A Comparison of Web Development Technologies: Webobjects Vs. ASP.NET
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

C# Programming
Course 419 C# Programming G419/CN/E.1/609/D.1 © LEARNING TREE INTERNATIONAL, INC. All rights reserved. All trademarked product and company names are the property of their respective trademark holders. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, or translated into any language, without the prior written permission of the publisher. Copying software used in this course is prohibited without the express permission of Learning Tree International, Inc. Making unauthorized copies of such software violates federal copyright law, which includes both civil and criminal penalties. Introduction and Overview Course Objectives In this course, we will discuss the syntax and semantics of C# as • An object-oriented language ◦ Using encapsulation, inheritance, interfaces, realization, polymorphism, associations, and aggregates • A component-oriented language focusing on reuse via the .NET Framework Library, including ◦ Desktop graphical and web-based user interfaces ◦ Enabling cross-language operation ◦ Performing I/O using serial streams and serialization ◦ Interfacing to legacy COM components • A data-oriented language ◦ Using LINQ and the Entity Framework COM = component object model I/O = input/output LINQ = Language Integrated Query © Learning Tree International, Inc. All rights reserved. Not to be reproduced without prior written consent. Intro-2 Course Contents Introduction and Overview Chapter 1 Overview and Development Environment Chapter 2 From Your Language to C# Chapter 3 User Interface Development Chapter 4 Defining User-Written Data Types Chapter 5 The .NET Framework Chapter 6 Interfaces and Polymorphism Chapter 7 Writing .NET Components Chapter 8 Accessing Databases Chapter 9 Other C# Features Chapter 10 Course Summary Next Steps © Learning Tree International, Inc. -

1. What Is .NET Framework?
1. What is .NET Framework? The .NET Framework is the foundation on which you can design, develop, and deploy applications. t is the core of the .NET infrastructure. t e!ists as a layer "etween the .NET applications and the underlying operating system. The .NET Framework encapsulates much of the "asic functionality, such as de"ugging and security services, which was earlier "uilt into various programming languages. #. What does .NET Framework consists of? The .NET Framework consists of We" forms, Windows forms, and console applications that pertain to the presentation layer of an application. We" forms are used in We"$"ased applications, whereas Windows Forms are used in Windows$"ased applications for providing an interactive user interface. n addition, you can create character$"ased console applications that can "e e!ecuted from the command line. %esides these three components, the .NET Framework consists of two other components, the .NET Framework %ase &lasses and the &ommon Language (untime )&'(). +. Write a note on, a. -rogramming methodologies The .isual /tudio .NET programming methodology allows for mixed$ language programming. This is esta"lished through a &ommon Type /ystem )&T/) that is de0ned for all the languages that .NET Framework supports. 1ll these languages compile into an intermediate language "efore they compile in native code. Therefore, the .NET developer has the independence to code one module of an application in one language and the other module of the same application in another language. ". -latform technologies The .NET Framework includes platform technologies like 1DO.NET, 1/-.NET, and .%.NET. 1DO.NET allows .NET applications to communicate with a data"ase for retrieving, accessing, and updating data. -
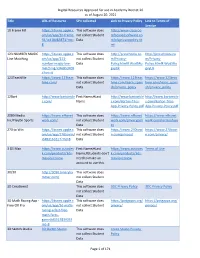
Digital Resources Approved for Use in Academy District 20 As Of
Digital Resources Approved for use in Academy District 20 as of August 20, 2021 Title URL of Resource SPII collected Link to Privacy Policy Link to Terms of Service 10 Frame Fill https://itunes.apple.c This software does http://www.classroo om/us/app/10-frame- not collect Student mfocusedsoftware.co fill/id418083871?mt= Data m/cfsprivacypolicy.ht 8 ml 123 NUMBER MAGIC https://itunes.apple.c This software does http://preschoolu.co http://preschoolu.co Line Matching om/us/app/123- not collect Student m/Privacy- m/Privacy- number-magic-line- Data Policy.html#.Wud5Ro Policy.html#.Wud5Ro matching/id46853409 gvyUk gvyUk 4?mt=8 123TeachMe https://www.123teac This software does https://www.123teac https://www.123teac hme.com/ not collect Student hme.com/learn_spani hme.com/learn_spani Data sh/privacy_policy sh/privacy_policy 12Bart http://www.bartontile First Name;#Last http://www.bartontile http://www.bartontile s.com/ Name s.com/Barton-Tiles- s.com/Barton-Tiles- App-Privacy-Policy.pdf App-Privacy-Policy.pdf 2080 Media https://www.nfhsnet This software does https://www.nfhsnet https://www.nfhsnet Inc/PlayOn Sports work.com/ not collect Student work.com/privacypoli work.com/termsofuse Data cy 270 to Win https://itunes.apple.c This software does https://www.270towi https://www.270towi om/us/app/270towin/ not collect Student n.com/privacy/ n.com/privacy/ id483161617?mt=8 Data 3 DS Max https://www.autodes First Name;#Last https://www.autodes Terms of Use k.com/products/3ds- Name;#Students don't k.com/products/3ds- max/overview need to make an max/overview account to use this. -

