China, Multinational Corporations, and Internet Privacy Issues: an Incoherent Landscape
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Official Record of Proceedings
LEGISLATIVE COUNCIL ─ 3 November 2010 1399 OFFICIAL RECORD OF PROCEEDINGS Wednesday, 3 November 2010 The Council met at Eleven o'clock MEMBERS PRESENT: THE PRESIDENT THE HONOURABLE JASPER TSANG YOK-SING, G.B.S., J.P. THE HONOURABLE ALBERT HO CHUN-YAN IR DR THE HONOURABLE RAYMOND HO CHUNG-TAI, S.B.S., S.B.ST.J., J.P. THE HONOURABLE LEE CHEUK-YAN DR THE HONOURABLE DAVID LI KWOK-PO, G.B.M., G.B.S., J.P. THE HONOURABLE FRED LI WAH-MING, S.B.S., J.P. DR THE HONOURABLE MARGARET NG THE HONOURABLE JAMES TO KUN-SUN THE HONOURABLE CHEUNG MAN-KWONG THE HONOURABLE CHAN KAM-LAM, S.B.S., J.P. THE HONOURABLE MRS SOPHIE LEUNG LAU YAU-FUN, G.B.S., J.P. THE HONOURABLE LEUNG YIU-CHUNG DR THE HONOURABLE PHILIP WONG YU-HONG, G.B.S. 1400 LEGISLATIVE COUNCIL ─ 3 November 2010 THE HONOURABLE WONG YUNG-KAN, S.B.S., J.P. THE HONOURABLE LAU KONG-WAH, J.P. THE HONOURABLE LAU WONG-FAT, G.B.M., G.B.S., J.P. THE HONOURABLE MIRIAM LAU KIN-YEE, G.B.S., J.P. THE HONOURABLE EMILY LAU WAI-HING, J.P. THE HONOURABLE ANDREW CHENG KAR-FOO THE HONOURABLE TIMOTHY FOK TSUN-TING, G.B.S., J.P. THE HONOURABLE TAM YIU-CHUNG, G.B.S., J.P. THE HONOURABLE ABRAHAM SHEK LAI-HIM, S.B.S., J.P. THE HONOURABLE LI FUNG-YING, S.B.S., J.P. THE HONOURABLE TOMMY CHEUNG YU-YAN, S.B.S., J.P. THE HONOURABLE FREDERICK FUNG KIN-KEE, S.B.S., J.P. -
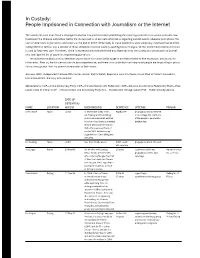
In Custody: People Imprisoned in Connection with Journalism Or the Internet
In Custody: People Imprisoned in Connection with Journalism or the Internet The official directive from China's Propaganda Bureau this past November prohibiting the reporting of incidents of unrest indicates how threatened the Chinese authorities feel by the dissemination of accurate information regarding current events. Likewise indicative is the rash of detentions of journalists and writers at the end of 2004. While many of these detentions were temporary, they have had an intimi- dating effect on writers, and a number of those detained remain in custody awaiting formal charges. On the 2004 index of press freedom issued by Reporters sans Frontieres, China is exceeded only by North Korea and Myanmar in its censorship and persecution of journal- ists, and tops the list of countries imprisoning journalists. The list below employs a broad definition of journalism to include a wide range of activities related to free expression and access to information. Even so, the list cannot claim to be comprehensive, and there is no doubt but that many more people are languishing in prison for no crime greater than the peaceful expression of their views. Sources: HRIC, Independent Chinese PEN Center, Human Rights Watch, Reporters sans Frontìeres, Committee to Protect Journalists, International PEN, Amnesty International Abbreviations: CDP—China Democracy Party; CDF—Chinese Democratic Federation; WAF—Workers Autonomous Federation; FLUC—Free Labor Union of China; CFDP—China Freedom and Democracy Party; RTL—Reeducation Through Labor; PSB—Public Security Bureau DATE OF DETENTION/ NAME LOCATION ARREST BACKGROUND SENTENCE OFFENSE PRISON Chen Renjie Fujian Jul-83 In September 1982 Chen, Aug-83, life propaganda and incitement Lin Youping and Chen Biling to encourage the overthrow published a pamphlet entitled of the people's democratic Freedom Report and distributed dictatorship around 300 copies in Fuzhou. -

