SWG 11.8 SOCKS Proxy Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Poster: Introducing Massbrowser: a Censorship Circumvention System Run by the Masses
Poster: Introducing MassBrowser: A Censorship Circumvention System Run by the Masses Milad Nasr∗, Anonymous∗, and Amir Houmansadr University of Massachusetts Amherst fmilad,[email protected] ∗Equal contribution Abstract—We will present a new censorship circumvention sys- side the censorship regions, which relay the Internet traffic tem, currently being developed in our group. The new system of the censored users. This includes systems like Tor, VPNs, is called MassBrowser, and combines several techniques from Psiphon, etc. Unfortunately, such circumvention systems are state-of-the-art censorship studies to design a hard-to-block, easily blocked by the censors by enumerating their limited practical censorship circumvention system. MassBrowser is a set of proxy server IP addresses [14]. (2) Costly to operate: one-hop proxy system where the proxies are volunteer Internet To resist proxy blocking by the censors, recent circumven- users in the free world. The power of MassBrowser comes from tion systems have started to deploy the proxies on shared-IP the large number of volunteer proxies who frequently change platforms such as CDNs, App Engines, and Cloud Storage, their IP addresses as the volunteer users move to different a technique broadly referred to as domain fronting [3]. networks. To get a large number of volunteer proxies, we This mechanism, however, is prohibitively expensive [11] provide the volunteers the control over how their computers to operate for large scales of users. (3) Poor QoS: Proxy- are used by the censored users. Particularly, the volunteer based circumvention systems like Tor and it’s variants suffer users can decide what websites they will proxy for censored from low quality of service (e.g., high latencies and low users, and how much bandwidth they will allocate. -

Secure Shell Encrypt and Authenticate Remote Connections to Secure Applications and Data Across Open Networks
Product overview OpenText Secure Shell Encrypt and authenticate remote connections to secure applications and data across open networks Comprehensive Data security is an ongoing concern for organizations. Sensitive, security across proprietary information must always be protected—at rest and networks in motion. The challenge for organizations that provide access to applications and data on host systems is keeping the data Support for Secure Shell (SSH) secure while enabling access from remote computers and devices, whether in a local or wide-area network. ™ Strong SSL/TLS OpenText Secure Shell is a comprehensive security solution that safeguards network ® encryption traffic, including internet communication, between host systems (mainframes, UNIX ™ servers and X Window System applications) and remote PCs and web browsers. When ™ ™ ™ ™ Powerful Kerberos included with OpenText Exceed or OpenText HostExplorer , it provides Secure Shell 2 (SSH-2), Secure Sockets Layer (SSL), LIPKEY and Kerberos security mechanisms to ensure authentication security for communication types, such as X11, NFS, terminal emulation (Telnet), FTP support and any TCP/IP protocol. Secure Shell encrypts data to meet the toughest standards and requirements, such as FIPS 140-2. ™ Secure Shell is an add-on product in the OpenText Connectivity suite, which encrypts application traffic across networks. It helps organizations achieve security compliance by providing Secure Shell (SSH) capabilities. Moreover, seamless integration with other products in the Connectivity suite means zero disruption to the users who remotely access data and applications from web browsers and desktop computers. Secure Shell provides support for the following standards-based security protocols: Secure Shell (SSH)—A transport protocol that allows users to log on to other computers over a network, execute commands on remote machines and securely move files from one machine to another. -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Telnet Client 5.11 Ssh Support
TELNET CLIENT 5.11 SSH SUPPORT This document provides This document describes how to install and configure SSH support in Wavelink Telnet Client 5.11. information on the SSH support available in Telnet Client 5.11 OVERVIEW OF SSH SUPPORT Secure Shell (SSH) is a protocol developed for transmitting private information over the Internet. SSH OVERVIEW encrypts data that is transferred over the Telnet session. • Overview of SSH The Telnet Client supports SSH version 1 and 2 and will automatically select the most secure protocol Support that the SSH server supports. • Installing Windows SSH Support This document describes the following: • Configuring the host • Installing Windows SSH support utility profile for SSH • Configuring the host profile for SSH support support • Deploying Windows • Deploying Windows SSH support to the device through Avalanche or ActiveSync SSH Support • Revision History INSTALLING WINDOWS SSH SUPPORT Installing SSH support is a two-step process. First, install SSH support on the PC from which you will deploy Telnet. Once you install SSH support on the PC, use Avalanche or ActiveSync to deploy the utility to the device. To install SSH support on your PC: 1. Obtain the installation executable for SSH support. NOTE: To obtain the Wavelink SSH support utility install, go to http://www.wavelink.com/downloads/ files/sshagreement.aspx. 2. Install SSH support on the PC from which you will deploy the Telnet Client. CONFIGURING THE HOST PROFILE FOR SSH SUPPORT SSH support is configured from the Host Profiles window of the configuration utility. NOTE: SSH is only an active option if SSH support has been installed on the PC running the Telnet Client configuration utility. -
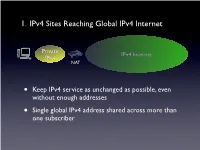
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3. -

