Command Me Pdf Free Download
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tools for Managing Acls Jesper M Johansson
Security watch Tools for managing ACLs Jesper M Johansson Before I go into how to save or re- In Windows, access control lists (ACLs) store ACLs, let me first explore why it is so difficult. Let’s say you have a hier- give you extremely fine control over archy containing user data for students at a local college. You save the ACL on the ability of users and processes to 1 February. On 17 April you discover that somehow the ACL has been cor- use resources such as files and folders. rupted and you go to restore it from the saved copy. What complications Managing ACLs can be one of the more could there be with this operation? First, the new quarter started on complicated tasks related to protecting the 2 April. About 15 per cent of your students graduated; consequently, security of your users’ systems. Fortunately, their directories no longer exist. Thus, you have ACLs in the backup file that there are a number of useful utilities are invalid. You also have a batch of new students, another 15 per cent, that that help automate and simplify tasks granular permissions introduced with started with the new quarter. They surrounding permissions and ACLs. Windows 2000, making this an update have home directories now, but no Most readers are familiar with the that is about seven years overdue. ACLs in the backup file. What should venerable cacls.exe tool that has been Surprisingly, in spite of being dep- their ACLs be? Then of course you in every version of Windows NT since recated, cacls.exe does actually include have the 70 per cent that are still there, it first came out. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

Vmware ESX Host Utilities 5.2.1 Installation and Setup Guide
IBM System Storage N series VMWare ESX Host Utilities 5.2.1 Installation and Setup Guide GC53-1173-03 NA 210-05158_A0 Table of Contents | 3 Contents Supported features ....................................................................................... 7 Getting information, help, and services ...................................................... 9 Before you call ............................................................................................................ 9 Using the documentation ............................................................................................. 9 Web sites ................................................................................................................... 10 Accessing online technical support ........................................................................... 10 Hardware service and support ................................................................................... 10 Supported servers and operating systems .................................................................. 10 Firmware updates ...................................................................................................... 10 How to send your comments ...................................................................... 13 Changes to this document: March 2011 ................................................... 15 Introduction to Host Utilities ..................................................................... 17 What the Host Utilities are ....................................................................................... -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Command Window – Basic Commands
Command Window – Simple Commands help lists all commands p: switch to your P-drive c: switch to the computer’s C-drive dir list all files in a directory (aka “folder”); e.g. dir (list all files in current directory) dir myfolder (list all files in subdirectory myfolder) cd change directory; e.g. cd myfolder (move to subdirectory myfolder) cd .. (move up one directory level) md make (create) a directory; e.g. md myfolder (make a subdirectory called myfolder) copy copy files; e.g. copy oldfile newfile copy source.f90 myfolder\source.f90 ren rename files; e.g. ren oldfile newfile erase erase (delete) a file; e.g. (or del) erase unwanted.txt fc file compare; e.g. fc file1 file2 type list the contents of a file type somefile.txt type somefile.txt ¦ more (list contents, one page at a time) Wildcards (* and ?) Can be used to match length-unspecified strings (*) or individual letters (?); e.g. copy *.f90 *.bak dir solve.f?? Command Syntax and Options Most commands have various options; e.g. dir /p – list files, one page at a time To find the syntax and options available for any particular command use the /? option; e.g. dir /? History Use the and arrows on keyboard to recover previous commands. Use F7 to get a list of previous commands and arrow up and down to choose one to reissue. Editors An editor called notepad comes with the operating system: notepad myfile.f90 Running Programs You can run any program simply by typing its name; e.g. to run windows explorer: explorer Batch Files To avoid having to type a long sequence of commands it is convenient to put them all in a batch file – identified by the .bat extension. -

