Enhanced Packet Delivery Techniques Using Crypto-Logic Riddle on Jamming Attacks for Wireless Communication Medium
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tap Code 1 2 3 4 5 1 a B C D E 2 F G H I J 3 L M N O P 4 Q R S T U 5
Solution to Kryptos 2: Challenge 1 The audio files indicate that the prisoners are communicating with each other by “tapping”. There are two distinct tapping sounds which indicate the two prisoners are exchanging some sort of information back and forth. Furthermore, unlike Morse Code, each audio file is made up of pairs of taps which leads one to believe that each pair of taps corresponds to a word or letter. The longest tapping sequence is five, so if one assumes that each tap-pair corresponds to a pair of integers between 1 and 5, then this code could encipher 25 items – most likely letters. At this point, one could try a frequency analysis to help identify which pairs of integers correspond to which letters. Alternatively, a little research might yield the “tap code” (see e.g. Wikipedia) which has been used by prisoners of war in various conflicts throughout history, most recently Vietnam. It is based on the Polybius square, some of which have slightly different arrangements of the 26 letters placed into 25 cells. Challenge 1 was based on the following key found on Wikipedia: Tap code 1 2 3 4 5 1 A B C D E 2 F G H I J 3 L M N O P 4 Q R S T U 5 V W X Y Z The tap code table This has all letters except “K”, so “C” is used instead. The letter “X” is used to separate sentences. The first audio file begins with the following tap-pairs: (2,4), (4,3), (1,3), (3,4), (5,1), (1,5), (4,2),… which yields the following plaintext: i, s, c, o, v, e, r, … By adding in the likely punctuation, the complete conversation can be decoded: PLAINTEXT Prisoner 1: Is cover intact? Prisoner 2: Yes. -

Jan. 2012 Issue
AmateurAmateur AA RR SS SocietySociety NewsNews Newsletter of The Amateur Radio Society of India (Member of IARU) English / Hindi Quarterly Volume I Issue 7 KARBIL/2009/38494 Jan. 2012 Price : Rs.10/- President’s message From the Editor’s desk Dear members all of us active hams are looking at Most of us were privileged to be a part learning more about. Here's wishing you all a HAPPY of Hamfest 2011 which was held in ARSI applied for and obtained special NEW YEAR 2012. More and more Kochi. It was an extremely well suffix for use by all Indian hams in amateurs are showing interest in organised and coordinated event with a commemoration of India's first HUGE gathering of hams and SWL's Formula 1 race meet at Greater Noida. working Satellites, so I have all having a chance to have an eyeball Many hams took an active part in the included a list of operational with their old friends and make new effort in running this most prestigious satellites along with the details. ones. The location and facilities were event. really great. Band conditions seems to be The propagation on the HF bands is improving – I expect a lot of activity The display and sales areas were just picking up nicely and we can hear and this year resulting in more news and like a major exhibition and there was work stations worldwide after a gap of space to move around and see what one some months. reports for me to include in the could pick up for homebrew efforts and newsletter, Hi Please send articles, augment one's shack. -
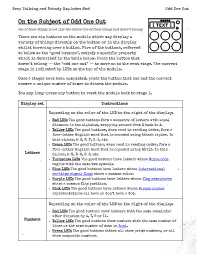
On the Subject of Odd One Out
Keep Talking and Nobody Explodes Mod Odd One Out On the Subject of Odd One Out One of these things is not like the others! One of these things just doesn’t belong! There are six buttons on the module which may display a variety of things directly on the button or in the display whilst hovering over a button. Five of the buttons, referred to below as the “good buttons”, satisfy a specific property which is described in the table below. Press the button that doesn’t belong — the “odd one out” — to move on to the next stage. The current stage is indicated by LEDs at the top of the module. Once 5 stages have been completed, press the button that has had the correct answer a unique number of times to disarm the module. You may long-press any button to reset the module back to stage 1. Display set Instructions Depending on the color of the LED to the right of the display: Red LED: The good buttons form a sequence of letters with equal distance in the alphabet, wrapping around from Z back to A. Yellow LED: The good buttons, when read in reading order, form a five-letter English word that is encoded using Atbash cipher. In this cipher, A↔Z, B↔Y, C↔X, etc. Green LED: The good buttons, when read in reading order, form a five-letter English word that is encoded using ROT13. In this Letters cipher, A↔N, B↔O, C↔P, etc. Turquoise LED: The good buttons have letters whose Morse code begins with the same two symbols. -

