Hacker Ghanoonmand
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Protokollsupport
Reference Guide WinRoute Pro 4.1 SE För version 4.1 Build 22 och sinare Tiny Software Inc. Contents Innehållsförteckning Läs mig först 2 Beskrivning av WinRoute 5 WinRoute sammanfattning...................................................................................... 6 Omfattande protokollsupport .................................................................................. 9 NAT-router............................................................................................................ 10 Introduktion i NAT .................................................................................... 11 Hur NAT fungerar...................................................................................... 12 WinRoutes struktur .................................................................................... 13 Att ställa in NAT på båda gränssnitten ...................................................... 15 Portmappning - paketbefordran ................................................................. 18 Portmappning för system med flera hem (flera IP-adresser)...................... 21 Multi-NAT ................................................................................................. 22 Gränssnittstabell......................................................................................... 24 VPN-support .............................................................................................. 24 Brandvägg med paketfilter.................................................................................... 25 Översikt -

J I Truste Ne Ork
Internet Security A Jumpstart for Systems Administrators and IT Managers Tim Speed Juanita Ellis Digital Press An imprint of Elsevier Science Amsterdam, Boston • London • New York o Oxford • Paris • San Diego San Francisco • Singapore • Sydney • Tokyo Digital Press is an imprint of Elsevier Science. Copyright © 2003, Elsevier Science (USA). All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Recognizing the importance of preserving what has been written, Elsevier Science prints its books on acid-free paper whenever possible. Library of Congress Cataloging-in-Publication Data ISBN 1-55558-298-2 British Library Cataloguing-in-Publication Data A catalogue record for this book is available from the British Library. The publisher offers special discounts on bulk orders of this book. For information, please contact: Manager of Special Sales Elsevier Science 200 Wheeler Road Burlington, MA 01803 Tel: 781-313-4700 Fax: 781-313-4882 For information on all Digital Press publications available, contact our World Wide Web home page at: http://www.digitalpress.com or http://www.bh.com/digitalpress 1098765432 1 Printed in the United States of America To Linda Speed~my split apart. -T.S. To my dad, Charles Ellis. -J.E. This Page Intentionally Left Blank Contents Foreword ix Acknowledgments xi Introduction xiii The Internet and Security I. I The -

Novell Bordermanager 3.9 Installation Guide Novdocx (ENU) 29 January 2007
Novell BorderManager 3.9 Installation Guide novdocx (ENU) 29 January 2007 January 29 (ENU) novdocx Novell BorderManager 3.9 www.novell.com INSTALLATION GUIDE April 05, 2007 novdocx (ENU) 29 January 2007 January 29 (ENU) novdocx Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. -

Novell Zenworks 6.5 Desktop Management Installation Guide May 19, 2006
Novell Confidential Manual (ENU) 21 December 2004 Novell ZENworks® Desktop Management 6.5 www.novell.com INSTALLATION GUIDE May 19, 2006 Novell Confidential Manual (ENU) 21 December 2004 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export, or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. Please refer to www.novell.com/info/exports/ for more information on exporting Novell software. -

Hacking for Dummies.Pdf
01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page v 01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page ii Hacking For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 Copyright © 2004 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permis- sion of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4447, e-mail: permcoordinator@ wiley.com. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. -

