Security for Linux on System Z
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Today's Howtos Today's Howtos
Published on Tux Machines (http://www.tuxmachines.org) Home > content > today's howtos today's howtos By Roy Schestowitz Created 09/12/2020 - 5:46am Submitted by Roy Schestowitz on Wednesday 9th of December 2020 05:46:15 AM Filed under HowTos [1] How to Install Nginx with Google PageSpeed on Ubuntu 20.04 [2] Nginx is a free and open-source web server that powers many sites on the internet. It can be used as a reverse proxy and load balancer. It is known for its high-performance and stability. ngx_pagespeed is an open-source Nginx module that can be used to optimize your website performance. It is developed by Google and reduces the page load time and speed up the website response time. Install and Configure ZFS on FreeBSD ? Linux Hint [3] This article will demonstrate how to set up FreeBSD 12.0, the latest version, on Zettabyte File System, or ZFS. The method we?ll employ is going to use BSDinstall and consequently allocate all of the disks to host the FreeBSD system. How to Share Files Between Windows and Linux [4] File sharing is the action of sending a file or more from one computer to another. In theory, it?s a simple thing. The process is quite simple and straightforward if both of the computers are running the same operating system. When it?s different, things get a bit complicated. How To Install Firefox on CentOS 8 - idroot [5] In this tutorial, we will show you how to install Firefox on CentOS 8. For those of you who didn?t know, Firefox is the default web browser in a number of Linux distributions and CentOS is one of them. -

Troubleshooting Passwords
Troubleshooting Passwords The following procedures may be used to troubleshoot password problems: • Performing Password Recovery with an Existing Administrator, page 1 • Performing Password Recovery with No Existing Administrator, page 1 • Performing Password Recovery for the Linux Grapevine User Account, page 2 Performing Password Recovery with an Existing Administrator To perform password recovery for a user (administrator, installer or observer) where there exists at least one controller administrator (ROLE_ADMIN) user account, take the following steps: 1 Contact the existing administrator to set up a temporary password for the user that requires password recovery. Note The administrator can set up a temporary password by deleting the user's account and then recreating it with the lost password. The user can then log back into the controller to regain access and change the password once again to whatever he or she desires. 2 The user then needs to log into the controller with the temporary password and change the password. Note Passwords are changed in the controller GUI using the Change Password window. For information about changing passwords, see Chapter 4, Managing Users and Roles in the Cisco Application Policy Infrastructure Controller Enterprise Module Configuration Guide. Performing Password Recovery with No Existing Administrator The following procedure describes how to perform password recovery where there exists only one controller administrator (ROLE_ADMIN) user account and this account cannot be successfully logged into. Cisco Application Policy Infrastructure Controller Enterprise Module Troubleshooting Guide, Release 1.3.x 1 Troubleshooting Passwords Performing Password Recovery for the Linux Grapevine User Account Note We recommend that you create at least two administrator accounts for your deployment. -