Inferences from Interactions with Smart Devices: Security Leaks and Defenses
Syracuse University SURFACE Dissertations - ALL SURFACE August 2019 Inferences from Interactions with Smart Devices: Security Leaks and Defenses Diksha Shukla Syracuse University Follow this and additional works at: https://surface.syr.edu/etd Part of the Engineering Commons Recommended Citation Shukla, Diksha, "Inferences from Interactions with Smart Devices: Security Leaks and Defenses" (2019). Dissertations - ALL. 1060. https://surface.syr.edu/etd/1060 This Dissertation is brought to you for free and open access by the SURFACE at SURFACE. It has been accepted for inclusion in Dissertations - ALL by an authorized administrator of SURFACE. For more information, please contact [email protected]. ABSTRACT We unlock our smart devices such as smartphone several times every day using a pin, password, or graphical pattern if the device is secured by one. The scope and usage of smart devices’ are expanding day by day in our everyday life and hence the need to make them more secure. In the near future, we may need to authenticate ourselves on emerging smart devices such as electronic doors, exercise equipment, power tools, medical devices, and smart TV remote control. While recent research focuses on developing new behavior-based methods to authenticate these smart devices, pin and password still remain primary methods to authenticate a user on a device. Although the recent research exposes the observation-based vulnerabilities, the popular belief is that the direct observation attacks can be thwarted by simple methods that obscure the attacker’s view of the input console (or screen). In this dissertation, we study the users’ hand movement pattern while they type on their smart devices. -

A Wire‑Tap Approach to Enhance Security in Communication Systems Using the Encoding‑Encryption Paradigm
This document is downloaded from DR‑NTU (https://dr.ntu.edu.sg) Nanyang Technological University, Singapore. A wire‑tap approach to enhance security in communication systems using the encoding‑encryption paradigm Mihaljevic, Miodrag; Oggier, Frederique 2010 Mihaljevic, M. & Oggier, F. (2010). A wire‑tap approach to enhance security in communication systems using the encoding‑encryption paradigm. Information and Coding Theory Workshop, International Conference on Telecommunications (ICT) 2010. https://hdl.handle.net/10356/93759 Downloaded on 28 Sep 2021 14:24:25 SGT A Wire-tap Approach to Enhance Security in Communication Systems using the Encoding-Encryption Paradigm Miodrag Mihaljevic´ Fred´ erique´ Oggier Mathematical Institute Division of Mathematical Sciences Serbian Academy of Sciences and Arts, Belgrade, Serbia School of Physical and Mathematical Sciences and Research Center for Information Security (RCIS) Nanyang Technological University Institute of Advanced Industrial Science and Technology (AIST), Singapore Tokyo, Japan Email: [email protected] Email:[email protected] Abstract—Motivated by the GSM system, we consider com- the redundant data from the cryptographic security point of munication systems which employ the encoding-encryption view has been pointed out even in [6] where the cryptography paradigm of first encoding the data before encrypting it for as a scientific topic has been established. Performing error- transmission. We add one level of security to the existing system designs by introducing a wiretap encoder. We analyze the security correction coding of a message before encryption introduces a from an information theoretical point of view, and prove the structured redundancy, which could be an origin for mounting enhanced security of the proposed scheme, focusing on the certain attacks against the employed keystream generator. -

On the Subject of Seven Choose Four
Keep Talking and Nobody Explodes Mod Seven Choose Four On the Subject of Seven Choose Four Pomelo colors? Pomelo colors! This module consists of four pink buttons, each with a flashing LED next to them. Tips to Success Successfully: In order to solve this module, you must submit four 4-digit codes in sequence. There are 4 possible type of flashes: Morse Code, Tap Code, a sequence of colors, and a number of long flashes between 1 and 7. The morse code and tap codes are deciphered in the usual way. NOTE: Always use C instead of K if the received tap code is 13. The sequence of colors will flash 5 different color. The number of long flashes corresponds to the position of this list below: R G B M C Y W Start from the LED which lights a sequence of colors, take the sequence of the colors and refer to the table below: Position Description 1 Color operator for Stage 1 2 Color operator for Stage 2 3 Color operator for Stage 3 4 Color operator for Stage 4 5 Input for Stage 1 (First letter of the color) The inputs for subsequent stages are based on the position of the LED which lights a sequence of colors, where remaining inputs continue from the its location downward, wrapping around as necessary. The instructions to determine the 4-digit code for each color operator can be found below. NOTE: When entering the code, shift down by N times, wrapping around as necessary, where N = (Current stage number - 1). -

