Mvm Journal of Research
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Politics of Dalit Mobilization in Tamil Nadu, India
Litigation against political organization? The politics of Dalit mobilization in Tamil Nadu, India Article (Accepted Version) Carswell, Grace and De Neve, Geert (2015) Litigation against political organization? The politics of Dalit mobilization in Tamil Nadu, India. Development and Change, 46 (5). pp. 1106-1132. ISSN 0012-155X This version is available from Sussex Research Online: http://sro.sussex.ac.uk/id/eprint/56843/ This document is made available in accordance with publisher policies and may differ from the published version or from the version of record. If you wish to cite this item you are advised to consult the publisher’s version. Please see the URL above for details on accessing the published version. Copyright and reuse: Sussex Research Online is a digital repository of the research output of the University. Copyright and all moral rights to the version of the paper presented here belong to the individual author(s) and/or other copyright owners. To the extent reasonable and practicable, the material made available in SRO has been checked for eligibility before being made available. Copies of full text items generally can be reproduced, displayed or performed and given to third parties in any format or medium for personal research or study, educational, or not-for-profit purposes without prior permission or charge, provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way. http://sro.sussex.ac.uk Litigation against Political Organization? The Politics of Dalit Mobilization in Tamil Nadu, India Grace Carswell and Geert De Neve ABSTRACT This article examines contemporary Dalit assertion in India through an ethnographic case study of a legal tool being mobilized by Tamil Nadu’s lowest-ranking Arunthathiyars in their struggle against caste-based offences. -

Read Book Migrations in Medieval and Early Colonial India 1St Edition
MIGRATIONS IN MEDIEVAL AND EARLY COLONIAL INDIA 1ST EDITION PDF, EPUB, EBOOK Vijaya Ramaswamy | 9781351558259 | | | | | Migrations in Medieval and Early Colonial India 1st edition PDF Book Download eBook. These can be changed versions of a language, new social customs and new deities or forms of worship. The caste is divided into a number of exogamous clans called Kootams. Satish Chandra — was a leading authority on Medieval Indian History. Vijaya Ramaswamy. Abc Large. A last ditch effort to save the colonial era AIT myth. Even when they settle in the host societies there is a minimum connection between their homeland and where they have settled. Mridula Mukherjee. Politics and Nation. Whether it is Turkish gastarbeiter in Germany, Japanese Nisei in Seattle, Filipinos in Kuwait, or Haitians in Brooklyn, the costs and benefits of human mobility on such a wide and rapid scale are hotly debated. From the genome, can you tell who is an Aryan? The Indian population is a result of four major migrations, including that of the Aryans , into the country in prehistoric times, says a new book. The lecture will discuss two categories of migrants, the pastoralists and the traders and will be confined to the early period of Indian history, namely up to about the fourteenth century. Migrations are being differentiated from the other forms of the movement of people, such as invasions and settlers. Historians in earlier years had tended to neglect the subject of migration but now it is receiving attention. This will be of great interest to scholars and students of migration and diaspora studies, medieval and modern South Asian history, social anthropology and subaltern studies. -

Love Meets Death: “Honour,” Violence, and Inter-Caste Marriages in Tamil Nadu
Love Meets Death: “Honour,” Violence, and Inter-caste Marriages in Tamil Nadu Perundevi Srinivasan* Introduction The decapitated body of a young man was found on a railway track near Pallipalayam village in Namakkal district, Tamil Nadu on June 24, 2015. The young man was identified as Gokulraj, a twenty-two-year-old engi- neering graduate from a Dalit caste (Paraiyar) from nearby Omalur in Salem district. Though it was initially speculated that he might have been run over by a train, post-mortem reports revealed that he had suffered multiple injuries prior to his death. The circumstances leading to this murder eventually became public. As the media reported it, Yuvaraj, the founder of Dheeran Chinnamalai Peravai, an outfit serving the “interests” of the Kongu Vellala Kavundar (hereafter, I will refer to it as Kavundar) caste, was allegedly involved in the murder.1 Yuvaraj and his accomplices, who belong to the caste outfit, are said to have abducted Gokulraj from the famous Siva-Ardhanariswarar temple, located at the top of a hillock in Tiruchengode, when they saw him along with his lover (kātali), a girl named Swathi of the Kavundar caste. The abduction was recorded by the temple’s CCTV camera and was subsequently listed as police evidence against the perpetrators. According to the police, the group took Gokulraj to a secluded place, murdered him, and dumped him on the railway track. The violence Dalit men face when they become romantically involved with or marry non-Dalit women from members of dominant caste groups is not entirely new to Tamil Nadu. -

