The Mac Malware of 2019.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Preview Objective-C Tutorial (PDF Version)
Objective-C Objective-C About the Tutorial Objective-C is a general-purpose, object-oriented programming language that adds Smalltalk-style messaging to the C programming language. This is the main programming language used by Apple for the OS X and iOS operating systems and their respective APIs, Cocoa and Cocoa Touch. This reference will take you through simple and practical approach while learning Objective-C Programming language. Audience This reference has been prepared for the beginners to help them understand basic to advanced concepts related to Objective-C Programming languages. Prerequisites Before you start doing practice with various types of examples given in this reference, I'm making an assumption that you are already aware about what is a computer program, and what is a computer programming language? Copyright & Disclaimer © Copyright 2015 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book can retain a copy for future reference but commercial use of this data is not allowed. Distribution or republishing any content or a part of the content of this e-book in any manner is also not allowed without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected] ii Objective-C Table of Contents About the Tutorial .................................................................................................................................. -

Chapter 0X9: Dynamic Monitoring (Tools)
The Art of Mac Malware: Analysis p. wardle Chapter 0x9: Dynamic Monitoring (Tools) Note: This book is a work in progress. You are encouraged to directly comment on these pages ...suggesting edits, corrections, and/or additional content! To comment, simply highlight any content, then click the icon which appears (to the right on the document’s border). 1 The Art of Mac Malware: Analysis p. wardle Note: As dynamic analysis involves executing the malware (to observe its actions), always perform such analysis in a virtual machine (VM) or on a dedicated malware analysis machine. ...in other words, don’t perform dynamic analysis on your main (base) system! In this chapter, we’ll focus on various dynamic analysis monitoring tools. Specifically, we’ll illustrate how process, file, and network monitors can efficiently provide invaluable insight into the capabilities and functionality of malware specimens. Process Monitoring Malware often spawns or executes child processes. If observed via a process monitor, such processes may quickly provide insight into the behavior and capabilities of the malware. Often such processes are built-in (system) command line utilities that the malware executes in order to (lazily) delegate required actions. For example: ■ A malicious installer might invoke the move (/bin/mv) or copy (/bin/cp) utilities to persistently install the malware. ■ To survey the system, the malware might invoke the process status (/bin/ps) utility to get a list of running processes, or the /usr/bin/whoami utility to determine the current user’s permissions. ■ The results of this survey may then be exfiltrated to a remote command and control server via /usr/bin/curl. -

The “Stabs” Debug Format
The \stabs" debug format Julia Menapace, Jim Kingdon, David MacKenzie Cygnus Support Cygnus Support Revision TEXinfo 2017-08-23.19 Copyright c 1992{2021 Free Software Foundation, Inc. Contributed by Cygnus Support. Written by Julia Menapace, Jim Kingdon, and David MacKenzie. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License". i Table of Contents 1 Overview of Stabs ::::::::::::::::::::::::::::::: 1 1.1 Overview of Debugging Information Flow ::::::::::::::::::::::: 1 1.2 Overview of Stab Format ::::::::::::::::::::::::::::::::::::::: 1 1.3 The String Field :::::::::::::::::::::::::::::::::::::::::::::::: 2 1.4 A Simple Example in C Source ::::::::::::::::::::::::::::::::: 3 1.5 The Simple Example at the Assembly Level ::::::::::::::::::::: 4 2 Encoding the Structure of the Program ::::::: 7 2.1 Main Program :::::::::::::::::::::::::::::::::::::::::::::::::: 7 2.2 Paths and Names of the Source Files :::::::::::::::::::::::::::: 7 2.3 Names of Include Files:::::::::::::::::::::::::::::::::::::::::: 8 2.4 Line Numbers :::::::::::::::::::::::::::::::::::::::::::::::::: 9 2.5 Procedures ::::::::::::::::::::::::::::::::::::::::::::::::::::: 9 2.6 Nested Procedures::::::::::::::::::::::::::::::::::::::::::::: 11 2.7 Block Structure -