Les Codes Secrets Décryptés
Les codes secrets décryptés 3ème édition corrigée et augmentée Didier Müller Nymphomath Éditions Contact : [email protected] © Nymphomath Éditions, 2018-2020 version 3.0 : 9 septembre 2018 version 3.2 : 13 décembre 2020 ISBN 978-2-8399-2485-6 À Pierre Baud « It may be roundly asserted that human ingenuity cannot concoct a cipher which human ingenuity cannot resolve... » « On peut affirmer que l'ingéniosité humaine ne peut pas élaborer un chiffre que l'ingéniosité humaine ne peut résoudre... » Edgar Allan Poe A Few Words on Secret Writing, 1841. Avant-propos AVANT-PROPOS La cryptologie, plus communément appelée la science des codes secrets, est à la fois une science et un art. C'est une science, car elle fait appel aux mathématiques et à l'informatique, que ce soit pour chiffrer des messages ou pour les décrypter. La cryptologie est aussi un art, car elle fait appel aux talents d'intuition, d'imagination et d'invention du décrypteur, ces facultés étant elles-mêmes secondées par des connaissances linguistiques approfondies. Je voulais écrire un livre qui s'inscrirait dans la ligne de ceux des grands cryptologues du 20 ème siècle : Baudouin, Friedman, Givierge, Langie, Sacco, Fouché Gaines, Sinkov, et quelques autres. Leurs livres ne se contentaient pas de présenter des systèmes de chiffrement, ils montraient aussi leurs faiblesses et comment les décrypter. Je vous invite donc à un voyage dans le temps, depuis l'Antiquité jusqu'à nos jours, où vous découvrirez les systèmes de chiffrement qui ont marqué leur époque. Nous regarderons plus d'une centaine de chiffres, la plupart ne demandant que du papier et un crayon. -

&./3?J- Ornl-5183 Programs
}&./3?J- ORNL-5183 PROGRAMS •ll-TEMFEMTIIE US ClllEI lEJtCTM SAFETY STIIIES PRWRESS wrwi lawni 1,1974 • Iwe 31,1975 T. t. Col* J. P. Sondvrs *. R. Kosttn ORRL-51S3 Distribution Category OC-77 Contract Ho. H-7405-eng-26 HICB-TEKPERATURE GAS-COOLED REACTOR SAPETT STUDIES PROGRESS lEPORT FOR JANUARY 1, 1974, THROUGH JURE 30, 1975 Tt S. Cole and J. P. Sanders, Program Managers P. R. Kasten, Prograa Director Dole Published: July 1977 OAK RIDGE RATIONAL LABORATORY Oak Ridge, Tennessee 37830 operated by UWI01I CARBIDE CORPORATIOR for the EHERCY RESEARCH AMD DEVELOPHERT ADMIRISTRATIOR mr CiSlRIBUTICN OF THIS DOCUMENT IS UNUMlTEd 90UHBKD The Gas-Cooled Reactor Program being carried oat at the Oak Ridge national laboratory contribute to the development and evaluation of nign-tenpereture gas-cooled reactors (nTGRs) and of gas-cooled fast reactors (OCRs). The development programa that are •nonsored by the U.S. Energy Besearch and Development Administration (Etta) include the Iberian Utilisation Program (RGg fuel lecycle Development Program), the RGR base Technology Program, the HTCK Safety Programs, and the CCFt Progran. In addition to the Una progress, safety stadias and assess- •eats have aleo been perfornad at the request and under sponsorship of the Division of Systens and Safety and the Division of leactor Safety Research of the U.S. nuclear Regulatory Commission. These stadias con sisted of Independent, objective assessnents of the safety aspects of specific systens of power stations for which construction or operating licenses were being considered. This report documents the work perfomed under all phases of the RGB safety atodies at OWL. -

Perception and Action Planning
EUROPEANJOURNAL OF COGNITIVE PSYCHOLOGY, 1997, 9 (2), 129± 154 Perception and Action Planning Wolfgang Prinz Max-Planck-Institute for Psychological Research and Institute for Psychology, University of Munich, Munich, Germany A new framework for the understanding of functional relationships between perception and action is discussed. According to this framework, perceived events and planned actions share a common representational domain (common-coding approach). Supporting evidence from two classes of experimental paradigms is presented: induction paradigms and interference paradigms. Induction paradigms study how certain stimuli induce certain actions by virtue of similarity. Evidence from two types of induction tasks is reviewed: sensorimotor synchronisation and spatial compatibility tasks. Interference paradigms study the mutual interference between the perception of ongoing events and the preparation and control of ongoing action. Again, evidence from two types of such tasks is reviewed, implying interfer- ence in either direction. It is concluded that the evidence available supports the common coding principle. A further general principle emerging from these studies is the action e ect principleÐ that is, the principle that cogni- tive representations of action e ects play a critical role in the planning and control of these actions. INTRODUCTION In this paper, I present a framework for understanding some aspects of the functional relationships between perception and action. It is mainly a framework for action control and action planning, but to some extent it is a framework for perception as well. Its core contention is that Downloaded by [University of Arizona] at 05:18 24 December 2012 perceived events and planned actions share a common representational domain. -

