Automated Malware Analysis Report For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Musescore 2.0 Handbook
Handbook Downloaded from musescore.org on Jun 08 2017 Released under Creative Commons Attribution-ShareAlike GETTING STARTED 17 INSTALLATION 17 INSTALL ON WINDOWS 17 Install 17 Start MuseScore 21 Uninstall 21 Troubleshooting 21 External links 21 CREATE A NEW SCORE 21 Start center 21 Create new score 22 Title, composer and other information 22 Select template 23 Choose instruments or voice parts 24 Add staff 25 Add Linked Staff 25 Select key signature and tempo 25 Time signature, pickup measure (anacrusis), and number of measures 26 Adjustments to score after creation 27 Add/delete measures 27 Add/edit text 27 Change instrument set-up 27 Templates 27 User template folder 27 System template folder 27 See also 28 External links 28 INSTALL ON MACOS 28 Install 28 Uninstall 29 Install with Apple Remote Desktop 29 External links 29 INSTALL ON LINUX 29 AppImage 29 Step 1 - Download 29 Step 2 - Give execute permission 30 Step 3 - Run it! 30 Installing the AppImage (optional) 30 Using command line options 30 Distribution Packages 31 Fedora 31 External links 31 INSTALL ON CHROMEBOOK 31 External links 31 LANGUAGE SETTINGS AND TRANSLATION UPDATES 31 Change language 32 Update translation 32 See also 33 External links 33 CHECKING FOR UPDATES 33 Automated update check 33 Check for update 34 See also 34 BASICS 35 2 NOTE INPUT 35 Basic note entry (Step-time) 35 Step 1: Starting position 35 Step 2: Note input mode 35 Step 3: Duration of the note (or rest) 35 Step 4: Enter pitch (or rest) 35 Other input modes 35 Input devices 36 Mouse 36 Keyboard 36 MIDI -

ACS – the Archival Cytometry Standard
http://flowcyt.sf.net/acs/latest.pdf ACS – the Archival Cytometry Standard Archival Cytometry Standard ACS International Society for Advancement of Cytometry Candidate Recommendation DRAFT Document Status The Archival Cytometry Standard (ACS) has undergone several revisions since its initial development in June 2007. The current proposal is an ISAC Candidate Recommendation Draft. It is assumed, however not guaranteed, that significant features and design aspects will remain unchanged for the final version of the Recommendation. This specification has been formally tested to comply with the W3C XML schema version 1.0 specification but no position is taken with respect to whether a particular software implementing this specification performs according to medical or other valid regulations. The work may be used under the terms of the Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free to share (copy, distribute and transmit), and adapt the work under the conditions specified at http://creativecommons.org/licenses/by-sa/3.0/legalcode. Disclaimer of Liability The International Society for Advancement of Cytometry (ISAC) disclaims liability for any injury, harm, or other damage of any nature whatsoever, to persons or property, whether direct, indirect, consequential or compensatory, directly or indirectly resulting from publication, use of, or reliance on this Specification, and users of this Specification, as a condition of use, forever release ISAC from such liability and waive all claims against ISAC that may in any manner arise out of such liability. ISAC further disclaims all warranties, whether express, implied or statutory, and makes no assurances as to the accuracy or completeness of any information published in the Specification. -

Instant Messaging Video Converter, Iphone Converter Application
