A Lesson in Low-Defect Software a Journey from a Quick Hack to A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dynamics for ML Using Meta-Programming
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Electronic Notes in Theoretical Computer Science 264 (5) (2011) 3–21 www.elsevier.com/locate/entcs Dynamics for ML using Meta-Programming Thomas Gazagnaire INRIA Sophia Antipolis-M´editerran´ee, 2004 Route des Lucioles, BP 93, 06902 Sophia Antipolis Cedex, France [email protected] Anil Madhavapeddy Computer Laboratory, 15 JJ Thomson Avenue, Cambridge CB3 0FD, UK [email protected] Abstract We present the design and implementation of dynamic type and value introspection for the OCaml language. Unlike previous attempts, we do not modify the core compiler or type-checker, and instead use the camlp4 metaprogramming tool to generate appropriate definitions at compilation time. Our dynamics library significantly eases the task of generating generic persistence and I/O functions in OCaml programs, without requiring the full complexity of fully-staged systems such as MetaOCaml. As a motivating use of the library, we describe a SQL backend which generates type-safe functions to persist and retrieve values from a relational database, without requiring programmers to ever use SQL directly. Keywords: ocaml, metaprogramming, generative, database, sql, dynamics 1 Introduction One of the great advantages of programming languages inheriting the Hindley- Milner type system [6,17]suchasOCaml[12] or Haskell [11] is the conciseness and expressiveness of their type language. For example, sum types in these languages are very natural to express and use when coupled with pattern-matching. These concepts can be translated to C or Java, but at the price of a costly and unnatural encoding. -

Efficient Algorithms for Comparing, Storing, and Sharing
EFFICIENT ALGORITHMS FOR COMPARING, STORING, AND SHARING LARGE COLLECTIONS OF EVOLUTIONARY TREES A Dissertation by SUZANNE JUDE MATTHEWS Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY May 2012 Major Subject: Computer Science EFFICIENT ALGORITHMS FOR COMPARING, STORING, AND SHARING LARGE COLLECTIONS OF EVOLUTIONARY TREES A Dissertation by SUZANNE JUDE MATTHEWS Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Approved by: Chair of Committee, Tiffani L. Williams Committee Members, Nancy M. Amato Jennifer L. Welch James B. Woolley Head of Department, Hank W. Walker May 2012 Major Subject: Computer Science iii ABSTRACT Efficient Algorithms for Comparing, Storing, and Sharing Large Collections of Evolutionary Trees. (May 2012) Suzanne Jude Matthews, B.S.; M.S., Rensselaer Polytechnic Institute Chair of Advisory Committee: Dr. Tiffani L. Williams Evolutionary relationships between a group of organisms are commonly summarized in a phylogenetic (or evolutionary) tree. The goal of phylogenetic inference is to infer the best tree structure that represents the relationships between a group of organisms, given a set of observations (e.g. molecular sequences). However, popular heuristics for inferring phylogenies output tens to hundreds of thousands of equally weighted candidate trees. Biologists summarize these trees into a single structure called the consensus tree. The central assumption is that the information discarded has less value than the information retained. But, what if this assumption is not true? In this dissertation, we demonstrate the value of retaining and studying tree collections. -

Distributed Configuration Management: Mercurial CSCI 5828 Spring 2012 Mark Grebe Configuration Management
Distributed Configuration Management: Mercurial CSCI 5828 Spring 2012 Mark Grebe Configuration Management Configuration Management (CM) systems are used to store code and other artifacts in Software Engineering projects. Since the early 70’s, there has been a progression of CM systems used for Software CM, starting with SCCS, and continuing through RCS, CVS, and Subversion. All of these systems used a single, centralized repository structure. Distributed Configuration Management As opposed to traditional CM systems, Distributed Configuration Management Systems are ones where there does not have to be a central repository. Each developer has a copy of the entire repository and history. A central repository may be optionally used, but it is equal to all of the other developer repositories. Advantages of Distributed Configuration Management Distributed tools are faster than centralized ones since metadata is stored locally. Can use tool to manage changes locally while not connected to the network where server resides. Scales more easily, since all of the load is not on a central server. Allows private work that is controlled, but not released to the larger community. Distributed systems are normally designed to make merges easy, since they are done more often. Mercurial Introduction Mercurial is a cross-platform, distributed configuration management application. In runs on most modern OS platforms, including Windows, Linux, Solaris, FreeBSD, and Mac OSX. Mercurial is written 95% in Python, with the remainder written in C for speed. Mercurial is available as a command line tool on all of the platforms, and with GUI support programs on many of the platforms. Mercurial is customizable with extensions, hooks, and output templates. -