Economic and Political Change and Caste Relations in Tamil Nadu Early in the 21St Century
Privilege in Dispute: Economic and Political Change and Caste Relations in Tamil Nadu Early in the 21st Century John Harriss Simons Papers in Security and Development No. 44/2014 | September 2015 Simons Papers in Security and Development No. 44/2015 2 The Simons Papers in Security and Development are edited and published at the School for International Studies, Simon Fraser University. The papers serve to disseminate research work in progress by the School’s faculty and associated and visiting scholars. Our aim is to encourage the exchange of ideas and academic debate. Inclusion of a paper in the series should not limit subsequent publication in any other venue. All papers can be downloaded free of charge from our website, www.sfu.ca/internationalstudies. The series is supported by the Simons Foundation. Series editor: Jeffrey T. Checkel Managing editor: Martha Snodgrass Harriss, John, Privilege in Dispute: Economic and Political Change and Caste Relations in Tamil Nadu Early in the 21st Century, Simons Papers in Security and Development, No. 44/2015, School for International Studies, Simon Fraser University, Vancouver, September 2015. ISSN 1922-5725 Copyright remains with the author. Reproduction for other purposes than personal research, whether in hard copy or electronically, requires the consent of the author(s). If cited or quoted, reference should be made to the full name of the author(s), the title, the working paper number and year, and the publisher. Copyright for this issue: John Harriss, jharriss(at)sfu.ca. School for International Studies Simon Fraser University Suite 7200 - 515 West Hastings Street Vancouver, BC Canada V6B 5K3 Privilege in Dispute: Caste Relations in Tamil Nadu 3 Privilege in Dispute: Economic and Political Change and Caste Relations in Tamil Nadu Early in the 21st Century Simons Papers in Security and Development No. -
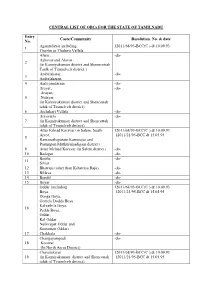
CENTRAL LIST of Obcs for the STATE of TAMILNADU Entry No
CENTRAL LIST OF OBC FOR THE STATE OF TAMILNADU E C/Cmm Rsoluti No. & da N. Agamudayar including 12011/68/93-BCC(C ) dt 10.09.93 1 Thozhu or Thuluva Vellala Alwar, -do- Azhavar and Alavar 2 (in Kanniyakumari district and Sheoncottah Taulk of Tirunelveli district ) Ambalakarar, -do- 3 Ambalakaran 4 Andi pandaram -do- Arayar, -do- Arayan, 5 Nulayar (in Kanniyakumari district and Shencottah taluk of Tirunelveli district) 6 Archakari Vellala -do- Aryavathi -do- 7 (in Kanniyakumari district and Shencottah taluk of Tirunelveli district) Attur Kilnad Koravar (in Salem, South 12011/68/93-BCC(C ) dt 10.09.93 Arcot, 12011/21/95-BCC dt 15.05.95 8 Ramanathapuram Kamarajar and Pasumpon Muthuramadigam district) 9 Attur Melnad Koravar (in Salem district) -do- 10 Badagar -do- Bestha -do- 11 Siviar 12 Bhatraju (other than Kshatriya Raju) -do- 13 Billava -do- 14 Bondil -do- 15 Boyar -do- Oddar (including 12011/68/93-BCC(C ) dt 10.09.93 Boya, 12011/21/95-BCC dt 15.05.95 Donga Boya, Gorrela Dodda Boya Kalvathila Boya, 16 Pedda Boya, Oddar, Kal Oddar Nellorepet Oddar and Sooramari Oddar) 17 Chakkala -do- Changayampadi -do- 18 Koravar (In North Arcot District) Chavalakarar 12011/68/93-BCC(C ) dt 10.09.93 19 (in Kanniyakumari district and Shencottah 12011/21/95-BCC dt 15.05.95 taluk of Tirunelveli district) Chettu or Chetty (including 12011/68/93-BCC(C ) dt 10.09.93 Kottar Chetty, 12011/21/95-BCC dt 15.05.95 Elur Chetty, Pathira Chetty 20 Valayal Chetty Pudukkadai Chetty) (in Kanniyakumari district and Shencottah taluk of Tirunelveli district) C.K. -