Web Browsing Mozilla Firefox The premier free, open-source browser. Tabs, pop-up blocking, themes, and extensions. Considered by many to be the world's best browser. Download Page Video Player, Torrents, Podcasting Miro Beautiful interface. Plays any video type (much more than quicktime). Subscribe to video RSS, download, and watch all in one. Torrent support. Search and download from YouTube and others. Download Page IM - Instant Messaging Adium Connect to multiple IM accounts simultaneously in a single app, including: AOL IM, MSN, and Jabber. Beautiful, themable interface. Download Page Video Converter, iPhone Converter Miro Video Converter Convert any type of video to mp4 or theora. Convert any video for use with iPhone, iPod, Android, etc. Very clean, easy to use interface. Download Page Application Launching Quicksilver Quicksilver lets you start applications (and do just about everything) with a few quick taps of your fingers. Warning: start using Quicksilver and you won't be able to imagine using a Mac without it. Download Page Email Mozilla Thunderbird Powerful spam filtering, solid interface, and all the features you need. Download Page Utilities The Unarchiver Uncompress RAR, 7zip, tar, and bz2 files on your Mac. Many new Mac users will be puzzled the first time they download a RAR file. Do them a favor and download UnRarX for them! Download Page DVD Ripping Handbrake DVD ripper and MPEG-4 / H.264 encoding. Very simple to use. Download Page RSS Vienna Very nice, native RSS client. Download Page RSSOwl Solid cross-platform RSS client. Download Page Peer-to-Peer Filesharing Cabos A simple, easy to use filesharing program. -
7Z Zip File Download How to Open 7Z Files
7z zip file download How to Open 7z Files. This article was written by Nicole Levine, MFA. Nicole Levine is a Technology Writer and Editor for wikiHow. She has more than 20 years of experience creating technical documentation and leading support teams at major web hosting and software companies. Nicole also holds an MFA in Creative Writing from Portland State University and teaches composition, fiction-writing, and zine-making at various institutions. There are 8 references cited in this article, which can be found at the bottom of the page. This article has been viewed 292,786 times. If you’ve come across a file that ends in “.7z”, you’re probably wondering why you can’t open it. These files, known as “7z” or “7-Zip files,” are archives of one or more files in one single compressed package. You’ll need to install an unzipping app to extract files from the archive. These apps are usually free for any operating system, including iOS and Android. Learn how to open 7z files with iZip on your mobile device, 7-Zip or WinZip on Windows, and The Unarchiver in Mac OS X. 7z zip file download. If you are looking for 7-Zip, you have come to the right place. We explain what 7-Zip is and point you to the official download. What is 7-Zip? 7-zip is a compression and extraction software similar to WinZIP and WinRAR, that can read from and write to .7z archive files (although it can open other compressed archives such as .zip and .rar, among others, even including limited access to the contents of .msi, or Microsoft Installer files, and .exe files, or executable files). -

Macwelt XL 1/2011
Sonderheft 01/11 · Dezember/Januar/Februar Mit DVD · 270 Seiten Mac OS-X Mit DVD 1000 Power-Tipps für Mac-OS X System installieren Daten übertragen Updates aufspielen Rechner einrichten DSL-Modem und Router Drucker einbinden Firewall konfigurieren Webmail, Safari, Chat, Skype Mediathek verwalten iTunes und iPod 150 Tools iPhoto und Vorschau Helfer für Mac-OS X Photoshop Elements Digitale Bilder 1000 Utilities iMovie & Garageband Schriften, Icons … Adressbuch und iCal iWork & Office 30 Videos Troubleshooting Tests, Apps u.v.m. Hardware prüfen Special iPhone Probleme beheben 100 Seiten E-Paper € 14,95 Dezember/Januar/Februar Schweiz: SFR 29,90 • Österreich € 16,45 BeNeLux € 17,20 Encore™ Thehigh-designiPadstand Vertrieb Deutschland Bezugsquellen und Distribution über www.macland.de www.just-mobile.eu ©2010 Just Mobile Ltd. Just Mobile und andere Just Mobile Marken sind Eigentum von Just Mobile Ltd. Alle anderen Marken sind Eigentum ihrer jeweiligen Rechteinhaber. Dekoration und Apple Produkte dienen nur der Illustration und sind nicht im Lieferumfang enthalten. Macwelt XL 01/2011 EDITORIAL 1000 Tipps und Tricks im XL-Format Die größte Tipp-Sammlung für den Mac, die es je gab Es ist noch gar nicht so lange her, da feierte Mac-OS X seinen zehnten Geburtstag. Am 13. September 2000 kam die erste (Beta-)Version heraus – seitdem hat sich viel getan. Mac-OS X ist sehr viel ausgereifter, einfacher zu bedienen und auch komplexer geworden. Macwelt feiert den Geburtstag mit diesem 270-seitigen Special, das die besten Tipps und How-Tos der Redaktion zum Mac-Betriebssystem vereint. Alle Tipps sind thema- tisch gegliedert und können so auch zum Nachschlagen verwendet werden. -