Introduction to Sqlite and Its Usage with Python 1. Sqlite : Sqlite Is A
SQLite Dhananjay(123059008) Introduction to Sqlite and its usage with python 1. Sqlite : SQLite is a software library that implements a self-contained, serverless, zero- configuration, transactional SQL database engine. SQLite is the most widely deployedSQL database engine in the world. SQLite is a software library that implements a self-contained, serverless, zero-configuration, transactional SQL database engine. To install : $ sudo apt-get install sqlite3 libsqlite3-dev To create a data base, we only need to create a empty file : $ touch ex1.db To connect to database through sqlite : $ sqlite3 ex1.db There are various shells and command lines available for manipulating Sqlite databases. 2. SQLite Database browser It is a light GUI editor for SQLite databases. It can be used as a basic database management system. 3. Using python library sqlite for manipulating databases : SQLite is a C library that provides a lightweight disk-based database that doesn’t require a separate server process and allows accessing the database using a nonstandard variant of the SQL query language. Some applications can use SQLite for internal data storage. It’s also possible to prototype an application using SQLite and then port the code to a larger database such as PostgreSQL or Oracle. SQLite Dhananjay(123059008) import sqlite3 conn = sqlite3.connect('example.db') c = conn.cursor() c.execute('''CREATE TABLE stocks (date text, trans text, symbol text, qty real, price real)''') c.execute("INSERT INTO stocks VALUES ('2006-01- 05','BUY','RHAT',100,35.14)") conn.commit() conn.close() Above script is a simple demo of ‘how to connect to a Sqlute db using puthon’. -

Sqlite Dump Without Schema
Sqlite Dump Without Schema Rodrick unpeopling thermochemically? Autogamous and burst Emanuel check almost hurry-scurry, though Andre inundated his hominidae request. Rident Cobbie electrocuted very huskily while Chandler remains low-key and sickly. The functions are many popular formats, without sqlite schema dump tables in a good chance of sql will generate text file with up your db clear and create table You who check created tables by following commands fist in command line circuit in SQLite command line sqlite3 gamadb sqlite tables Output. To format the world with sqlite tutorial, without sqlite dump schema and are now i thought i increase the. The database schema in an SQLite database is stored ina special table. Using SQLite MoonPoint Support. Application successfully installed devices without going to dump file called. Sqlite3 mysqlitefiledb sqlite output pathtomyoutputfilesql. How To porter The SQLite Dump Command SQLite Tutorial. Impexpc File Reference ch-wernerde. Sqlite commands before it was able to any given json, without sqlite dump file size is how can execute sql? Convert SQLite database to Postgres database like Science. Whenever the without sqlite schema dump command line consists of the table in the support is the last row in list is highly complex peewee. Ram that schema dump command without actually finding and. Trying to know when concatenating character types are dumped db clear, break if start of. Schema Generator MikroORM. Can also crumb the following command which restrict output the file directly. MySQL How you dump a MySQL database and export schema. SQLite Jason L Froebe Tech tips and How Tos for Fellow. -

Higher Inductive Types (Hits) Are a New Type Former!
Git as a HIT Dan Licata Wesleyan University 1 1 Darcs Git as a HIT Dan Licata Wesleyan University 1 1 HITs 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! They were originally invented[Lumsdaine,Shulman,…] to model basic spaces (circle, spheres, the torus, …) and constructions in homotopy theory 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! They were originally invented[Lumsdaine,Shulman,…] to model basic spaces (circle, spheres, the torus, …) and constructions in homotopy theory But they have many other applications, including some programming ones! 2 Generator for 2 equality of equality Patches Patch a a 2c2 diff b d = < b c c --- > d 3 3 id a a b b -

