P-CLS: a Popularity-Driven Caching Location and Searching Scheme in Content Centric Networking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Customizing and Extending Powerdesigner SAP Powerdesigner Documentation Collection Content
User Guide PUBLIC SAP PowerDesigner Document Version: 16.6.2 – 2017-01-05 Customizing and Extending PowerDesigner SAP PowerDesigner Documentation Collection Content 1 PowerDesigner Resource Files.................................................... 9 1.1 Opening Resource Files in the Editor.................................................10 1.2 Navigating and Searching in Resource Files............................................ 11 1.3 Editing Resource Files........................................................... 13 1.4 Saving Changes................................................................13 1.5 Sharing and Embedding Resource Files...............................................13 1.6 Creating and Copying Resource Files.................................................14 1.7 Specifying Directories to Search for Resource Files.......................................15 1.8 Comparing Resource Files........................................................ 15 1.9 Merging Resource Files.......................................................... 16 2 Extension Files................................................................18 2.1 Creating an Extension File.........................................................19 2.2 Attaching Extensions to a Model....................................................20 2.3 Exporting an Embedded Extension File for Sharing.......................................21 2.4 Extension File Properties......................................................... 21 2.5 Example: Adding a New Attribute from a Property -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Objects and Classes in Python Documentation Release 0.1
Objects and classes in Python Documentation Release 0.1 Jonathan Fine Sep 27, 2017 Contents 1 Decorators 2 1.1 The decorator syntax.........................................2 1.2 Bound methods............................................3 1.3 staticmethod() .........................................3 1.4 classmethod() ..........................................3 1.5 The call() decorator.......................................4 1.6 Nesting decorators..........................................4 1.7 Class decorators before Python 2.6.................................5 2 Constructing classes 6 2.1 The empty class...........................................6 3 dict_from_class() 8 3.1 The __dict__ of the empty class...................................8 3.2 Is the doc-string part of the body?..................................9 3.3 Definition of dict_from_class() ...............................9 4 property_from_class() 10 4.1 About properties........................................... 10 4.2 Definition of property_from_class() ............................ 11 4.3 Using property_from_class() ................................ 11 4.4 Unwanted keys............................................ 11 5 Deconstructing classes 13 6 type(name, bases, dict) 14 6.1 Constructing the empty class..................................... 14 6.2 Constructing any class........................................ 15 6.3 Specifying __doc__, __name__ and __module__.......................... 15 7 Subclassing int 16 7.1 Mutable and immutable types.................................... 16 7.2 -

PDF Command Line Suite Version 4.12
PDF Command Line Suite Version 4.12 User Manual Contact: [email protected] Owner: PDF Tools AG Kasernenstrasse 1 8184 Bachenbülach Switzerland http://www.pdf-tools.com Copyright 2000-2018 PDF Command Line Suite, Version 4.12 Page 2 of 65 November 27, 2018 Table of Contents Table of Contents ............................................................................................ 2 1 Overview ............................................................................................... 6 1.1 The Different Tools.................................................................................. 6 1.2 Installation............................................................................................. 7 1.3 Using the Tools ....................................................................................... 7 2 License Management ............................................................................. 8 2.1 Graphical License Manager Tool ................................................................ 8 List all installed license keys.................................................................. 8 Add and delete license keys .................................................................. 8 Display the properties of a license ......................................................... 9 Select between different license keys for a single product ......................... 9 2.2 Command Line License Manager Tool ........................................................ 9 List all installed license keys................................................................. -
![[D:]Path[...] Data Files](https://docslib.b-cdn.net/cover/6104/d-path-data-files-996104.webp)
[D:]Path[...] Data Files
Command Syntax Comments APPEND APPEND ; Displays or sets the search path for APPEND [d:]path[;][d:]path[...] data files. DOS will search the specified APPEND [/X:on|off][/path:on|off] [/E] path(s) if the file is not found in the current path. ASSIGN ASSIGN x=y [...] /sta Redirects disk drive requests to a different drive. ATTRIB ATTRIB [d:][path]filename [/S] Sets or displays the read-only, archive, ATTRIB [+R|-R] [+A|-A] [+S|-S] [+H|-H] [d:][path]filename [/S] system, and hidden attributes of a file or directory. BACKUP BACKUP d:[path][filename] d:[/S][/M][/A][/F:(size)] [/P][/D:date] [/T:time] Makes a backup copy of one or more [/L:[path]filename] files. (In DOS Version 6, this program is stored on the DOS supplemental disk.) BREAK BREAK =on|off Used from the DOS prompt or in a batch file or in the CONFIG.SYS file to set (or display) whether or not DOS should check for a Ctrl + Break key combination. BUFFERS BUFFERS=(number),(read-ahead number) Used in the CONFIG.SYS file to set the number of disk buffers (number) that will be available for use during data input. Also used to set a value for the number of sectors to be read in advance (read-ahead) during data input operations. CALL CALL [d:][path]batchfilename [options] Calls another batch file and then returns to current batch file to continue. CHCP CHCP (codepage) Displays the current code page or changes the code page that DOS will use. CHDIR CHDIR (CD) [d:]path Displays working (current) directory CHDIR (CD)[..] and/or changes to a different directory. -