Leopard 10.5.8 Latest Software
Leopard 10.5.8 latest software Here is a list of the latest software that OS X Leopard supports. If you have software that can be added, tell me in the thread and where to find it, so we can expand the list. A lot of the software is not on the mac repository sites or other sites, some download links are broken and programs or any info about them will be extremely hard to find. I have a lot of free space on my HDD and I store all this software & can send a download link whenever someone needs something (ideal solution is if we can make a file server or make a new updated PCC store). I first used a list from “The Leopard Thread”, sorted everything better (sorry if something isn't in order) and added programs that weren't there before. Also, some of the programs weren't the latest version, so I found the latest, found a serial and added it in the folder. Please, if you want to add something on the list, check if it truly is the latest version for PPC! Also, if some program is put under incorrect label or there is a better version, please tell me in the thread, i want to make it as best as possible! Green Have latest version of the software and a working serial if it needs one Blue Have latest version of the software, but no serial Red Downloaded latest version of the software, but haven’t tested it Magenta I guess that this is the latest version, but can’t find a download link anywhere Black Not downloaded or checked if it works or latest version Bold Black - made a list like this before without checking too much if the programs were latest version & these weren't on the Leopard Thread list, so i copied them & need to check again 1. -

Manual Gta San Andreas Pc Zip File Mac
Manual Gta San Andreas Pc Zip File Mac GTA IV San Andreas is the free game mod for PC which enriches the gameplay of Grand Theft Auto IV Download.zip.rar mod files from GTA modding sites. Mod Loader is an ASI Plugin for Rockstar's Grand Theft Auto San Andreas that IPL and IDE files given to modloader NEED to be registered in *gta.dat* like. gta San Andreas PC Game Highly Compressed ( download free ) +Andreas+ PC+Game+. When following the steps in the official Games4TheWorld guide for Mac OSX I RAR file, so you will need to extract it first with an appropriate program (StuffIt Mafia II, GTA: Vice City, GTA: San Andreas, GTA IV & Episodes from Liberty City. Contents. 1: Windows PC Guide, 2: Mac OS X Guide Launch the setup file you just downloaded. Mac OS X Guide. Download the Android zip file from here: adb-fastboot-install Grand Theft Auto: San Andreas List Price: $6.99 Price: $4.99. review(s) for the gta san andreas crack serial keygen torrent Hero Iii 3 Patch 1 2 Fixed + To Play Online Pc Gh3. file 1581 kb/s Direct file Download 2410 kb/s. if you avoid searching for words such as: key, rapidshare cracked download,rar,zip, etc. Free full Downloads, movies, mac software, activators and for software. Manual Gta San Andreas Pc Zip File Mac Read/Download You need to extract this ISO using: 7-Zip (Windows) / The Unarchiver (Mac) » Play this on your Android You may click the link below to download your file If you are a moderator please see our troubleshooting guide. -
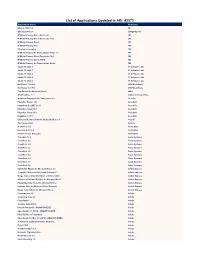
List of Applications Updated in ARL #2573
