Boa Motion to Dismiss
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2016 8Th International Conference on Cyber Conflict: Cyber Power
2016 8th International Conference on Cyber Conflict: Cyber Power N.Pissanidis, H.Rõigas, M.Veenendaal (Eds.) 31 MAY - 03 JUNE 2016, TALLINN, ESTONIA 2016 8TH International ConFerence on CYBER ConFlict: CYBER POWER Copyright © 2016 by NATO CCD COE Publications. All rights reserved. IEEE Catalog Number: CFP1626N-PRT ISBN (print): 978-9949-9544-8-3 ISBN (pdf): 978-9949-9544-9-0 CopyriGHT AND Reprint Permissions No part of this publication may be reprinted, reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of the NATO Cooperative Cyber Defence Centre of Excellence ([email protected]). This restriction does not apply to making digital or hard copies of this publication for internal use within NATO, and for personal or educational use when for non-profit or non-commercial purposes, providing that copies bear this notice and a full citation on the first page as follows: [Article author(s)], [full article title] 2016 8th International Conference on Cyber Conflict: Cyber Power N.Pissanidis, H.Rõigas, M.Veenendaal (Eds.) 2016 © NATO CCD COE Publications PrinteD copies OF THIS PUBlication are availaBLE From: NATO CCD COE Publications Filtri tee 12, 10132 Tallinn, Estonia Phone: +372 717 6800 Fax: +372 717 6308 E-mail: [email protected] Web: www.ccdcoe.org Head of publishing: Jaanika Rannu Layout: Jaakko Matsalu LEGAL NOTICE: This publication contains opinions of the respective authors only. They do not necessarily reflect the policy or the opinion of NATO CCD COE, NATO, or any agency or any government. -

Advanced Packaging Solutions
Advanced Packaging Solutions Highlights Providing silicon-scaling • Advanced packaging capabilities in solutions for tomorrow’s applications 2.5D, 3D, WLP and Silicon Photonics GLOBALFOUNDRIES post-fab services provide complementary and extended • Power, performance, cost and solutions with complete supply chain management including bump, probe, form-factor optimized solutions packaging and final test. The flexible supply chain model is tailored to your • Industry leader in smart interposers needs with services ranging from bump and probe only to a more comprehen- sive spectrum of services including package design, assembly and test. • In-house bump and wafer probe capabilities In addition to in-house bump and probe capabilities, we provide packaging • Advanced memory integration services in collaboration with a network of established OSAT partners, includ- with stacked memories ing 2D packages as well as 2.5D and 3D advanced package technologies. Test development and capabilities include RF, analog, embedded memory, • Ownership and process maturity for HVM and mmWave applications, with wide array of tester platforms for wafer sort operations. • Advanced silicon node CPI and qualification Packaging Requirements • RF system-in-package and Package types are selected based on performance requirements and optimized mmWave packaging capability for market segments including IoT, RF, Automotive, Mobile, High-end • Partnerships and strong relationships Computing, Networking and Storage. with leading-edge OSATs • Flexible supply chain and Mobile IoT RF Automotive Computing Networking Storage collaborative business models QFN FBGA WLCSP FOWLP SiP fcCSP FCBGA 2.5D 3D Si-PH Advanced Packaging Solutions Packaging Technologies TSV Si Interposer Availability GF Si nodes are qualified in a wide range of package Full Reticle 26x33mm2 technologies including 2D wirebond designs, flip Stitched Interposer >1300 mm2 chip, WLCSP and FOWLP configurations, as well 10:1 Aspect Ratio TSV 10um Dia./ 100um Depth as 2.5D, 3D and Si-Photonics. -