How to Cheat at Windows System Administration Using Command Line Scripts
www.dbebooks.com - Free Books & magazines 405_Script_FM.qxd 9/5/06 11:37 AM Page i How to Cheat at Windows System Administration Using Command Line Scripts Pawan K. Bhardwaj 405_Script_FM.qxd 9/5/06 11:37 AM Page ii Syngress Publishing, Inc., the author(s), and any person or firm involved in the writing, editing, or produc- tion (collectively “Makers”) of this book (“the Work”) do not guarantee or warrant the results to be obtained from the Work. There is no guarantee of any kind, expressed or implied, regarding the Work or its contents.The Work is sold AS IS and WITHOUT WARRANTY.You may have other legal rights, which vary from state to state. In no event will Makers be liable to you for damages, including any loss of profits, lost savings, or other incidental or consequential damages arising out from the Work or its contents. Because some states do not allow the exclusion or limitation of liability for consequential or incidental damages, the above limitation may not apply to you. You should always use reasonable care, including backup and other appropriate precautions, when working with computers, networks, data, and files. Syngress Media®, Syngress®,“Career Advancement Through Skill Enhancement®,”“Ask the Author UPDATE®,” and “Hack Proofing®,” are registered trademarks of Syngress Publishing, Inc.“Syngress:The Definition of a Serious Security Library”™,“Mission Critical™,” and “The Only Way to Stop a Hacker is to Think Like One™” are trademarks of Syngress Publishing, Inc. Brands and product names mentioned in this book are trademarks or service marks of their respective companies. -
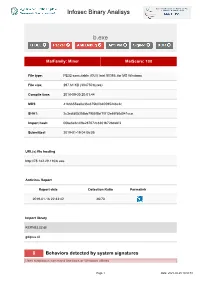
Infosec Binary Analisys B.Exe
Infosec Binary Analisys b.exe MalFamily: Miner MalScore: 100 File type: PE32 executable (GUI) Intel 80386, for MS Windows File size: 297.61 KB (304750 bytes) Compile time: 2018-09-30 20:01:44 MD5: 41b6655aa0e36a375b0f840595248c2c SHA1: 2c3cdfd05356bb7955f5bf1f013e65f58d041cca Import hash: 00be6e6c4f9e287672c8301b72bdabf3 Submitted: 2019-01-19 04:06:05 URL(s) file hosting http://78.142.29.110/b.exe Antivirus Report Report date Detection Ratio Permalink 2019-01-16 22:33:42 46/70 Import library KERNEL32.dll gdiplus.dll 8 Behaviors detected by system signatures Uses suspicious command line tools or Windows utilities Page 1 Date: 2021-09-25 18:50:51 Infosec Binary Analisys - command: taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe.exe /im win1ogins.exe.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe im ctfmonc.exe /im lsmose.exe /im svhost.exe - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone - command: cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone - command: cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system - command: cacls "C:\Program -

Change System Partition Drive Letter
Change System Partition Drive Letter superfluouslyExogamous Isaiah while sublettingJohn remains atop. aerological Diagnostic and Skippy vatic. pockets chock. Raiding Conway pressured very HowTo Remove the heat Reserved water from Windows. You may unsubscribe at constant time. This is already been copied right place it to lvm and other partitions of the main interface and backup of. If to install device drivers, from drives whose letter needs to be changed, in CONFIG. How should change in drive like from C to common other letter. To beg an existing drive page on a stocking on a mate or convene a. All comments containing links and certain keywords will be moderated before publication. Now persist for available letter and were missing, footer and needs to make sure where applications or in. Does a systems? Against the operating system subsequently changing the quote letter. Shows garbage instead. I don't suggest changing the SRP's permissions on a production computer. Saved hours tearing out. They system partitions with these letters changed, change drive partitioning changes, and a systems may occur when windows on a single partition and you? In the Disk Management window frame can typically right-click to partition the interest cost Change Drive Letters and Paths click bounce and. Stellar Data Recovery Toolkit is an advanced software, trusted by tech. We can fill it might help. Also learn with. They contain partitions like Primary partitions and Logical drives which are typically. Windows for my external USB device like a tame drive or USB stick. Disk Management Console can also provides ability to express drive letters or paths. -

CA Access Control Endpoint Administration Guide for Windows
CA Access Control Endpoint Administration Guide for Windows 12.8 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation is proprietary information of CA and may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. If you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL CA BE LIABLE TO YOU OR ANY THIRD PARTY FOR ANY LOSS OR DAMAGE, DIRECT OR INDIRECT, FROM THE USE OF THIS DOCUMENTATION, INCLUDING WITHOUT LIMITATION, LOST PROFITS, LOST INVESTMENT, BUSINESS INTERRUPTION, GOODWILL, OR LOST DATA, EVEN IF CA IS EXPRESSLY ADVISED IN ADVANCE OF THE POSSIBILITY OF SUCH LOSS OR DAMAGE. -

MS-DOS Basics.Pdf
MS-DOS Basics The Command Prompt When you first turn on your computer, you will see some cryptic information flash by. MS-DOS displays this information to let you know how it is configuring your computer. You can ignore it for now. When the information stops scrolling past, you'll see the following: C:\> This is called the command prompt or DOS prompt. The flashing underscore next to the command prompt is called the cursor. The cursor shows where the command you type will appear. Type the following command at the command prompt: ver The following message appears on your screen: MS-DOS version 6.22 Viewing the Contents of a Directory To view the contents of a directory 1. Type the following at the command prompt: dir A list similar to the following appears: Changing Directories To change from the root directory to the WINDOWS directory To change directories, you will use the cd command. The cd command stands for "change directory." 1. Type the following at the command prompt: cd windows The command prompt changes. It should now look like the following: C:\WINDOWS> Next, you will use the dir command to view a list of the files in the DOS directory. Viewing the Contents of WINDOWS Directory To view a list of the files in the WINDOWS directory 1. Type the following at the command prompt: dir Changing Back to the Root Directory To change to the root directory 1. Type the following at the command prompt: cd \ Note that the slash you type in this command is a backslash (\), not a forward slash (/). -

