Routedetector: Sensor-Based Positioning System That Exploits Spatio-Temporal Regularity of Human Mobility
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Saitama Page 1/ 4
SAITAMA PAGE 1/ 4 PG-309 SAITAMA 10th Fl., Tokyo Kotsu Kaikan Bldg., 2-10-1, Yurakucho, Chiyoda-ku, Tokyo 100-0006 Tel. (03)3201-3331 Saitama Prefecture, pop. 6,938,000 located in the middle of the Apart from the mountainous northern region, and the Chichibu region, Kanto Plain area, is blessed with an abundance of nature. Visitors can most of the prefecture consists of level ground, and it has the same encounter beautiful scenery with clear spring waters and greenery. warm climate as the Central Tokyo. Access: To From Type of train Time required Fare(¥) Daily runs JR LEX “Narita Express” 1 hr. 2,940 23 Narita Airport JR Rapid “Airport Narita” 1 hr. 24 min. 1,280 16 Tokyo Monorail & JR Yamanote Line (change at Hamamatsu-cho Sta.) 28 min. 620 10–15/hr. Haneda Airport Keikyu Line & JR Yamanote Line 30 min. 560 Every 10 min. Tokyo St.a. (change at Shinagawa Sta.) JR Shinkansen “Nozomi” 2 hrs. 40 min. 14,720 29 Shin-Osaka Sta. JR Shinkansen “Hikari” 3 hrs. 13,750 93 Shin-Kobe Sta. JR Shinkansen “Hikari” 3 hrs. 15 min. 14,270 41 JR Shinkansen “Nozomi” 1 hr. 36 min. 11,340 29 Nagoya Sta. JR Shinkansen “Hikari” 1 hr. 50 min. 10,580 93 Keisei Railways “Skyliner” 56 min. 1,920 21 Ueno Sta. Keisei Railways LEX 1 hr. 16 min. 1,000 4–5/hr. Nippori Sta. Keisei Railways LEX 1 hr. 13 min. 1,000 4–5/hr. Narita Airport Omiya Sta. 2 hrs. ~ 2 hrs. 30 min. Saitama- Bus service “ON Liner” 2,750 18 Shintoshin Sta. -
SAITAMA, JAPAN Just North of Tokyo Nature, Koedo, Shopping and Events
Crayon Shin-chan There's plenty to see! © U/ F・S・A・A , Saitama Sightseeing Supporter SAITAMA, JAPAN Just North of Tokyo Nature, Koedo, shopping and events Chichibu & North Area West Area Central & East Area Crayon Shin-chan © U/ F・S・A・A , Saitama Sightseeing Supporter Tourism Division, Department of Industry and Labor, Saitama Prefecture ※Some of the facilities shown in this brochure may be temporarily closed, or their hours may be changed due to COVID-19. Please also note that events and festivals may either be delayed or canceled. Thank you for understanding. Visit Saitama Prefecture, where you can experience the past and present of Japan! The Chichibu Area and North Area are full of the appeal of richGUMMA nature, the West Area is where you can feel the atmosphere of Japan, and the Central Area and East Area are a fusion of city and nature. Experience Japanese history and culture in Saitama Prefecture, which is full of attractions! Fujioka IC Fujioka JCT y a w Tobu Nikko Line s e s pr x Joetsu Shinkansen/Hokuriku Shinkansen E 17 u k o Chichibu & North Area h o Chichibu Area and the North Area are full of excitement. T Refresh the soul in magnifi cent natural beauty of Chichibu and T o Hanyu IC b Nagatoro, and taste local dishes of the North Area that have Gyodashi u Ise Sta. s → FOR ak been developed independently. Tohoku Shinkansen 140 125 i L Kazo IC Narita Kumagaya Sta.Takasaki Line ine Airport Hanazono IC H a c Nagatoro Sta. h Kan-etsu ik o L Expressway y ine Kuki a w Shiraoka- l IC Mandarin orange i a Ogawamachi Sta. -

Presentation File(PDF 4.3