Annual Report Sometimes Brutally
“Human rights defenders have played an irreplaceable role in protecting victims and denouncing abuses. Their commitment Steadfast in Protest has exposed them to the hostility of dictatorships and the most repressive governments. […] This action, which is not only legitimate but essential, is too often hindered or repressed - Annual Report sometimes brutally. […] Much remains to be done, as shown in the 2006 Report [of the Observatory], which, unfortunately, continues to present grave violations aimed at criminalising Observatory for the Protection and imposing abusive restrictions on the activities of human 2006 of Human Rights Defenders rights defenders. […] I congratulate the Observatory and its two founding organisations for this remarkable work […]”. Mr. Kofi Annan Former Secretary General of the United Nations (1997 - 2006) The 2006 Annual Report of the Observatory for the Protection Steadfast in Protest of Human Rights Defenders (OMCT-FIDH) documents acts of Foreword by Kofi Annan repression faced by more than 1,300 defenders and obstacles to - FIDH OMCT freedom of association, in nearly 90 countries around the world. This new edition, which coincides with the tenth anniversary of the Observatory, pays tribute to these women and men who, every day, and often risking their lives, fi ght for law to triumph over arbitrariness. The Observatory is a programme of alert, protection and mobilisation, established by the International Federation for Human Rights (FIDH) and the World Organisation Against Torture (OMCT) in 1997. It aims to establish -

Number of Jailed Journalists Sets Global Record a Special Report by the Committee to Protect Journalists
Number of jailed journalists sets global record A special report by the Committee to Protect Journalists Committee to Protect Journalists Number of jailed journalists sets global record Worldwide tally reaches highest point since CPJ began surveys in 1990. Governments use charges of terrorism, other anti-state offenses to silence critical voices. Turkey is the world’s worst jailer. A CPJ special report At least 49 journalists remain jailed in Turkey. (AFP) Published December 11, 2012 Imprisonment of journalists worldwide reached a record high in 2012, driven in part by the widespread use of charges of terrorism and other anti-state offenses against critical reporters and editors, the Committee to Protect Journalists has found. In its annual census of imprisoned journalists, CPJ identified 232 individuals behind bars on December 1, an increase of 53 over its 2011 tally. Large-scale imprisonments in Turkey, Iran, and China helped lift the global tally to its highest point since CPJ began conducting worldwide surveys in 1990, surpassing the previous record of 185 in 1996. The three nations, the world’s worst jailers of the press, each made extensive use of vague anti-state laws to silence dissenting political views, including those expressed by ethnic minorities. Worldwide, anti-state charges such as terrorism, treason, and subversion were the most common allegations brought against journalists in 2012. At least 132 journalists were being held around the world on such charges, CPJ ’s census found. Eritrea and Syria also ranked among the world’s worst, each jailing numerous journalists without charge or due process and holding them in secret prisons without access to lawyers or family members. -

Hong Kong Media Law a Guide for Journalists and Media Professionals
Hong Kong Media Law A Guide for Journalists and Media Professionals Expanded Second Edition Doreen Weisenhaus with contributions by Rick Glofcheski and Yan Mei Ning Hong Kong University Press The University of Hong Kong Pokfulam Road Hong Kong www.hkupress.org © Hong Kong University Press 2007 Expanded Second Edition, 2014 ISBN 978-988-8208-25-8 (Hardback) ISBN 978-988-8208-09-8 (Paperback) All rights reserved. No portion of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any information storage or retrieval system, without prior permission in writing from the publisher. British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. 10 9 8 7 6 5 4 3 2 1 Printed and bound by Paramount Printing Co., Ltd. in Hong Kong, China Reviews for the fi rst edition of Hong Kong Media Law: A Guide for Journalists and Media Professionals “This book deserves to be the fi rst port of call for anyone seeking guidance on free speech and media law in Hong Kong . That the book fulfi lls a felt need is beyond doubt.” —The Commonwealth Lawyer, London “The book is truly the fi rst of its kind in the recent past (and) a singularly important addition to the increasing body of country-specifi c media law books in Asia . Hong Kong Media Law covers all the key topics in the area of communication law . The scholarly merit of the book is substantial.” —Kyu Ho Youm, Communications Lawyer, American Bar Association “An accessible guide to media law in Hong Kong and China . -

INTERNATIONAL PEN Writers in Prison Committee
INTERNATIONAL PEN Writers in Prison Committee Case List – July to December 2008 INTERNATIONAL PEN Writers in Prison Committee HALF-YEARLY CASELIST To 31 December 2008 International PEN Writers in Prison Committee 50/51 High Holborn London WC1V 6ER United Kingdom Tel: + 44 020 74050338 Fax: + 44 020 74050339 e-mail: [email protected] web site: www.internationalpen.org.uk INTERNATIONAL PEN Writers in Prison Committee International PEN is the leading voice of literature worldwide, bringing together poets, novelists, essayists, historians, critics, translators, editors, journalists and screenwriters. Its members are united in a common concern for the craft and art of writing and a commitment to freedom of expression through the written word. Through its Centres, PEN operates on all five continents with 144 centres in 102 countries. Founded in London in 1921, PEN connects an international community of writers. It is a forum where writers meet freely to discuss their work. It is also a voice speaking out for writers silenced in their own countries. The Writers in Prison Committee of International PEN was set up in 1960 as a result of mounting concern about attempts to silence crit- ical voices around the world through the detention of writers. It works on behalf of all those who are detained or otherwise persecuted for their opinions expressed in writing and for writers who are under attack for their peaceful political activities or for the practice of their profession, provided that they did not use violence or advocate violence or racial hatred. Member centres of International PEN are active in campaigning for an improvement in the conditions of persecuted writers and journalists. -

Shi Tao, Yahoo!, and the Lessons for Corporate Social Responsibility
Shi Tao, Yahoo!, and the lessons for corporate social responsibility A working paper (Version 1.0 – December 30, 2007) by Rebecca MacKinnon Assistant Professor, Journalism & Media Studies Centre, University of Hong Kong e-mail: [email protected] weblog: http://rconversation.blogs.com Corrections and comments welcome. Future revisions will be posted at: http://rconversation.blogs.com/about.html This work is licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc/3.0/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. (In other words: you are welcome to distribute this document to your students, friends, colleagues, whoever, as long as you attribute me as the author and don’t publish it for profit.) ABSTRACT: In 2005, Chinese journalist Shi Tao was convicted and sentenced to ten years in prison for leaking state secrets abroad. Key evidence cited in Chinese court documents included information about Shi’s account supplied by Yahoo! to the Chinese State Security Bureau. Condemnation by human rights groups and investors, U.S. congressional hearings, a Hong Kong government investigation, and a U.S. lawsuit followed. This paper documents the core facts, events, issues and debates involved. The Shi Tao case highlights the complex challenges of corporate social responsibility for Internet and telecommunications companies: They are caught between demands of governments on one hand and rights of users on the other – not only in authoritarian countries such as China but in virtually all countries around the world. -

Yahoo! Incident”
CRF-2008-01-02.qxd:HRIC-Report 3/11/08 10:14 AM Page 38 A HISTORY OF THE “YAHOO! INCIDENT” By Hu Kunming The Yahoo! incident is a warning to American companies nation from all sides, as well as tremendous pressure doing business in China: they can no longer just point to from the media. However, the company has consistently commercial interests as an excuse for their actions, even if maintained that doing business in China means abiding their actions are ordered by Chinese authorities. by Chinese laws, and therefore, that it had no choice but to provide information from its database to China ’s American Internet giant Yahoo ! Inc. officially national security departments and police. Right up to announced on November 13 , 2007, that it had settled February 2006, Michael Callahan, general counsel for out of court with the family members of Chinese Inter - Yahoo! Inc., maintained in testimony before the United net dissidents Shi Tao and Wang Xiaoning. The media States Congress that when Yahoo! provided the Chinese and various experts have pointed out that in choosing authorities with Shi Tao’s personal data , the intention to settle, Yahoo !’ s position has undergone dramatic of the Chinese side in obtaining this data was not clear change. Since Shi Tao’s arrest in 2004, Yahoo !, despite to the company . He claimed that Yahoo! provided the pressure from the international and mainland Chinese information because its operations in China must com - public as well as from international human rights ply with Chinese law. organizations, has continuously stressed that it had no alternative but to comply with legal requirements set by In April 2007, the families of Shi Tao and Wang Xiaon - the Chinese authorities. -

Ngày Tự Do Báo Chí Quốc Tế International Press Freedom Day Ngày 3 Tháng 5 Nam Phong Tổng Hợp
Ngày Tự Do Báo Chí Quốc Tế International Press Freedom Day Ngày 3 tháng 5 Nam Phong tổng hợp Mục Lục Ngày Tự Do Báo Chí Thế Giới – Wikipedia 2 Giải Tự Do Báo Chí Quốc Tế - Wikipedia 4 3 Nhà Báo Việt Nam Được Tổ Chức Ký Gỉa Không Biên Giới Vinh Danh “Anh Hùng Thông Tin” - Hoài Hương –VOA 9 Anh Hùng Thông Tin Năm 2014 – Nam Phong 13 1 Ngày Tự Do Báo Chí Thế Giới Bách khoa toàn thư mở Wikipedia Ngày Tự do Báo chí thế giới Ngày 3 tháng 5 Ngày Tự do Báo chí thế giới là ngày Liên Hiệp Quốc dành riêng để cổ vũ và nâng cao nhận thức về tầm quan trọng của Tự do báo chí trên toàn thế giới. Mục lục 1 Lịch sử 2 Ngày Tự do Báo chí thế giới và các chủ đề 3 Tham khảo 4 Liên kết ngoài Lịch sử Theo đề nghị của Tổ chức Giáo dục, Khoa học và Văn hóa Liên Hiệp Quốc, ngày 20.12.1993 Đại Hội đồng Liên Hiệp Quốc đã công bố ngày 3 tháng 5 là "Ngày Tự do Báo chí thế giới" (Nghị quyết số 48/432)[1][2] để nâng cao nhận thức về tầm quan trọng của tự do báo chí và nhắc nhở các chính phủ về bổn phận phải tôn trọng và duy trì quyền tự do ngôn luận theo Điều 19 của Tuyên ngôn Quốc tế Nhân quyền và đánh dấu ngày kỷ niệm Tuyên ngôn Windhoek, một tuyên ngôn về những nguyên tắc tự do báo chí do các nhà báo châu Phi đưa ra năm 1991. -

Gong Zizhen, Ren Bonian, and Kang Youwei
Modern Transformations of Visuality in Late Qing China: Gong Zizhen, Ren Bonian, and Kang Youwei Jian Gong A thesis in fulfilment of requirements for the degree of Doctor of Philosophy School of Humanities & Languages Faculty of Arts and Social Sciences February 2016 COPYRIGHT STATEMENT ‘I hereby grant the University of New South Wales or its agents the right to archive and to make available my thesis or dissertation in whole or part in the University libraries in all forms of media, now or here after known, subject to the provisions of the Copyright Act 1968. I retain all proprietary rights, such as patent rights. I also retain the right to use in future works (such as articles or books) all or part of this thesis or dissertation. I also authorise University Microfilms to use the 350 word abstract of my thesis in Dissertation Abstract International (this is applicable to doctoral theses only). I have either used no substantial portions of copyright material in my thesis or I have obtained permission to use copyright material; where permission has not been granted I have applied/will apply for a partial restriction of the digital copy of my thesis or dissertation.' Signed ……………………………………………........................... Date ……………………………………………........................... AUTHENTICITY STATEMENT ‘I certify that the Library deposit digital copy is a direct equivalent of the final officially approved version of my thesis. No emendation of content has occurred and if there are any minor variations in formatting, they are the result of the conversion to digital format.’ Signed ……………………………………………........................... Date ……………………………………………........................... ORIGINALITY STATEMENT ‘I hereby declare that this submission is my own work and to the best of my knowledge it contains no materials previously published or written by another person, or substantial proportions of material which have been accepted for the award of any other degree or diploma at UNSW or any other educational institution, except where due acknowledgement is made in the thesis. -

ATTACKS O N T H E Press in 2009
A Worldwide Survey by the Committee to Protect Journalists ATTACKS o n t h e press in 2009 Preface by fareed zakaria Founded in 1981, the Committee to Protect Journalists responds to attacks THE COMMITTEE TO PROTECT JOURNALISTS on the press worldwide. CPJ documents hundreds of cases every year and takes action on behalf of journalists and news organizations without board of directors regard to political ideology. To maintain its independence, CPJ accepts no government funding. CPJ is funded entirely by private contributions from Chairman Honorary Co-Chairmen executive director individuals, foundations, and corporations. Paul E. Steiger Walter Cronkite (1916-2009) Joel Simon Terry Anderson The Associated Press, Thomson Reuters, and Agence France-Presse provided news and photo services for Attacks on the Press in 2009. directors Andrew Alexander Michael Massing Associated Press Franz Allina Geraldine Fabrikant Metz Christiane Amanpour Victor Navasky Editorial Director: Bill Sweeney Dean Baquet Andres Oppenheimer Deputy Editor: Lauren Wolfe Kathleen Carroll Burl Osborne Designer: Justin Goldberg Rajiv Chandrasekaran Clarence Page Chief Copy Editor: Lew Serviss Sheila Coronel Norman Pearlstine Copy Editor and Proofreader: Shazdeh Omari Josh Friedman Ahmed Rashid Anne Garrels Dan Rather Photo credits James C. Goodale Gene Roberts Cover: Reuters/Oswaldo Rivas—Honduran police surround AP photographer Cheryl Gould María Teresa Ronderos Dario Lopez-Mills as he covers protests that followed the June presidential coup. Charlayne Hunter-Gault Sandra Mims Rowe Back cover: AP/Bullit Marquez—Protesters in Manila call for justice in the mass killings of journalists and others in Maguindanao province, Philippines. Gwen Ifill Diane Sawyer Jane Kramer David Schlesinger David Laventhol Paul C. -

Attacks on the Press in 2011 a Worldwide Survey by the Committee to Protect Journalists
Attacks on the Press in 2011 A Worldwide Survey by the Committee to Protect Journalists Preface by Sandra Mims Rowe Committee to Protect Journalists Attacks on the Press in 2011 A Worldwide Survey by the Committee to Protect Journalists Committee to Protect Journalists (212) 465-1004 330 Seventh Avenue, 11th Fl. www.cpj.org New York, NY 10001 [email protected] Twitter: @pressfreedom Facebook: @committeetoprotectjournalists Founded in 1981, the Committee to Protect Journalists responds to attacks on the press worldwide. CPJ documents hundreds of cases every year and takes action on behalf of journalists and news organizations without regard to political ideology. To maintain its independence, CPJ accepts no government funding. CPJ is funded entirely by private contributions from individuals, foundations, and corporations. !omson Reuters, Agence France-Presse, and !e Associated Press provided news and photo services for Attacks on the Press in 2011. Editorial Director: Bill Sweeney Senior Editor: Elana Beiser Deputy Editors: Kamal Singh Masuta, Shazdeh Omari Designer: John Emerson Chief Copy Editor: Lew Serviss Copy Editor: Lisa Flam Proofreader: Naomi Serviss : Journalists run for cover during a bombing raid in Ras Lanuf, Libya. (Reuters/Paul Conroy) © 2012 Committee to Protect Journalists, New York All rights reserved Printed by United Book Press in the United States of America Attacks on the Press in 2011: A Worldwide Survey by the Committee to Protect Journalists : 978-0-944823-31-6 Board of Directors Sandra Mims Rowe Terry Anderson Joel Simon Andrew Alexander Rebecca MacKinnon Franz Allina Kati Marton Christiane Amanpour Michael Massing Dean Baquet Geraldine Fabrikant Metz John S. Carroll Victor Navasky Kathleen Carroll Andres Oppenheimer Rajiv Chandrasekaran Burl Osborne Sheila Coronel Clarence Page Josh Friedman Norman Pearlstine Anne Garrels Ahmed Rashid James C.