Implement HTTP/HTTPS Transparent Proxy with Safe Content Solution
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

9 Caching Proxy Server
webXaccelerator: Owner's Guide by Luis Soltero, Ph.D., MCS Revision 1.06 February 10, 2010 (v1.2.3.10-RELEASE) Copyright © 2010 Global Marine Networks, LLC Table of Contents 1 Quick Start..............................................................................................................................................5 2 Introduction.............................................................................................................................................8 3 Initial Installation and Configuration......................................................................................................9 3.1 Connections.....................................................................................................................................9 3.2 Power-up..........................................................................................................................................9 3.3 Power-down...................................................................................................................................10 3.4 Web Administrator........................................................................................................................10 3.5 LAN Setup.....................................................................................................................................10 3.6 WAN Setup....................................................................................................................................11 3.7 WAN2 (Backup WAN) Setup........................................................................................................13 -

Configuracion De Un Servidor Proxy Para Filtrado De Contenidos Web En Ubuntu Linux
Configuracion de un Servidor Proxy para Filtrado de Contenidos Web en Ubuntu Linux ¿Qué es un Proxy? «Proxy» tiene un significado muy general y al mismo tiempo ambiguo, sinónimo del concepto de «Intermediario». Se suele traducir como delegado o apoderado. Un Servidor Intermediario (Proxy) se define como una computadora o dispositivo que ofrece un servicio de red que consiste en permitir a los clientes realizar conexiones de red indirectas hacia otros servicios de red. Durante el proceso ocurre lo siguiente: -Cliente se conecta hacia un Servidor Intermediario (Proxy). -Cliente solicita una conexión, fichero u otro recurso disponible en un servidor distinto. -Servidor Intermediario (Proxy) proporciona el recurso ya sea conectándose hacia el servidor especificado o sirviendo éste desde un caché. -En algunos casos el Servidor Intermediario (Proxy) puede alterar la solicitud del cliente o bien la respuesta del servidor para diversos propósitos. Los Servidores Intermediarios (Proxies) generalmente se hacen trabajar simultáneamente como muro cortafuegos operando en el Nivel de Red, actuando como filtro de paquetes, como en el caso de IPTABLES, o bien operando en el Nivel de Aplicación, controlando diversos servicios, como es el caso de TCP Wrapper. Dependiendo del contexto, el muro cortafuegos también se conoce como BPD o Border Protection Device o simplemente filtro de paquetes. Tipos de Proxy ● Proxy de web / Proxy cache de web ● Proxies transparentes ● Reverse Proxy ● Proxy NAT (Network Address Translation) / Enmascaramiento ● Proxy Abierto ¿Que es Squid? Squid es un programa de software libre que implementa un servidor proxy y un demonio para caché de páginas web. Está especialmente diseñado para ejecutarse bajo entornos tipo Unix. -

Securing Debian Manual
Securing Debian Manual Javier Fernández-Sanguino Peña <[email protected]> ‘Authors’ on this page Version: 3.13, Sun, 30 Jan 2011 19:58:16 +0000 Abstract This document describes security in the Debian project and in the Debian operating system. Starting with the process of securing and hardening the default Debian GNU/Linux distribu- tion installation, it also covers some of the common tasks to set up a secure network environ- ment using Debian GNU/Linux, gives additional information on the security tools available and talks about how security is enforced in Debian by the security and audit team. Copyright Notice Copyright © 2002-2007 Javier Fernández-Sanguino Peña Copyright © 2001 Alexander Reelsen, Javier Fernández-Sanguino Peña Copyright © 2000 Alexander Reelsen Some sections are copyright © their respective authors, for details please refer to ‘Credits and thanks!’ on page 28. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU General Public License, Version 2 (http://www.gnu.org/licenses/ old-licenses/gpl-2.0.html) or any later version (http://www.gnu.org/copyleft/ gpl.html) published by the Free Software Foundation. It is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY. Permission is granted to make and distribute verbatim copies of this document provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this document under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. -