Abstract Introduction Methodology
Kajetan Hinner (2000): Statistics of major IRC networks: methods and summary of user count. M/C: A Journal of Media and Culture 3(4). <originally: http://www.api-network.com/mc/0008/count.html> now: http://www.media-culture.org.au/0008/count.html - Actual figures and updates: www.hinner.com/ircstat/ Abstract The article explains a successful approach to monitor the major worldwide Internet Relay Chat (IRC) networks. It introduces a new research tool capable of producing detailed and accurate statistics of IRC network’s user count. Several obsolete methods are discussed before the still ongoing Socip.perl program is explained. Finally some IRC statistics are described, like development of user figures, their maximum count, IRC channel figures, etc. Introduction Internet Relay Chat (IRC) is a text-based service, where people can meet online and chat. All chat is organized in channels which a specific topic, like #usa or #linux. A user can be taking part in several channels when connected to an IRC network. For a long time the only IRC network has been EFnet (Eris-Free Network, named after its server eris.berkeley.edu), founded in 1990. The other three major IRC networks are Undernet (1993), DALnet (1994) and IRCnet, which split off EFnet in June 1996. All persons connecting to an IRC network at one time create that IRC network’s user space. People are constantly signing on and off, the total number of users ever been to a specific IRC network could be called social space of that IRC network. It is obvious, that the IRC network’s social space by far outnumbers its user space. -

Networking Telnet
IBM i Version 7.2 Networking Telnet IBM Note Before using this information and the product it supports, read the information in “Notices” on page 99. This edition applies to IBM i 7.2 (product number 5770-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. This document may contain references to Licensed Internal Code. Licensed Internal Code is Machine Code and is licensed to you under the terms of the IBM License Agreement for Machine Code. © Copyright International Business Machines Corporation 1998, 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Telnet................................................................................................................... 1 What's new for IBM i 7.2..............................................................................................................................1 PDF file for Telnet........................................................................................................................................ 1 Telnet scenarios...........................................................................................................................................2 Telnet scenario: Telnet server configuration.........................................................................................2 Telnet scenario: Cascaded Telnet -

In Computer Networks, A
Practical No.1 Date:- Title:- Installation of Proxy-Server Windows Server 2003 What is proxy server? In computer networks, a proxy server is a server (a computer system or an application program) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource, available from a different server. The proxy server evaluates the request according to its filtering rules. For example, it may filter traffic by IP address or protocol. If the request is validated by the filter, the proxy provides the resource by connecting to the relevant server and requesting the service on behalf of the client. A proxy server may optionally alter the client's request or the server's response, and sometimes it may serve the request wit hout contacting the specified server. In this case, it 'caches' responses from the remote server, and returns subsequent requests for the same content directly . Most proxies are a web proxy, allowing access to content on the World Wide Web. A proxy server has a large variety of potential purposes, including: To keep machines behind it anonymous (mainly for security).[1] To speed up access to resources (using caching). Web proxies are commonly used to cache web pages from a web server.[2] To apply access policy to network services or content, e.g. to block undesired sites. To log / audit usage, i.e. to provide company employee Internet usage reporting. To bypass security/ parental controls. To scan transmitted content for malware before delivery. -

Internet Protocol Suite
InternetInternet ProtocolProtocol SuiteSuite Srinidhi Varadarajan InternetInternet ProtocolProtocol Suite:Suite: TransportTransport • TCP: Transmission Control Protocol • Byte stream transfer • Reliable, connection-oriented service • Point-to-point (one-to-one) service only • UDP: User Datagram Protocol • Unreliable (“best effort”) datagram service • Point-to-point, multicast (one-to-many), and • broadcast (one-to-all) InternetInternet ProtocolProtocol Suite:Suite: NetworkNetwork z IP: Internet Protocol – Unreliable service – Performs routing – Supported by routing protocols, • e.g. RIP, IS-IS, • OSPF, IGP, and BGP z ICMP: Internet Control Message Protocol – Used by IP (primarily) to exchange error and control messages with other nodes z IGMP: Internet Group Management Protocol – Used for controlling multicast (one-to-many transmission) for UDP datagrams InternetInternet ProtocolProtocol Suite:Suite: DataData LinkLink z ARP: Address Resolution Protocol – Translates from an IP (network) address to a network interface (hardware) address, e.g. IP address-to-Ethernet address or IP address-to- FDDI address z RARP: Reverse Address Resolution Protocol – Translates from a network interface (hardware) address to an IP (network) address AddressAddress ResolutionResolution ProtocolProtocol (ARP)(ARP) ARP Query What is the Ethernet Address of 130.245.20.2 Ethernet ARP Response IP Source 0A:03:23:65:09:FB IP Destination IP: 130.245.20.1 IP: 130.245.20.2 Ethernet: 0A:03:21:60:09:FA Ethernet: 0A:03:23:65:09:FB z Maps IP addresses to Ethernet Addresses -