Mcafee Foundstone Fsl Update
2017-JUL-27 FSL version 7.5.946 MCAFEE FOUNDSTONE FSL UPDATE To better protect your environment McAfee has created this FSL check update for the Foundstone Product Suite. The following is a detailed summary of the new and updated checks included with this release. NEW CHECKS 22152 - (JSA10802) Juniper Junos Insufficient Authentication Security Bypass Vulnerability Category: SSH Module -> NonIntrusive -> SSH Miscellaneous Risk Level: High CVE: CVE-2017-10601 Description A security-bypass vulnerability is present in some versions of Juniper Junos OS. Observation Juniper Junos OS is an operating system used in Juniper devices. A security-bypass vulnerability is present in some versions of Juniper Junos OS. The flaw lies in the Juniper Junos OS. Successful exploitation could allow a remote attacker to bypass authentication and gain access on the target system. 22161 - (JSA10791) Juniper Junos SRX Hardcoded Credentials Vulnerability Category: SSH Module -> NonIntrusive -> SSH Miscellaneous Risk Level: High CVE: CVE-2017-2343 Description An information disclosure vulnerability is present in some versions of Juniper Junos OS. Observation Juniper Junos OS is an operating system used in Juniper devices. An information disclosure vulnerability is present in some versions of Juniper Junos OS. The flaw lies in the UserFW services authentication API. Successful exploitation could allow an unauthenticated, remote attacker to gain access to sensitive information. 141631 - Red Hat Enterprise Linux RHSA-2017-1798 Update Is Not Installed Category: SSH Module -> NonIntrusive -> Red Hat Enterprise Linux Patches and Hotfixes Risk Level: High CVE: CVE-2017-7895 Description The scan detected that the host is missing the following update: RHSA-2017-1798 Observation Updates often remediate critical security problems that should be quickly addressed. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Taxonomy of Linux Kernel Vulnerability Solutions
Taxonomy of Linux Kernel Vulnerability Solutions Serguei A. Mokhov Marc-Andre´ Laverdiere` Djamel Benredjem Computer Security Laboratory Computer Security Laboratory Computer Security Laboratory Concordia Institute for Concordia Institute for Concordia Institute for Information Systems Engineering Information Systems Engineering Information Systems Engineering Concordia University, Concordia University, Concordia University, Montreal, Quebec, Canada Montreal, Quebec, Canada Montreal, Quebec, Canada Email: [email protected] Email: ma [email protected] Email: d [email protected] Abstract—This paper presents the results of a case study on C programs in general, as well as statistics on their relative software vulnerability solutions in the Linux kernel. Our major importance. We also introduce a new methodology to track contribution is the introduction of a classification of methods used the patch solving a security issue based only on the contents to solve vulnerabilities. Our research shows that precondition validation, error handling, and redesign are the most used of the security advisory. methods in solving vulnerabilities in the Linux kernel. This The paper is organized as follows: we examine previous contribution is accompanied with statistics on the occurrence work that was done regarding Linux and C security in of the different types of vulnerabilities and their solutions that Section II, followed by a description of the methodology we observed during our case study, combined with example used in order to obtain the solutions to the vulnerabilities in source code patches. We also combine our findings with existing programming guidelines to create the first security-oriented Section III. Afterwards, in Section IV, we show our results, coding guidelines for the Linux kernel. -

Have You Driven an Selinux Lately? an Update on the Security Enhanced Linux Project
Have You Driven an SELinux Lately? An Update on the Security Enhanced Linux Project James Morris Red Hat Asia Pacific Pte Ltd [email protected] Abstract All security-relevant accesses between subjects and ob- jects are controlled according to a dynamically loaded Security Enhanced Linux (SELinux) [18] has evolved mandatory security policy. Clean separation of mecha- rapidly over the last few years, with many enhancements nism and policy provides considerable flexibility in the made to both its core technology and higher-level tools. implementation of security goals for the system, while fine granularity of control ensures complete mediation. Following integration into several Linux distributions, SELinux has become the first widely used Mandatory An arbitrary number of different security models may be Access Control (MAC) scheme. It has helped Linux to composed (or “stacked”) by SELinux, with their com- receive the highest security certification likely possible bined effect being fully analyzable under a unified pol- for a mainstream off the shelf operating system. icy scheme. SELinux has also proven its worth for general purpose Currently, the default SELinux implementation com- use in mitigating several serious security flaws. poses the following security models: Type Enforcement (TE) [7], Role Based Access Control (RBAC) [12], While SELinux has a reputation for being difficult to Muilti-level Security (MLS) [29], and Identity Based use, recent developments have helped significantly in Access Control (IBAC). These complement the standard this area, and user adoption is advancing rapidly. Linux Discretionary Access Control (DAC) scheme. This paper provides an informal update on the project, With these models, SELinux provides comprehensive discussing key developments and challenges, with the mandatory enforcement of least privilege, confidential- aim of helping people to better understand current ity, and integrity. -

Pluggable Authentication Modules
Who this book is written for This book is for experienced system administrators and developers working with multiple Linux/UNIX servers or with both UNIX and Pluggable Authentication Windows servers. It assumes a good level of admin knowledge, and that developers are competent in C development on UNIX-based systems. Pluggable Authentication Modules PAM (Pluggable Authentication Modules) is a modular and flexible authentication management layer that sits between Linux applications and the native underlying authentication system. The PAM framework is widely used by most Linux distributions for authentication purposes. Modules Originating from Solaris 2.6 ten years ago, PAM is used today by most proprietary and free UNIX operating systems including GNU/Linux, FreeBSD, and Solaris, following both the design concept and the practical details. PAM is thus a unifying technology for authentication mechanisms in UNIX. This book provides a practical approach to UNIX/Linux authentication. The design principles are thoroughly explained, then illustrated through the examination of popular modules. It is intended as a one-stop introduction and reference to PAM. What you will learn from this book From Technologies to Solutions • Install, compile, and configure Linux-PAM on your system • Download and compile third-party modules • Understand the PAM framework and how it works • Learn to work with PAM’s management groups and control fl ags • Test and debug your PAM confi guration Pluggable Authentication Modules • Install and configure the pamtester utility -
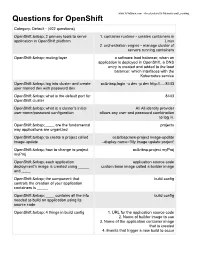
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -

Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car
2015-01-0224 Published 04/14/2015 Copyright © 2015 SAE International doi:10.4271/2015-01-0224 saepcelec.saejournals.org Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car Patrick Shelly Mentor Graphics Corp. ABSTRACT With the dramatic mismatch between handheld consumer devices and automobiles, both in terms of product lifespan and the speed at which new features (or versions) are released, vehicle OEMs are faced with a perplexing dilemma. If the connected car is to succeed there has to be a secure and accessible method to update the software in a vehicle's infotainment system - as well as a real or perceived way to graft in new software content. The challenge has become even more evident as the industry transitions from simple analog audio systems which have traditionally served up broadcast content to a new world in which configurable and interactive Internet- based content rules the day. This paper explores the options available for updating and extending the software capability of a vehicle's infotainment system while addressing the lifecycle mismatch between automobiles and consumer mobile devices. Implications to the design and cost of factory installed equipment will be discussed, as will expectations around the appeal of these various strategies to specific target demographics. CITATION: Shelly, P., "Addressing Challenges in Automotive Connectivity: Mobile Devices, Technologies, and the Connected Car," SAE Int. J. Passeng. Cars – Electron. Electr. Syst. 8(1):2015, doi:10.4271/2015-01-0224. INTRODUCTION be carefully taken into account. The use of app stores is expected to grow significantly in the coming years as automotive OEMs begin to Contemporary vehicle infotainment systems face an interesting explore apps not only on IVI systems, but on other components of the challenge. -

Linux for Zseries: Device Drivers and Installation Commands (March 4, 2002) Summary of Changes
Linux for zSeries Device Drivers and Installation Commands (March 4, 2002) Linux Kernel 2.4 LNUX-1103-07 Linux for zSeries Device Drivers and Installation Commands (March 4, 2002) Linux Kernel 2.4 LNUX-1103-07 Note Before using this document, be sure to read the information in “Notices” on page 207. Eighth Edition – (March 2002) This edition applies to the Linux for zSeries kernel 2.4 patch (made in September 2001) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Summary of changes .........v Chapter 5. Linux for zSeries Console || Edition 8 changes.............v device drivers............27 Edition 7 changes.............v Console features .............28 Edition 6 changes ............vi Console kernel parameter syntax .......28 Edition 5 changes ............vi Console kernel examples ..........28 Edition 4 changes ............vi Usingtheconsole............28 Edition 3 changes ............vii Console – Use of VInput ..........30 Edition 2 changes ............vii Console limitations ............31 About this book ...........ix Chapter 6. Channel attached tape How this book is organized .........ix device driver ............33 Who should read this book .........ix Tapedriverfeatures...........33 Assumptions..............ix Tape character device front-end........34 Tape block -

FLOSS Final Report – Part 3 Free/Libre Open Source Software: Survey and Study
FLOSS Final Report – Part 3 Free/Libre Open Source Software: Survey and Study Basics of Open Source Software Markets and Business Models Berlin, July 2002 3 BERLECON RESEARCH GmbH Oranienburger Str. 32 10117 Berlin Tel.: +49 30 285296-0 Fax: +49 30 285296-29 Web: http://www.berlecon.de Email: [email protected] Acknowledgements: This work was prepared by Dorit Spiller and Thorsten Wichmann from Berlecon Research. It is part of the final report for the project „FLOSS – Free/Libre Open Source Software: Survey and Study“, which was financed under the European Com- mission‘s IST programme, key action 4 as accompanying measure (IST-2000-4.1.1). Disclaimer: The views expressed in this report are those of the authors and do not necessarily re- flect those of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use that might be made of the following information. Nothing in this report implies or expresses a warranty of any kind. Results from this report should only be used as guidelines as part of an overall strategy. For detailed ad- vice on corporate planning, business processes and management, technology integra- tion and legal or tax issues, the services of a professional should be obtained. Names and trademarks mentioned in the report are the property of their respective owners. © 2002 by Berlecon Research GmbH. 4 V 1.1 - 020905 © 2002 by Berlecon Research GmbH. 5 Table of contents 1 Introduction....................................................................................................... 9 2 Software and the Open Source phenomenon.................................................... 11 2.1 The Open Source phenomenon .................................................................