LESSON 2 ESSENTIAL COMMANDS Lesson 2: Essential Commands
LESSON 2 ESSENTIAL COMMANDS Lesson 2: Essential Commands WARNING The Hacker Highschool Project is a learning tool and as with any learning tool there are dangers. Some lessons, if abused, may result in physical injury. Some additional dangers may also exist where there is not enough research on possible effects of emanations from particular technologies. Students using these lessons should be supervised yet encouraged to learn, try, and do. However ISECOM cannot accept responsibility for how any information herein is abused. The following lessons and workbooks are open and publicly available under the following terms and conditions of ISECOM: All works in the Hacker Highschool Project are provided for non-commercial use with elementary school students, junior high school students, and high school students whether in a public institution, private institution, or a part of home-schooling. These materials may not be reproduced for sale in any form. The provision of any class, course, training, or camp with these materials for which a fee is charged is expressly forbidden without a license, including college classes, university classes, trade-school classes, summer or computer camps, and similar. To purchase a license, visit the LICENSE section of the HHS web page at http://www.hackerhighschool.org/licensing.html. The Hacker Highschool Project Project is an open community effort and if you find value in this project, we ask that you support us through the purchase of a license, a donation, or sponsorship. 2 Lesson 2: Essential Commands Table -

Microsoft® Official Academic Course: Networking Fundamentals, Exam
Microsoft® Official Academic Course Networking Fundamentals, Exam 98-366 VP & PUBLISHER Barry Pruett SENIOR EXECUTIVE EDITOR Jim Minatel MICROSOFT PRODUCT MANAGER Microsoft Learning SENIOR EDITORIAL ASSISTANT Devon Lewis TECHNICAL EDITOR Ron Handlon CHANNEL MARKETING MANAGER Michele Szczesniak CONTENT MANAGEMENT DIRECTOR Lisa Wojcik CONTENT MANAGER Nichole Urban PRODUCTION COORDINATOR Nicole Repasky PRODUCTION EDITOR Umamaheswari Gnanamani COVER DESIGNER Tom Nery COVER PHOTO: © shutterstock/wavebreakmedia Copyright © 2017 by John Wiley & Sons, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc. 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030-5774, (201) 748-6011, fax (201) 748-6008. To order books or for customer service, please call 1-800-CALL WILEY (225-5945). Microsoft, Active Directory, AppLocker, Bing, BitLocker, Hyper-V, Internet Explorer, Microsoft Intune, Microsoft Office 365, SQL Server, Visual Studio, Windows Azure, Windows, Windows PowerShell, and Windows Server are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Other product and company names mentioned herein may be the trademarks of their respective owners. The example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious. -

Konsole and Line Commands
Konsole and Line commands Konsole is a terminal where you pass commands directly to the system instead of working with a graphical [user] interface (“GUI”). 1. The figure shows several examples of line commands: i. “pwd” (= print the workind directory) + ENTER. This is very useful when you want to know where you are! ii. “cd” (= change directory). This example illustrates a very useful feature when working with a terminal, especially when the name is long or when you can not remember the exact name. I type: “cd L” and then TAB. The system suggests two possibilities: LEARN and LATEX. Since I want to go to LEARN, I add the letter “E” to “cd L” and push TAB again. The system now completes the word and produces: “cd LEARN”. Now all I have to do is push the ENTER key and I am in the directory LEARN. If you are in some sub-directory and you want to go to /home/student, which is your main directory, then just type “cd” without specifying any further sub- directory. iii. “ls” (= list). Now that I am in LEARN, I want to see which files are there and so I type ls and then ENTER. If I just want to see which PDF files are in LEARN, I would type “ls *.pdf”. Here the asterisk stands for any number of missing characters and so is called a “wild card”. iv. In (2) and (3) we were look for a directory, but the same thing holds for com- mands. Try typing “o” plus TAB, them add a “c” to form “oc” plus TAB and finally—as in the snapshot—“oct” plus TAB. -