Information Theoretic Secrecy for Some Multiuser Wireless
The Pennsylvania State University The Graduate School College of Engineering INFORMATION THEORETIC SECRECY FOR SOME MULTIUSER WIRELESS COMMUNICATION CHANNELS A Dissertation in Electrical Engineering by Ender Tekin c 2008 Ender Tekin Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy August 2008 The dissertation of Ender Tekin was reviewed and approved∗ by the following: Aylin Yener Associate Professor of Electrical Engineering Dissertation Adviser Chair of Committee David J. Miller Associate Professor of Electrical Engineering John F. Doherty Professor of Electrical Engineering Guohong Cao Associate Professor of Computer Science W. Kenneth Jenkins Professor of Electrical Engineering Head of the Department of Electrical Engineering ∗Signatures are on file in the Graduate School. iii Abstract The widespread use of multiuser wireless communications has been raising the demand for higher data rates and until now that has been the main design focus in wireless systems. This design focus, however, neglects the critical issue of communications security inherent in wireless systems that present a channel that is very easy for people of criminal intent to tap. Existing approaches leave this important issue to the higher layers of the protocol hierarchies, yet the need to deal with it in lower layers is imminent as the security of many cryptographic algorithms is hard to evaluate and has caused disappointment in the past. In addition, there is rising interest in large networks of low-complexity transmitters such as sensor nodes and RF-ID tags that do not have room for complicated and computationally intensive cryptographic algo- rithms. Historically, communication secrecy has been evaluated using one of two approaches: information theory or computational complexity. -

Computer and Data Security Class 4 ﺳﻜﻴﻨﺔ ﺣﺴﻦ هﺎﺷﻢ . د: أﺳﺘﺎذة اﻟﻤﺎدة
Save from: www.uotechnology.edu.iq/dep‐cs Computer and Data security 4th Class أﺳﺘﺎذة اﻟﻤﺎدة: د. ﺳﻜﻴﻨﺔ ﺣﺴﻦ هﺎﺷﻢ Introduction to Data Security Basic Terminology Suppose that someone wants to send a message to a receiver, and wants to be sure that no-one else can read the message. However, there is the possibility that someone else opens the letter or hears the electronic communication. In cryptographic terminology, the message is called plaintext or cleartext. Encoding the contents of the message in such a way that hides its contents from outsiders is called encryption. The encrypted message is called the ciphertext. The process of retrieving the plaintext from the ciphertext is called decryption. Encryption and decryption usually make use of a key, and the coding method is such that decryption can be performed only by knowing the proper key. Cryptography is the art or science of keeping messages secret. Cryptanalysis is the art of breaking ciphers, i.e. retrieving the plaintext without knowing the proper key. People who do cryptography are cryptographers, and practitioners of cryptanalysis are cryptanalysts. Cryptography deals with all aspects of secure messaging, authentication, digital signatures, electronic money, and other applications. Cryptology is the branch of mathematics that studies the mathematical foundations of cryptographic methods. Basic Cryptographic Algorithms A method of encryption and decryption is called a cipher. Some cryptographic methods rely on the secrecy of the algorithms; such algorithms are only of historical interest and are not adequate for real-world needs. All modern algorithms 1 use a key to control encryption and decryption; a message can be decrypted only if the key matches the encryption key. -

SUNY Delhi Financial Aid
SUNY Delhi Financial Aid The Process Obtain a FSA ID for student and one parent at https://fsaid.ed.gov (opens new window). How to apply for a FSA ID Keep FSA IDs in a safe place. Use FSA IDs as electronic signatures on the FAFSA and other aid applications. File the FAFSA on the Web (opens a new window) as soon after Jan. 1st as possible. Filing online is highly recommended. It speeds the aid process. Questions? Click here for "7 Easy Steps to the FAFSA." For a paper FAFSA call 1-800-4FEDAID. SUNY Delhi does not have paper FAFSAs List SUNY Delhi on your FAFSA. Our Federal school code is 002857. Complete a Tuition Assistance Program (TAP) application (New York State residents only) at https://www.tapweb.org. Be sure to list the correct SUNY Delhi's TAP code: 3020 for certificate and associate degree programs 6020 for bachelor's degrees. Review your financial aid awards on the Bronco Web. SUNY Delhi will send you all forms, applications, and instructions needed to complete your aid, including student and parent loans. Read and follow all directions carefully. Respond promptly to all requests from SUNY Delhi for additional information. Use http://www.hesc.ny.gov to check the status of your TAP awards. Use www.studentloans.gov to check the status of your federal direct loans. Track your progress using the Financial Aid Checklist (Adobe Acrobat Reader required) Contact us if you have questions: 1-800-96-DELHI, 1-607-746-4570 or [email protected] .