Irmx Command Reference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
RED HAT ENTERPRISE LINUX 5, 6, AND 7 SOFTWARE MANAGEMENT NETWORKING Common administrative commands TASK RHEL TASK RHEL yum install iptables and ip6tables 5 6 5 yum groupinstall /etc/sysconfig/ip*tables Install software iptables and ip6tables 1 Be aware of potential issues when using subscription-manager yum install 7 Configure firewall /etc/sysconfig/ip*tables 6 SYSTEM BASICS on Red Hat Enterprise Linux 5: https://access.redhat.com/ yum group install system-config-firewall solutions/129003. TASK RHEL yum info firewall-cmd 2 Subscription-manager is used for Satellite 6, Satellite 5.6 with 5 6 7 SAM and newer, and Red Hat’s CDN. yum groupinfo firewall-config /etc/sysconfig/rhn/systemid 5 3 RHN tools are deprecated on Red Hat Enterprise Linux 7. View software info /etc/hosts yum info 5 6 rhn_register should be used for Satellite server 5.6 and newer 7 /etc/resolv.conf /etc/sysconfig/rhn/systemid yum group info View subscription information 6 only. For details, see: Satellite 5.6 unable to register RHEL 7 Configure name subscription-manager identity client system due to rhn-setup package not included in Minimal resolution /etc/hosts installation (https://access.redhat.com/solutions/737373) Update software yum update 5 6 7 /etc/resolv.conf 7 subscription-manager identity 7 nmcli con mod rhn_register 5 Upgrade software yum upgrade 5 6 7 /etc/sysconfig/network 5 6 subscription-manager 1 Configure hostname hostnamectl rhn_register Configure software subscription-manager repos 5 6 7 /etc/hostname 7 rhnreg_ks 6 /etc/yum.repos.d/*.repo Configure -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Emerging Technologies Multi/Parallel Processing
Emerging Technologies Multi/Parallel Processing Mary C. Kulas New Computing Structures Strategic Relations Group December 1987 For Internal Use Only Copyright @ 1987 by Digital Equipment Corporation. Printed in U.S.A. The information contained herein is confidential and proprietary. It is the property of Digital Equipment Corporation and shall not be reproduced or' copied in whole or in part without written permission. This is an unpublished work protected under the Federal copyright laws. The following are trademarks of Digital Equipment Corporation, Maynard, MA 01754. DECpage LN03 This report was produced by Educational Services with DECpage and the LN03 laser printer. Contents Acknowledgments. 1 Abstract. .. 3 Executive Summary. .. 5 I. Analysis . .. 7 A. The Players . .. 9 1. Number and Status . .. 9 2. Funding. .. 10 3. Strategic Alliances. .. 11 4. Sales. .. 13 a. Revenue/Units Installed . .. 13 h. European Sales. .. 14 B. The Product. .. 15 1. CPUs. .. 15 2. Chip . .. 15 3. Bus. .. 15 4. Vector Processing . .. 16 5. Operating System . .. 16 6. Languages. .. 17 7. Third-Party Applications . .. 18 8. Pricing. .. 18 C. ~BM and Other Major Computer Companies. .. 19 D. Why Success? Why Failure? . .. 21 E. Future Directions. .. 25 II. Company/Product Profiles. .. 27 A. Multi/Parallel Processors . .. 29 1. Alliant . .. 31 2. Astronautics. .. 35 3. Concurrent . .. 37 4. Cydrome. .. 41 5. Eastman Kodak. .. 45 6. Elxsi . .. 47 Contents iii 7. Encore ............... 51 8. Flexible . ... 55 9. Floating Point Systems - M64line ................... 59 10. International Parallel ........................... 61 11. Loral .................................... 63 12. Masscomp ................................. 65 13. Meiko .................................... 67 14. Multiflow. ~ ................................ 69 15. Sequent................................... 71 B. Massively Parallel . 75 1. Ametek.................................... 77 2. Bolt Beranek & Newman Advanced Computers ........... -

