. Použitie fotoaparátu ................................................................................................................................................ -

(HFP) Phonebook Transfer Call
file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html KV-PX501 / KV-PX701 / KV-PX707 File Phone Function Manufacturer Model Pairing Dialing / Receiving Phonebook transfer Call log SMS / Text message File transfer (HFP) receipt notification Apple iPhone BlackBerry 7100g BlackBerry 7130g BlackBerry 7290 BlackBerry 8100 BlackBerry 8300 BlackBerry 8700G Dopod 586W ETEN M600 HTC HTC TyTN II HP iPAQ rw6828 LG KG90c LG VX8300 LG VX8500 file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html (1/12) [2008/06/26 11:03:19] file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html LG VX8550 LG VX8600 LG VX8700 LG VX9400 LG VX9900 Motorola A630 Motorola E1 Motorola E1000 Motorola E1070 Motorola E398 Motorola E550 Motorola E680 Motorola E770 Motorola KRZR K1 Motorola KRZR K1m Motorola KRZR K3 Motorola L6 Motorola L7 Motorola MPX220 Motorola PEBL U6 Motorola RAZR V3x file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html (2/12) [2008/06/26 11:03:19] file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html Motorola RAZR V6 Motorola RAZR V8 Motorola RAZR V9 Motorola RIZR Z3 Motorola ROKR Z6 Motorola SLVR L72 Motorola V3 Motorola V360 Motorola V361 Motorola V3c Motorola V3i Motorola V3m Motorola V3x Motorola V500 Motorola V501 Motorola V525 Motorola V547 Motorola V550 Motorola V551 Motorola V600 Motorola V600i file:////Fs03-web/JVC%20(WEB)/car_mobile/jvc_car_mobile/english/car/bluetooth/2008_pn_print.html -

Characterizing Radio Resource Allocation for 3G Networks
Characterizing Radio Resource Allocation for 3G Networks Feng Qian Zhaoguang Wang Alexandre Gerber University of Michigan University of Michigan AT&T Labs Research Z. Morley Mao Subhabrata Sen Oliver Spatscheck University of Michigan AT&T Labs Research AT&T Labs Research ABSTRACT Keywords 3G cellular data networks have recently witnessed explosive UMTS, 3G Networks, RRC state machine, Inactivity timers, growth. In this work, we focus on UMTS, one of the most Tail effects, Smartphones, Multimedia streaming popular 3G mobile communication technologies. Our work is the first to accurately infer, for any UMTS network, the state 1. INTRODUCTION machine (both transitions and timer values) that guides the 3G cellular data networks have recently witnessed rapid radio resource allocation policy through a light-weight prob- growth, especially due to the emergence of smartphones. In ing scheme. We systematically characterize the impact of this paper, we focus on the UMTS (the Universal Mobile operational state machine settings by analyzing traces col- Telecommunications System) 3G network, which is among lected from a commercial UMTS network, and pinpoint the the most popular 3G mobile communication technologies. inefficiencies caused by the interplay between smartphone As evidence of this popularity, in Q3 2008, among the 400 applications and the state machine behavior. Besides ba- million of worldwide 3G users, 300 million were UMTS sub- sic characterizations, we explore the optimal state machine scribers [1]. settings in terms of several critical