Introducing Linux on IBM Z Systems IT Simplicity with an Enterprise Grade Linux Platform
Introducing Linux on IBM z Systems IT simplicity with an enterprise grade Linux platform Wilhelm Mild IBM Executive IT Architect for Mobile, z Systems and Linux © 2016 IBM Corporation IBM Germany What is Linux? . Linux is an operating system – Operating systems are tools which enable computers to function as multi-user, multitasking, and multiprocessing servers. – Linux is typically delivered in a Distribution with many useful tools and Open Source components. Linux is hardware agnostic by design – Linux runs on multiple hardware architectures which means Linux skills are platform independent. Linux is modular and built to coexist with other operating systems – Businesses are using Linux today. More and more businesses proceed with an evolutionary solution strategy based on Linux. 2 © 2016 IBM Corporation What is IBM z Systems ? . IBM z Systems is the family name used by IBM for its mainframe computers – The z Systems families were named for their availability – z stands for zero downtime. The systems are built with spare components capable of hot failovers to ensure continuous operations. IBM z Systems paradigm – The IBM z Systems family maintains full backward compatibility. In effect, current systems are the direct, lineal descendants of System/360, built in 1964, and the System/370 from the 1970s. Many applications written for these systems can still run unmodified on the newest z Systems over five decades later. IBM z Systems variety of Operating Systems – There are different traditional Operating Systems that run on z Systems like z/OS, z/VSE or TPF. With z/VM IBM delivers a mature Hypervisor to virtualize the operating systems. -

Online Banking Customer Awareness and Education Program
Online Banking Customer Awareness and Education Program Online Banking Customer Awareness and Education Program Rev. 6/21 Table of Contents Online Banking Customer Awareness and Education Program Overview ............................................................... 1 Unsolicited Contact .................................................................................................................................................................... 1 Luther Burbank Savings Contact Information ................................................................................................................... 1 Online Banking Security Certification .................................................................................................................................. 1 Email Security............................................................................................................................................................................... 2 Malicious Emails ........................................................................................................................................................................ 2 Email Attachments .................................................................................................................................................................... 2 Verify Emails .............................................................................................................................................................................. 2 Strong and Complex -
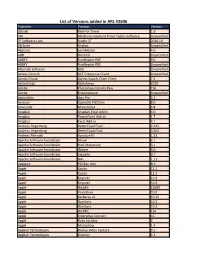
List of Versions Added in ARL #2606
List of Versions added in ARL #2606 Publisher Product Version 3bitlab Red Hot Timer 1.9 3M Medicare Inpatient Pricer Tables Software Unspecified 3T Software Labs Studio 3T 2020.10 AB Sciex Analyst Unspecified Abacom LochMaster 4.0 ABB WinCCU Unspecified ABBYY FineReader PDF 9.0 ABBYY FineReader PDF Unspecified Absolute Software DDS Unspecified Access Control ACT Enterprise Client Unspecified Access Group Access Supply Chain Client 7.2 ActiveCrypt DbDefence 2020 Adobe Photoshop Camera Raw CS6 Adobe Dreamweaver Unspecified algoriddim djay Pro 2.2 Amazon OpenJDK Platform 8.0 Anaconda Miniconda3 3.8 Anaplan Anaplan Excel Addin 4.0 Anaplan PowerPoint Add-in 1.7 Anaplan Excel Add-in 4.1 Andreas Hegenberg BetterTouchTool 2.425 Andreas Hegenberg BetterTouchTool 3.505 Andreas Pehnack Synalyze It! 1.23 Apache Software Foundation Hbase 2.1 Apache Software Foundation Hive Metastore 3.1 Apache Software Foundation JMeter 3.0 Apache Software Foundation zeppelin 0.7 Apache Software Foundation NiFi 1.11 Applanix POSPac UAV 8.5 Apple Xcode 12.1 Apple Xcode 12.2 Apple Keynote 10.2 Apple Keynote 10.3 Apple WebKit 15609 Apple VoiceOver 10.0 Apple Kerberos v5 10.15 Apple Numbers 10.2 Apple Numbers 10.3 Apple WebKit 156 Apple Enterprise Connect 16 Apple Ruby for Mac 2 Apple Monodraw 1.4 Applian Technologies Replay Video Capture 9.1 Applian Technologies Director 4.3 Applied Systems WealthTrack 10.0 Aranda Software Asset Management Unspecified ArcSoft WD Backup Unspecified ASG Technologies ASG-Zena Platform Agent 4.1 Aspose Aspose.Words for Reporting Services -