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -

Publication Title 1-1962
publication_title print_identifier online_identifier publisher_name date_monograph_published_print 1-1962 - AIEE General Principles Upon Which Temperature 978-1-5044-0149-4 IEEE 1962 Limits Are Based in the rating of Electric Equipment 1-1969 - IEEE General Priniciples for Temperature Limits in the 978-1-5044-0150-0 IEEE 1968 Rating of Electric Equipment 1-1986 - IEEE Standard General Principles for Temperature Limits in the Rating of Electric Equipment and for the 978-0-7381-2985-3 IEEE 1986 Evaluation of Electrical Insulation 1-2000 - IEEE Recommended Practice - General Principles for Temperature Limits in the Rating of Electrical Equipment and 978-0-7381-2717-0 IEEE 2001 for the Evaluation of Electrical Insulation 100-2000 - The Authoritative Dictionary of IEEE Standards 978-0-7381-2601-2 IEEE 2000 Terms, Seventh Edition 1000-1987 - An American National Standard IEEE Standard for 0-7381-4593-9 IEEE 1988 Mechanical Core Specifications for Microcomputers 1000-1987 - IEEE Standard for an 8-Bit Backplane Interface: 978-0-7381-2756-9 IEEE 1988 STEbus 1001-1988 - IEEE Guide for Interfacing Dispersed Storage and 0-7381-4134-8 IEEE 1989 Generation Facilities With Electric Utility Systems 1002-1987 - IEEE Standard Taxonomy for Software Engineering 0-7381-0399-3 IEEE 1987 Standards 1003.0-1995 - Guide to the POSIX(R) Open System 978-0-7381-3138-2 IEEE 1994 Environment (OSE) 1003.1, 2004 Edition - IEEE Standard for Information Technology - Portable Operating System Interface (POSIX(R)) - 978-0-7381-4040-7 IEEE 2004 Base Definitions 1003.1, 2013 -
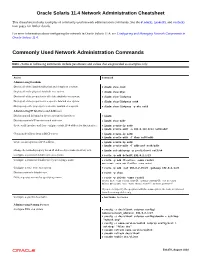
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Command Window – Basic Commands
Command Window – Simple Commands help lists all commands p: switch to your P-drive c: switch to the computer’s C-drive dir list all files in a directory (aka “folder”); e.g. dir (list all files in current directory) dir myfolder (list all files in subdirectory myfolder) cd change directory; e.g. cd myfolder (move to subdirectory myfolder) cd .. (move up one directory level) md make (create) a directory; e.g. md myfolder (make a subdirectory called myfolder) copy copy files; e.g. copy oldfile newfile copy source.f90 myfolder\source.f90 ren rename files; e.g. ren oldfile newfile erase erase (delete) a file; e.g. (or del) erase unwanted.txt fc file compare; e.g. fc file1 file2 type list the contents of a file type somefile.txt type somefile.txt ¦ more (list contents, one page at a time) Wildcards (* and ?) Can be used to match length-unspecified strings (*) or individual letters (?); e.g. copy *.f90 *.bak dir solve.f?? Command Syntax and Options Most commands have various options; e.g. dir /p – list files, one page at a time To find the syntax and options available for any particular command use the /? option; e.g. dir /? History Use the and arrows on keyboard to recover previous commands. Use F7 to get a list of previous commands and arrow up and down to choose one to reissue. Editors An editor called notepad comes with the operating system: notepad myfile.f90 Running Programs You can run any program simply by typing its name; e.g. to run windows explorer: explorer Batch Files To avoid having to type a long sequence of commands it is convenient to put them all in a batch file – identified by the .bat extension. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

N94-13338 1.1.1 3Rd NASA Symposium on VLSI Design 1991
N94-13338 1.1.1 3rd NASA Symposium on VLSI Design 1991 Experience with Custom Processors in Space Flight Applications M. E. Fraeman, J. R. Hayes, D. A. Lohr, B. W. Ballard, R. L. Williams, and R. M. Henshaw Johns Hopkins University Applied Physics Laboratory Laurel, Maryland 20723 Abstract- APL has developed a magnetometer instrument for a Swedish satel- lite named Freja with launch scheduled for August 1992 on a Chinese Long March rocket. The magnetometer controller utilized a custom microprocessor designed at APL with the Genesil silicon compiler. The processor evolved from our experience with an older bit-slice design and two prior single chip efforts. The architecture of our microprocessor greatly lowered software development costs because it was optimized to provide an interactive and extensible pro- gramming environment hosted by the target hardware. Radiation tolerance of the microprocessor was also tested and was adequate for Freja's mission-- 20 kRad(Si) total dose and very infrequent latch-up and single event upset events. 1 Introduction The Johns Hopkins University Applied Physics Laboratory (APL) has developed a micro- processor that is well suited to one-of-a-kind embedded applications especially in satellite instrument control. The chip has been qualified for use in a magnetometer instrument for the Swedish Freja satellite. The processor's language directed architecture reduced Freja software costs because the flight hardware served as its own development system. Thus, unlike traditional interpreted programming languages like Basic, Lisp, or Smalltalk, our Forth language development system was fully supported on the embedded flight proces- sor. Performance was also equivalent or better than that obtained by other microprocessors programmed in languages like C with traditional cross-compilers and development systems. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -

Space Station Freedom Data Management System Growth and Evolution Report
NASA Technical Memorandum 103869 Space Station Freedom Data Management System Growth and Evolution Report R. Bartlett, G. Davis, T. L. Grant, J. Gibson, R. Hedges, M. J. Johnson, Y. K. Liu, A. Patterson-Hine, N. Sliwa, H. Sowizral, and J. Yan N93-15k77 (NASA-TM- I03869) SPACE STATION FREEDOM DATA MANAGEMENT SYSTEM GROWTH ANO EVOLU TIr}N REPORT (NASA) Uncl as September 1992 66 P G3/17 0178407 National Aeronautics and Space Administration Z NASA Technical Memorandum 103869 Space Station Freedom Data Management System Growth and Evolution Report T. L. Grant and J. Yan, Ames Research Center, Moffett Field, California September 1992 RIASA National Aeronauticsand Space Administration Ames Research Center MoffettField, CaJifomia94035-1000 The Study Team The Data Management System (DMS) analysis team Digital Equipment Corporation, Moffett Field, CA consists of civil servants and contractors at NASA Ames Roger Bartlett Research Center, Information Sciences Division. Prof. Joanne Bechta Dugan provided the reliability Intelligent Systems Technology Branch, Ames analysis of the DMS network reported in appendix B; she Research Center, Moffett Field, CA used the HARP code and the work was sponsored by Gloria Davis Langley Research Center (LaRC). Members of the Failure Terry Grant Tolerance/Redundancy Management Working Group Bob Hedges provided network failure information and preliminary Y. K. Liu models that aided our study of the failure tolerance of the Dr. Ann Patterson-Hine DMS network. Nancy Sliwa We also acknowledge the following individuals for Sterling Federal Systems, Inc., Palo Alto, CA reviewing early versions of the manuscripts: Dr. Jerry Yah Gregg Swietek (NASA Headquarters), Mike Pasciuto (NASA), Donald Woods (McDonnell Douglas Space Research Institute for Advanced Computational Systems Company (MDSSC)) and George Ganoe Science, Moffett Field, CA (NASA LaRC).