706 What's New in Security 07 FINAL.Key
System Frameworks #WWDC16 What’s New in Security Session 706 Lucia Ballard Secure Transports Engineering Manager Simon Cooper Trusted Execution Engineering Manager © 2016 Apple Inc. All rights reserved. Redistribution or public display not permitted without written permission from Apple. What’s New in Security? What’s New in Security? Network Security What’s New in Security? Network Security Cryptography APIs What’s New in Security? Network Security Cryptography APIs Platform Security on macOS What’s New in Network Security Lucia Ballard Secure Transports Engineering Manager Secure Communications Secure Communications HTTPS is the new HTTP • Confidentiality • Data integrity Secure Communications HTTPS is the new HTTP • Confidentiality • Data integrity Not all HTTPS is created equal App Transport Security Current standards App Transport Security Current standards For NSURLSession and NSURLConnection APIs App Transport Security Current standards For NSURLSession and NSURLConnection APIs • TLS v1.2 App Transport Security Current standards For NSURLSession and NSURLConnection APIs • TLS v1.2 • Strong crypto—AES-128 and SHA-2 App Transport Security Current standards For NSURLSession and NSURLConnection APIs • TLS v1.2 • Strong crypto—AES-128 and SHA-2 • Forward secrecy—ECDHE App Transport Security Current standards For NSURLSession and NSURLConnection APIs • TLS v1.2 • Strong crypto—AES-128 and SHA-2 • Forward secrecy—ECDHE Exceptions—global or for particular domains App Transport Security Enforcement App Transport Security Enforcement Enforced -

“A Magnetzed Needle and a Steady Hand”
“A Magne)zed Needle and a Steady Hand” Alternaves in the modern world of Integrated Development Environments Jennifer Wood CSCI 5828 Spring 2012 Real Programmers hp://xkcd.com/378/ For the rest of us • Modern Integrated Development Environments (IDE) – A one-stop shop with mul)ple features that can be easily accessed by the developer (without switching modes or ac)vang other u)li)es) to ease the task of creang soYware – A mul)tude of IDEs exist for each programming language (Java, C++, Python, etc.) and each plaorm (desktops, cell phones, web-based, etc.) – Some IDEs can handle mul)ple programming languages, but most are based in just one – There are many good free IDEs out there, but you can also pay for func)onality from $ to $$$$ – IDEs are like opinions, everyone has one and everyone thinks everyone else's s)nks Why are IDEs a good thing? • They aack many of the sources of accidental difficul)es in soYware development by having: – Real-)me protec)on from fault generang typos and bad syntax – High levels of abstrac)on to keep developers from being forced to redevelop basic (and not so basic) classes and structures for every project – IDE increases the power of many development tools by merging them into one that provides “integrated libraries, unified file formats, and pipes and filters. As a result, conceptual structures that in principle could always call, feed, and use one another can indeed easily do so in prac)ce.” (Brooks, 1987). • A core focus of IDE developers is con)nuous improvement in transparency to minimize searching for func)ons -

Programming Java for OS X
Programming Java for OS X hat’s so different about Java on a Mac? Pure Java applica- tions run on any operating system that supports Java. W Popular Java tools run on OS X. From the developer’s point of view, Java is Java, no matter where it runs. Users do not agree. To an OS X user, pure Java applications that ignore the feel and features of OS X are less desirable, meaning the customers will take their money elsewhere. Fewer sales translates into unhappy managers and all the awkwardness that follows. In this book, I show how to build GUIs that feel and behave like OS X users expect them to behave. I explain development tools and libraries found on the Mac. I explore bundling of Java applications for deployment on OS X. I also discuss interfacing Java with other languages commonly used on the Mac. This chapter is about the background and basics of Java develop- ment on OS X. I explain the history of Java development. I show you around Apple’s developer Web site. Finally, I go over the IDEs commonly used for Java development on the Mac. In This Chapter Reviewing Apple Java History Exploring the history of Apple embraced Java technologies long before the first version of Java on Apple computers OS X graced a blue and white Mac tower. Refugees from the old Installing developer tan Macs of the 1990s may vaguely remember using what was tools on OS X called the MRJ when their PC counterparts were busy using JVMs. Looking at the MRJ stands for Mac OS Runtime for Java. -