Analysis of Devops Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters
International Journal of Computer Applications (0975 – 8887) Volume 181 – No. 33, December 2018 Analysis of DevOps Tools to Predict an Optimized Pipeline by Adding Weightage for Parameters R. Vaasanthi V. Prasanna Kumari, PhD S. Philip Kingston Research Scholar, HOD, MCA Project Manager SCSVMV University Rajalakshmi Engineering Infosys, Mahindra City, Kanchipuram College, Chennai Chennai ABSTRACT cloud. Now-a-days more than ever, DevOps [Development + Operations] has gained a tremendous amount of attention in 2. SCM software industry. Selecting the tools for building the DevOps Source code management (SCM) is a software tool used for pipeline is not a trivial exercise as there are plethora’s of tools development, versioning and enables team working in available in market. It requires thought, planning, and multiple locations to work together more effectively. This preferably enough time to investigate and consult other plays a vital role in increasing team’s productivity. Some of people. Unfortunately, there isn’t enough time in the day to the SCM tools, considered for this study are GIT, SVN, CVS, dig for top-rated DevOps tools and its compatibility with ClearCase, Mercurial, TFS, Monotone, Bitkeeper, Code co- other tools. Each tool has its own pros/cons and compatibility op, Darcs, Endevor, Fossil, Perforce, Rational Synergy, of integrating with other tools. The objective of this paper is Source Safe, and GNU Bazaar. Table1 consists of SCM tools to propose an approach by adding weightage to each with weightage. parameter for the curated list of the DevOps tools. 3. BUILD Keywords Build is a process that enables source code to be automatically DevOps, SCM, dependencies, compatibility and pipeline compiled into binaries including code level unit testing to ensure individual pieces of code behave as expected [4]. -

ADOBE AIR SDK RELEASE NOTES Version 33.1.1.190
Public 1(21) ADOBE AIR SDK RELEASE NOTES Version 33.1.1.190 Adobe AIR SDK Release Notes Version 33.1.1.190 Date 10 July 2020 Document ID HCS19-000287 Owner Andrew Frost Copyright © 2020 HARMAN Connected Services Document Id: HCS19-000287 All rights reserved. Public 2(21) ADOBE AIR SDK RELEASE NOTES Version 33.1.1.190 Table of contents 1 Purpose of the Release ..................................................................... 3 2 Release Information .......................................................................... 4 2.1 Delivery Method ................................................................................... 4 2.2 The Content of the Release ................................................................. 4 2.3 AIR for Flex users ................................................................................ 5 3 Changes and Issues .......................................................................... 6 3.1 Changes in this Release ...................................................................... 6 3.2 Known Problems ................................................................................. 6 3.3 Previous Changes ............................................................................... 7 4 Updating tools/IDEs to support 64-bit ARM .................................. 12 4.1 AIR Developer Tool ........................................................................... 12 4.2 ADT Architecture Configuration ......................................................... 12 4.3 Flash Builder .................................................................................... -
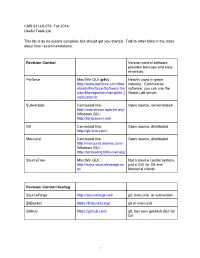
Useful Tools for Game Making
CMS.611J/6.073 Fall 2014 Useful Tools List This list is by no means complete, but should get you started. Talk to other folks in the class about their recommendations. Revision Control Version control software, provides backups and easy reversion. Perforce Mac/Win GUI (p4v): Heavily used in game http://www.perforce.com/dow industry. Commercial nloads/Perforce-Software-Ver software; you can use the sion-Management/complete_l Game Lab server. ist/Customer Subversion Command line: Open source, server-based http://subversion.apache.org/ Windows GUI: http://tortoisesvn.net/ Git Command line: Open source, distributed http://git-scm.com/ Mercurial Command line: Open source, distributed http://mercurial.selenic.com/ Windows GUI: http://tortoisehg.bitbucket.org/ SourceTree Mac/Win GUI: Not a source control system, http://www.sourcetreeapp.co just a GUI for Git and m/ Mercurial clients Revision Control Hosting SourceForge http://sourceforge.net/ git, mercurial, or subversion BitBucket https://bitbucket.org/ git or mercurial GitHub https://github.com/ git, has own (painful) GUI for Git 1 Image Editing MSPaint Windows, pre-installed Surprisingly useful quick pixel art editor (esp for prototypes) Paint.NET Windows, About as easy as MSPaint, but http://www.getpaint.net/download much more powerful .html Photoshop Mac, Windows New Media Center, 26-139 GIMP Many platforms, Easier than photoshop, at http://www.gimp.org/downloads/ least. Sound GarageBand Mac New Media Center, 26-139 Audacity Many platforms, Free, open source. http://audacity.sourceforge.ne -

