Administration Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ETS4P4 Terminal Server
ETS4P4 Terminal Server Installation Guide Thank you for purchasing this Lantronix ETS Ethernet Terminal Server. As the newest addition to our successful Ethernet terminal server family, the ETS uses software for multiprotocol Ethernet connections that has over 5 years of real-world feedback and de- velopment behind it. Lantronix is constantly improving the capabilities of our prod- ucts, and we encourage you to take advantage of new features through our FREE software upgrades (available via ftp over the Internet or BBS.) Our Flash ROM products, including this ETS, provide the sim- plest means for upgrades and installation. I hope you find this manual easy to use, and thorough in its explanation of the power- ful features you can now access on your network. Brad Freeburg President Contents 1 Introduction Overview...........................................................................1-1 Configuration ................................................1-1 Software ..........................................................1-2 About the Manuals ..........................................................1-2 2 Installation Overview...........................................................................2-1 ETS Components..............................................................2-1 Installation ........................................................................2-2 Selecting a Location for the ETS ..................2-2 Connecting to the Ethernet...........................2-2 Connecting a Terminal..................................2-3 -

Watchdt User Guide Pitney Bowes1 Is Making This Document Available to You, Free of Charge, for Use with the Software, in Order to Make Your Experience More Convenient
P/I Enterprise Manager Version: 1.4 WatchDT User Guide Pitney Bowes1 is making this document available to you, free of charge, for use with the software, in order to make your experience more convenient. Every effort has been made to ensure the accuracy and usefulness of this document reflecting our experience. Product information may change after publication without notice. This document is being distributed on an "as is" basis and we make no representations or warranties, express or implied, with respect to its accuracy, reliability or completeness and the entire risk of its use shall be assumed by you. In no event shall we be liable to you or any other person, regardless of the cause, for the effectiveness or accuracy of this document or for any special, indirect, incidental or consequential damages arising from or occasioned by your use, even if advised of the possibility of such damages. All software described in this document is either our software and/or our licensed property. No license either expressed or implied is granted for the use of the software by providing this document and/or content. Under copyright law, neither this document nor the software may be copied, photocopied, reproduced, transmitted, or reduced to any electronic medium or machine-readable form, in whole or in part, without our prior written consent. We will continue to maintain this document and we welcome any clarifications or additional information regarding its content. Address comments concerning the content of this publication to: Pitney Bowes Building 600 6 Hercules Way Leavesden Watford WD25 7GS United Kingdom We may use or distribute the information supplied in any way we deem appropriate without incurring any obligation to the submitter of the information 1 Copyright © Pitney Bowes Software. -

ARTERIAL SIGNAL TIMING OPTIMIZATION USING PASSER II-87 T-.,--=-Ju---:-L Y 1 9~88__ ~:--- ___~ - MICROCOMPUTER USER's GU I DE 6
TECHNICAL REPORT ST ANDARD TITLE PAGE 1. Report No. 2. Govt"tnment Acces'lon No. 3. Rec,p,ent's Catalog No. FHWA/TX-88/467-1 ~4-. ~T~,tl~e-an~d~S~ub-ti~Ile-------------~-------------------------+·5.~Re-p-or-t~Da-Ie-------------------- ARTERIAL SIGNAL TIMING OPTIMIZATION USING PASSER II-87 t-.,--=-Ju---:-l_y_1_9~88__ ~:--- ___~ - MICROCOMPUTER USER'S GU I DE _ 6. Performing Organ,zalion Code 7. Author'.: B. Performing Organi zatian Report No. Edmond C.P. Chang, James C. Lei, and Carroll J. Messer Research Report 467-1 9. Perform,ng D'Qanl zatlon Name and Addre .. 10. Work Unit No. Texas Transportation Institute Texas A&M University System II. Contract or Grant No. College Station, Texas 77843-3135 Study No. 2-18-86-467 13. Type 01 Report and Pe"ad Covered ----------------------------~ 12. Sponsoring Agency Name ond Address September 1, 1985 State Department of Highways and Public Transportation Final July 15, 1988 Transportation Planning Division I P.O. Box 5051 14. Sponsoring Agency Code Austin, Texas 78763 15. Supplementary Notes Research Performed in Cooperation with U.S. DOT, FHWA. Research Study Title "Enhancement to PASSER II-84" 16. Abstract PASSER 11-87 microcomputer program version 1.0 has been developed and is available for public distribution. PASSER II can be used to assist transportation professionals to analyze (1) Isolated intersection timing evaluations, (2) Progression signal timing optimization, and (3) "Existing" timing evaluations. The system contains the updated microcomputer version of the PASSER II program, advanced analyses similar to and beyond those used in the 1985 Highway Capacity Manual (HCM), and the latest Artificial Intelligence technology and Expert Systems designs. -