(12) United States Patent (10) Patent No.: US 8,943,201 B2 Larson Et Al
USOO8943 201B2 (12) United States Patent (10) Patent No.: US 8,943,201 B2 Larson et al. (45) Date of Patent: Jan. 27, 2015 (54) METHOD FORESTABLISHING ENCRYPTED (58) Field of Classification Search CHANNEL USPC .......................................... 709/225 229, 245 See application file for complete search history. (75) Inventors: Victor Larson, Fairfax, VA (US); Robert Dunham Short, Leesburg, VA (56) References Cited (US); Edmund Colby Munger, Crownsville, MD (US); Michael U.S. PATENT DOCUMENTS Williamson, South Riding, VA (US) 2,895,502 A 7/1959 Roper et al. 4.405,829 A 9, 1983 RiveSt (73) Assignee: VirnetX, Inc., Zephyr Cove, NV (US) (Continued) (*) Notice: Subject to any disclaimer, the term of this patent is extended or adjusted under 35 FOREIGN PATENT DOCUMENTS U.S.C. 154(b) by 0 days. DE 1992.4575 12/1999 EP O838.930 4f1988 (21) Appl. No.: 13/285,962 (Continued) (22) Filed: Oct. 31, 2011 OTHER PUBLICATIONS (65) Prior Publication Data Exhibit G, Opening Expert Report of Dr. Stuart Stubblebine Regard ing Invalidity of the 135,211, and 504 Patents. US 2012/OO4208.6 A1 Feb. 16, 2012 (Continued) Related U.S. Application Data Primary Examiner — Krisna Lim (60) Continuation of application No. 1 1/679,416, filed on (74) Attorney, Agent, or Firm — McDermott, Will & Emery Feb. 27, 2007, now Pat. No. 8,051,181, which is a continuation of application No. 10/702,486, filed on (57) ABSTRACT Nov. 7, 2003, now Pat. No. 7,188,180, which is a A technique is disclosed for establishing a secure communi cation link between a first computer and a second computer (Continued) over a computer network. -
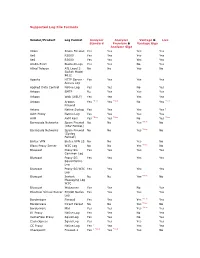
Supported Log File Formats
Supported Log File Formats Vendor/Product Log Format Analyzer Analyzer Vantage & Live Standard Premium & Vantage Giga Analyzer Giga 3Com 3Com Firewall Yes Yes Yes Yes 8e6 R2000 Yes Yes Yes Yes 8e6 R3000 Yes Yes Yes Yes Aladin Esafe Blocked Logs Yes Yes No Yes Allied Telesyn ATI Level 3 No No Yes No Switch Model 9812 Apache HTTP Server - Yes Yes Yes Yes Access Log Applied Data Control Native Log Yes Yes No Yes Arkoon SMTP No Yes Yes Yes Arkoon Web (WELF) Yes Yes Yes Yes Arkoon Arkoon Yes *New Yes *New No Yes *New Firewall Astaro Native Syslog Yes Yes Yes Yes 3 Avirt Proxy Native Log Yes Yes Yes Yes AVM AVM Ken! Yes *New Yes *New No Yes *New Barracuda Networks Spam Firewall No No Yes *New No (CSV Format) Barracuda Networks Spam Firewall No No Yes *New No (Syslog Format) Bintec VPN Bintec VPN 25 No No Yes No Bloxx Proxy Server W3C Log No No Yes *New No Bluecoat Proxy SG Yes Yes Yes Yes Common Log Bluecoat Proxy SG Yes Yes Yes Yes Squid Native Log Bluecoat Proxy SG W3C Yes Yes Yes Yes Log Bluecoat Instant No No Yes *New No Messaging Log W3C Bluecoat Websense Yes Yes No Yes BlueReef Virtual Server SQUID Native Yes Yes Yes Yes Log Borderware Firewall Yes Yes Yes *New Yes Borderware Direct Packet No No Yes *New No Borderware Mail Yes Yes Yes *New Yes BT Proxy Native Log Yes Yes No Yes CacheFlow Proxy Squid Log Yes Yes No Yes CacheXpress Squid Log Yes Yes Yes Yes CC Proxy Native Log Yes 1 Yes Yes Yes Checkpoint Firewall-1 Yes 1 *Mod Yes *Mod Yes No Checkpoint Firewall Yes 1 *Mod Yes *Mod Yes No Custom Checkpoint NG Yes 1 *Mod Yes *Mod Yes No CipherTrust -

Novell Bordermanager 3.9 Administration Guide Novdocx (ENU) 29 January 2007
Novell BorderManager 3.9 Administration Guide novdocx (ENU) 29 January 2007 January 29 (ENU) novdocx Novell BorderManager 3.9 www.novell.com ADMINISTRATION GUIDE April 5, 2007 novdocx (ENU) 29 January 2007 January 29 (ENU) novdocx Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. -

Log & Event Manager
Log & Event Manager Copyright © 1995-2012 SolarWinds Worldwide, LLC. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of SolarWinds. All right, title, and interest in and to the software and documentation are and shall remain the exclusive property of SolarWinds and its respective licensors. SOLARWINDS DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE, AND NONINFRINGEMENT. IN NO EVENT SHALL SOLARWINDS, ITS SUPPLIERS, NOR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF SOLARWINDS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. The SolarWinds, the SolarWinds & Design, ipMonitor, LANsurveyor, Orion, and other SolarWinds marks, identified on the SolarWinds website, as updated from SolarWinds from time to time and incorporated herein, are registered with the U.S. Patent and Trademark Office and may be registered or pending registration in other countries. All other SolarWinds trademarks may be common law marks or registered or pending registration in the United States or in other countries. All other trademarks or registered trademarks contained and/or mentioned herein are used for identification purposes only and may be trademarks or registered trademarks of their respective companies. Microsoft®, Windows®, and SQL Server® are registered trademarks of Microsoft Corporation in the United States and/or other countries. -