Post-Hearing Comments on Exemption to Prohibition On
1 UNITED STATES COPYRIGHT OFFICE Rulemaking on Exemptions from Prohibition on Circumvention of Technological Measures that Control Access to Copyrighted Works Docket No. RM 2002-4 RESPONSE TO WRITTEN QUESTIONS OF JUNE 5, 2003 of N2H2, INC., 8e6 Technologies, Bsafe Online Submitted by: David Burt June 30, 2003 N2H2, Inc. 900 4th Avenue, Suite 3600 Seattle, WA 98164 Tel: (206) 982-1130; Fax: (509) 271-4226 Email: [email protected] 2 The Question Posed by the Copyright Office 3 Problems with Narrowing the Exemption to Exclude "Security Suites" 5 First Amendment Concerns Expressed by Proponents are Misplaced 8 Concerns that CIPA Requires Schools and Libraries to Use "Closed Lists" are Misplaced 9 Opponents Do Not Believe the Record Justifies an Exemption 11 The Threats Posed by the Exemption are Real 18 Conclusion 19 Footnotes 20 3 The Question Posed by the Copyright Office On June 5th, 2003, the Copyright Office asked the opponents of the proposed exemption for "Compilations consisting of lists of websites blocked by filtering software applications" for our response to the following: Please clarify, as specifically as possible, the types of applications you believe should or should not be subject to an exception for the circumvention of access controls on filtering software lists, if such an exception is recommended. Please provide any documentation and/or citations that will support any of the factual assertions you make in answering these questions. The opponents of the exemption do not believe any exemption is justified because there is no supporting record to justify it. The opponents further believe that a narrowed exemption designed to exclude "security suite" applications that include lists of blocked websites would unfairly render the databases of some vendors of lists of blocked websites with protection and others without on an arbitrary basis. -

Ipcop Linux Release 1.4.X Zum Kennenlernen
IPcop Linux release 1.4.x zum Kennenlernen Bruno Hopp Jan. 2006 Linuxuser der Universität zu Köln: www.uni-koeln.de/themen/linux Warum ausgerechnet IPcop ?? Vorteile: recycling eines ausgedienten PC möglich. Bislang IPcop auf i386-i686 etabliert, IPcop für Alpha gibt es schon, für Sparc|Ultrasparc nicht geplant. Standardhardware (NIC) wird unterstützt: alle NIC-driver sind als Module ausgelegt. Interfaces: Modem: JA ISDN: JA Ethernet: JA GB-Ethernet: ist in Arbeit, z.Zt. nur einige wenige Adapter unterstützt. Dedizierter HW-router kann besser spezialisierte Auf- gaben (package filtering) erledigen als eine workstation, auf der "nebenher" noch nameserver (bind9), Samba und ein grafisches Interface laufen. Software ● bis release 1.3 auf RedHat Linux basierend, Installation ncurses-basiert ● Grundlegende Überarbeitung ab release 1.4.x LSB conform, Linux from Scratch, angepasste Smoothwall-Skripte ● aktuelle IPcop releases 1.4.9/1.4.10 mit Kernel 2.4.31, kernel 2.6.x in Planung ● iptables 1.4.1; OpenSSH 3.9p1; OpenSSL 0.9.7e-fips; Apache 1.3.33 (build oct.2005) Perl 5.8.5; GRUB 0.9.5; vim 6.3 IPcop basics ● unterliegt der GNU/GPL ● Routing: forwarding & NAT ● Was kann/soll ein Router neben dem reinen ¹Routingª noch tun? ● Package filtering: iptables ● Web traffic: Proxy Squid ± SquidGuard ± DansGuardian ± URL-filter ● Pop3/Imap: Copfilter u.a. ● Logging lokal oder via Log-server Voraussetzungen zur Installation Download des ca. 42 MB groûen iso-images von CD booten oder Startdiskette+ image von Webserver hda wird kpl neu formatiert mit ext3 (egal ob 500 MB oder 10 GB - Partitionierung nicht beeinflussbar) 486/DX2 mit 16 MB mindestens, 586 (Pentium1)+ 64 MB erlaubt normales Arbeiten - abhängig von Zahl der Requests, der Clients, der Addons etc. -

Configurando Um Servidor Proxy Com O Squid
Configurando um servidor proxy com o Squid Capítulo 2: Compartilhamento, DHCP e Proxy • Configurando um servidor proxy com o Squid o Instalando o Squid o Criando uma configuração básica o Configurando o cache de páginas e arquivos o Adicionando restrições de acesso . Bloqueando por domínios ou palavras . Bloqueando por horário o Gerenciando o uso da banda o Proxy com autenticação o Configurando um proxy transparente o Configuração automática de proxy nos clientes o Mais detalhes sobre a configuração dos caches • Usando o Sarg para monitorar o acesso • Monitorando com o ntop • Usando o SquidGuard para bloquear páginas impróprias • Usando o DansGuardian o Atualizando as blacklists o Proxy transparente com o DansGuardian • Obtendo um endereço fixo, usando um DNS dinâmico Configurando um servidor proxy com o Squid O Squid permite compartilhar a conexão entre vários micros, servindo como um intermediário entre eles e a internet. Usar um proxy é diferente de simplesmente compartilhar a conexão diretamente, via NAT. Ao compartilhar via NAT, os micros da rede acessam a internet diretamente, sem restrições. O servidor apenas repassa as requisições recebidas, como um garoto de recados. O proxy é como um burocrata que não se limita a repassar as requisições: ele analisa todo o tráfego de dados, separando o que pode ou não pode passar e guardando informações para uso posterior. Compartilhar a conexão via NAT é mais simples do que usar um proxy como o Squid sob vários aspectos. Você compartilha a conexão no servidor, configura os clientes para o utilizarem como gateway e pronto. Ao usar um proxy, além da configuração da rede, é necessário configurar o navegador e cada outro programa que for acessar a Internet (em cada um dos clientes da rede) para usar o proxy. -