Mastering EOS Release 1.0
Mastering EOS Release 1.0 Sean Fisk and Ira Woodring May 12, 2015 CONTENTS 1 Introduction 3 1.1 Physical Access (Keycards) ....................................... 3 1.2 Computer Access (Credentials) ..................................... 3 2 Rules and Procedures 5 2.1 Disk Space ................................................ 5 2.2 Copyrighted Material ........................................... 5 2.3 Food and Drink .............................................. 6 2.4 Overnight Parking ............................................ 6 2.5 Living in the Lab ............................................. 6 2.6 Malicious Activity ............................................ 6 2.7 Games .................................................. 6 3 Using the Command Line 7 3.1 Command-Line Basics .......................................... 7 3.2 Available Shells ............................................. 7 3.3 Interactive Shell Use ........................................... 10 3.4 Shell Scripting .............................................. 24 4 Remote Access (SSH/VNC) 27 4.1 Inter-EOS SSH .............................................. 27 4.2 Microsoft Windows ........................................... 28 4.3 Mac OS X ................................................ 36 4.4 GNU/Linux ................................................ 49 5 User-level Software Installation 65 5.1 The Standard Hierarchy ......................................... 65 5.2 Manual Installation ............................................ 66 5.3 Linuxbrew ............................................... -

Perle Winattach User Guide Part Number 5500141-10
Perle WinAttach User Guide Part number 5500141-10 All trademarks are the property of the respective manufactures of the products associated with them. 2 INTRODUCTION...................................................................................................................................5 SYSTEM REQUIREMENTS ................................................................................................................6 HARDWARE ...........................................................................................................................................6 SERIAL CABLING ...................................................................................................................................6 SYSTEM USAGE .....................................................................................................................................6 CPU ..................................................................................................................................................6 Memory .............................................................................................................................................6 Disk ...................................................................................................................................................6 INSTALLATION....................................................................................................................................7 CONFIGURATION AND STARTUP.............................................................................................................8 -
Tricks of the Internet Gurus
Ebook banner rotater for General Internet This banner was supplied by SAFE Audit Tricks of the Internet Gurus ● Introduction ❍ Overview ❍ Foreword ❍ About the Authors Part I - First Things First ● Chapter 1 - Getting Connected: The Guru's Options ● Chapter 2 - Access at All Costs ● Chapter 3 - Tricks of the Trade: Tools ● Chapter 4 - Where's the Complaint Department? Or, What to Do When Things Don't Work Part II - Everyday Guru Facilities ● Chapter 5 - E-Mail ● Chapter 6 - Faxing from the Internet ● Chapter 7 - FTP ● Chapter 8 - Telnet ● Chapter 9 - Usenet ● Chapter 10 - World Wide Web Part III - A Guru's Diversions ● Chapter 11 - Online Entertainment for the Internet Guru ● Chapter 12 - Listservs and Mailing Lists ● Chapter 13 - MBone: The Internet's Multimedia Backbone ● Chapter 14 - Community Computing http://docs.rinet.ru/ITricks/ (1 of 2) [4/18/1999 12:36:06 AM] Ebook banner rotater for General Internet Part IV - Finding Stuff: You Name It, a Guru Can Find It (and So Can You) ● Chapter 15 - Life with Archie ● Chapter 16 - Veronica ● Chapter 17 - Discussion Forums ● Chapter 18 - Gopher Part V - Tricks of the Professional Internet Gurus ● Chapter 19 - Internet in The Classroom: How Educators Use the Internet ● Chapter 20 - Business and Commerce ● Chapter 21 - Finding Information You Want ● Chapter 22 - Art on the Internet ● Appendix A - Uniform Resource Locators (URLs) ● Appendix B - Signature Files ● Appendix C - Standards and Where To Find Them http://docs.rinet.ru/ITricks/ (2 of 2) [4/18/1999 12:36:06 AM] Tricks of the Internet -
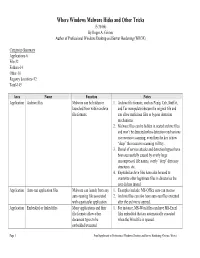
Potentially Malicious Windows Files
Where Windows Malware Hides and Other Tricks (5/30/06) By Roger A. Grimes Author of Professional Windows Desktop and Server Hardening (WROX) Categories Summary Applications-6 File-32 Folders-14 Other-10 Registry Locations-92 Total-145 Area Name Function Notes Application Archive files Malware can be hidden or 1. Archive file formats, such as Pkzip, Cab, Stuff-it, launched from within archive and Tar manipulate/obscure the original file and file formats. can allow malicious files to bypass detection mechanisms. 2. Malware files can be hidden in nested archive files, and won’t be detected unless detection mechanisms use recursive scanning; even then the key is how “deep” the recursive scanning will try. 3. Denial of service attacks and detection bypass have been successfully caused by overly large uncompressed file names, overly “deep” directory structures, etc. 4. Exploded archive files have also be used to overwrite other legitimate files in directories the user did not intend. Application Auto-run application files Malware can launch from any 1. Examples include: MS-Office auto-run macros auto-running file associated 2. Archive files can also have auto-run files executed with a particular application. after the archive is opened. Application Embedded or linked files Many applications and their 1. For instance, MS-Word files can have MS-Excel file formats allow other files embedded that are automatically executed document types to be when the Word file is opened. embedded/executed Page 1 Free Supplement to Professional Windows Desktop and Server Hardening (Grimes, Wrox) Area Name Function Notes Application Microsoft Word Embedded scripting can be 1. -