Novells Guide to Bordermanager Pdf, Epub, Ebook
NOVELLS GUIDE TO BORDERMANAGER PDF, EPUB, EBOOK J.D. Marymee, Sandy Stevens | 384 pages | 01 Jan 1998 | John Wiley & Sons Inc | 9780764545405 | English | Foster City, United States pdfFiller. On-line PDF form Filler, Editor, Type on PDF, Fill, Print, Email, Fax and Export All of the information presented in this book has been gathered from hands-on, real world experiences of the authors. A best-seller that once showed you how to reign in a panther can now show you …. Today, software engineers need to know not only how to program effectively but also how to …. You Will Learn Python 3! Zed Shaw has perfected the world's best system for learning Python …. If you think you should have access to this content, click the button to contact our support team. Contact us. To read the full version of this content please select one of the options below. You may be able to access this content by logging in via Shibboleth, Open Athens or with your Emerald account. To rent this content from Deepdyve, please click the button. Rent from Deepdyve. Join us on our journey Platform update page Visit emeraldpublishing. This retrieval method along with NetWare's fast file IO and other proprietary code made BorderManager's proxy engine one of the fastest in existence. This makes it possible for the customer to choose which NetWare or Linux kernel the services will run on. At this time Novell all but announced the end of development for the NetWare kernel numerous public and private statements that there is no bit future for NetWare and that Linux is the path to bit computing for OES. -

Novell Zenworks Desktop Management? 17 Automatisches Importieren Und Entfernen Von Arbeitsstationen
Novell Confidential Manual (DEU) 6 October 2004 Novell ZENworks® Desktop Management 6.5 www.novell.com INSTALLATIONSHANDBUCH 11.02.05 Novell Confidential Manual (DEU) 6 October 2004 Rechtliche Belange Novell, Inc., leistet keinerlei Gewähr bezüglich des Inhalts oder Gebrauchs dieses Handbuchs. Insbesondere werden keine ausdrücklichen oder stillschweigenden Gewährleistungen hinsichtlich der handelsüblichen Qualität oder Eignung für einen bestimmten Zweck übernommen. Novell, Inc. behält sich weiterhin das Recht vor, diese Dokumentation zu revidieren sowie ihren Inhalt jederzeit und ohne vorherige Ankündigung zu ändern. Novell, Inc. gibt ebenfalls keine Erklärungen oder Garantien in Bezug auf Softwareprodukte und schließt insbesondere jegliche ausdrückliche oder stillschweigende Garantie auf Marktgängigkeit oder Eignung für einen bestimmten Zweck aus. Außerdem behält sich Novell, Inc. das Recht vor, Novell-Software jederzeit ganz oder teilweise zu ändern, ohne dass für Novell, Inc. die Verpflichtung entsteht, Personen oder Organisationen von diesen Änderungen in Kenntnis zu setzen. Die Ausfuhr bzw. die Wiederausfuhr dieses Produkts ist nur im Rahmen gültiger Gesetze bzw. Richtlinien, darunter die US-Exportbestimmungen bzw. Gesetze Ihres Heimatlands, gestattet. Copyright © 2005 Novell, Inc. Alle Rechte vorbehalten. Ohne ausdrückliche schriftliche Genehmigung des Herausgebers darf kein Teil dieser Veröffentlichung reproduziert, fotokopiert, übertragen oder in einem Speichersystem verarbeitet werden. Novell, Inc., besitzt die Rechte auf geistiges Eigentum für die Technologie, die in dem in dieser Dokumentation beschriebenen Produkt enthalten ist. Diese Rechte auf geistiges Eigentum umfassen möglicherweise insbesondere ein oder mehrere Patente in den USA, die unter http://www.novell.com/ company/legal/patents aufgeführt sind (ohne darauf beschränkt zu sein). Diese Rechte umfassen möglicherweise außerdem ein oder mehrere andere Patente oder laufende Patentanträge in den USA und in anderen Ländern. -
Appendix a Practical Technical Implementation
Optimising Internet Bandwidth in Developing Country Higher Education Appendix A Practical technical implementation 1. Web caching A Web proxy server is a server on the local network that keeps copies of recently retrieved or often used Web pages, or parts of pages. When the next person retrieves these pages, they are served from the local proxy server instead of from the Internet. This results in faster Web access in most cases. Bandwidth usage can also be reduced. When a proxy server is implemented, the administrator should also be aware that some pages are not cacheable – for example, pages that are the output of server-side scripts. Loading of Web pages is also affected. Where previously the page would begin to load slowly, first showing some text and then displaying the graphics one by one, in a network with a proxy server, there could be a delay when nothing seems to happen, and then the page will load almost at once. The time it takes to load the whole page might take 10 seconds, whereas without a proxy server it may take 30 seconds, but unless this is explained to some impatient users, they may say the proxy server has made things slower. It is usually the task of the network administrator to deal with user perception like these. 1.1 Proxy server products Squid. Open source Squid is the de facto standard at universities. It is free, reliable, easy to use and can be enhanced with for example content filtering and advertisement blocking. Squid produces logs that can be analysed using software such as Sawmill (commercial) or Awstats, Webalizer (Open Source), both of which produce good graphical reports.