Dash1.Thinkaboutthefuture.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Venti Analysis and Memventi Implementation
Master’s thesis Venti analysis and memventi implementation Designing a trace-based simulator and implementing a venti with in-memory index Mechiel Lukkien [email protected] August 8, 2007 Committee: Faculty of EEMCS prof. dr. Sape J. Mullender DIES, Distributed and Embedded Systems ir. J. Scholten University of Twente ir. P.G. Jansen Enschede, The Netherlands 2 Abstract [The next page has a Dutch summary] Venti is a write-once content-addressed archival storage system, storing its data on magnetic disks: each data block is addressed by its 20-byte SHA-1 hash (called score). This project initially aimed to design and implement a trace-based simula- tor matching Venti behaviour closely enough to be able to use it to determine good configuration parameters (such as cache sizes), and for testing new opti- misations. A simplistic simulator has been implemented, but it does not model Venti behaviour accurately enough for its intended goal, nor is it polished enough for use. Modelled behaviour is inaccurate because the advanced optimisations of Venti have not been implemented in the simulator. However, implementation suggestions for these optimisations are presented. In the process of designing the simulator, the Venti source code has been investigated, the optimisations have been documented, and disk and Venti per- formance have been measured. This allowed for recommendations about per- formance, even without a simulator. Beside magnetic disks, also flash memory and the upcoming mems-based storage devices have been investigated for use with Venti; they may be usable in the near future, but require explicit support. The focus of this project has shifted towards designing and implementing memventi, an alternative implementation of the venti protocol. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

Persistent 9P Sessions for Plan 9
Persistent 9P Sessions for Plan 9 Gorka Guardiola, [email protected] Russ Cox, [email protected] Eric Van Hensbergen, [email protected] ABSTRACT Traditionally, Plan 9 [5] runs mainly on local networks, where lost connections are rare. As a result, most programs, including the kernel, do not bother to plan for their file server connections to fail. These programs must be restarted when a connection does fail. If the kernel’s connection to the root file server fails, the machine must be rebooted. This approach suffices only because lost connections are rare. Across long distance networks, where connection failures are more common, it becomes woefully inadequate. To address this problem, we wrote a program called recover, which proxies a 9P session on behalf of a client and takes care of redialing the remote server and reestablishing con- nection state as necessary, hiding network failures from the client. This paper presents the design and implementation of recover, along with performance benchmarks on Plan 9 and on Linux. 1. Introduction Plan 9 is a distributed system developed at Bell Labs [5]. Resources in Plan 9 are presented as synthetic file systems served to clients via 9P, a simple file protocol. Unlike file protocols such as NFS, 9P is stateful: per-connection state such as which files are opened by which clients is maintained by servers. Maintaining per-connection state allows 9P to be used for resources with sophisticated access control poli- cies, such as exclusive-use lock files and chat session multiplexers. It also makes servers easier to imple- ment, since they can forget about file ids once a connection is lost. -

HTTP-FUSE Xenoppix
HTTP-FUSE Xenoppix Kuniyasu Suzaki† Toshiki Yagi† Kengo Iijima† Kenji Kitagawa†† Shuichi Tashiro††† National Institute of Advanced Industrial Science and Technology† Alpha Systems Inc.†† Information-Technology Promotion Agency, Japan††† {k.suzaki,yagi-toshiki,k-iijima}@aist.go.jp [email protected], [email protected] Abstract a CD-ROM. Furthermore it requires remaking the entire CD-ROM when a bit of data is up- dated. The other solution is a Virtual Machine We developed “HTTP-FUSE Xenoppix” which which enables us to install many OSes and ap- boots Linux, Plan9, and NetBSD on Virtual plications easily. However, that requires in- Machine Monitor “Xen” with a small bootable stalling virtual machine software. (6.5MB) CD-ROM. The bootable CD-ROM in- cludes boot loader, kernel, and miniroot only We have developed “Xenoppix” [1], which and most part of files are obtained via Internet is a combination of CD/DVD bootable Linux with network loopback device HTTP-FUSE “KNOPPIX” [2] and Virtual Machine Monitor CLOOP. It is made from cloop (Compressed “Xen” [3, 4]. Xenoppix boots Linux (KNOP- Loopback block device) and FUSE (Filesys- PIX) as Host OS and NetBSD or Plan9 as Guest tem USErspace). HTTP-FUSE CLOOP can re- OS with a bootable DVD only. KNOPPIX construct a block device from many small block is advanced in automatic device detection and files of HTTP servers. In this paper we describe driver integration. It prepares the Xen environ- the detail of the implementation and its perfor- ment and Guest OSes don’t need to worry about mance. lack of device drivers. -