JR East Group Management Vision “Move Up” 2027 Investor Meeting July 4, 2018 Table of Contents 1. Changes in the business environment P3 2. JR East Group’s strengths P5 3. Basic Policies of “Move Up” 2027 P6 4. “Move Up” 2027 (1) Overview P8 (2) Making cities more comfortable P12 (3) Making regional areas more affluent P21 (4) Developing businesses for the world P23 (5) Numerical targets (FY2023), etc. P24 Environmental Group “Move Up” 2027 “Move Up” 2027 1. Changes in the business environment: Decreasing population change strengths Basic Policies Overview Urban cities Regional areas World Targets ■ After 2025, the population in Tokyo metropolitan area (Tokyo, Saitama, Chiba, Kanagawa) is expected to decrease gradually. ■ In Tohoku region (Aomori, Iwate, Miyagi, Akita, Yamagata, Fukushima), the population is expected to decrease by nearly 30% by 2040. (Population in 2015 = 100) 100% Tokyo metropolitan area 90% JR East service area National 80% By 2040 Tohoku region 70% 2015 2020 2025 2030 2035 2040 (Year) Decrease by nearly 30% Source: IPSS (National Institute of Population and Social Security Research) Population Projections by Prefecture (2018) 3 Environmental Group “Move Up” 2027 “Move Up” 2027 1. Changes in the business environment: Decreasing need for railway transportation change strengths Basic Policies Overview Urban cities Regional areas World Targets ■ After 2020, due to decreasing population, changes in the working style, development of internet society and practical application of autonomous driving technologies, the need for railway transportation is expected to decline. Since our railway business has large xed costs, we face a high risk of a drastic prot loss. -
Park Cube Shin Itabashi and Another Property)
March 13, 2018 To All Concerned Parties Issuer of Real Estate Investment Trust Securities 4-1, Nihonbashi 1-chome, Chuo-Ku, Tokyo 103-0027 Nippon Accommodations Fund Inc. Executive Director Takashi Ikeda (Code Number 3226) Investment Trust Management Company Mitsui Fudosan Accommodations Fund Management Co., Ltd. President and CEO Tateyuki Ikura Contact CFO and Director Satoshi Nohara (TEL. 03-3246-3677) Notification Concerning Acquisition of Domestic Real Estate Properties (Park Cube Shin Itabashi and another property) This is a notification that Mitsui Fudosan Accommodations Fund Management Co., Ltd., an investment trust management company, which has been commissioned by Nippon Accommodations Fund Inc. (“NAF”) to manage its assets, decided on the acquisition of real estate properties in Japan as shown below. 1. Reason for acquisition Based on the provisions for investments and policies on asset management provided in the Articles of Incorporation, the decision to acquire the following properties was made to ensure the steady growth of assets under management, and for the diversification and further enhancement of the investment portfolio. 2. Overview for acquisition Type of Planned acquisition Appraised value Name of property to be acquired property price (Note 3) (Note 4) to be acquired (thousands of yen) (thousands of yen) Property 1 Park Cube Shin Itabashi (Note 1) Real estate 1,700,000 1,740,000 Property 2 Park Cube Nishi Shinjuku (Note 2) Real estate 2,400,000 2,430,000 Total 4,100,000 4,170,000 (1) Date of conclusion of sale contract March 13, 2018 (2) Planned date of handover Property 1 March 29, 2018 Property 2 September 3, 2018 (3) Seller Property 1 Not disclosed (Note 5) Property 2 ITOCHU Property Development, Ltd. -
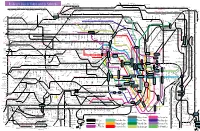
Railway Lines in Tokyo and Its Suburbs