List of Applications Updated in ARL #2573 Application Name Publisher BIOS to UEFI 1.4 1E SyncBackPro 9.3 2BrightSparks M*Modal Fluency Direct Connector 3M M*Modal Fluency Direct Connector 7.85 3M M*Modal Fluency Direct 3M M*Modal Fluency Flex 3M Fluency for Imaging 3M M*Modal Fluency for Transcription Editor 7.6 3M M*Modal Fluency Direct Connector 10.0 3M M*Modal Fluency Direct CAPD 3M M*Modal Fluency for Transcription Editor 3M Studio 3T 2020.5 3T Software Labs Studio 3T 2020.7 3T Software Labs Studio 3T 2020.2 3T Software Labs Studio 3T 2020.8 3T Software Labs Studio 3T 2020.3 3T Software Labs MailRaider 3.69 Pro 45RPM software MailRaider 3.67 Pro 45RPM software Text Toolkit for Microsoft Excel 4Bits ASAP Utilities 7.7 A Must in Every Office Graphical Development Environment 3.2 Ab Initio PrizmDoc Server 13.8 AccuSoft ImageGear for .NET 24.11 AccuSoft PrizmDoc Client 13.8 AccuSoft PrizmDoc Client 13.9 AccuSoft ImagXpress 13.5 AccuSoft Universal Restore Bootable Media Builder 11.5 Acronis True Image 2020 Acronis ActivePerl 5.12 ActiveState Komodo Edit 12.0 ActiveState ActivePerl 5.26 Enterprise ActiveState TransMac 12.6 Acute Systems CrossFont 6.5 Acute Systems CrossFont 6.6 Acute Systems CrossFont 6.2 Acute Systems CrossFont 5.5 Acute Systems CrossFont 5.6 Acute Systems CrossFont 6.3 Acute Systems CrossFont 5.7 Acute Systems CrossFont 6.0 Acute Systems Split Table Wizard for Microsoft Excel 2.3 Add-in Express Template Phrases for Microsoft Outlook 4.7 Add-in Express Merge Tables Wizard for Microsoft Excel 2018 Add-in Express Advanced -

Juhtolv-Fontsamples
juhtolv-fontsamples Juhapekka Tolvanen Contents 1 Copyright and contact information 3 2 Introduction 5 3 How to use these PDFs 6 3.1 Decompressing ............................... 6 3.1.1 bzip2 and tar ............................. 8 3.1.2 7zip .................................. 11 3.2 Finding right PDFs ............................. 12 4 How to edit these PDFs 16 4.1 What each script do ............................ 16 4.2 About shell environment .......................... 19 4.3 How to ensure each PDF take just one page .............. 20 4.4 Programs used ................................ 20 4.5 Fonts used .................................. 23 4.5.1 Proportional Gothic ......................... 24 4.5.2 Proportional Mincho ........................ 26 4.5.3 Monospace (Gothic and Mincho) ................. 27 4.5.4 Handwriting ............................. 28 4.5.5 Fonts that can not be used .................... 29 5 Thanks 30 2 1 Copyright and contact information Author of all these files is Juhapekka Tolvanen. Author’s E-Mail address is: juhtolv (at) iki (dot) fi This publication has included material from these dictionary files in ac- cordance with the licence provisions of the Electronic Dictionaries Research Group: • kanjd212 • kanjidic • kanjidic2.xml • kradfile • kradfile2 See these WWW-pages: • http://www.edrdg.org/ • http://www.edrdg.org/edrdg/licence.html • http://www.csse.monash.edu.au/~jwb/edict.html • http://www.csse.monash.edu.au/~jwb/kanjidic_doc.html • http://www.csse.monash.edu.au/~jwb/kanjd212_doc.html • http://www.csse.monash.edu.au/~jwb/kanjidic2/ • http://www.csse.monash.edu.au/~jwb/kradinf.html 3 All generated PDF- and TEX-files of each kanji-character use exactly the same license as kanjidic2.xml uses; Name of that license is Creative Commons Attribution-ShareAlike Licence (V3.0). -

차세대 기록관리 모델 재설계 연구 개발 a Study on Conceptual Redesign of the Next Generation Record Management
발 간 등 록 번 호 연 구 결 과 보 고 서 - 2 11-1741050-000011-01 차세대 기록관리 모델 재설계 연구 개발 A Study on Conceptual Redesign of the next generation record management (2세부 연구과제) 주관수행 : 명지대학교 산학협력단 디지털아카이빙연구소 공동수행 : ㈜아카이브랩, 네모아이씨티(주), ㈜알엠소프트, ㈜에이더블유아이 국가기록원 제 출 문 국가기록원장 귀 하 이 보고서를 “차세대 기록관리모델 재설계 연구(명지대학교 디지털아카이빙연구소/이해영)” 과제의 연구결과보고서로 제출합니다. 2017. 12. 주관연구기관명 : 명지대학교 디지털아카이빙연구소 주관연구책임자 : 이해영 제 1세부과제명 : 차세대 전자기록관리의 개념설계와 정보 거버넌스형 기능·조직·법제 구축 방안 (제1세부연구기관/세부과제책임자): 명지대학교 디지털아카이빙연구소/김익한 제 2세부과제명 : 차세대 전자기록관리 프로세스와 시스템 설계 (제2세부연구기관/세부과제책임자): 네모아이씨티(주), (주)에이더블유아이, ㈜알엠소프트/오세라 제 3세부과제명 : 차세대 지능형 기록 서비스 모델 설계 (제3세부연구기관/세부과제책임자): ㈜아카이브랩/안대진 목 차 Ⅰ. 연구개발결과 요약문 (한글) 차세대 기록관리모델 재설계 연구 (영문) A Study on Conceptual Redesign of the next generation record management Ⅱ. 