Text Processing Tools
Tools for processing text David Morgan Tools of interest here sort paste uniq join xxd comm tr fmt sed fold head file tail dd cut strings 1 sort sorts lines by default can delimit fields in lines ( -t ) can sort by field(s) as key(s) (-k ) can sort fields of numerals numerically ( -n ) Sort by fields as keys default sort sort on shell (7 th :-delimited) field UID as secondary (tie-breaker) field 2 Do it numerically versus How sort defines text ’s “fields ” by default ( a space character, ascii 32h = ٠ ) ٠bar an 8-character string ٠foo “By default, fields are separated by the empty string between a non-blank character and a blank character.” ٠bar separator is the empty string between non-blank “o” and the space ٠foo 1 2 ٠bar and the string has these 2 fields, by default ٠foo 3 How sort defines text ’s “fields ” by –t specification (not default) ( a space character, ascii 32h = ٠ ) ٠bar an 8-character string ٠foo “ `-t SEPARATOR' Use character SEPARATOR as the field separator... The field separator is not considered to be part of either the field preceding or the field following ” separators are the blanks themselves, and fields are ' "٠ " ٠bar with `sort -t ٠foo whatever they separate 12 3 ٠bar and the string has these 3 fields ٠foo data sort fields delimited by vertical bars field versus sort field ("1941:japan") ("1941") 4 sort efficiency bubble sort of n items, processing grows as n 2 shell sort as n 3/2 heapsort/mergesort/quicksort as n log n technique matters sort command highly evolved and optimized – better than you could do it yourself Big -O: " bogdown propensity" how much growth requires how much time 5 sort stability stable if input order of key-equal records preserved in output unstable if not sort is not stable GNU sort has –stable option sort stability 2 outputs, from same input (all keys identical) not stable stable 6 uniq operates on sorted input omits repeated lines counts them uniq 7 xxd make hexdump of file or input your friend testing intermediate pipeline data cf. -

QLOAD Queue Load / Unload Utility for IBM MQ
Queue Load / Unload Utility for IBM MQ User Guide Version 9.1.1 27th August 2020 Paul Clarke MQGem Software Limited [email protected] Queue Load / Unload Utility for IBM MQ Take Note! Before using this User's Guide and the product it supports, be sure to read the general information under "Notices” Twenty-fourth Edition, August 2020 This edition applies to Version 9.1.1 of Queue Load / Unload Utility for IBM MQ and to all subsequent releases and modifications until otherwise indicated in new editions. (c) Copyright MQGem Software Limited 2015, 2020. All rights reserved. ii Queue Load / Unload Utility for IBM MQ Notices The following paragraph does not apply in any country where such provisions are inconsistent with local law. MQGEM SOFTWARE LIMITED PROVIDES THIS PUBLICATION "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore this statement may not apply to you. The information contained in this document has not be submitted to any formal test and is distributed AS IS. The use of the information or the implementation of any of these techniques is a customer responsibility and depends on the customer's ability to evaluate and integrate them into the customer's operational environment. While each item has been reviewed by MQGem Software for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. -

Plan 9 from Bell Labs
Plan 9 from Bell Labs “UNIX++ Anyone?” Anant Narayanan Malaviya National Institute of Technology FOSS.IN 2007 What is it? Advanced technology transferred via mind-control from aliens in outer space Humans are not expected to understand it (Due apologies to lisperati.com) Yeah Right • More realistically, a distributed operating system • Designed by the creators of C, UNIX, AWK, UTF-8, TROFF etc. etc. • Widely acknowledged as UNIX’s true successor • Distributed under terms of the Lucent Public License, which appears on the OSI’s list of approved licenses, also considered free software by the FSF What For? “Not only is UNIX dead, it’s starting to smell really bad.” -- Rob Pike (circa 1991) • UNIX was a fantastic idea... • ...in it’s time - 1970’s • Designed primarily as a “time-sharing” system, before the PC era A closer look at Unix TODAY It Works! But that doesn’t mean we don’t develop superior alternates GNU/Linux • GNU’s not UNIX, but it is! • Linux was inspired by Minix, which was in turn inspired by UNIX • GNU/Linux (mostly) conforms to ANSI and POSIX requirements • GNU/Linux, on the desktop, is playing “catch-up” with Windows or Mac OS X, offering little in terms of technological innovation Ok, and... • Most of the “modern ideas” we use today were “bolted” on an ancient underlying system • Don’t believe me? A “modern” UNIX Terminal Where did it go wrong? • Early UNIX, “everything is a file” • Brilliant! • Only until people started adding “features” to the system... Why you shouldn’t be working with GNU/Linux • The Socket API • POSIX • X11 • The Bindings “rat-race” • 300 system calls and counting.. -

