A Survey of the Use of Adobe Flash Local Shared Objects to Respawn HTTP Cookies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Ccleaner Download for Pc Windows 7 Ccleaner for Windows
ccleaner download for pc windows 7 CCleaner for Windows. CCleaner for Windows is a free PC optimizer that frees up space on your computer by r emoving unnecessary files such as cookies, unused data, and temporary files . This Piriform’s programme runs regular checks and finds those elements that slow down your computer performance . What is the CCleaner application? CCleaner is used to clean and tune up the operating system of the PC. With CCleaner, we can carry out a thorough cleaning of the PC in a simple way, which will allow us to gain space on the hard disk and prevent the PC from slowing down. It is one of those free tools for PC that works exceptionally well when it comes to deleting temporary files . CCleaner is a free , closed-source programme that can be downloaded to various devices and has been developed by the private software company Piriform Ltd , based in London, UK. Its launch date was September 23, 2003. Over the years it has undergone several updates and versions on the three platforms on which it is available: Windows, MacOS and Android . By downloading CCleaner, the software allows the cleaning up of different files, as well as optimisation of the operating system . In addition, it is capable of uninstalling multiple programmes from the interface and disabling certain applications from being executed at system startup. The benefits that the device in question derives from downloading CCleaner are improved boot speed , reduced system load and release of wasted disk space . Also, access becomes much faster. What are the benefits of downloading CCleaner? To be more specific, the useful tasks that CCleaner performs are as follows: Deleting unnecessary files Deleting temporary files and other data Freeing up hard disk space Disabling programs whose start-up is linked to the system boot Eliminating application waste Deleting browsing histories Cleaning the registry Identifying duplicate files Correcting errors that cause problems. -

Datasheets Datasheet
PROFESSIONAL DATASHEETSDATASHEET Get that fresh ‘new PC’ feeling back with CCleaner Professional If your PC is slow, crashing or running out of hard drive space, CCleaner Professional is the solution. Its patented cleaner clears the clutter from your hard drive, removes junk from the Windows Registry, and protects your privacy by removing tracking cookies and browser history. All without touching your documents, music, videos and other files. If you have more than one person using your PC, CCleaner Professional can clean multiple user profiles. With system monitoring it keeps an eye on your system in the background and cleans when needed. It updates itself automatically, so you’ve always got the latest version. And if you have any questions, our priority technical support team has answers. Regain your PC’s speed, stability and privacy with CCleaner Professional. CCLEANER PROFESSIONAL HIGHLIGHTS 1. CCleaner Professional analyzes PCs to see what can be cleaned. You decide when and what to clean. 2. The patented Registry cleaner locates and fixes problems in the Windows Registry so that Windows remains stable on your PC. 3. CCleaner Professional removes tracking cookies, while keeping the cookies you need to access web-based applications like Gmail and Facebook. MADE BY For more information contact [email protected] www.piriform.com PROFESSIONAL DATASHEET CCLEANER PROFESSIONAL: A FASTER, MORE RELIABLE PC – INSTANTLY Make your PC last longer CCleaner Professional speeds up your PC and recovers hard drive space. It’s like getting a brand-new PC for a fraction of the cost. Easy to use If you can use email, you can use CCleaner Professional. -

Defraggler Windows 10 Download Free - Reviews and Testimonials
defraggler windows 10 download free - Reviews and Testimonials. It's great to hear that so many people have found Defraggler to be the best defrag tool available. Here's what people are saying in the media: "Defraggler is easy to understand and performs its job well. if you want to improve computer performance, this is a great place to start." Read the full review. LifeHacker. "Freeware file defragmentation utility Defraggler analyzes your hard drive for fragmented files and can selectively defrag the ones you choose. The graphical interface is darn sweet." Read the full review. PC World. "Defraggler will show you all your fragmented files. You can click one to see where on the disk its various pieces lie, or defragment just that one. This can be useful when dealing with very large, performance critical files such as databases. Piriform Defraggler is free, fast, marginally more interesting to watch than the default, and has useful additional features. What's not to like?" Read the full review. - Features. Most defrag tools only allow you to defrag an entire drive. Defraggler lets you specify one or more files, folders, or the whole drive to defragment. Safe and Secure. When Defraggler reads or writes a file, it uses the exact same techniques that Windows uses. Using Defraggler is just as safe for your files as using Windows. Compact and portable. Defraggler's tough on your files – and light on your system. Interactive drive map. At a glance, you can see how fragmented your hard drive is. Defraggler's drive map shows you blocks that are empty, not fragmented, or needing defragmentation. -

Windows Apps Will Help You Get the Most out of Your New PC (Digitaltrends.Com)
Free Windows 10 Applications MARCH 21, 2019 SIR Computer & Tech Leadership Team CAT Tech Advisors (The “Experts”) Phil Goff Derek Southern Dean Steichen Barry Brown Frank May Neil Schmidt CAT Support Team Dan Green (Treasurer) Nick Bowes (Asst. Treasurer) Dick Curry (Coffee Master) Bill Phelon (Membership) Windows 10 App News Articles Several 1 st of Year Tech articles about Windows 10 Apps: Useful and Unknown Software and Tools of 2018 for Windows (ampercent.com) Top 35 free apps for Windows 10 (computerworld.com) The 20 Best Productivity Apps for Windows in 2018 (zapier.com) 2019 list: Best free software for a new Windows 10 (windowsreport.com) Our favorite Windows apps will help you get the most out of your new PC (digitaltrends.com) SIR Area 16 Computer & Technology Group “Tech Advisors” Windows Store How do you load “apps”? Windows Store Find it in your “Start” screen Or just type “Store” in the search bar Download program from web site PC Utility Apps Flipboard News aggregator Personalize to include articles of interest to you: Technology CNET Mobile Technology The DYI PC Home Automation Etc., etc. Available for PC, mobile Free (Windows Store) Also available for Mac Digital Trends Microsoft “OfficeOnline” Web based MS Office View, edit and create Office files on your browser Get many of the features of Word, Excel, Powerpoint and OneNote Somewhat similar to Google Docs Free (Windows Store) Computerworld FreeOffice Office productivity suite Similar to WORD, EXCEL, etc. Runs inside your favorite -
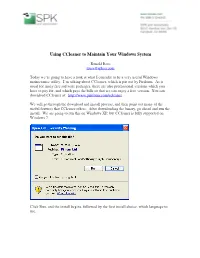
Using Ccleaner to Maintain Your Windows System
Using CCleaner to Maintain Your Windows System Ronald Ross [email protected] Today we’re going to have a look at what I consider to be a very useful Windows maintenance utility. I’m talking about CCleaner, which is put out by Piriform. As is usual for many free software packages, there are also professional versions which you have to pay for, and which pays the bills so that we can enjoy a free version. You can download CCleaner at: http://www.piriform.com/ccleaner We will go through the download and install process, and then point out many of the useful features that CCleaner offers. After downloading the binary, go ahead and run the install. We are going to run this on Windows XP, but CCleaner is fully supported on Windows 7. Click Run, and the install begins, followed by the first install choice, which language to use. Select the language of choice, and click OK. At this point, the install can begin. Click Next to continue. Have a look at the license, and if you decide to continue, click on “I Agree”. Here is where it gets more interesting. Make the choices in the Install Options that suit your tastes. I don’t much care for shortcuts cluttering up my desktop, for example, but you may feel differently. Click Install or Advanced to continue. Here, we are going to click Advanced, which will take us to the next panel. Usually the default for this install option is best, but perhaps you are sharing this computer with a child, or some other person that you don’t fully trust to always do the right thing when it comes to computers. -

Ccleaner & Defraggler Performance Report
CCleaner & Defraggler Performance Report (September 2017) Windows 7 & Windows 10 Performance Benchmark Document: CCleaner & Defraggler Performance Report Authors: M. Baquiran, D. Wren Company: PassMark Software Date: 27 September 2017 File: Piriform_CCleaner_Performance_Ed2.docx Edition 2 CCleaner & Defraggler Performance Report PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 SUMMARY ........................................................................................................................................................ 3 PRODUCTS AND VERSIONS ............................................................................................................................... 4 TEST RESULTS ................................................................................................................................................... 5 BENCHMARK 1 – DISK SPACE RECOVERED FROM INITIAL CLEANUP ..................................................................................... 5 BENCHMARK 2 – DISK SPACE RECOVERED PER WEEK ....................................................................................................... 5 BENCHMARK 4 – CHANGE IN FREE RAM ...................................................................................................................... 6 BENCHMARK 4 – MACHINE BOOT TIME ....................................................................................................................... -

How-To-Secure-Your-Computer.Pdf
© 2020– Institute For War And Peace Reporting https://iwpr.net/ This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International (CC BY-SA 4.0) license. https://creativecommons.org/licenses/by-sa/4.0/deed.en Contents 1 How to secure your computer 5 Leading the Session ........................... 6 Part 1 - Introduction ........................ 6 Part 2 – Physical Environments and Maintenance ....... 6 Part 3 – Software Safety ...................... 7 Part 4 – Data Protection and Backups .............. 9 Part 5 - Deleting Files and Recovering Them ........... 10 References ................................ 11 3 Contents 4 How to secure your computer • Objective(s): Identifying good practices to keep our computers safe. • Length: 50 minutes • Format: Session • Skill level: Basic • Required knowledge: – None required • Related sessions/exercises: – How does the internet work?1 – Safe browsing2 – Malware and viruses3 – Storage and encryption4 • Needed materials: – Slides (with key points included below) – Laptop/Computer and Projector setup – Printed copies of the Backup Format Template (see below) • Recommendations: It is strongly recommended that you do live demon- 1https://cyber-women.com/en/digital-security-basics-1/how-does-the-internet-work/ 2https://cyber-women.com/en/digital-security-basics-1/safe-browsing/ 3https://cyber-women.com/en/digital-security-basics-1/malware-and-viruses/ 4https://cyber-women.com/en/digital-security-basics-2/storage-and-encryption/ 5 How to secure your computer stration – using a projector connected to your laptop - of any tools you choose to cover in this session, so that participants can follow along and practice on their own computers using “dummy” files created for the purposes of the session (not actually important data or files!) Leading the Session Part 1 - Introduction 1. -
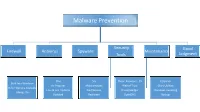
Malware Prevention Tools
Malware Prevention Security Good Firewall Antivirus Spyware Maintenance Tools Judgment One One Three Browsers - CV CCleaner Built Into Windows AV Program Malwarebytes Web of Trust Glary Utilities Other Options Available Free & Fee Options Paid Version Privacy Badger Windows Tweaking Always On Updated Real-time OpenDNS Backup Malware Prevention Tools • Firewall - included with the Windows operating system, is real-time • Antivirus – start with MS Security Essentials available www.ninite.com , is real-time • Spyware – free version Malwarebytes available www.ninite.com , free version can be upgraded to paid version, free version is not real-time • Browsers – Internet Explorer comes with the Windows operating system, Google Chrome and Mozilla Firefox are available from www.ninite.com , all browsers are free • Web of Trust – free, available https://www.mywot.com/en/download , real-time • Privacy Badger - https://www.eff.org/privacybadger , available Chrome & Firefox only, free, real-time • OpenDNS – free, available https://www.opendns.com/home-internet-security/opendns-ip-addresses/ • CCleaner – free, available www.piriform.com , paid version not needed, and or, or both • Glary Utilities – free, available www.ninite.com , run 2x per month, update do not upgrade • Windows Tweaking – free, 38 features by default, “direct download only”, careful what you click on http://www.tweaking.com/content/page/windows_repair_all_in_one.html , run in Safe Mode • Backup – three “free” choices 1. Windows backup built into OS, files & folders and image backup available 2. EaseUs – free, available http://www.todo-backup.com/products/home/free-backup-software.htm , files & folders and image 3. Bvckup 2 – free, simple backup, available https://bvckup2.com/ , files only, non encrypted, very fast • FYI – The Sun City Computer Club will more than likely “host” some or all of the foregoing, www.ninite.com is the safest source for a variety of “free” downloads, if a product is not available on ninite.com, install software only from the vendors website! Malware Removal Process 1. -

Ccleaner Technician Edition Is the Portable Tool Your Techs Need to Keep Pcs Running Without Interruption
TECHNICIAN EDITION DATASHEETSDATASHEET The portable system optimization tool your technicans can’t live without The faster your technicians can solve a customer’s PC problem, the faster they can move on to the next client. CCleaner Technician Edition is the portable tool your techs need to keep PCs running without interruption. Its patented cleaner cleans out unnecessary files, recovers hard drive space, prevents crashes, speeds up Windows and helps to protect privacy and security. It can be installed on a USB drive or used as a remote tool – whatever suits your business model. CCleaner Technician Edition also cleans multiple user profiles, updates itself automatically, includes background monitoring and comes with priority technical support. CCleaner Technician Edition is a must-have optimization tool for your team. CCLEANER TECHNICIAN EDITION HIGHLIGHTS 1. CCleaner analyzes PCs to see what can be cleaned. Your techs decides when and what to clean. 2. The patented Registry cleaner locates and fixes problems in the Windows Registry so that Windows remains stable on your customers’ PCs. 3. CCleaner removes tracking cookies, while keeping the cookies your customers need to access web-based applications. MADE BY For more information contact [email protected] www.piriform.com TECHNICIAN EDITION DATASHEET CCLEANER TECHNICIAN EDITION - AN ESSENTIAL PART OF YOUR PC REPAIR TOOLKIT Extend the lifecycle of customers’ PCs CCleaner speeds up PCs and recovers hard drive space. Your customers’ PCs can last longer – saving them money and providing you with a great value proposition. Perfect complement to anti-virus CCleaner is the first step in repairing and diagnosing a PC prior to running anti-virus programs. -

Ccleaner APT Attack: a Technical Look Inside
#RSAC SESSION ID: HTA-T10 CCleaner APT Attack: A Technical Look Inside Ondrej Vlcek CTO, EVP and GM, Consumer Avast @AvastVlk @avast_antivirus A CCleaner Overview The No. 1 PC Cleaning Tool on the Market #RSAC • #1 PC Cleaning Tool on the market • Piriform (the company) founded in 2004 • Monthly releases 2 BILLION+ • Freemium DOWNLOADS – Free – Professional – Business • CCleaner Cloud • Windows XP to Windows 10, 32-bit & 64-bit version CCleaner APT Attack: A TECHNICAL LOOK INSIDE 2 A CCleaner Overview Worldwide Footprint #RSAC • 100M active users • Worldwide • 10M - Latest CCleaner APT Attack: A TECHNICAL LOOK INSIDE 3 #RSAC CCleaner = The Perfect Target In The Firing Line B The Attack In the Firing Line #RSAC • Multi (3+) stage attack delivered • Affected products: via compromised supply chain – CCleaner v5.33.6162 and • Compromised Piriform’s build server (outside of Avast infrastructure) – CCleaner Cloud v1.7.0.3191 • Altered compiler’s library resulting • Up to 2.27M installations of in an APT digitally signed by Piriform compromised versions • Distributed for a month before • 1.65M confirmed to have found, fixed and disclosed communicated with the CNC server • 40 PCs received the 2nd stage payload CCleaner APT Attack: A TECHNICAL LOOK INSIDE 5 B CCleaner = The Perfect Target Timeline of Events #RSAC March - July Jul 18 Aug 11 Aug 25 Sept 15 Sept 19 Breach and Avast acquires Build of CCleaner Build of CCleaner 1st Stage CnC 1st Stage CnC lateral movement Piriform Cloud with 5.34 without taken down dump received; 2nd in Piriform malicious -

Ccleaner - Version History
CCleaner - Version History For Home For Business Download Support Company Home Products CCleaner Version History CCleaner Version History v5.02.5101 (26 Jan 2015) Download - Improved Firefox Local Storage and Cookie cleaning. Features - Improved Google Chrome 64-bit support. FAQ - Improved Firefox Download History analysis and cleaning. Screenshots - Optimized Disk Analyzer scanning process. Reviews - Improved detection and cleaning of portable browsers. Update - Updated various translations. - Minor GUI Improvements. Help - Minor bug fixes. v5.01.5075 (18 Dec 2014) Products - New Disk Analyzer tool. - Improved Firefox 34 cleaning. CCleaner - Improved Opera History cleaning. - Optimized Memory and CPU usage. CCleaner Network Edition - Improved localization support. Defraggler - Minor GUI Improvements. - Minor bug fixes. Recuva Speccy v5.00.5050 (25 Nov 2014) - New improved GUI. - Improved internal architecture for better performance. - Added Google Chrome plugin management. Email Newsletter - Improved Google Chrome Startup item detection. - Optimized automatic updates for Pro version. - Improved system restore detection routine. - Updated exception handling and reporting architecture. - Optimized 64-bit builds on Windows 8, 8.1 and 10. - Updated various translations. Product News - Many performance improvements and bug fixes. v4.19.4867 (24 Oct 2014) February 3, 2015 - Added Windows 10 Preview compatibility. CCleaner for Android v1.07 - Improved Opera 25 Cache cleaning. Now with root uninstall! - Improved exception handling and reporting architecture. - Improved Auto-Update checking process. January 26, 2015 - Updated various translations. CCleaner v5.02 - Minor GUI Improvements. Improved Firefox local storage and - Minor bug fixes. cookie cleaning! v4.18.4844 (26 Sep 2014) January 21, 2015 - Added Active System Monitoring for Free users Speccy v1.28 - Improved Firefox Saved Password cleaning. -
Ccleaner Business Passmark Report
in association with CCleaner , faster: proven! How optimized business endpoints boost productivity and save IT time and money CCleaner Defraggler Built for small businesses, big businesses and service providers. E: [email protected] www.piriform.com/business T: 001-800-816-9004 (toll free) Our business software was built to take the strain off your IT department. Cleaning and defragmenting PCs probably isn’t at the top of your agenda. We know that. You probably know that you should do it but it’s time consuming and with resources constantly under strain, it seems to be a bottom-of-the-list task which you never get around to doing. Or at least not until the support tickets come in. This is why we invented CCleaner and Defraggler. Automated cleaning and defragmenting means your IT department spends less time on basic maintenance and end users work on better performing machines, without the constant threat of low disk space. We believe our software is a win-win solution for any businesses using PCs. But of course we’d say that, which is why we asked Passmark, a third-party software testing specialist, to put our software through its paces. In this report we’ve highlighted Passmark’s main findings. You can view the full report here: www.passmark.com/reports/ccleaner17.pdf 2 Contents • Summary ......................................................................................................................................................... 4 • What CCleaner and Defraggler do .............................................................................................................