Minami-Sakurai Hasuta Shin-Shiraoka Fujino-Ushijima Shimizu-Koen Railway Lines in Tokyo and its Suburbs Higashi-Omiya Shiraoka Kuki Kasukabe Kawama Nanakodai Yagisaki Obukuro Koshigaya Atago Noda-Shi Umesato Unga Edogawadai Hatsuisi Toyoshiki Fukiage Kita-Konosu JR Takasaki Line Okegawa Ageo Ichinowari Nanasato Iwatsuki Higashi-Iwatsuki Toyoharu Takesato Sengendai Kita-Koshigaya Minami-Koshigaya Owada Tobu-Noda Line Kita-Kogane Kashiwa Abiko Kumagaya Gyoda Konosu Kitamoto Kitaageo Tobu Nota Line Toro Omiya-Koen Tennodai Miyahara Higashi-Urawa Higashi-Kawaguchi JR Musashino Line Misato Minami-Nagareyama Urawa Shin-Koshigaya Minami- Kita- Saitama- JR Tohoku HonsenKita-Omiya Warabi Nishi-Kawaguchi Kawaguchi Kashiwa Kashiwa Hon-Kawagoe Matsudo Shin- Gamo Takenozuka Yoshikawa Shin-Misato Shintoshin Nishi-Arai Umejima Mabashi Minoridai Gotanno Yono Kita-Urawa Minami-Urawa Kita-Akabane Akabane Shinden Yatsuka Shin- Musashiranzan Higashi-Jujo Kita-Matsudo Shinrin-koenHigashi-MatsuyamaTakasaka Omiya Kashiwa Toride Yono Minami- Honmachi Yono- Matsubara-Danchi Shin-Itabashi Minami-FuruyaJR Kawagoe Line Musashishi-Urawa Kita-Toda Toda Toda-Koen Ukima-Funato Kosuge JR Saikyo Line Shimo Matsudo Kita-Sakado Kita- Shimura- Akabane-Iwabuchi Soka Masuo Ogawamachi Naka-Urawa Takashimadaira Shiden Matsudo- Yono Nishi-Takashimadaira Hasune Sanchome Itabashi-Honcho Oji Kita-senju Kami- Myogaku Sashiogi Nisshin Nishi-Urawa Daishimae Tobu Isesaki Line Kita-Ayase Kanamachi Hongo Shimura- Jujo Oji-Kamiya Oku Sakasai Yabashira Kawagoe Shingashi Fujimino Tsuruse -

Automatic Fare Collection System with Contactless IC (Smart) Card
Automatic Fare Collection System with Contactless IC (Smart) Card Masami TAKAHASHI, Satoshi KATAGATA, Jun ANDO, Shin-ya SHIROTO & Masahiro SAITO East Japan Railway Company 2-2-2 Yoyogi Shibuya-ku Tokyo JAPAN Tel:+81 3 5334 1243 Fax:+81 3 5334 1192 E-mail: [email protected] Summary East Japan Railway Company (JR East) will introduce new automatic fare collection (AFC) system with contactless IC card (CIC) as a new generation AFC system by the end of 2001. We have been investigating AFC system with CIC card from 1987 and as its technology reached a practical usage level, we have been developing and building the new AFC system from 1998. We have done a monitor test among 10,000 customers from April to July this year. As we received a lot of affirmative opinions from them, we are sure this system will be accepted by our customers and 6 million CIC cards (4 million Suica Passes and 2 million Suica IO cards) will be sold at the official debut. Thanks to this project, introduction and use of IT and other new technologies, we are moving forward steadily into a new cash less and ticket less era. Keywords: automatic fare collection system (AFC), contactless IC card (CIC) 1 1. Introduction East Japan Railway Company (JR East) is the largest railway company in Japan, which has approximately 7,500 km of railway network in the east part of Honshu island. Approximately 12,000 trains are operated and approximately 16 million customers use our trains every day. And more than 80% of our customers are in the Tokyo metropolitan area, in a radius of about 100 km from Tokyo station. -
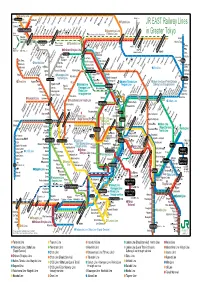
JR Railways Lines in Greater Tokyo
- 31 Joetsu- Line - Nikko- Line Shibukawa 渋川 Maebashi Kiryu Sano 32 - - Agatsuma Line Yagihara - Omata Tomita Ryomo Line oshima KomagataIsesaki Iwajuku Iwafune Tochigi JR EAST Railway Lines Kunisada Ashikaga Maebashi Yamamae Ohirashita Omoigawa Gumma-Soja 新前橋 Shim-Maebashi 17 - Utsunomiya Line Joetsu Kita- ( - ) in Greater Tokyo Shinkansen Ino KuraganoShimmachiJimboharaHonjoOkabeFukayaKagohara GyodaFukiage KonosuKonosuKitamotoOkegawaKita-AgeoAgeo Tohoku.Yamagata.Akita Shinkansen Tohoku Line KoganeiJichiidaiIshibashiSuzumenomiya Takasaki Miyahara tonyamachi Hitachi - akasaki Honjowaseda Joetsu. Nagano Hitachi-Taga 高崎 Kumagaya 18 Takasaki Line Oyama Utsunomiya Ujiie Yaita T 本庄早稲田 熊谷 Shinkansen Line Toro Kuki - Koga Nogi 小山 宇都宮 Nozaki Kuroiso Omika Omiya Shin- OkamotoHoshakuji Kataoka Nagano Higashi- Hasuda Shiraoka Higashi- 3 - Shiraoka Kurihashi Mamada 宝積寺 Tokai Shinkansen Shin-etsu Line Shonan-Shinjuku Line Kamasusaka Saitama- Karasuyama Line Nishi-NasunoNasushiobara那須塩原 Sawa odo Kawagoe Washinomiya Kita-Fujiokaansho Y orii Shintoshin T Y 川越 Omiya Suigun Line Katsuta Kodama Takezawa Nishi- Kita-Yono Yono Matsuhisa Kawagoe 大宮 Oku-Tama Gumma-Fujioka Kita-Urawa Yuki Mito 16 - Orihara Nisshin Yono-Hommachi Otabayashi Yuki Iwase Hachiko Line Ogawamachi Matoba Sashiogi Urawa Niihari Yamato Haguro Inada Shiromaru Minami-Yono Higashi- Tamado Fukuhara 水戸 Kairakuen Myokaku Kasahata Kawashima Shimodate (Extra) Hatonosu Minami-Furuya Naka-Urawa 33 Mito Line Nishi-Urawa 南浦和 Higashi-Urawa Higashi- Akatsuka Kori Ogose Musashi-Takahagi Musashi-Urawa Minami-Urawa Kawaguchi Kasama 武蔵浦和 Kawai Moro 20 Kawagoe Line Kita-Toda Warabi Shim-Misato Uchihara MitakeSawaiIkusabataFutamataoIshigamimaeHinatawadaMiyanohira 高麗川 Kita-Asaka Minami-oshigaya 友部 Ome - Toda Nishi-Kawaguchi K Komagawa Hachiko Line Yoshikawa Shishido Tomobe - Toda-Koen Kawaguchi - Misato - 14 Ome Line Higashi-Ome 4 Keihin-Tohoku- Line 23 Joban Line [Local Train]-Chiyoda Niiza - Ukimafunado 22 Iwama Kabe Higashi-Hanno 19 Saikyo- Line. -

Tokyo Metoropolitan Area Railway and Subway Route
NikkNikkō Line NikkNikkō Kuroiso Iwaki Tōbu-nikbu-nikkkō Niigata Area Shimo-imaichi ★ ★ Tōbu-utsunomiya Shin-fujiwara Shibata Shin-tochigi Utsunomiya Line Nasushiobara Mito Uetsu Line Network Map Hōshakuji Utsunomiya Line SAITAMA Tōhoku Shinkansen Utsunomiya Tomobe Ban-etsu- Hakushin Line Hakushin Line Niitsu WestW Line ■Areas where Suica・PASMO can be used RAILWAY Tochigi Oyama Shimodate Mito Line Niigata est Line Shinkansen Moriya Tsukuba Jōmō- Jōetsu Minakami Jōetsu Akagi Kuzū Kōgen ★ Shibukawa Line Shim-Maebashi Ryōmō Line Isesaki Sano Ryōmō Line Hokuriku Kurihashi Minami- ban Line Takasaki Kuragano Nagareyama Gosen Shinkansen(via Nagano) Takasaki Line Minami- Musashino Line NagareyamaNagareyama-- ō KukiKuki J Ōta Tōbu- TOBU Koshigaya ōōtakanomoritakanomori Line Echigo Jōetsu ShinkansenShinkansen Shin-etsu Line Line Annakaharuna Shin-etsu Line Nishi-koizumi Tatebayashi dōbutsu-kōen Kasukabe Shin-etsu Line Yokokawa Kumagaya Higashi-kHigashi-koizumioizumi Tsubamesanjō Higashi- Ogawamachi Sakado Shin- Daishimae Nishiarai Sanuki SanjSanjōō Urawa-Misono koshigaya Kashiwa Abiko Yahiko Minumadai- Line Uchijuku Ōmiya Akabane- Nippori-toneri Liner Ryūgasaki Nagaoka Kawagoeshi Hon-Kawagoe Higashi- iwabuchi Kumanomae shinsuikoen Toride Yorii Ogose Kawaguchi Machiya Kita-ayase TSUKUBA Yahiko Yoshida HachikHachikō Line Kawagoe Line Kawagoe ★ ★ NEW SHUTTLE Komagawa Keihin-Tōhoku Line Ōji Minami-Senju EXPRESS Shim- Shinkansen Ayase Kanamachi Matsudo ★ Seibu- Minami- Sendai Area Higashi-HanHigashi-Hannnō Nishi- Musashino Line Musashi-Urawa Akabane -

Construction of Ueno–Tokyo Line
Special Feature Construction of Ueno–Tokyo Line JR East Construction Department Introduction to support through services between the Utsunomiya, Takasaki, Joban, and Tokaido lines (Fig. 1). The Council East Japan Railway Company (JR East) has a wide-ranging for Transport Policy Report No. 18 published in January operations area from Kanto and Koshin’etsu to Tohoku. When 2000, targeted opening of the Ueno–Tokyo Line (A1) by JR East was established in 1987, traffic conditions on most 2015. In November 2007, the Minister of Transport gave sections of conventional (narrow-gauge) lines in the Tokyo permission to change the basic plan to a plan for laying area, including major sections of lines radiating from central new tracks between Tokyo Station and Ueno Station and Tokyo (Tokaido, Chuo, Joban, Sobu lines), the Yamanote then permission was given in March 2008 to change the Line, etc., had morning rush-hour congestion rates in excess railway facilities. Construction started in May 2008 and was of 200%. As a result, enhancing transportation capacity completed in about 6 years. The line opened on 14 March to alleviate congestion was a major issue. Furthermore, 2015, following 5–month training run. with subsequent diversification of values accompanying social changes, users’ railway needs went beyond merely Expected Effects alleviating congestion to shorter travel times and improved comfort while travelling, etc., so problems related to Alleviating congestion on Yamanote and Keihin-Tohoku improving transportation in the Tokyo area also diversified. In lines this context, JR East has taken various initiatives to improve The sections between Ueno Station and Okachimachi the quality of railway services. -

Integrated Report 2019 Tokyu Corporation
INTEGRATED 2019 REPORT INTEGRATED TOKYU CORPORATION Corporate Planning Office https://www.tokyu.co.jp/global/english/index.html This product is made of FSC® -certified and other controlled material. INTEGRATED REPORT 2019 Urban Development DNA That Has Flowed Through Our Veins Since the founding of the Tokyu Group, we have balanced our public and private natures with Tokyu Corporation traces its roots back to Den-en-toshi Company, the development of public transportation and residential areas as our two pillars. At the same time, which was started in 1918 under the leadership of Eiichi Shibusawa. we have strived to offer new life values ahead of our competitors as we continued to work on In 1922, Den-en-toshi Company’s railway division was separated to independently found developing sustainable communities. Meguro-Kamata Electric Railway Company. Going forward, we will always offer quality of living from new perspectives and create beautiful living In the approximately 100 years since our founding, we have been undertaking environments so that all people may find genuine happiness and express an individual lifestyle amid urban development as a private company together with local residents. a harmonious society overflowing with kindness and consideration. The characteristics of our urban development have been summarized below. Balancing the convenience of urban access with the living environment of the suburbs based on the garden city ideology founded by Englishman Ebenezer Howard Group Slogan Creating towns centered on stations, and urban -

SMOKING AREA MAP Akihabara