Fundamentals of Linux and Shell Programming” F Linux Ing”
“Fundamentals of Linux and Shell Programming” Prepared by Hirendra Deora Assistant Professor DEPARTMENT OF COMPUTER ENGINEERING VYAS COLLEGE OF ENGINEERING & TECHNOLOGY JODHPUR (RAJASTHAN) September 2013 Introduction & Overview Chapter 1 Introduction & Overview 1.1Operating System An operating system (OS) is a collection of software that manages computer hardware resources and provides common services for computer programs. The operating system is a vital component of the system software in a computer system. Application programs usually require an operating system to function. Fig 1.1 Operating System 1.2Types Of Operating System a. Real-time A real-time operating system is a multitasking operating system that aims at executing real-time applications. Real-time operating systems often use specialized scheduling algorithms so that they can achieve a deterministic nature of behavior. The main objective of real-time operating systems is their quick and predictable response to events. They have an event-driven or time- sharing design and often aspects of both. An event-driven system switches between tasks based on their priorities or external events while time-sharing operating systems switch tasks based on clock interrupts. b. Multi-user A multi-user operating system allows multiple users to access a computer system at the same time. Time-sharing systems and Internet servers can be classified as multi-user systems as they enable multiple-user access to a Hirendra Deora Page 1 Fundamental of Linux & Shell Programming computer through the sharing of time. Single-user operating systems have only one user but may allow multiple programs to run at the same time. c. Multi-tasking vs. -

WELSH: WINDOWS EASY LANGUAGE SHELL Lane Hill,Southwestern University Faculty Advisor: Dr
WELSH: WINDOWS EASY LANGUAGE SHELL Lane Hill,Southwestern University Faculty Advisor: Dr. Suzanne Buchele,Southwestern University ABSTRACT The Windows Easy Language Shell, WELSH, is a command-line shell for Windows that is an alternative to the standard DOS shell that comes with Windows. WELSH's goal is to provide an easy but powerful command-line shell for users, to help bridge the gap between similar Linux and Windows shell commands and to educate users on the benefits of using a command-line shell. INTRODUCTION A shell is a piece of software that allows a user to interact with a computer's operating system. There are two types of shells: graphical shells and command-line shells. Most users are more familiar with the graphical shell (such as Windows Explorer or the Gnome Desktop Environment), and it has been shown that these shells are easier to use for most users [2]. As a result, the concept of a command-line shell that operates mostly on text commands can be seen as "scary" or more advanced by users who do not know much about computers [3]. However, it is possible to get more tasks done in the time it takes to type a command in the command-line shell than in a graphical shell. Also, the use of a command line allows the user to focus on one task at a time, while still allowing commands to be processed in the background. Furthermore, the user can interact with the operating system at a deeper level of detail than what may be offered with the GUI [3,6]. -

Solaris PC Netlink 2.0 Administration Guide
Solaris™ PC NetLink 2.0 Administration Guide Sun Microsystems, Inc. 901 San Antonio Road Palo Alto, CA 94303-4900 U.S.A. 650-960-1300 Part No. 816-0266-10 March 2002, Revision A Send comments about this document to: [email protected] Copyright 2002 Sun Microsystems, Inc., 901 San Antonio Road, Palo Alto, CA 94303-4900 U.S.A. All rights reserved. This product or document is distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, AnswerBook2, docs.sun.com, Java, and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. PostScript is a trademark or registered trademark of Adobe Systems, Inc., which may be registered in certain jurisdictions. The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. -

Job Control Guide
Job Control Guide Job Control Guide Schrödinger Software Release 2015-2 Schrödinger Press Job Control Guide Copyright © 2015 Schrödinger, LLC. All rights reserved. While care has been taken in the preparation of this publication, Schrödinger assumes no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. Canvas, CombiGlide, ConfGen, Epik, Glide, Impact, Jaguar, Liaison, LigPrep, Maestro, Phase, Prime, PrimeX, QikProp, QikFit, QikSim, QSite, SiteMap, Strike, and WaterMap are trademarks of Schrödinger, LLC. Schrödinger, BioLuminate, and MacroModel are registered trademarks of Schrödinger, LLC. MCPRO is a trademark of William L. Jorgensen. DESMOND is a trademark of D. E. Shaw Research, LLC. Desmond is used with the permission of D. E. Shaw Research. All rights reserved. This publication may contain the trademarks of other companies. Schrödinger software includes software and libraries provided by third parties. For details of the copyrights, and terms and conditions associated with such included third party software, use your browser to open third_party_legal.html, which is in the docs folder of your Schrödinger software installation. This publication may refer to other third party software not included in or with Schrödinger software ("such other third party software"), and provide links to third party Web sites ("linked sites"). References to such other third party software or linked sites do not constitute an endorsement by Schrödinger, LLC or its affiliates. Use of such other third party software and linked sites may be subject to third party license agreements and fees. Schrödinger, LLC and its affiliates have no responsibility or liability, directly or indirectly, for such other third party software and linked sites, or for damage resulting from the use thereof. -

Pc-9801 System Disc Download VETUSWARE.COM
pc-9801 system disc download VETUSWARE.COM. the biggest free abandonware downloads collection in the universe. Che Guevara never used Windows. Software made by NEC. Set Localization Show only: EN JA All. dBase II User's Guide v2.3B. The dBASE II system for the NEC Advanced Personal Computer (APC) is distributed with a diskette containing the dBASE II programs and several sample applications and data bases. ThedBASEIIUser's Guide for the APC is a tutorial guide and reference manual for use with dBASE II. The first part ofthis guide is a tutorial. It explains the basic dBASE II commands and leads you through the processes ofdefining and manipUlating data bases. To run the sample application described in Appendix H of this manual, you must create the data base described in the tutorial. The appendices at the end of the manual are the reference materials. Appendix A through Appendix G summarize the concepts, commands, functions, and procedures presented in the tutorial section of the manual. Appendix H describes one sample application. Appendix I defines the function key assignments. Appendix J contains listings ofprograms created by dBASE II users like you. It will give you an idea of the kinds ofcommand files you can create using this system. N-88 BASIC(86) (DISK ver 6.2) This is for NEC PC-9801 series. N-88 BASIC(86) (DISK ver 6.3) This is for NEC PC-9801/9821 series. N-88 BASIC(86) (DOS interpreter compiler runtime ver6.0) N-88 BASIC(86) (DOS interpreter ver6.2) This is for NEC PC-9801 series.