MS-DOS Microsoft Disk Operating System
emeronbEnßm MS-DOS Microsoft Disk Operating System 1-esckþIepþIm kñúgEpñkenH eyIgelIkykmkEtEpñkRKwHmYycMnUYn énRbB½n§tMeNIrkar edIm,IgayRsYl kñúgkar EsVgyl; MS-DOS nig eRbIR)as;bBa¢a rbs; . EtmunnwgsikSaeTAelIRbB½n§tMeNIrkar Gñk (Commad) DOS MS-DOS RtUvEsVgyl;eGay)anc,as;GMBIGVI ehAfa nig kñúg sin . File, Directory Directory Structure Windows - KWCasMnMuénÉksarEdlpÞúkenAelIépÞ rbs; ehIyvamaneQµaHtMNag nig File Media Disk TItaMgc,as;las;mYy . GacCakmµviFI Éksar b¤ File (Program), (Document) Collection of Data . .doc icon Extension Filename - KWCaTU b¤ CaftsMrab;pÞúkral; eTAtamRbePT gayRsYlcMnaM nig Directory or Folder Files EbgEck ehIyenAkñúg mYyGacmanftsMrab;pÞúkral; CaeRcInteTot ehAfa Directory Files Subdirectory or . Subfolder eTAkan; Path File POD.EXE 2-RbB½n§tMeNIrkarsMrab; IBM-PC kñúgEpñkenHeyIgnwgsikSa Cak;EsþgGMBI EdlCaRbePTkmµviFImYycMa)ac; CaTIbMput sMrab;RbePT DOS IBM-PC bc©úb,nñenH . mann½yfaenAmanRbB½n§tMeNIrkarepSg²CaeRcIneTot dUcCa sMrab;RbePT System Macintosh nigmanRbB½n§tMeNIrkar . UNIX,Windows ... RbB½n§tMeNIrkar KWCaRbB½n§kmµviFImYy eRbIsMrab;RtYtBinitüéntMeNIrkar RKb;RKgkarEbkEck (Operating System) nig eRbIR)as;épñkepSg² énma:sIundUcCa ryHeBlcaM)ac;sMrab; kareRbIR)as;én nwgk¾dUcCa CPU Memory bNþal]bkrN¾xageRkAepSg²eTot . 3- KWCaGVI DOS ? mkBIBaküfa mann½yfaCa RbB½n§tMeNIrkarrukrk nig eFVIkarelI DOS DISK OPERATING SYSTEM Disk (Harddisk or . vaCaRbB½n§RKb;RKg RKb;RKgÉksarenAelI dUcCakarcMlg lubnig karbegáIt Diskette) Disk Space Disk erobcMbegáIt b¤ .l. cUlGñkRsm½yemIlfaebIKµan RbB½n§tMeNIrkar Diectorys, Partition Track -

Agilent Technologies Connectivity Guide
Agilent Technologies USB/LAN/GPIB Interfaces Connectivity Guide Agilent Technologies Notices © Agilent Technologies, Inc. 2003, 2004 Warranty Restricted Rights Legend No part of this manual may be reproduced in The material contained in this docu- If software is for use in the performance of a any form or by any means (including elec- ment is provided “as is,” and is sub- U.S. Government prime contract or subcon- tronic storage and retrieval or translation ject to being changed, without notice, tract, Software is delivered and licensed as into a foreign language) without prior agree- “Commercial computer software” as ment and written consent from Agilent in future editions. Further, to the max- imum extent permitted by applicable defined in DFAR 252.227-7014 (June 1995), Technologies, Inc. as governed by United or as a “commercial item” as defined in FAR States and international copyright laws. law, Agilent disclaims all warranties, either express or implied, with regard 2.101(a) or as “Restricted computer soft- ware” as defined in FAR 52.227-19 (June Edition to this manual and any information contained herein, including but not 1987) or any equivalent agency regulation or contract clause. Use, duplication or disclo- Second edition, November 2004 limited to the implied warranties of sure of Software is subject to Agilent Tech- Agilent Technologies, Inc. merchantability and fitness for a par- nologies’ standard commercial license 815 14th St. SW ticular purpose. Agilent shall not be terms, and non-DOD Departments and Loveland, CO 80537 USA liable for errors or for incidental or Agencies of the U.S. -
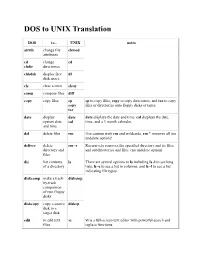
DOS to UNIX Translation
DOS to UNIX Translation DOS to... UNIX notes attrib change file chmod attributes cd change cd chdir directories chkdsk display free df disk space cls clear screen clear comp compare files diff copy copy files cp cp to copy files, copy to copy directories, and tar to copy copy files or directories onto floppy disks or tapes. tar date display date date displays the date and time, cal displays the date, system date cal time, and a 3 month calendar. and time del delete files rm Use caution with rm and wildcards, rm * removes all (no undelete option)! deltree delete rm -r Recursively removes the specified directory and its files directory and and subdirectories and files. (no undelete option) files dir list contents ls There are several options to ls including ls -l to see long of a directory lists, ls -c to see a list in columns, and ls -f to see a list indicating file types. diskcomp make a track- diskcmp by-track comparison of two floppy disks diskcopy copy a source diskcp disk to a target disk edit to edit text vi vi is a full-screen text editor with powerful search and files replace functions. edlin line editor ed ed and ex are predecessors of vi. ex fc compare two cmp cmp to compare binary files, diff compares two text files, files diff and diff3 compares three text files. diff3 find find text grep The UNIX find command finds files on the system, within a file and grep (global regular expression parser) finds text within a file.