From Donor to Patient: Collection, Preparation and Cryopreservation of Fecal Samples for Fecal Microbiota Transplantation
diseases Review From Donor to Patient: Collection, Preparation and Cryopreservation of Fecal Samples for Fecal Microbiota Transplantation Carole Nicco 1 , Armelle Paule 2, Peter Konturek 3 and Marvin Edeas 1,* 1 Cochin Institute, INSERM U1016, University Paris Descartes, Development, Reproduction and Cancer, Cochin Hospital, 75014 Paris, France; [email protected] 2 International Society of Microbiota, 75002 Paris, France; [email protected] 3 Teaching Hospital of the University of Jena, Thuringia-Clinic Saalfeld, 07318 Saalfeld, Germany; [email protected] * Correspondence: [email protected] Received: 6 March 2020; Accepted: 10 April 2020; Published: 15 April 2020 Abstract: Fecal Microbiota Transplantation (FMT) is suggested as an efficacious therapeutic strategy for restoring intestinal microbial balance, and thus for treating disease associated with alteration of gut microbiota. FMT consists of the administration of fresh or frozen fecal microorganisms from a healthy donor into the intestinal tract of diseased patients. At this time, in according to healthcare authorities, FMT is mainly used to treat recurrent Clostridium difficile. Despite the existence of a few existing stool banks worldwide and many studies of the FMT, there is no standard method for producing material for FMT, and there are a multitude of factors that can vary between the institutions. The main constraints for the therapeutic uses of FMT are safety concerns and acceptability. Technical and logistical issues arise when establishing such a non-standardized treatment into clinical practice with safety and proper governance. In this context, our manuscript describes a process of donor safety screening for FMT compiling clinical and biological examinations, questionnaires and interviews of donors. -

A Type System for Format Strings E
ifact t * r * Comple t te A A n * te W E is s * e C n l l o D C A o * * c T u e m S s E u e S e n I R t v A Type System for Format Strings e o d t y * s E a * a l d u e a t Konstantin Weitz Gene Kim Siwakorn Srisakaokul Michael D. Ernst University of Washington, USA {weitzkon,genelkim,ping128,mernst}@cs.uw.edu ABSTRACT // Untested code (Hadoop) Most programming languages support format strings, but their use Resource r = ... format("Insufficient memory %d", r); is error-prone. Using the wrong format string syntax, or passing the wrong number or type of arguments, leads to unintelligible text // Unchecked input (FindBugs) output, program crashes, or security vulnerabilities. String urlRewriteFormat = read(); This paper presents a type system that guarantees that calls to format(urlRewriteFormat, url); format string APIs will never fail. In Java, this means that the API will not throw exceptions. In C, this means that the API will not // User unaware log is a format routine (Daikon) log("Exception " + e); return negative values, corrupt memory, etc. We instantiated this type system for Java’s Formatter API, and // Invalid syntax for Formatter API (ping-gcal) evaluated it on 6 large and well-maintained open-source projects. format("Unable to reach {0}", server); Format string bugs are common in practice (our type system found Listing 1: Real-world code examples of common programmer 104 bugs), and the annotation burden on the user of our type system mistakes that lead to format routine call failures. -

