Source Code Analysis, Management, and Visualization for PROLOG
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ASSESSING the MAINTAINABILITY of C++ SOURCE CODE by MARIUS SUNDBAKKEN a Thesis Submitted in Partial Fulfillment of the Requireme
ASSESSING THE MAINTAINABILITY OF C++ SOURCE CODE By MARIUS SUNDBAKKEN A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Science WASHINGTON STATE UNIVERSITY School of Electrical Engineering and Computer Science DECEMBER 2001 To the Faculty of Washington State University: The members of the Committee appointed to examine the thesis of MARIUS SUNDBAKKEN find it satisfactory and recommend that it be accepted. Chair ii ASSESSING THE MAINTAINABILITY OF C++ SOURCE CODE Abstract by Marius Sundbakken, M.S. Washington State University December 2001 Chair: David Bakken Maintenance refers to the modifications made to software systems after their first release. It is not possible to develop a significant software system that does not need maintenance because change, and hence maintenance, is an inherent characteristic of software systems. It has been estimated that it costs 80% more to maintain software than to develop it. Clearly, maintenance is the major expense in the lifetime of a software product. Predicting the maintenance effort is therefore vital for cost-effective design and development. Automated techniques that can quantify the maintainability of object- oriented designs would be very useful. Models based on metrics for object-oriented source code are necessary to assess software quality and predict engineering effort. This thesis will look at C++, one of the most widely used object-oriented programming languages in academia and industry today. Metrics based models that assess the maintainability of the source code using object-oriented software metrics are developed. iii Table of Contents 1. Introduction .................................................................................................................1 1.1. Maintenance and Maintainability....................................................................... -

Software Maintenance Maintenance Is Inevitable Types of Maintenance
SoftWindows 8/18/2003 Software Maintenance • Managing the processes of system change Reverse Engineering (Software Maintenance & Reengineering) © SERG Maintenance is Inevitable • The system requirements are likely to change while the system is being developed because the environment is changing. • When a system is installed in an environment it changes that environment and therefore changes the system requirements. Reverse Engineering (Software Maintenance & Reengineering) © SERG Types of Maintenance • Perfective maintenance – Changing a system to make it meet its requirements more effectively. • Adaptive maintenance – Changing a system to meet new requirements. • Corrective maintenance – Changing a system to correct deficiencies in the way meets its requirements. Reverse Engineering (Software Maintenance & Reengineering) © SERG Distributed Objects 1 SoftWindows 8/18/2003 Distribution of Maintenance Effort Corrective maintenance (17%) Adaptive maintenance Perfective (18%) maintenance (65%) Reverse Engineering (Software Maintenance & Reengineering) © SERG Evolving Systems • It is usually more expensive to add functionality after a system has been developed rather than design this into the system: – Maintenance staff are often inexperienced and unfamiliar with the application domain. – Programs may be poorly structured and hard to understand. – Changes may introduce new faults as the complexity of the system makes impact assessment difficult. – The structure may be degraded due to continual change. – There may be no documentation available to describe the program. Reverse Engineering (Software Maintenance & Reengineering) © SERG The Maintenance Process • Maintenance is triggered by change requests from customers or marketing requirements. • Changes are normally batched and implemented in a new release of the system. • Programs sometimes need to be repaired without a complete process iteration but this is dangerous as it leads to documentation and programs getting out of step. -

System Software Maintenance and Support 24X7
SYSTEM SOFTWARE MAINTENANCE AND SUPPORT SERVICES - PREMIUM These Premium System Software Maintenance and Support Service terms and conditions (“Terms and Conditions”) apply to any quote, order, order acknowledgment, and invoice, and any sale or provision of Premium System Software Maintenance and Support Services as defined herein provided to Customer by Viavi Solutions Inc. (“Viavi”), in addition to Viavi’s General Terms (“General Terms”) and/or Software License Terms, which are incorporated by reference herein and are either attached hereto, available at www.viavisolutions.com/terms or available upon request. k) Severity Level means classification of a problem determined by Viavi personnel 1. PURPOSE AND SCOPE based upon the Customer’s assessment of business impact. The three (3) Severity Levels that apply to the Services are as follows: These Terms and Conditions describe the Services that Viavi will provide to, and perform for, Customer. These Terms and Conditions apply to Services for standard Software, as 1) Problem Report – Critical means conditions that severely affect the defined herein, and are limited to the System configuration specified in a Statement of primary functionality of the System and because of the business impact to the Work (“SOW”) or other ordering document (i.e., a quote, order, order acknowledgment customer requires non-stop immediate corrective action, regardless of time of day or invoice) which contains a description of the System. All Services and Documentation or day of the week as viewed by a customer -

ALGORITHMS for ARTIFICIAL INTELLIGENCE in Apl2 By
MAY 1986 REVISED Nov 1986 TR 03·281 ALGORITHMS FOR ARTIFICIAL INTELLIGENCE IN APl2 By DR JAMES A· BROWN ED EUSEBI JANICE COOK lEO H GRONER INTERNATIONAL BUSINESS MACHINES CORPORATION GENERAL PRODUCTS DIVISION SANTA TERESA LABORATORY SAN JOSE~ CALIFORNIA ABSTRACT Many great advances in science and mathematics were preceded by notational improvements. While a g1yen algorithm can be implemented in any general purpose programming language, discovery of algorithms is heavily influenced by the notation used to Lnve s t Lq a t.e them. APL2 c o nce p t.ua Lly applies f unc t Lons in parallel to arrays of data and so is a natural notation in which to investigate' parallel algorithins. No c LaLm is made that APL2 1s an advance in notation that will precede a breakthrough in Artificial Intelligence but it 1s a new notation that allows a new view of the pr-obl.ems in AI and their solutions. APL2 can be used ill problems tractitionally programmed in LISP, and is a possible implementation language for PROLOG-like languages. This paper introduces a subset of the APL2 notation and explores how it can be applied to Artificial Intelligence. 111 CONTENTS Introduction. • • • • • • • • • • 1 Part 1: Artificial Intelligence. • • • 2 Part 2: Logic... · • 8 Part 3: APL2 ..... · 22 Part 4: The Implementations . · .40 Part 5: Going Beyond the Fundamentals .. • 61 Summary. .74 Conclus i ons , . · .75 Acknowledgements. • • 76 References. · 77 Appendix 1 : Implementations of the Algorithms.. 79 Appendix 2 : Glossary. • • • • • • • • • • • • • • • • 89 Appendix 3 : A Summary of Predicate Calculus. · 95 Appendix 4 : Tautologies. · 97 Appendix 5 : The DPY Function. -

Event Management for the Development of Multi-Agent Systems Using Logic Programming
Event Management for the Development of Multi-agent Systems using Logic Programming Natalia L. Weinbachy Alejandro J. Garc´ıa [email protected] [email protected] Laboratorio de Investigacio´n y Desarrollo en Inteligencia Artificial (LIDIA) Departamento de Ciencias e Ingenier´ıa de la Computacio´n Universidad Nacional del Sur Av. Alem 1253, (8000) Bah´ıa Blanca, Argentina Tel: (0291) 459-5135 / Fax: (0291) 459-5136 Abstract In this paper we present an extension of logic programming including events. We will first describe our proposal for specifying events in a logic program, and then we will present an implementation that uses an interesting communication mechanism called \signals & slots". The idea is to provide the application programmer with a mechanism for handling events. In our design we consider how to define an event, how to indicate the occurrence of an event, and how to associate an event with a service predicate or handler. Keywords: Event Management. Event-Driven Programming. Multi-agent Systems. Logic Programming. 1 Introduction An event represents the occurrence of something interesting for a process. Events are useful in those applications where pieces of code can be executed automatically when some condition is true. Therefore, event management is helpful to develop agents that react to certain occurrences produced by changes in the environment or caused by another agents. Our aim is to support event management in logic programming. An event can be emitted as a result of the execution of certain predicates, and will result in the execution of the service predicate or handler. For example, when programming a robot behaviour, an event could be associated with the discovery of an obstacle in its trajectory; when this event occurs (generated by some robot sensor), the robot might be able to react to it executing some kind of evasive algorithm. -
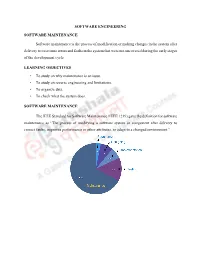
Software Engineering Software Maintenance
SOFTWARE ENGINEERING SOFTWARE MAINTENANCE Software maintenance is the process of modification or making changes in the system after delivery to overcome errors and faults in the system that were not uncovered during the early stages of the development cycle. LEARNING OBJECTIVES • To study on why maintenance is an issue. • To study on reverse engineering and limitations. • To organize data. • To check what the system does. SOFTWARE MAINTENANCE The IEEE Standard for Software Maintenance (IEEE 1219) gave the definition for software maintenance as “The process of modifying a software system or component after delivery to correct faults, improves performance or other attributes, or adapt to a changed environment.” Maintenance Principles 100 Hardware Development 60 Software 20 Maintenance Percent of total cost total of Percent 1995 2000 2010 The IEEE/EIA 12207 Standard defines maintenance as modification to code and associated documentation due to a problem or the need for improvement. Nature of Maintenance Modification requests are logged and tracked, the impact of proposed changes are determined, code and other software artifacts are modified, testing is conducted, and a new version of the software product is released. Maintainers can learn from the developer´s knowledge of the software. Need for Maintenance Maintenance must be performed in order to: • Correct faults. • Improve the design. • Implement enhancements. • Interface with other systems. • Adapt programs so that different hardware, software, system features, and telecommunications facilities can be used. • Migrate legacy software. • Retire software Tasks of a maintainer The maintainer does the following functions: • Maintain control over the software´s day-to-day functions. • Maintain control over software modification. -

Portability of Prolog Programs: Theory and Case-Studies
Portability of Prolog programs: theory and case-studies Jan Wielemaker1 and V´ıtorSantos Costa2 1 VU University Amsterdam, The Netherlands, [email protected] 2 DCC-FCUP & CRACS-INESC Porto LA Universidade do Porto, Portugal [email protected] Abstract. (Non-)portability of Prolog programs is widely considered as an important factor in the lack of acceptance of the language. Since 1995, the core of the language is covered by the ISO standard 13211-1. Since 2007, YAP and SWI-Prolog have established a basic compatibility framework. This article describes and evaluates this framework. The aim of the framework is running the same code on both systems rather than migrating an application. We show that today, the portability within the family of Edinburgh/Quintus derived Prolog implementations is good enough to allow for maintaining portable real-world applications. 1 Introduction Prolog is an old language with a long history, and its user community has seen a large number of implementations that evolved largely independently. This sit- uation is totally different from more recent languages, e.g, Java, Python or Perl. These language either have a single implementation (Python, Perl) or are con- trolled centrally (a language can only be called Java if it satisfies certain stan- dards [9]). The Prolog world knows dialects that are radically different, even with different syntax and different semantics (e.g., Visual Prolog [11]). Arguably, this is a handicap for the language because every publically available significant piece of code must be carefully examined for portability issues before it can be applied. As an anecdotal example, answers to questions on comp.lang.prolog typically include \on Prolog XYZ, this can be done using . -

A View of the Fifth Generation and Its Impact
AI Magazine Volume 3 Number 4 (1982) (© AAAI) Techniques and Methodology A View of the Fifth Generation And Its Impact David H. D. Warren SRI International Art$icial Intellagence Center Computer Scaence and Technology Davzsaon Menlo Park, Calafornia 94025 Abstract is partly secondhand. I apologise for any mistakes or misin- terpretations I may therefore have made. In October 1981, .Japan announced a national project to develop highly innovative computer systems for the 199Os, with the title “Fifth Genera- tion Computer Systems ” This paper is a personal view of that project, The fifth generation plan its significance, and reactions to it. In late 1978 the Japanese Ministry of International Trade THIS PAPER PRESENTS a personal view of the <Japanese and Industry (MITI) gave ETL the task of defining a project Fifth Generation Computer Systems project. My main to develop computer syst,ems for the 199Os, wit,h t,he title sources of information were the following: “Filth Generation.” The prqject should avoid competing with IBM head-on. In addition to the commercial aspects, The final proceedings of the Int,ernational Conference it should also enhance Japan’s international prestige. After on Fifth Generat,ion Computer Systems, held in Tokyo in October 1981, and the associated Fifth Generation various committees had deliberated, it was finally decided research reports distributed by the Japan Information to actually go ahead with a “Fifth Generation Computer Processing Development Center (JIPDEC); Systems” project in 1981. The project formally started in April, 1982. Presentations by Koichi Furukawa of Electrotechnical The general technical content of the plan seems to be Laboratory (ETL) at the Prolog Programming Environ- largely due to people at ETL and, in particular, to Kazuhiro ments Workshop, held in Linkoping, Sweden, in March 1982; Fuchi. -

Read Ms. Shaw's First Amended Complaint
Janet L. Goldstein Peter W. Chatfield THE MARTYN FIRM, PLLC PHILLIPS & COHEN LLP 1054 31st Street, NW 2000 Massachusetts Ave., NW Washington, D.C. 20007 Washington, D.C. 20036 Tel: (202) 965-3060 Tel: (202) 833-4567 Fax: (202) 965-3063 Fax: (202) 833-1815 Jonathan A. Willens (JW-9180) JONATHAN A. WILLENS LLC 217 Broadway, Suite 707 New York, New York 10007 Tel: (212) 619-3749 Fax: (800) 879-7938 Attorneys for qui tam plaintiff Ann-Marie Shaw UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF NEW YORK UNITED STATES OF AMERICA ) 06 CV 3552 (DLI) (SMG) ex rel. ANN-MARIE SHAW ) and ) AMENDED COMPLAINT ) FOR VIOLATIONS OF STATE OF CALIFORNIA ex rel.ANN-MARIE SHAW ) FEDERAL AND STATE DISTRICT OF COLUMBIA ex rel.ANN-MARIE SHAW ) FALSE CLAIMS ACTS STATE OF FLORIDA ex rel.ANN-MARIE SHAW ) STATE OF HAWAII ex rel.ANN-MARIE SHAW ) STATE OF ILLINOIS ex rel.ANN-MARIE SHAW ) COMMONWEALTH OF MASSACHUSETTS ) ex rel.ANN-MARIE SHAW ) STATE OF NEVADA ex rel.ANN-MARIE SHAW ) COMMONWEALTH OF VIRGINA ) ex rel.ANN-MARIE SHAW ) STATE & CITY OF NEW YORK ) ex rel.ANN-MARIE SHAW, ) ) JURY TRIAL DEMANDED Plaintiffs, ) ) FILED UNDER SEAL v. ) ) CA, INC., ) ) Defendant. ) _______________________________________________ ) Through her attorneys, plaintiff and qui tam relator Ann-Marie Shaw, for her Amended Complaint against Defendant CA, Inc. (“CA”), formerly known as Computer Associates International, Inc. or “Computer Associates,” alleges as follows: FACTS COMMON TO ALL COUNTS A. Introduction 1. This is a civil action to recover damages and civil penalties arising from false and/or fraudulent statements, records, and claims made and caused to be made by the Defendant CA and/or its agents and employees in violation of the Federal Civil False Claims Act, 31 U.S.C. -

CSC384: Intro to Artificial Intelligence Brief Introduction to Prolog
CSC384: Intro to Artificial Intelligence Brief Introduction to Prolog Part 1/2: Basic material Part 2/2 : More advanced material 1 Hojjat Ghaderi and Fahiem Bacchus, University of Toronto CSC384: Intro to Artificial Intelligence Resources Check the course website for several online tutorials and examples. There is also a comprehensive textbook: Prolog Programming for Artificial Intelligence by Ivan Bratko. 2 Hojjat Ghaderi and Fahiem Bacchus, University of Toronto What‟s Prolog? Prolog is a language that is useful for doing symbolic and logic-based computation. It‟s declarative: very different from imperative style programming like Java, C++, Python,… A program is partly like a database but much more powerful since we can also have general rules to infer new facts! A Prolog interpreter can follow these facts/rules and answer queries by sophisticated search. Ready for a quick ride? Buckle up! 3 Hojjat Ghaderi and Fahiem Bacchus, University of Toronto What‟s Prolog? Let‟s do a test drive! Here is a simple Prolog program saved in a file named family.pl male(albert). %a fact stating albert is a male male(edward). female(alice). %a fact stating alice is a female female(victoria). parent(albert,edward). %a fact: albert is parent of edward parent(victoria,edward). father(X,Y) :- %a rule: X is father of Y if X if a male parent of Y parent(X,Y), male(X). %body of above rule, can be on same line. mother(X,Y) :- parent(X,Y), female(X). %a similar rule for X being mother of Y A fact/rule (statement) ends with “.” and white space ignored read :- after rule head as “if”. -

An Architecture for Making Object-Oriented Systems Available from Prolog
An Architecture for Making Object-Oriented Systems Available from Prolog Jan Wielemaker and Anjo Anjewierden Social Science Informatics (SWI), University of Amsterdam, Roetersstraat 15, 1018 WB Amsterdam, The Netherlands, {jan,anjo}@swi.psy.uva.nl August 2, 2002 Abstract It is next to impossible to develop real-life applications in just pure Prolog. With XPCE [5] we realised a mechanism for integrating Prolog with an external object-oriented system that turns this OO system into a natural extension to Prolog. We describe the design and how it can be applied to other external OO systems. 1 Introduction A wealth of functionality is available in object-oriented systems and libraries. This paper addresses the issue of how such libraries can be made available in Prolog, in particular libraries for creating user interfaces. Almost any modern Prolog system can call routines in C and be called from C (or other impera- tive languages). Also, most systems provide ready-to-use libraries to handle network communication. These primitives are used to build bridges between Prolog and external libraries for (graphical) user- interfacing (GUIs), connecting to databases, embedding in (web-)servers, etc. Some, especially most GUI systems, are object-oriented (OO). The rest of this paper concentrates on GUIs, though the argu- ments apply to other systems too. GUIs consist of a large set of entities such as windows and controls that define a large number of operations. These operations often involve destructive state changes and the behaviour of GUI components normally involves handling spontaneous input in the form of events. OO techniques are very well suited to handle this complexity. -

Techniques for Software Maintenance 57 02 58
01 Techniques for Software Maintenance 57 02 58 03 59 04 60 Kostas Kontogiannis 05 61 Department of Electrical and Computer Engineering, National Technical University of Athens, 06 62 Athens, Greece 07 63 08 64 09 65 10 66 Abstract 11 Software maintenance constitutes a major phase of the software life cycle. Studies indicate that software 67 12 maintenance is responsible for a significant percentage of a system’s overall cost and effort. The software 68 13 engineering community has identified four major types of software maintenance, namely, corrective, 69 14 perfective, adaptive, and preventive maintenance. Software maintenance can be seen from two major points 70 15 of view. First, the classic view where software maintenance provides the necessary theories, techniques, 71 16 methodologies, and tools for keeping software systems operational once they have been deployed to their 72 17 operational environment. Most legacy systems subscribe to this view of software maintenance. The second 73 18 view is a more modern emerging view, where maintenance is an integral part of the software development 74 19 process and it should be applied from the early stages in the software life cycle. Regardless of the view by 75 which we consider software maintenance, the fact is that it is the driving force behind software evolution, a 20 76 very important aspect of a software system. This entry provides an in-depth discussion of software 21 77 Q1 maintenance techniques, methodologies, tools, and emerging trends. 22 78 23 79 24 80 25 INTRODUCTION type of software maintenance is referred to as Adaptive 81 26 82 Software Maintenance and refers to activities that aim to 27 83 Software maintenance is an integral part of the software modify models and artifacts of existing systems so that 28 84 life cycle and has been identified as an activity that affects these systems can be integrated with new systems or 29 85 in a major way the overall system cost and effort.