Salem - 11 M.A., Degree Programme (History) - Course Structure Cbcs Pattern Applicable to the Candidates Admitted from the Academic Year 2015-2016
1 PERIYAR UNIVERSITY – SALEM - 11 M.A., DEGREE PROGRAMME (HISTORY) - COURSE STRUCTURE CBCS PATTERN APPLICABLE TO THE CANDIDATES ADMITTED FROM THE ACADEMIC YEAR 2015-2016 Hrs/ UNI Total Exam Semester Course (Paper) Course Title Credits CIA Week Marks Marks Duration History of Ancient India (Pre History to 1206CE) I Core Course - I 6 4 25 75 100 3 Hrs (15HIC01) Core Course - II History of Medieval India 1206 to 1707 CE (15HIC02) 6 4 25 75 100 3 Hrs Social and Cultural History of Tamil Nadu upto 1565 Core Course -III 6 4 25 75 100 3 Hrs CE(15HIC03) Core Course - IV Indian National Movement 1885-1947 CE (15HIC04) 6 4 25 75 100 3 Hrs Tourism - Principles, Policies and Practices / Adventure Elective Course –I 6 4 25 75 100 3 Hrs and Sports Tourism (15HIE01) II Core Course –V History of Kongu Nadu (15HIC05) 5 5 25 75 100 3 Hrs Socio-Economic and Cultural History of Tamil Nadu in Core Course – VI 5 5 25 75 100 3 Hrs the 19th and 20th Centuries (15HIC06) Core course – VII History of Europe from 1453-1789 CE(15HIC07) 5 5 25 75 100 3 Hrs Travel Agency and Tour Operation Management / Elective Course -II 5 4 25 75 100 3 Hrs Health and Medical Tourism (15HIE02) 2 Hrs UNI Total Exam Semester Course (Paper) Course Title Credits CIA / Week Marks Marks Duration 1. India‘s March Towards Freedom Non Major Elective 2. Working of Indian Constitution 5 4 25 75 100 3 Hrs Course 3. Indian Culture and Heritage Core Course –VIII Human Rights(15HIC08) 5 4 25 75 100 3 Hrs History of Modern World – 1789 - III Core Course – IX 6 5 25 75 100 3 1945CE(15HIC09) Core Course -

The Age of Hurt Sentiments
ISSN (Online) - 2349-8846 The Age of Hurt Sentiments Attack on Puliyur Murugesan KANNAN SUNDARAM Vol. 50, Issue No. 11, 14 Mar, 2015 Kannan Sundaram ([email protected]) works with Kalachuvadu Publications. He is the publisher of Perumal Murugan’s writings including the novel Mathorubhagan. The attack on Tamil author Puliyur Murugesan, like the one on Perumal Murugan, prove that groups that play divisive politics of caste are gaining ground in Tamil Nadu. Tamil writer Puliyur Murugesan was attacked in Karur on 25 February 2015 for “offending the Kongu Vellala Gounder community”—the same community that was “offended” by Perumal Murugan’s writings, especially the novel, Mathorubhagan (translated in English as One Part Woman). Murugesan recently self-published a short story collection titled Balachandran Endroru Peyarum Enakku Undu (“I am also named Balachandran”). It is alleged that one of the stories, “I wear heavy makeup”, about the transgender community, hurt the sentiments of the Gounders. Attack After Demanding Apology There were several incidents of lawlessness in the town in protest against the book: blocking the Karur-Trichy road in Puliyur, stone-throwing, etc. According to press reports a leading light of the Gounders approached the writer and demanded an apology. He also demanded that the writer should publicly apologise before the Kaliyamman temple gathering. The writer reasoned that the story was not intended to hurt anyone; however he agreed to apologise. Even after this he was attacked by goons. A police complaint has been filed against him because the Superintendent of Police (Karur) Joshy Nirmal Kumar had read the text and deemed the book very “offensive”! No action has so far been taken against anyone for physically assaulting Murugesan. -

NREGA De Neve
NREGA and the Return of Identity Politics in Western Tamil Nadu, India Geert De Neve (Department of Anthropology, University of Sussex) Grace Carswell (Department of Geography, University of Sussex) In her piece, Pamela Price raises a number of fascinating questions about the possibility of a major shift in electoral politics in India which deserves further analytical attention and empirical observation. The thesis that electoral politics is being reshaped by development agendas and performance targets rather than being driven by a politics of identity and patron-clientelism is thought-provoking. Our comment aims to make a contribution to this debate with evidence from Tamil Nadu, which, as Price points out, is recognised as a state that is successful in implementing the NREGA and as a state whose recent DMK-led governments have pursued a populist politics driven by key development and poverty alleviation agendas. A good place, we believe, to think about political behaviour, policy, and identity politics. We start with some ground-level facts about the popular uptake and perception of NREGA (and other pro-poor policies) in Tamil Nadu and then move on to some wider reflections on electoral politics. On the way, we largely share Price’s scepticism about a shift away from identity politics and patron-client relationships with the rise of development-focused electoral agendas (Manor 2010, Thachil 2010). We also point to some, perhaps unexpected, outcomes of UPA and state-level economic policies: not merely a potential back-firing 1 for the Congress-led government but also an electoral politics reinvigorated by the politics of caste and the dynamics of a regional political economy. -