AV-TEST Security Report for 2016/2017
FACTS AND FIGURES SECURITY REPORT The AV-TEST Security Report 2 WINDOWS Security Status 5 macOS Security Status 10 ANDROID Security Status 13 INTERNET THREATS Security Status 16 IoT Security Status 19 2016/17 Test Statistics 22 FACTS AND FIGURES Declining malware statistics It remains positive to note that the declining malware trend in 2016 The AV-TEST provided some relief, at least quantitatively. Thus, compared to 2015, detection systems were required to seek out and defend against 14% fewer Security Report malware samples. In total, this amounted to precisely 11,725,292 fewer newly developed malware programs than in the previous year. It should not be The best news right off the bat: forgotten, however, that the volume of newly developed malware in 2016 still represented the second-highest since the beginning of measurements by Compared to the previous year, the AV-TEST systems. In addition, 2015 saw skyrocketing growth in malware the detection systems of AV-TEST showed programs and in comparison to 2014, practically a doubling of the sample statistics. The overall number of malware programs for all operating systems a slight decline in the development currently exceeds 640 million. of malware programs for the year 2016. Without wanting to belittle the positive trend for 2016, the fact remains that Overall, that is a pleasing trend, however there have been several short-term downward trends since the beginning of by no means any reason to celebrate, measurements in 1984, a total of six times, without seriously influencing the clear, long-term trend – towards more malware. Despite declining numbers, as evidenced by the AV-TEST Institute‘s in 2016, the AV-TEST analysis systems still recorded an average of 350,000 statistics of this year‘s Security Report. -

LAZARUS FREE PASCAL Développement Rapide
LAZARUS FREE PASCAL Développement rapide Matthieu GIROUX Programmation Livre de coaching créatif par les solutions ISBN 9791092732214 et 9782953125177 Éditions LIBERLOG Éditeur n° 978-2-9531251 Droits d'auteur RENNES 2009 Dépôt Légal RENNES 2010 Sommaire A) À lire................................................................................................................5 B) LAZARUS FREE PASCAL.............................................................................9 C) Programmer facilement..................................................................................25 D) Le langage PASCAL......................................................................................44 E) Calculs et types complexes.............................................................................60 F) Les boucles.....................................................................................................74 G) Créer ses propres types..................................................................................81 H) Programmation procédurale avancée.............................................................95 I) Gérer les erreurs............................................................................................105 J) Ma première application................................................................................115 K) Bien développer...........................................................................................123 L) L'Objet..........................................................................................................129 -

Intelligent OS X Malware Threat Detection with Code Inspection
This is a repository copy of Intelligent OS X malware threat detection with code inspection. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/128371/ Version: Published Version Article: Pajouh, H.H., Dehghantanha, A. orcid.org/0000-0002-9294-7554, Khayami, R. et al. (1 more author) (2018) Intelligent OS X malware threat detection with code inspection. Journal of Computer Virology and Hacking Techniques, 14 (3). pp. 213-223. ISSN 2274-2042 https://doi.org/10.1007/s11416-017-0307-5 Reuse This article is distributed under the terms of the Creative Commons Attribution (CC BY) licence. This licence allows you to distribute, remix, tweak, and build upon the work, even commercially, as long as you credit the authors for the original work. More information and the full terms of the licence here: https://creativecommons.org/licenses/ Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ J Comput Virol Hack Tech DOI 10.1007/s11416-017-0307-5 ORIGINAL PAPER Intelligent OS X malware threat detection with code inspection Hamed Haddad Pajouh1 · Ali Dehghantanha2 · Raouf Khayami1 · Kim-Kwang Raymond Choo3,4 Received: 31 July 2017 / Accepted: 27 September 2017 © The Author(s) 2017. This article is an open access publication Abstract With the increasing market share of Mac OS X over 91% detection accuracy with 3.9% false alarm rate. -
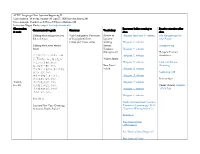
ALTEC Language Class: Japanese Beginning II
ALTEC Language Class: Japanese Beginning II Class duration: 10 weeks, January 28–April 7, 2020 (no class March 24) Class meetings: Tuesdays at 5:30pm–7:30pm in Hellems 145 Instructor: Megan Husby, [email protected] Class session Resources before coming to Practice exercises after Communicative goals Grammar Vocabulary & topic class class Talking about things that you Verb Conjugation: Past tense Review of Hiragana Intro and あ column Fun Hiragana app for did in the past of long (polite) forms Japanese your Phone (~desu and ~masu verbs) Writing Hiragana か column Talking about your winter System: Hiragana song break Hiragana Hiragana さ column (Recognition) Hiragana Practice クリスマス・ハヌカー・お Hiragana た column Worksheet しょうがつ 正月はなにをしましたか。 Winter Sports どこにいきましたか。 Hiragana な column Grammar Review なにをたべましたか。 New Year’s (Listening) プレゼントをかいましたか/ Vocab Hiragana は column もらいましたか。 Genki I pg. 110 スポーツをしましたか。 Hiragana ま column だれにあいましたか。 Practice Quiz Week 1, えいがをみましたか。 Hiragana や column Jan. 28 ほんをよみましたか。 Omake (bonus): Kasajizō: うたをききましたか/ Hiragana ら column A Folk Tale うたいましたか。 Hiragana わ column Particle と Genki: An Integrated Course in Japanese New Year (Greetings, Elementary Japanese pgs. 24-31 Activities, Foods, Zodiac) (“Japanese Writing System”) Particle と Past Tense of desu (Affirmative) Past Tense of desu (Negative) Past Tense of Verbs Discussing family, pets, objects, Verbs for being (aru and iru) Review of Katakana Intro and ア column Katakana Practice possessions, etc. Japanese Worksheet Counters for people, animals, Writing Katakana カ column etc. System: Genki I pgs. 107-108 Katakana Katakana サ column (Recognition) Practice Quiz Katakana タ column Counters Katakana ナ column Furniture and common Katakana ハ column household items Katakana マ column Katakana ヤ column Katakana ラ column Week 2, Feb. -