SUSE Linux Enterprise Server 11 SP4 Administration Guide Administration Guide SUSE Linux Enterprise Server 11 SP4
SUSE Linux Enterprise Server 11 SP4 Administration Guide Administration Guide SUSE Linux Enterprise Server 11 SP4 Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see http://www.suse.com/company/legal/ . All other third party trademarks are the property of their respective owners. A trademark symbol (®, ™ etc.) denotes a SUSE or Novell trademark; an asterisk (*) denotes a third party trademark. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xix 1 Available Documentation xx 2 Feedback xxii 3 Documentation Conventions xxii I SUPPORT AND COMMON TASKS 1 1 YaST Online Update 2 1.1 The Online Update Dialog 3 KDE Interface (Qt) 3 • GNOME Interface (GTK) 4 1.2 Installing Patches 6 1.3 Automatic Online Update 7 2 Gathering System Information for Support 9 2.1 Collecting System Information with Supportconfig -
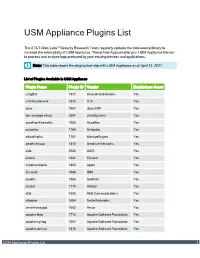
USM Appliance Plugins List
USM Appliance Plugins List The AT&T Alien Labs™ Security Research Team regularly updates the data source library to increase the extensibility of USM Appliance. These AlienApps enable your USM Appliance Sensor to process and analyze logs produced by your existing devices and applications. Note: This table shows the plugins that ship with USM Appliance as of April 13, 2021. List of Plugins Available in USM Appliance Plugin Name Plugin ID Vendor Enabled per Asset Linq2FA 1977 Innovative Solutions Yes a10-thunder-waf 1872 A10 Yes abas 1961 abas ERP Yes abs-scrooge-nxlog 2541 LimeSystems Yes accellion-kiteworks 1965 Accellion Yes actiontec 1764 Actiontec Yes adaudit-plus 1781 ManageEngine Yes aerohive-wap 1814 Aerohive Networks Yes aide 2528 AIDE Yes airlock 1641 Envault Yes airport-extreme 1805 Apple Yes aix-audit 1649 IBM Yes aladdin 1566 SafeNet Yes alcatel 1770 Alcatel Yes allot 1608 Allot Communications Yes alteonos 1684 Nortel Networks Yes amun-honeypot 1662 Amun Yes apache-ldap 1713 Apache Software Foundation Yes apache-syslog 1501 Apache Software Foundation Yes apache-tomcat 1816 Apache Software Foundation Yes USM Appliance Plugins List 1 List of Plugins Available in USM Appliance (Continued) Plugin Name Plugin ID Vendor Enabled per Asset apache 1501 Apache Software Foundation Yes aqtronix-webknight 1964 AQTRONiX Yes arista-switch 1820 Arista Yes arpalert-idm 50003 Arpalert Yes arpalert-syslog 1792 Arpalert Yes array-networks-sag 1906 Array Networks Yes artemisa 1668 Artemisa Yes artica 1775 Artica Yes artillery 1914 Binary Defense -

Un Réseau Sous Linux Avec Debian, Squid Et Squidguard
Un réseau sous linux avec Debian, squid et squidguard http://www.blanche-de-peuterey.com/Un-reseau-sous-linux-avec-Debian-squid-et-squidguard Un réseau sous linux avec Debian, squid et squidguard - Articles - Date de mise en ligne : mercredi 22 septembre 2010 Copyright © Blanche de Peuterey.com, création web à Grenoble - Tous droits réservés Copyright © Blanche de Peuterey.com, création web à Grenoble Page 1/11 Un réseau sous linux avec Debian, squid et squidguard Configurer un serveur sous Linux, afin de réaliser un réseau domestique ou de petite entreprise, avec un filtre parental, le tout réalisé grâce à des logiciels gratuits. Mise à jour de l'article j'ai écrit cet article en septembre 2010. J'avais utilisé à l'époque une distribution Xubuntu, légère, car je ne voulais pas tout faire en ligne de commandes. Depuis, il s'est passé pas mal de choses : 1. J'ai quitté Xubuntu pour Debian, beaucoup plus stable et opérationnel pour un serveur. Et les lignes de commandes, ce n'est pas si compliqué que cela. 2. Le disque dur de mon serveur a planté, et j'ai du tout réinstaller. J'en profite pour faire une mise à jour de cet article. Introduction J'ai beaucoup galéré, n'ayons pas peur des mots. Cela m'a pris un certain temps pour parvenir à ce que je voulais : réaliser la configuration d'un serveur pour un centre culturel. Permettre à chaque utilisateur d'aller sur le net, mettre en place un « filtre parental », capable de bloquer des pages indésirables et de faire un filtrage horaire, éventuellement installer un intranet. -