SNS COLLEGE of ENGINEERING, Coimbatore – 107
SNS COLLEGE OF ENGINEERING, Coimbatore – 107. Student Particular Form – 2014 Batch Branch : EEE Name : ANUSHASHRI.R Parent’s Name : G.RAJAPPAN - R.JAYAMALA Affix Recent Photograph Register No. : 100106121001 Roll No.: 10EE01 Date of Birth : 13/03/1993 Gender : F Email : [email protected] Mobile No. : 9003646561 Religion : Hindu Community: BC Caste: DEVANGA Address : ROOF NO 10, ANUPREENAM ILLAM SATHYA NAGAR ,SOUTH COLONY, KOMARAPALAYAM NAMAKKAL Pin code: 638183. Verified above details and found correct Signature of Tutor/Faculty Advisor Signature of the Student Date: SNS COLLEGE OF ENGINEERING, Coimbatore – 107. Student Particular Form – 2014 Batch Branch : EEE Name : ARULMOZHI.R Parent’s Name : R.RAJENDRAN - R.SUSILA Affix Recent Photograph Register No. : 100106121002 Roll No.: 10EE02 Date of Birth : 24/04/1993 Gender : F Email : [email protected] Mobile No. : 9659980740 Religion : Hindu Community: BC Caste: OKKALIGAR Address : 2/115 A, BILICHIGOUNDANUR SEELIYUR (VIA), KARAMADAI BUJANGANUR PO COIMBATORE Pin code: 641113. Verified above details and found correct Signature of Tutor/Faculty Advisor Signature of the Student Date: SNS COLLEGE OF ENGINEERING, Coimbatore – 107. Student Particular Form – 2014 Batch Branch : EEE Name : ARUNKUMAR.P Parent’s Name : R.PUGAZHENDHI - P.LAKSHMI Affix Recent Photograph Register No. : 100106121003 Roll No.: 10EE03 Date of Birth : 30/07/1992 Gender : M Email : [email protected] Mobile No. : 9843330099 Religion : Hindu Community: MBC Caste: VANNIYAR Address : L44, M.K.COLONY, MANDHARAKUPPAM NEYVELI Pin code: 607802. Verified above details and found correct Signature of Tutor/Faculty Advisor Signature of the Student Date: SNS COLLEGE OF ENGINEERING, Coimbatore – 107. Student Particular Form – 2014 Batch Branch : EEE Name : ARUN KUMAR.V Parent’s Name : C.VENUGOPAL (LATE) - B.JOTHIMANI Affix Recent Photograph Register No. -

ABSTRACT Title of Document: PLACE and CASTE IDENTIFICATION
ABSTRACT Title of Document: PLACE AND CASTE IDENTIFICATION: DISTANCIATION AND SPATIAL IMAGINARIES ON A CASTE-BASED SOCIAL NETWORK. Jillet Sarah Sam, Doctor of Philosophy, 2014 Directed By: Professor George Ritzer, Sociology This thesis studies the potency of place in mobilizing social categories, and its implications for both social categories and places. I use the theory of distanciation to study associations between caste identity and place. I conducted an ethnographic study of a caste-based digital group, the Cyber Thiyyars of Malabar, to understand the connections and disconnections between the Thiyya caste and Malabar from the perspectives of different sets of actors involved in the identification of caste, namely the nation-state and members of this caste-based network. The nation-state knows the Thiyya caste in a manner that is disconnected from Malabar, while the Cyber Thiyyars of Malabar seek to re-emphasize the identification of this caste through the region. Participant observation and in-depth interviews indicate that through references to Malabar, the group seeks to establish a Thiyya caste identity that is distinct from the Ezhavas, a caste group within which the nation-state subsumes them. I demonstrate that references to Malabar serve to counter the stigma that the Cyber Thiyyars of Malabar experience when the spatially abstract categorization of the Thiyyas interacts with notions of caste inferiority/superiority. Further, it serves as a mobilizational tool through which they hope to negotiate with the nation-state for greater access to affirmative action. I also demonstrate that caste identification continues to be relevant to the production of place. Place-based identification of the Thiyyas influences the manner in which the group envisions the physical boundaries of Malabar and how other social groups can belong to this region. -