Introduction to Managing Mobile Devices Using Linux on System Z
Introduction to Managing Mobile Devices using Linux on System z SHARE Pittsburgh – Session 15692 Romney White ([email protected]) System z Architecture and Technology © 2014 IBM Corporation Mobile devices are 80% of devices sold to access the Internet Worldwide Shipment of Internet Access Devices 2013 2017 PC (Desktop & Notebook) PC (Ultrabook) Tablet Phone Worldwide Devices Shipments by Segment (Thousands of Units) Device Type 2012 2013 2014 2017 PC (Desk-Based and Notebook) 341,263 315,229 302,315 271,612 PC (Ultrabooks) 9,822 23,592 38,687 96,350 Tablet 116,113 197,202 265,731 467,951 Mobile Phone 1,746,176 1,875,774 1,949,722 2,128,871 Total 2,213,373 2,411,796 2,556,455 2,964,783 2 Source: Gartner (April 2013) © 2014 IBM Corporation Mobile Internet users will surpass PC internet users by 2015 The number of people accessing the Internet from smartphones, tablets and other mobile devices will surpass the number of users connecting from a home or office computer by 2015, according to a September 2013 study by market analyst firm IDC. PC is the new Legacy! 3 © 2014 IBM Corporation Five mobile trends with significant implications for the enterprise Mobile enables the Mobile is primary Internet of Things Mobile is primary 91% of mobile users keep Global Machine-to-machine 91% of mobile users keep their device within arm’s connections will increase their device within arm’s reach 100% of the time from 2 billion in 2011 to 18 reach 100% of the time billion at the end of 2022 Mobile must create a continuous brand Insights from mobile experience -

Software Withdrawal and Service Discontinuance: IBM Middleware, IBM Security, IBM Analytics, IBM Storage Software, and IBM Z
IBM United States Withdrawal Announcement 916-117, dated September 13, 2016 Software withdrawal and service discontinuance: IBM Middleware, IBM Security, IBM Analytics, IBM Storage Software, and IBM z Systems select products - Some replacements available Table of contents 1 Overview 107Replacement program information 10 Withdrawn programs 210Corrections Overview Effective on the dates shown, IBM(R) will withdraw support for the following program's VRM licensed under the IBM International Program License Agreement: VRM (V3.2.1) Note: V= All means all versions Note: V#.x means all releases of the version # listed Note: V#.#.x means all mods of the version release # listed For Advanced Administration System (AAS) Systems products Program number Program release VRM Withdrawal from name support date 5608-W07 IBM Tivoli(R) 3.2.x September 30, Storage 2017 (See Note FlashCopy(R) SUPT below) Manager For Passport Advantage(R) (PPA) On Premises products IBM Analytics products Program number Program release VRM Withdrawal from name support date 5639-I80 IBM Content 2.3.x September 30, Manager 2018 ImagePlus(R) Workstation program 5722-VI1 IBM DB2(R) 5.3.x September 30, Content Manager 2018 for iSeries 5724-B35 IBM InfoSphere(R) 5.5.x September 30, OptimTM 2016 Application Repository Analyzer 5724-B35 IBM InfoSphere 6.x September 30, Optim Application 2016 Repository Analyzer IBM United States Withdrawal Announcement 916-117 IBM is a registered trademark of International Business Machines Corporation 1 Program number Program release VRM Withdrawal -

Spring 2017 Industry Study Industry Report Electronics
Spring 2017 Industry Study Industry Report Electronics The Dwight D. Eisenhower School for National Security and Resource Strategy National Defense University Fort McNair, Washington, DC 20319-5062 i ELECTRONICS 2017 ABSTRACT: While currently assessed as mature and healthy, the global semiconductor industry is facing a strategic inflection point. This inflection will shape a future for the industry that is significantly different than the past. Although outlook for that future remains favorable, numerous challenges place that future at risk. Challenges found in Chinese competition, skilled workforce shortages, commercial semiconductor market shifts, unique DoD electronics needs, and ongoing requirements for rapid innovation threaten the stability of the market, the U.S. competitive advantage, and U.S. economic and national security. Future success in the industry hinges upon policies which address these challenges and enable U.S. companies to embrace future opportunities. LTC Khalid Alothman, Saudi Arabian Army CDR Terri L. Gabriel, U.S. Navy LTC Kevin F. Hanrahan, U.S. Army COL Jeffrey Howell, U.S. Army Mr. Benjamin Lam, U.S. Dept. of State Mr. Steven Mapes, Office of the Secretary of Defense Lt Col Adrian Meyer, Air National Guard COL Michael Samson, Philippine Army Col James E. Smith, U.S. Air Force Mr. Keith Smithson, Dept. of Energy COL William Smoot, U.S. Army Mr. Sim Walker, Dept. of the Army Lt Col Aaron Weiner, U.S. Air Force Ms. Denise L. Williams, Office of the Secretary of Defense Dr. Stephen Basile, Faculty Mr. Michael Dixon, Department of State, Faculty Col Thomas A. Santoro, Jr., U.S. Air Force, Faculty ii Industry Study Outreach and Field Studies On Campus Presenters BAE Systems, Inc., Arlington, VA Bureau of East Asian and Pacific Affairs, U.S. -

Heading Towards Big Data Building a Better Data Warehouse for More Data, More Speed, and More Users
Heading Towards Big Data Building A Better Data Warehouse For More Data, More Speed, And More Users Raymond Gardiner Goss [email protected] Kousikan Veeramuthu [email protected] Manufacturing Technology GLOBALFOUNDRIES Malta, NY, USA Abstract—As a new company, GLOBALFOUNDRIES is determine the caller’s income level and specify to which agent aggressively agile and looking at ways to not just mimic existing to route the call or the switch would timeout. When switches semiconductor manufacturing data management but to leverage were overwhelmed with data, they would drop packets and new technologies and advances in data management without algorithms had to infer states based on most probable current sacrificing performance or scalability. Being a global technology state. Other industries, such as social media, are challenged company that relies on the understanding of data, it is important to centralize the visibility and control of this information, bringing more by unstructured data and need tools to help turn text it to the engineers and customers as they need it. messages and photos into useful information for search engines and marketing purposes. The challenge in the semiconductor Currently, the factories are employing the best practices and world is with the size of the data. Speed becomes a secondary data architectures combined with business intelligence analysis problem because so many sources are needed to be joined and reporting tools. However, the expected growth in data over together in a timely manner. Large recipes, complex output the next several years and the need to deliver more complex data integration for analysis will easily stress the traditional tools from the test floor combined now with more Interface-A trace beyond the limits of the traditional data infrastructure. -

IBM® Security Trusteer Rapport™- Extension Installation
Treasury & Payment Solutions Quick Reference Guide IBM® Security Trusteer Rapport™- Extension Installation For users accessing Web-Link with Google Chrome or Mozilla Firefox, Rapport is also available to provide the same browser protection as is provided for devices using Internet Explorer. This requires that a browser extension be enabled. A browser extension is a plug-in software tool that extends the functionality of your web browser without directly affecting viewable content of a web page (for example, by adding a browser toolbar). Google Chrome Extension - How to Install: To install the extension from the Rapport console: 1. Open the IBM Security Trusteer Rapport Console by clicking Start>All Programs>Trusteer Endpoint Protection>Trusteer Endpoint Protection Console. 2. In the Product Settings area, next to ‘Chrome extension’, click install. Note: If Google Chrome is not set as your default browser, the link will open in whichever browser is set as default (e.g., Internet Explorer, as in the image below). 3. Copy the URL from the address bar below and paste it into a Chrome browser to continue: https://chrome.google.com/ webstore/detail/rapport/bbjllphbppobebmjpjcijfbakobcheof 4. Click +ADD TO CHROME to add the extension to your browser: Tip: If the Trusteer Rapport Console does not lead you directly to the Chrome home page, you can: 1. Click the menu icon “ ” at the top right of the Chrome browser window, choose “Tools” and choose “Extensions” to open a new “Options” tab. 1 Quick Reference Guide IBM Security Trusteer Rapport™ -Extension Installation 2. Select the Get more extensions link at the bottom of the page. -