Dot Net Programming CLASS: TYBBA(CA) V SEM (2013 PATTERN)
DNYANSAGAR ARTS AND COMMERCE COLLEGE, BALEWADI, PUNE – 45 Subject: 503 : Dot Net Programming CLASS: TYBBA(CA) V SEM (2013 PATTERN) Unit 1 :Introduction to .Net Framework Introduction to .NET Framework .NET is a software framework which is designed and developed by Microsoft. The first version of the .Net framework was 1.0 which came in the year 2002. In easy words, it is a virtual machine for compiling and executing programs written in different languages like C#, VB.Net etc. It is used to develop Form-based applications, Web-based applications, and Web services. There is a variety of programming languages available on the .Net platform, VB.Net and C# being the most common ones. It is used to build applications for Windows, phone, web, etc. It provides a lot of functionalities and also supports industry standards. .NET Framework supports more than 60 programming languages in which 11 programming languages are designed and developed by Microsoft. The remaining Non-Microsoft Languages which are supported by .NET Framework but not designed and developed by Microsoft. Common Language Runtime(CLR): CLR is the basic and Virtual Machine component of the .NET Framework. It is the run-time environment in the .NET Framework that runs the codes and helps in making the development process easier by providing the various services such as remoting, thread management, type-safety, memory management, robustness, etc.. Basically, it is responsible for managing the execution of .NET programs regardless of any .NET programming language. It also helps in the management of code, as code that targets the runtime is known as the Managed Code and code doesn’t target to runtime is known as Unmanaged code. -

*Library/ Mentoring/ Association/ Club Activities *Library/ Mentoring
REGULATION 2020-21 B.Sc. INFORMATION TECHNOLOGY SEMSTER III B.Sc. INFORMATION TECHNOLOGY SL. COMPONENTS HOURS CREDITS PART III CORE SUBJECTS 1. Numerical Method and Operation Research 4 4 2. Object Oriented Programming with C++ 4 4 3. Object Oriented Programming with C++ - LAB 6 3 ALLIED SUBJECTS - 1 4. Data Structure 4 4 5. Data Structure – LAB 4 2 6. Skill Based Core Subject – I DTP 5(IT+4P) 4 7. Non – Major Elective – I 2 2 8. Common Yoga -- 2 TOTAL (5T + 3P = 8 COURSE) 30* 25 *Library/ Mentoring/ Association/ Club Activities SEMSTER IV B.Sc. INFORMATION TECHNOLOGY SL. COMPONENTS HOURS CREDITS PART III CORE SUBJECTS 1. Java Programming 4 4 2. Java Programming Lab 6 3 3. Operating System 4 4 ALLIED SUBJECTS - 1 4. Relational Data Base Management System 4 4 5. ORACLE – LAB 4 2 6. Skill Based Core Subject – II VISUAL PROGRAMMING 5(2T+3P) 4 7. Non – Major Elective – II 2 2 8. Computers for Digital Era -- 2 9. Extension Activity -- 1 10. Library Mentoring and Associations 1 -- TOTAL (5T + 3P = 8 COURSE) 30* 26 *Library/ Mentoring/ Association/ Club Activities SEMSTER V B.Sc. INFORMATION TECHNOLOGY SL. COMPONENTS HOURS CREDITS PART III CORE SUBJECTS 1. Scripting Language 4 4 2. Software Engineering and Testing 4 4 3. Data Communication and Networking 4 4 4. Scripting Language – LAB 6 3 5. Major Elective – I (Group – A) 4 4 Skill Based Common Subject – 6. Personality Development /Effective Communication/Youth 2 2 Leadership 7. Mini Project 5 5 TOTAL (5T + 1P + 1Project = 7 COURSE) 30* 26 *Library/ Mentoring/ Association/ Club Activities SEMSTER VI B.Sc. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Interview Questions ASP.NET
Interview Questions ASP.NET 1. Describe the role of inetinfo.exe, aspnet_isapi.dll andaspnet_wp.exe in the page loading process. inetinfo.exe is theMicrosoft IIS server running, handling ASP.NET requests among other things.When an ASP.NET request is received (usually a file with .aspx extension),the ISAPI filter aspnet_isapi.dll takes care of it by passing the request tothe actual worker process aspnet_wp.exe. 2. What’s the difference between Response.Write() andResponse.Output.Write()? The latter one allows you to write formattedoutput. 3. What methods are fired during the page load? Init() - when the pageis instantiated, Load() - when the page is loaded into server memory,PreRender() - the brief moment before the page is displayed to the user asHTML, Unload() - when page finishes loading. 4. Where does the Web page belong in the .NET Framework class hierarchy? System.Web.UI.Page 5. Where do you store the information about the user’s locale? System.Web.UI.Page.Culture 6. What’s the difference between Codebehind="MyCode.aspx.cs" andSrc="MyCode.aspx.cs"? CodeBehind is relevant to Visual Studio.NET only. 7. What’s a bubbled event? When you have a complex control, like DataGrid, writing an event processing routine for each object (cell, button, row, etc.) is quite tedious. The controls can bubble up their eventhandlers, allowing the main DataGrid event handler to take care of its constituents. 8. Suppose you want a certain ASP.NET function executed on MouseOver overa certain button. Where do you add an event handler? It’s the Attributesproperty, the Add function inside that property. -

Programming with Windows Forms
A P P E N D I X A ■ ■ ■ Programming with Windows Forms Since the release of the .NET platform (circa 2001), the base class libraries have included a particular API named Windows Forms, represented primarily by the System.Windows.Forms.dll assembly. The Windows Forms toolkit provides the types necessary to build desktop graphical user interfaces (GUIs), create custom controls, manage resources (e.g., string tables and icons), and perform other desktop- centric programming tasks. In addition, a separate API named GDI+ (represented by the System.Drawing.dll assembly) provides additional types that allow programmers to generate 2D graphics, interact with networked printers, and manipulate image data. The Windows Forms (and GDI+) APIs remain alive and well within the .NET 4.0 platform, and they will exist within the base class library for quite some time (arguably forever). However, Microsoft has shipped a brand new GUI toolkit called Windows Presentation Foundation (WPF) since the release of .NET 3.0. As you saw in Chapters 27-31, WPF provides a massive amount of horsepower that you can use to build bleeding-edge user interfaces, and it has become the preferred desktop API for today’s .NET graphical user interfaces. The point of this appendix, however, is to provide a tour of the traditional Windows Forms API. One reason it is helpful to understand the original programming model: you can find many existing Windows Forms applications out there that will need to be maintained for some time to come. Also, many desktop GUIs simply might not require the horsepower offered by WPF. -

Web Technologies-Ii
$ Edited by: Sarabjit Kumar WEB TECHNOLOGIES-II Edited By Sarabjit Kumar Printed by EXCEL BOOKS PRIVATE LIMITED A-45, Naraina, Phase-I, New Delhi-110028 for Lovely Professional University Phagwara SYLLABUS Web Technologies-II S. No. Topics 1. Making Sense of .NET & Anatomy of an ASP.NET Page: The Microsoft .NET Vision, ASP in NET, Introduction to C#, A Simple Web Page, Adding a Web Control, Introduction to In-Line Script, The Page Class. 2. Server Controls: Postback, Data Binding, Web Server Controls. 3. Server Controls: HTML Server Controls, Validation Controls. 4. Database Access: Error Handling, Database Access Using ADO.NET, Connection, Command, DataAdapter, and DataSet, DataReader, Connection Pooling. 5. Creating More Advanced ASP.NET Pages: Communicating with the Browser, Web.Config. 6. Creating More Advanced ASP.NET Pages: Page Sub-classing, User Controls, More Advanced Data Binding. 7. Applying What We’ve Learned So Far: The Database Model, Creating a Basic Object Model, Creating the User Interface. 8. Web Services: XML Web Services, Uses for Web Services, Web Services in Visual Studio .NET, Creating Web Services, Expanding Web Application with Web Services. 9. Security and Membership: IIS Security, ASP.NET Authentication. Adding E-Commerce Essentials: XML Tools, Freight Calculations, Email. 10. Debugging and Optimization: Debugging in an ASP.NET Application, Optimization, Optimizing Using Caching, Optimizing via Performance Profiling. CONTENT Unit 1: Making Sense of .NET and Anatomy of an ASP.Net Page 1 Kumar Vishal, Lovely -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Making Access Project and Data Technologies Choices
05 0672321025 CH03 8/10/01 8:20 AM Page 71 Making Access Project and CHAPTER Data Technologies Choices 3 IN THIS CHAPTER • Using Microsoft Database Versus Access Database Project 72 • Using DAO Versus ADO Versus XML 75 05 0672321025 CH03 8/10/01 8:20 AM Page 72 The Root of Power Programming 72 PART I Before Access 2000, when you created an application, you had to plan whether you wanted to use a Jet (the database engine Access uses natively) or a client/server back end. Depending on the type of back end chosen, you would use various methods to create the application. Although this is still the case, you now have more choices to make when starting on a project. Now, in addition to the back-end choice, you must decide what type of database container to use: the traditional MDB or ADP. The other choice to make is the method of accessing the data while working in VBA: DAO (Data Access Objects), which has been used since Access 2, or ADO (ActiveX Data Objects), the data-access technology now used throughout a number of Microsoft products, including Visual InterDev. You now have an additional choice of XML (Extensible Markup Language), which transfers data between systems and applications. Helping you decide which technology to use in which case is what this chapter is all about. When you first look at the choices, it’s hard to see when one should be used over another. NOTE This chapter isn’t intended as an in-depth discussion of these technologies. -

Webobjects Technical Overview
Session 401 WebObjects Technical Overview Steve Hayman Systems Engineer, Apple iServices 1 Apple Confidential 6/28/00 Introduction • Understand the WO architecture • See the tools, frameworks, and development process in action 2 Apple Confidential 6/28/00 What You’ll Learn • WO Tools • WO Frameworks • WO Deployment • Understand the titles of the other WO sessions 406—Rapid Development with Direct to Java Client 3 Apple Confidential 6/28/00 What WebObjects Does • It’s an Application Server • Who invented that term anyway? • It’s more than just that – Developer Tools – Pre-written objects (Frameworks) The best part! – Runtime environment – Monitoring and control tools 4 Apple Confidential 6/28/00 For Instance Java Clients Web Browsers Data Services Web Servers Distributed Objects Data Sources 5 Apple Confidential 6/28/00 Who WebObjects Is For • Developers • Very powerful • Steep learning curve • But that’s OK 6 Apple Confidential 6/28/00 WebObjects Works With… • Java. Objective-C. WebScript • Databases—Oracle, Informix, Sybase, SQL Server, LDAP, OpenBase, FrontBase, … • Mainframes—CORBA, 3270 screen-scraping • Different UIs—HTML, WAP, PDF, XML • Most web servers—Apache, Netscape, IIS • Lots of 3rd-party objects and APIs • Open open open open open open open open 7 Apple Confidential 6/28/00 Where You Can Use WebObjects • Develop on Mac OS X, Mac OS X Server, or Windows NT • Deploy on OS X, OS X Server, NT, Solaris, HP/UX, Linux – (Note: database support varies by platform) • Mix and match as needed • Start small and grow bigger 8 Apple Confidential