Minutes of the Meeting of the Hon'ble Judges
IN THE HIGH COURT OF JUDICATURE AT MADRAS Reserved on : 20..01..2016 Delivered on : 05..07..2016 CORAM The Hon'ble Mr. SANJAY KISHAN KAUL, CHIEF JUSTICE and The Honourable Mrs. Justice PUSHPA SATHYANARAYANA Writ Petition Nos.1215 and 20372 of 2015 and Criminal Original Petition Nos.7086 and 7153 of 2015 W.P. No.1215 of 2015 1. S. Tamilselvan 2. Perumal Murugan … Petitioners (R-2 impleaded as per order dated 24.02.2015 in M.P. No.2 of 2015 in W.P. No.1215 of 2015) Versus 1. The Government of Tamil Nadu, Rep. by the Secretary, Home Department, Fort St. George, Chennai 600 009. 2. The District Collector, Namakkal. 3. The District Revenue Officer Tiruchencode, Namakkal District. 4. The Deputy Superintendent of Police Tiruchencode, Namakkal District. 5. Pon. Govindarasu, Arulmigu Arthanaareeswarar Girivala Nala Sangam, No.36, Anjaneyar Koil Street, Tiruchengode Taluk, Namakkal District. P a g e | 2 6. K. Chinnusamy, Hindu Munnani Office, Door No.74/34, Anjaneyar Koil Street, Tiruchengode, Namakkal District. 7. Kandasamy, President, Morur Kannakula Kongu Nattu Vellalar Trust, Morur Village & Post, Sangagiri Taluk, Salem District-637 304. 8. M. Madesh, President, Sengunthar Mahajana Sangam, No.9-H, B. Komarapalayam, Namakkal District. 9. P.T. Rajamanickam, General Secretary, Federation of Kongu Vellalar Sangam, Kongu Kalai Arangam, No.34, Sampath Nagar, Erode-11. 10. Mahalingam, President, Hindu Munnani, Tiruchengode Taluk, Namakkal District. 11. Yuvaraj, President, Dheeran Chinnamalai Peravai, Sangagiri, Salem District. 12. Anitha Velu, President, Lorry Owners Association, Tiruchengode, Namakkal District. 13. Muthusamy, T.V.A.N. Jewellery, President, Vaniga Peravai, Tiruchengode, Namakkal District. -

Sericul Ture and the Process of Change
SERICULTURE AND THE PROCESS OF CHANGE A SOCIO-CULTURAL STUDY OF A TAMIL NADU VILLAGE A Thesis Submitted to the University of Mysore For the Award of the Degree of DOCTOR OF PHILOSOPHY In Development Studies By SGREGORY Supervisor GKKARANTH Professor and Head Sociology Unit INSTITUTE FOR SOCIAL AND ECONOMIC CHANGE Nagarbhavi, Bangalore - 560 072 INDIA 1997 INSTITUTE FOR SOCIAL ISEC AND ECONOMIC CHANGE AN ALL INDIA INSTITUTE FOR INTER-DISCIPLINARY RESEARCH & TRAINING IN THE SOCIAL SCIENCES SILVER JUBILEE YEAR 1996 - 97 CERTI FI( 'ATE I hercby cl'rtit\ thai the prescnl ThesIs enlltkd Sericulture and Ihl' Procl'ss of Change A Socio-Cultural Study of A Tamil "'auu \'illage' is an independent rl'sl'arch of Shri S Gregory, PhD Ft:llow. Institute for Social and Economic Change, Bangalorc. carried out under mv guidance and supervision I also certif)' that it has not prcviously formed the basis for award of any Degree. Diploma or Associate Fellowship of Mysore Univcrsity or any othcr University / I ( Professor ilTld Head. Sociolog, Ilnlt Institute for Social & Econrymir. rC",nQ8 Na1 ar Jbhavi rlangabra • 550 ry72 PHONE 3355468 3355592 3355519 GRAMS. ECOSOCI Bangalore - 560 040 FAX 91-080-3387008 INDIA Nagarbhavi PO. Bangalore - 560072 E- MAll: ssisecOren.nic in DECLARATION I hereby declare that this Thesis entitled 'Sericulture and the Process of Change: A Soci<rCultural Study of A Tamil Nadu Village' is the result of my own work, carried out at the Institute for Social and Economic Change, Bangalore, and it has not been either wholly or in part submitted for any other degree.