제2세부연구개발과제 연구결과 제1장 제2세부연구개발과제의 최종 연구개발 목표 ····················································· 1P 제2장 제2세부연구개발과제의 연구대상 및 방법 ·························································4P 제3장 제2세부연구개발과제의 최종 연구개발 결과 ··················································· 10P 제4장 제2세부연구개발과제의 연구결과 고찰 및 결론 ············································405P 제5장 제2세부연구개발과제의 연구성과 ···································································· 406P 제6장 기타 중요변경사항 ···························································································· 408P 제7장 참고문헌 ············································································································· 408P 제8장 첨부서류 목록 ···································································································· 408P 연구결과보고서 요약문 연구과제명 차세대 기록관리 -
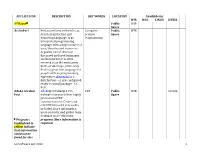
GC Software List 2012 1 APPLICATION DESCRIPTION KEY
APPLICATION DESCRIPTION KEY WORDS LOCATION Available for WIN MAC LINUX CITRIX 1st Bayer° Public WIN Space ActivePerl Perl, sometimes referred to as Computer Public WIN Practical Extraction and Science, Space Reporting Language, is an Programming interpreted programming language with a huge number of uses, libraries and resources. Arguably one of the most discussed and used languages on the internet, it is often referred to as the swiss army knife, or duct tape, of the web. Perl is a great first language for people with no programming experience. ActivePerl is a distribution - or pre-configured, ready-to-install package - of Perl. Adobe Acrobat Adobe® Acrobat® X Pro PDF Public WIN CITRIX Prof software lets you deliver highly Space professional PDF communications. Create and edit PDF files with rich media included, share information more securely, and gather team feedback more efficiently. ° Programs program. More information is highlighted in required. yellow indicate that information could not be found for this GC Software List 2012 1 APPLICATION DESCRIPTION FIELDS LOCATION WIN MAC LINUX CITRIX Adobe Creative Adobe® Creative Suite® 5.5 App development Public MAC Suite software keeps you ahead of the Space rapid proliferation of mobile devices. Develop rich interactive apps for Android™, BlackBerry®, and iOS. Design engaging browser content in HTML5, and create immersive digital magazines. Mobilize your creative vision with the suite edition that's right for you. Adobe Web Adobe® Creative Suite® 5.5 Website Public WIN Premium Web Premium software development Space provides everything you need to create and deliver standards- based websites with HTML5, jQuery Mobile, and CSS3 support. -

Certificate Installation Instruction
Introduction In the attachment you will find the ZIP file that you requested. Due to a limitation in Adobe Reader, the requested ZIP file is enclosed in another ZIP file which has file extension .NXP. To access the ZIP file, you can do the following: General method 1. Open the attachment by clicking the paperclip in the left margin. i Reader 9: Paperclip not shown? Click View Navigation Panels Attachments (See screenshot 1) i Reader 10: Paperclip not shown? Click View Show/Hide Navigation Panes Attachments (See screenshot 2) 2. You will find a .NXP file added to this PDF as an attachment. Right-click the file & click Save attachment. Store it at a permanently available (network) storage location. (See screenshot 3 for reader 9; see screenshot 4 for Reader 10.) With Adobe Reader before Adobe Reader X you can also drag and drop the attachment. 3. Open the location where you saved the attachment. 4. Rename the file. Change the extension from .NXP into .zip. 5. Now you can open the zip file which contains the requested ZIP file. Method if you have ZIP handling software If you have software which can handle ZIP files, like WinZip, 7Zip or WinRAR then you can follow this instruction. Instruction 1. Open the attachment by clicking the paperclip in the left margin. i Reader 9: Paperclip not shown? Click View Navigation Panels Attachments (See screenshot 1) i Reader 10: Paperclip not shown? Click View Show/Hide Navigation Panes Attachments (See screenshot 2) 2. You will find a .NXP file added to this PDF as an attachment.