Ginza Line Iidabashi Station Area Akihabara Station Area Suehirocho Sta. Ueno Public Smoking Area Private Smoking Area Iidabashi Oedo Line Both cigarette and Only heating type Government Offices Bldg. Iidabashi Sta. 2 00 00 heating type are possible 00 is possible Taito 3 Akihabara Tsukudo Elem. Sch. 4 Iidabashi Station Area Akihabara Station Area paspa Iidabashi West Exit Café Veloce Akihabara Station East Exit store Namboku Line/ 36 B-3 52 B-5 Kanda Fire Station Legal Affairs Bureau Onabuta Building 1F 1-7-7 Fujimi Ohgaku Building 1F 2-19 Kanda-Sakumacho Yurakucho Line 70 Taito Branch Office Iidabashi Sta. paspa Iidabashi East Exit Café Veloce Akihabara Station Ekimae-Square store B-5 37 Create Building 1F 1-8-10 Iidabashi B-3 53 Tsk building 1F 104 Kanda-Matsunagacho Agebacho 34 Shohei Elem. Sch. 22 Tabacco Sale Free Smoking Area Toshida Tully's Coffee Akihabara UDX store 29 38 B-3 80 B-5 80 1-7-8 Iidabashi Akihabara UDX 1 4-14-1 Soto-Kanda 69 Tokyo Kusei Kaikan 4 Iidabashi Sta. Soto-Kanda Doutor Coffee Shop Iidabashi Tokyo Kusei-Kaikan store Tully's Coffee Sumitomo Fudosan Akihabara First Building Terrace store 102 Tozai Line 34 B-3 81 B-4 Akihabara Tokyo Kusei Kaikan 3-5-1 Iidabashi Sumitomo Fudosan Akihabara First Building Terrace 1F 1-9-1 Soto-Kanda Kaguragashi Iidabashi Sta. 44 90 Chuo-dori Ave. 87 Sta. 12 Doutor Coffee Shop Iidabashi-Fujimi store 8 35 2-3-10 Fujimi B-2 Kanda- 53 Café de Crie Iidabashi East Exit store Kanda Station Area B-3 Aioicho 69 Rock Belay Building 1F 4-7-1 Iidabashi KISUKE SMOKING SPACE 81 C-4 13 Café de Crie Iidabashi Ramla store 16 3-3-9 Kanda-Kajicho B-2 37 11 70 Iidabashi Central Plaza Ramla 1F 4-25 Iidabashi 35 Iidabashi Kaneko Tobacco Shop Smoking Area 7 10 17 C-4 Akihabara Sta. -

Keio Presso Inn Otemachi
KEIO PRESSO INN OTEMACHI TEL Check-in 3:00 p.m. 03-3241-0202 We may cancel your reservation, if you do not arrive at the indicated FAX 03-3241-0203 arrival time without any notice. URL www.presso-inn.com/otemachi/ Check-out 10:00 a.m. 4-4-1 Honkokucho, Nihombashi, Chuo-ku, Number of Guest Rooms 386 Tokyo 103-0021 Number Room Type Room Size Capacity of Rooms Single 363Rooms 12m2 1Person Double 11Rooms 18m2 1-2 Persons Twin 11Rooms 18m2 1-2 Persons (Example pictured above) Universal- Complimentary Breakfast 1Room 24m2 1-2 Persons Designed Twin 6:30a.m. 9:30a.m. Kanda Sta. JR Yamanote Line Kamakurabashi South Mizuho Shin-nihombashi Tozai Line Ueno Exit Sta. Chugoku Bank Ginza Line Exit2 Mitsukoshi-mae Sta. JR Chuo Line/ Muromachi Sobu Line Kanda 3 chome COREDO Muromachi Edo Dori MINI STOP Mitsukoshimae Hanzomon Line Bank of Japan, Otemachi Sta. Chiyoda Line Otemachi Sta. Mitsukoshi Marunouchi Line Head Office Shin- Nihombashi River jobanbashi Marunouchi Line Otemachi Kayabacho Jobanbashi Hanzomon Line Ginza Line ExitB1 Tokyo Hanzomon Mitsukoshi-mae Sta. Toei Asakusa Line Nihombashi Line Shutoko Circular LineNihombashi Sta. Chiyoda Line Kasumigaseki ExitA5 COREDO Nihombashi ExitB6 Tozai Line Roppongi Tozai Line Otemachi Sta. Eitai Dori Nihombashi Sta. Otemachi Sta. Sta. Nihombashi Hibiya Ginza Line Hibiya Line Toei Mita Line Marunouchi Gofukubashi Ginza Nihombashi Sotobori Dori Toei Mita Line Oazo Exit Takashimaya Tokaido Shinkansen Marunouchi Line JR Keiyo Line Tokyo Sta. Yaesu North Showa Dori Shinagawa Hamamatsucho Exit Chuo Dori Monorail Tokyo Marunouchi North Exit Daimaru Marunouchi Tokyo Yaesu Dori Building Sta.