RF CMOS: Integrated on a Chip FE ANALOG Modules: ANALOG
TowerJazz (TSEM) Investor and Analyst Day November 16, 2016 | New York Safe Harbor This presentation contains forward-looking statements within the meaning of the “safe harbor” provisions of the Private Securities Litigation Reform Act of 1995. These statements are based on management’s current expectations and beliefs and are subject to a number of risks, uncertainties and assumptions that could cause actual results to differ materially from those described in the forward-looking statements. All statements other than statements of historical fact are statements that could be deemed forward-looking statements. For example, statements regarding expected (i) customer demand, (ii) utilization and cross utilization of our Fabs, (iii) growth in our end markets, (iv) market and technology trends, and (v) growth in revenues, cash flow, margins and net profits are all forward-looking statements. Actual results may differ materially from those projected or implied by such forward-looking statements due to various risks and uncertainties applicable to TowerJazz’s business as described in the reports filed by Tower Semiconductor Ltd. (“Tower”) with the Securities and Exchange Commission (the “SEC”) and the Israel Securities Authority (“ISA”), including the risks identified under the heading "Risk Factors" in Tower’s most recent filings on Forms 20-F and 6-K. No assurances can be given that any of the events anticipated by the forward-looking statements will transpire or occur, or if any of them do, what impact they will have on the results of operations or financial condition of TowerJazz. TowerJazz is providing this information as of the date of this presentation and expressly disclaims any obligation to update any of the forward-looking statements or other information contained in this document as a result of new information, future events or otherwise. -

Service Description IBM Trusteer Fraud Protection This Service Description Describes the Cloud Service IBM Provides to Client
Service Description IBM Trusteer Fraud Protection This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized users and recipients of the Cloud Service. The applicable Quotation and Proof of Entitlement (PoE) are provided as separate Transaction Documents. 1. Cloud Service The following Cloud Services are covered by this Service Description: Pinpoint Assure Cloud Services: ● IBM Trusteer Pinpoint Assure ● IBM Trusteer Pinpoint Assure Application ● IBM Trusteer Mobile Carrier Intelligence Rapport Cloud Services: ● IBM Trusteer Rapport for Business Premium Support ● IBM Trusteer Rapport for Retail Premium Support ● IBM Trusteer Rapport II for Business ● IBM Trusteer Rapport II for Retail ● IBM Trusteer Rapport Fraud Feeds for Business ● IBM Trusteer Rapport Fraud Feeds for Business Premium Support ● IBM Trusteer Rapport Fraud Feeds for Retail ● IBM Trusteer Rapport Fraud Feeds for Retail Premium Support ● IBM Trusteer Rapport Phishing Protection for Business ● IBM Trusteer Rapport Phishing Protection for Business Premium Support ● IBM Trusteer Rapport Phishing Protection for Retail ● IBM Trusteer Rapport Phishing Protection for Retail Premium Support ● IBM Trusteer Rapport Mandatory Service for Business ● IBM Trusteer Rapport Mandatory Service for Retail ● IBM Trusteer Rapport Additional Applications for Retail ● IBM Trusteer Rapport Additional Applications for Business ● IBM Trusteer Rapport Large Redeployment ● IBM Trusteer Rapport Small Redeployment Pinpoint Cloud