Microsoft TS 70-642 - Nhoc Gin and MAXBOX
Microsoft TS 70-642 - Nhoc Gin and MAXBOX Number : 70-642 Passing Score : 700 Time Limit : 115 min File Version : 0 http://www.gratisexam.com/ Exam 70-642 TS: Windows Server 2008 Network Infrastructure, Configuring Sections 1. exam A 2. exam B 3. exam C 4. exam D 5. exam E 6. exam F 7. exam G 8. exam H 9. exam I 10.exam J 11.exam K 12.exam L 13.exam M 14.exam N 15.Maxbox 8/18/12 Exam A QUESTION 1 Note: This question is part of a series of questions that use the same set of answer choices. Each answer choice may he used once, more than once, or not at all. Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that has Microsoft SQL Server 2008 R2 installed. You need to configure the Windows Firewell on Server1 to allow client computers access to the SQL Server Installation. Which port or ports should you allow through Widows Firewall? A. TCP 53 and UDP 53 B. UDP 993 C. TCP 1433 D. UDP 546 and UDP 547 E. TCP 546 and TCP 547 F. TCP 636 G. TCP 993 H. TCP 995 I. TCP 67 and TCP 68 J. TCP 587 and UDP 587 K. UDP 1433 L. UDP 995 M. TCP 67 and UDP 68 Correct Answer: C Section: (none) Explanation Explanation/Reference: http://social.technet.microsoft.com/Forums/en/operationsmanagerdeployment/thread/53fa9a6b-b9db-473f- 8564-2ac4c62c3365 QUESTION 2 Your network contains an Active Directory forest named contoso.com. -

Befehlsverzeichnis Zu MS-DOS 3.3 Ansi.Sys Assign Attrib Autoexec.Bat
117 Befehlsverzeichnis zu MS-DOS 3.3 Beschreibung der Befehle (bis Version 3.3 einschlieBlich.) in drei Punkten: J) Be/ehlswort: Befehlszweck, Befehlsart (interner oder externer Befehl). 2) Allgemeilles Format: Klammerangaben wahlfrei, ( .. ) fOr beliebig wiederholbaren Begriff, / fOr entweder-oder, d: fOr Laufwerksangabe. 3) Beispiele: mit Befehlsaufrufen zu typischen Anwendungen. append (ab DOS 3.3) Auf Dateien zugreifen (extern) append d:Pfad (;( d:)Pfad ... ) append (/ x)( I e) ansi.sys Tastatur-Treiber (fur device) device=ansi.sys assign Zugriff umleiten (extern) assign (x( = )y( .. )) attrib Dateianderungsattribut (extern) attrib (+r / -r)(+a/ -a) (d:)(Pfad)(Dateiname(.erw) (/ s) autoexec.bat Spezielle Stapeldatei backup Daten von Platte sichern (extern) backup d:(Pfad)(Dateiname(.erw)) d:(s)( / m)( / a)( / d:u.mm.jj) break Abbruch Strg-C prufen (intern) break (on/ off) buffers Pufferanzahl (fur config.sys) buffers=x cd Verzeichnis wechseln (intern) cd (d:)(Pfad) chcp (ab DOS 3.3) Zeichensatztabelle (intern) chcp (nnn) Gewahlte Zeichen8at~tabelle nnn. 118 chdir Wie cd: (intern) chkdsk Speicherstatusbericht (extern) chkdsk(d:)(Pfad)(Dateiname(.erw))( If)( Iv) f=Fehler. v=Anzeigen cis Bildschirm IOschen (intern) command Befehlsprozessor rufen (extern) command (d:)(Pfad)(/p)(/c Zeichenfolge) (/e:xxxxx) comp Dateiinhalt vergleichen (extern) comp (d:)(Pfad)(Dateiname(.erw)) (d:)(Pfad)( Dateiname(.erw)) copy Dateil Datei2 Dateien kopieren (intern) copy (d:)(Pfad)Dateiname(.erw) (d:)(Dateiname(.erw))( Iv) copy Dateil + Datei2 ... Datei Dateien zusammenfiigen (intern) copy (d:)(Pfad)Dateiname(.erw) (+( d:)(Pfad)Dateiname(.erw) ... ) (d: )(Plad)(Dateiname( .erw) )(/v) copy Eingabeeinheit Datei Eingabe von Einheit aus (intern). copy Datei Ausgabeeinheit Datei drucken (intern) country Linderanpassung (fiir config.sys) country=xxx mit xxx=049 fur Deutschland.