Reference Opensuse Leap 42.3 Reference Opensuse Leap 42.3
Reference openSUSE Leap 42.3 Reference openSUSE Leap 42.3 Publication Date: November 05, 2018 SUSE LLC 10 Canal Park Drive Suite 200 Cambridge MA 02141 USA https://www.suse.com/documentation Copyright © 2006– 2018 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Docu- mentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see http://www.suse.com/company/legal/ . All other third-party trademarks are the prop- erty of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xvi I ADVANCED ADMINISTRATION 1 1 YaST in Text Mode 2 1.1 Navigation in Modules 3 1.2 Advanced Key Combinations 5 1.3 Restriction of Key Combinations 5 1.4 YaST Command Line Options 6 Starting the Individual Modules 6 • Installing Packages from the Command Line 6 • Command Line Parameters of the YaST Modules 7 2 Managing Software with Command Line Tools 8 2.1 Using Zypper 8 General Usage 8 -
System Administration with Webmin by Joe Cooper System Administration with Webmin by Joe Cooper Copyright © 2000, , 2001, , 2002 Joe Cooper
System Administration With Webmin by Joe Cooper System Administration With Webmin by Joe Cooper Copyright © 2000, , 2001, , 2002 Joe Cooper “System Administration With Webmin” documents system configuration and ongoing system maintenance using the Webmin [http://www.webmin.com/webmin] web based administration tool. Table of Contents Preface ......................................................................................... xii Conventions Used in This Guide ............................................................. xii Who Webmin is For ....................................................................... xiii Who This Book is For ...................................................................... xiv Why a Webmin Book? ...................................................................... xv How to Contact the Author and Errata ....................................................... xvii How to Contact No Starch Press ............................................................ xvii Acknowledgments ........................................................................ xvii 1. Getting and Installing Webmin ................................................................... 1 Where to Download Webmin ................................................................. 1 Installing Webmin ........................................................................... 1 Installing from a tar.gz .................................................................. 1 Installing from an RPM ................................................................ -

Servidor De Seguridad Perimetral II
Servidor de seguridad perimetral II Por. Daniel Vazart Proxy + filtro de contenidos + estadísticas ● Squid (http://www.squid-cache.org/): Squid es un Servidor Intermediario (Proxy) de alto desempeño que se ha venido desarrollando desde hace varios años y es hoy en día un muy popular y ampliamente utilizado entre los sistemas operativos como GNU/Linux y derivados de Unix®. Es muy confiable, robusto y versátil y se distribuye bajo los términos de la Licencia Pública General GNU (GNU/GPL). Proxy + filtro de contenidos + estadísticas ● Dansguardian (http://dansguardian.org/): Dansguardian es un Proxy con filtro de contenidos para sistemas Unix como: Linux, FreeBSD, OpenBSD, NetBSD, Mac OS X, HP-UX y Solaris que pueden correr Squid como WEB Proxy. Dansguardian realiza el filtrado por diferentes métodos como el filtrado de URL y nombres de dominio, filtrado de frases en el contenido de una pagina, filtrado por PICS, filtro por tipos de archivos y filtros por POST. El filtrado de frases en el contenido chequea las paginas en busca de palabras obscenas, pornográficas y otras no deseadas. El filtrado de POSTS permite bloquear o limitar la subida de archivos por Internet. El filtro de URL y de nombres de dominio, permite manejar grandes listas y es considerablemente mas rápido que SquidGuard. Proxy + filtro de contenidos + estadísticas ● SARG (http://sarg.sourceforge.net): Es un analizador de logs para Squid que genera reportes WEB sobre la navegación a través del proxy. Requerimientos del sistema ● Dansguardian requiere un mínimo de 150 MHz de procesador y 32 MB de memoria RAM por cada 50 usuarios concurrentes.