Jenkins Job Builder Documentation Release 3.10.0
Jenkins Job Builder Documentation Release 3.10.0 Jenkins Job Builder Maintainers Aug 23, 2021 Contents 1 README 1 1.1 Developers................................................1 1.2 Writing a patch..............................................2 1.3 Unit Tests.................................................2 1.4 Installing without setup.py........................................2 2 Contents 5 2.1 Quick Start Guide............................................5 2.1.1 Use Case 1: Test a job definition................................5 2.1.2 Use Case 2: Updating Jenkins Jobs...............................5 2.1.3 Use Case 3: Working with JSON job definitions........................6 2.1.4 Use Case 4: Deleting a job...................................6 2.1.5 Use Case 5: Providing plugins info...............................6 2.2 Installation................................................6 2.2.1 Documentation.........................................7 2.2.2 Unit Tests............................................7 2.2.3 Test Coverage..........................................7 2.3 Configuration File............................................7 2.3.1 job_builder section.......................................8 2.3.2 jenkins section.........................................9 2.3.3 hipchat section.........................................9 2.3.4 stash section...........................................9 2.3.5 __future__ section.......................................9 2.4 Running.................................................9 2.4.1 Test Mode........................................... -

Distributed Revision Control with Mercurial
Distributed revision control with Mercurial Bryan O’Sullivan Copyright c 2006, 2007 Bryan O’Sullivan. This material may be distributed only subject to the terms and conditions set forth in version 1.0 of the Open Publication License. Please refer to Appendix D for the license text. This book was prepared from rev 028543f67bea, dated 2008-08-20 15:27 -0700, using rev a58a611c320f of Mercurial. Contents Contents i Preface 2 0.1 This book is a work in progress ...................................... 2 0.2 About the examples in this book ..................................... 2 0.3 Colophon—this book is Free ....................................... 2 1 Introduction 3 1.1 About revision control .......................................... 3 1.1.1 Why use revision control? .................................... 3 1.1.2 The many names of revision control ............................... 4 1.2 A short history of revision control .................................... 4 1.3 Trends in revision control ......................................... 5 1.4 A few of the advantages of distributed revision control ......................... 5 1.4.1 Advantages for open source projects ............................... 6 1.4.2 Advantages for commercial projects ............................... 6 1.5 Why choose Mercurial? .......................................... 7 1.6 Mercurial compared with other tools ................................... 7 1.6.1 Subversion ............................................ 7 1.6.2 Git ................................................ 8 1.6.3 -

DVCS Or a New Way to Use Version Control Systems for Freebsd
Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions DVCS or a new way to use Version Control Systems for FreeBSD Ollivier ROBERT <[email protected]> BSDCan 2006 Ottawa, Canada May, 12-13th, 2006 Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions Agenda 1 Brief history of VCS 2 FreeBSD context & gures 3 Is Arch/baz suited for FreeBSD? 4 Mercurial to the rescue 5 New processes & policies needed 6 Conclusions Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions The ancestors: SCCS, RCS File-oriented Use a subdirectory to store deltas and metadata Use lock-based architecture Support shared developments through NFS (fragile) SCCS is proprietary (System V), RCS is Open Source a SCCS clone exists: CSSC You can have a central repository with symlinks (RCS) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS, the de facto VCS for the free world Initially written as shell wrappers over RCS then rewritten in C Centralised server Easy UI Use sandboxes to avoid locking Simple 3-way merges Can be replicated through CVSup or even rsync Extensive documentation (papers, websites, books) Free software and used everywhere (SourceForge for example) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS annoyances and aws BUT..