Portable Executable File Format
Chapter 11 Portable Executable File Format IN THIS CHAPTER + Understanding the structure of a PE file + Talking in terms of RVAs + Detailing the PE format + The importance of indices in the data directory + How the loader interprets a PE file MICROSOFT INTRODUCED A NEW executable file format with Windows NT. This for- mat is called the Portable Executable (PE) format because it is supposed to be portable across all 32-bit operating systems by Microsoft. The same PE format exe- cutable can be executed on any version of Windows NT, Windows 95, and Win32s. Also, the same format is used for executables for Windows NT running on proces- sors other than Intel x86, such as MIPS, Alpha, and Power PC. The 32-bit DLLs and Windows NT device drivers also follow the same PE format. It is helpful to understand the PE file format because PE files are almost identi- cal on disk and in RAM. Learning about the PE format is also helpful for under- standing many operating system concepts. For example, how operating system loader works to support dynamic linking of DLL functions, the data structures in- volved in dynamic linking such as import table, export table, and so on. The PE format is not really undocumented. The WINNT.H file has several struc- ture definitions representing the PE format. The Microsoft Developer's Network (MSDN) CD-ROMs contain several descriptions of the PE format. However, these descriptions are in bits and pieces, and are by no means complete. In this chapter, we try to give you a comprehensive picture of the PE format. -

Webobjects Bundle Reference
WebObjects Bundle Reference 2006-10-03 Times is a registered trademark of Apple Computer, Inc. Heidelberger Druckmaschinen AG, © 2006 Apple Computer, Inc. available from Linotype Library GmbH. All rights reserved. Simultaneously published in the United States and Canada. No part of this publication may be Even though Apple has reviewed this document, reproduced, stored in a retrieval system, or APPLE MAKES NO WARRANTY OR transmitted, in any form or by any means, REPRESENTATION, EITHER EXPRESS OR IMPLIED, WITH RESPECT TO THIS mechanical, electronic, photocopying, DOCUMENT, ITS QUALITY, ACCURACY, recording, or otherwise, without prior MERCHANTABILITY, OR FITNESS FOR A written permission of Apple Computer, Inc., PARTICULAR PURPOSE. AS A RESULT, THIS DOCUMENT IS PROVIDED “AS IS,” AND with the following exceptions: Any person YOU, THE READER, ARE ASSUMING THE is hereby authorized to store documentation ENTIRE RISK AS TO ITS QUALITY AND ACCURACY. on a single computer for personal use only IN NO EVENT WILL APPLE BE LIABLE FOR and to print copies of documentation for DIRECT, INDIRECT, SPECIAL, INCIDENTAL, personal use provided that the OR CONSEQUENTIAL DAMAGES documentation contains Apple’s copyright RESULTING FROM ANY DEFECT OR INACCURACY IN THIS DOCUMENT, even if notice. advised of the possibility of such damages. The Apple logo is a trademark of Apple THE WARRANTY AND REMEDIES SET FORTH ABOVE ARE EXCLUSIVE AND IN Computer, Inc. LIEU OF ALL OTHERS, ORAL OR WRITTEN, EXPRESS OR IMPLIED. No Apple dealer, agent, Use of the “keyboard” Apple logo or employee is authorized to make any (Option-Shift-K) for commercial purposes modification, extension, or addition to this without the prior written consent of Apple warranty.