(Brief) 2. an Extensible Compiler for Systems Programming
Show and Tell 1. Plan 9 Things (brief) 2. An Extensible Compiler for Systems Programming Russ Cox rsc@plan9 1127 Show and Tell April 19, 2005 who am i ................................................................................................................. ‘‘Neighborhood kid’’ 1995 summer hacking Excel (jlb) 1995-1997 cable modems (nls, tom) 1997-1999 annoying Plan 9 user 1999 summer doing Plan 9 graphics (rob, jmk) 1999-present assorted Plan 9 hacking Plan 9 Things ........................................................................................................ VBE ߝ use BIOS to set up VGA modes ߝ requires switching into real mode and back Venti ߝ reworked significantly ߝ aggressive caching, prefetching, batching, delayed writes ߝ Bloom filter to avoid index misses Plan 9 from User Space (plan9port) ߝ port bulk of Plan 9 software to Unix systems ߝ Linux, FreeBSD, NetBSD, SunOS, Mac OS X .................................................................................................................................... An Extensible Compiler for Systems Programming Russ Cox Frans Kaashoek Eddie Kohler [email protected] Outline ..................................................................................................................... Why bother? What could it do? How could it work? Ground rules: ߝ interrupt with questions ߝ work in progress ߝ show and tell, not a job talk Man vs. Machine ߝ Linguistic Tensions ................................................... The most important readers of a program are people. -
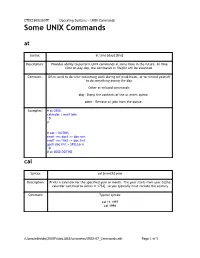
Some UNIX Commands At
CTEC1863/2007F Operating Systems – UNIX Commands Some UNIX Commands at Syntax: at time [day] [file] Description: Provides ability to perform UNIX commands at some time in the future. At time time on day day, the commands in filefile will be executed. Comment: Often used to do time-consuming work during off-peak hours, or to remind yourself to do something during the day. Other at-related commands: atq - Dump the contents of the at event queue. atrm - Remove at jobs from the queue. Examples: # at 0300 calendar | mail john ^D # # cat > DOTHIS nroff -ms doc1 >> doc.fmt nroff -ms file2 >> doc.fmt spell doc.fmt > SPELLerrs ^D # at 0000 DOTHIS cal Syntax: cal [month] year Description: Prints a calendar for the specified year or month. The year starts from year 0 [the calendar switched to Julian in 1752], so you typically must include the century Comment: Typical syntax: cal 11 1997 cal 1998 /Users/mboldin/2007F/ctec1863/unixnotes/UNIX-07_Commands.odt Page 1 of 5 CTEC1863/2007F Operating Systems – UNIX Commands calendar Syntax: calendar [-] Description: You must set-up a file, typically in your home directory, called calendar. This is a database of events. Comment: Each event must have a date mentioned in it: Sept 10, 12/5, Aug 21 1998, ... Each event scheduled for the day or the next day will be listed on the screen. lpr Syntax: lpr [OPTIONS] [FILE] [FILE] ... Description: The files are queued to be output to the printer. Comment: On some UNIX systems, this command is called lp, with slightly different options. Both lpr and lp first make a copy of the file(s) to be printed in the spool directory. -

The Effectiveness of Deduplication on Virtual Machine Disk Images
The Effectiveness of Deduplication on Virtual Machine Disk Images Keren Jin Ethan L. Miller Storage Systems Research Center Storage Systems Research Center University of California, Santa Cruz University of California, Santa Cruz [email protected] [email protected] ABSTRACT quired while preserving isolation between machine instances. Virtualization is becoming widely deployed in servers to ef- This approach better utilizes server resources, allowing many ficiently provide many logically separate execution environ- different operating system instances to run on a small num- ments while reducing the need for physical servers. While ber of servers, saving both hardware acquisition costs and this approach saves physical CPU resources, it still consumes operational costs such as energy, management, and cooling. large amounts of storage because each virtual machine (VM) Individual VM instances can be separately managed, allow- instance requires its own multi-gigabyte disk image. More- ing them to serve a wide variety of purposes and preserving over, existing systems do not support ad hoc block sharing the level of control that many users want. However, this between disk images, instead relying on techniques such as flexibility comes at a price: the storage required to hold overlays to build multiple VMs from a single “base” image. hundreds or thousands of multi-gigabyte VM disk images, Instead, we propose the use of deduplication to both re- and the inability to share identical data pages between VM duce the total storage required for VM disk images and in- instances. crease the ability of VMs to share disk blocks. To test the One approach saving disk space when running multiple effectiveness of deduplication, we conducted extensive eval- instances of operating systems on multiple servers, whether uations on different sets of virtual machine disk images with physical or virtual, is to share files between them; i.