Threat Modeling and Circumvention of Internet Censorship by David Fifield
Threat modeling and circumvention of Internet censorship By David Fifield A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor J.D. Tygar, Chair Professor Deirdre Mulligan Professor Vern Paxson Fall 2017 1 Abstract Threat modeling and circumvention of Internet censorship by David Fifield Doctor of Philosophy in Computer Science University of California, Berkeley Professor J.D. Tygar, Chair Research on Internet censorship is hampered by poor models of censor behavior. Censor models guide the development of circumvention systems, so it is important to get them right. A censor model should be understood not just as a set of capabilities|such as the ability to monitor network traffic—but as a set of priorities constrained by resource limitations. My research addresses the twin themes of modeling and circumvention. With a grounding in empirical research, I build up an abstract model of the circumvention problem and examine how to adapt it to concrete censorship challenges. I describe the results of experiments on censors that probe their strengths and weaknesses; specifically, on the subject of active probing to discover proxy servers, and on delays in their reaction to changes in circumvention. I present two circumvention designs: domain fronting, which derives its resistance to blocking from the censor's reluctance to block other useful services; and Snowflake, based on quickly changing peer-to-peer proxy servers. I hope to change the perception that the circumvention problem is a cat-and-mouse game that affords only incremental and temporary advancements. -

The Internet Protocol, Version 4 (Ipv4)
Today’s Lecture I. IPv4 Overview The Internet Protocol, II. IP Fragmentation and Reassembly Version 4 (IPv4) III. IP and Routing IV. IPv4 Options Internet Protocols CSC / ECE 573 Fall, 2005 N.C. State University copyright 2005 Douglas S. Reeves 1 copyright 2005 Douglas S. Reeves 2 Internet Protocol v4 (RFC791) Functions • A universal intermediate layer • Routing IPv4 Overview • Fragmentation and reassembly copyright 2005 Douglas S. Reeves 3 copyright 2005 Douglas S. Reeves 4 “IP over Everything, Everything Over IP” IP = Basic Delivery Service • Everything over IP • IP over everything • Connectionless delivery simplifies router design – TCP, UDP – Dialup and operation – Appletalk – ISDN – Netbios • Unreliable, best-effort delivery. Packets may be… – SCSI – X.25 – ATM – Ethernet – lost (discarded) – X.25 – Wi-Fi – duplicated – SNA – FDDI – reordered – Sonet – ATM – Fibre Channel – Sonet – and/or corrupted – Frame Relay… – … – Remote Direct Memory Access – Ethernet • Even IP over IP! copyright 2005 Douglas S. Reeves 5 copyright 2005 Douglas S. Reeves 6 1 IPv4 Datagram Format IPv4 Header Contents 0 4 8 16 31 •Version (4 bits) header type of service • Functions version total length (in bytes) length (x4) prec | D T R C 0 •Header Length x4 (4) flags identification fragment offset (x8) 1. universal 0 DF MF s •Type of Service (8) e time-to-live (next) protocol t intermediate layer header checksum y b (hop count) identifier •Total Length (16) 0 2 2. routing source IP address •Identification (16) 3. fragmentation and destination IP address reassembly •Flags (3) s •Fragment Offset ×8 (13) e t 4. Options y IP options (if any) b •Time-to-Live (8) 0 4 ≤ •Protocol Identifier (8) s e t •Header Checksum (16) y b payload 5 •Source IP Address (32) 1 5 5 6 •Destination IP Address (32) ≤ •IP Options (≤ 320) copyright 2005 Douglas S. -

SOCKS Protocol Version 6
SOCKS Protocol Version 6 draft-olteanu-intarea-socks-6-08 Vladimir Olteanu IETF 106 What’s new ● DNS provided by SOCKS ● Options for Happy Eyeballs at the proxy Clients need DNS-like features ● A and AAAA – LD_PRELOAD for non-SOCKS-aware apps: gedaddrinfo() separate from connect() – Happy Eyeballs: need to do queries separately ● TXT – ESNI ● MX, Service Binding, etc. – <Insert future use case here> Providing DNS-like features ● Individual SOCKS options (removed in -08) – Have to keep up with use cases – Duplicate DNS functionality – Until -07: A, AAAA, PTR ● Having the client use DNS – Hard to convey policies: resolver IPs, plaintext / over TLS / over HTTPS etc., maybe credentials, etc. – Provide a DNS proxy Why not separate DNS from SOCKS? Client Proxy Server HTTP/SOCKS :1080 HTTP :80 DNS :53 Why not separate DNS from SOCKS? Client Proxy Server HTTP/SOCKS :1080 HTTP :80 DNS :53 WHICH TOR CIRCUIT? ● Need context for DNS query – Otherwise: privacy leaks, suboptimal CDN use DNS provided by SOCKS ● Clients make CONNECT request to 0.0.0.0:53 – Proxy needn’t provide a valid bind address ● Plaintext DNS over SOCKS (opt. over TLS) – TCP by default: SOCKS + UDP more cumbersome to use ● Implementation in Sixtysocks – Run separate DNS proxy locally – Translate 0.0.0.0:53 to 127.0.0.1:53 Happy Eyeballs ● RFC 8305: resolve and connect to a server using both IPv4 and IPv6, keep only one connection – Failover from IPv6 to IPv4 – Better responsiveness if one is faster ● Clients can implement Happy Eyeballs locally – Have DNS + CONNECT Happy Eyeballs: