NC State University Campus Calendar and Email Initiative Appendix C Email System Inventory Summary
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

Toward an Automated Vulnerability Comparison of Open Source IMAP Servers Chaos Golubitsky – Carnegie Mellon University
Toward an Automated Vulnerability Comparison of Open Source IMAP Servers Chaos Golubitsky – Carnegie Mellon University ABSTRACT The attack surface concept provides a means of discussing the susceptibility of software to as-yet-unknown attacks. A system’s attack surface encompasses the methods the system makes available to an attacker, and the system resources which can be used to further an attack. A measurement of the size of the attack surface could be used to compare the security of multiple systems which perform the same function. The Internet Message Access Protocol (IMAP) has been in existence for over a decade. Relative to HTTP or SMTP, IMAP is a niche protocol, but IMAP servers are widely deployed nonetheless. There are three popular open source UNIX IMAP servers – UW-IMAP, Cyrus, and Courier-IMAP – and there has not been a formal security comparison between them. In this paper, I use attack surfaces to compare the relative security risks posed by these three products. I undertake this evaluation in service of two complementary goals: to provide an honest examination of the security postures and risks of the three servers, and to advance the study of attack surfaces by performing an automated attack surface measurement using a methodology based on counting entry and exit points in the code. Introduction Contributions and Roadmap System administrators frequently confront the The paper makes two major contributions. First, problem of selecting a software package to perform a I undertake an in-depth discussion of the relative secu- desired function. Many considerations affect this deci- rity postures of the three major open source IMAP sion, including functionality, ease of installation, soft- servers in use today. -

Dynamic Allocation of Mail Server Resources Among Users
INTERNATIONAL JOURNAL OF SCIENTIFIC & TECHNOLOGY RESEARCH VOLUME 9, ISSUE 03, MARCH 2020 ISSN 2277-8616 Dynamic Allocation Of Mail Server Resources Among Users Basti M.Aliyeva Index:The article was dedicated to the solution of the problem on the dynamic allocation of mail server resources among users. It was noted that recently the electronic mail system had undergone serious changes and new features have been added to this system. The article examines the working principles of email and defines possible operating modes for subscribers. It was noted that mail server memory should be dynamically allocated among users so that the email can successfully perform its functions. In the article,the linear programming is applied to the problem of dynamic allocation of mail server memory. Known methods at every operation can resolve this issue.Proximity measure has been defined based on the Levenstein Distance (LD) for the determination of the renewal of documents on the server to improve the use of the server resources. This tool can be used to determine whether the documents have changed on the server.In the result, similar documents can be identified, and their number can be reduced up to one. Key Words: email server, dynamic allocation of the memory, operating modes of subscribes, Levenstein Distance (LD), Measures of document proximity. ———————————————————— 1. INTRODUCTİON information networks. In this case, it is essential to pay It is known that e-mail is one of the most important special attention to data transmission issues.Numerous information resources of the Internet, as well as it is the ways to transmit data and many software tools have been most massive communication tool. -

Design and Management of Email Service
Design and Management of Email Service Source : homepage.ntu.edu.tw/~jsc/2005-mail.ppt Outline Introduction to the architecture and operation of SMTP Design of a suitable email system – Webmail solutions Postfix and simple configuration samples Spam and virus filtering Conclusion 2 Overview Electronic mail service has already evolved into one of the major Internet applications. It is not only fundamental, but also a must. Users may become impatient when mails were delayed, not to mention failed to access their emails. – Imagine we meet the situation of power failure or cut of water supply 3 Architecture of a Simple Mail System Consists of the following components – MTA - Mail transfer agent Sending and forwarding emails Server end – MDA - Mail delivery agent Delivering emails to recipients’ mailbox Server end – Pop3/Imap4 Daemons For users to download their mailboxs Server end – MUA - Mail user agent Reading and composing emails 4 Client end Architecture of a Simple Mail System Protocols Used for Mail System Protocols – For computer programs to communicate with each other – Similar to languages that human beings speak SMTP – Simple Mail Transfer Protocol – Too simple to provide any “advanced features” Authentication Authorization POP3 – Post Office Protocol version 3 – Simple IMAP4 – Internet Message Access Protocol version 4 – Fully compatible with internet message standards, e.g. MIME. – Allow messages to be accessed from more than one computer. – Provide support for online, offline, and disconnected modes. 6 – Multiple and share folders. Mail Forwarding Between Servers How to Find the Way to the Destination? How do we find the way to [email protected]? 8 DNS: The Key to All Internet Services Query DNS server by the address part of email address.([email protected]) 1. -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -
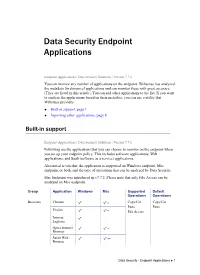
Data Security Endpoint Applications
Data Security Endpoint Applications Endpoint Applications | Data Security Solutions | Version 7.7.x You can monitor any number of applications on the endpoint. Websense has analyzed the metadata for dozens of applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 8 Built-in support Endpoint Applications | Data Security Solutions | Version 7.7.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy. This includes software applications, Web applications, and SaaS (software as a service) applications. Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by Data Security. Mac Endpoint was introduced in v7.7.2. Please note that only File Access can be analyzed on Mac endpoint. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome * Copy/Cut Copy/Cut Paste Paste Firefox * File Access Internet Explorer Opera Internet * Browser Safari Web ** Browser Data Security - Endpoint Applications 1 Data Security Endpoint Applications Group Application Windows Mac Supported Default Operations Operations CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility -
Malware: Computer Viruses, Spyware, and Key-Loggers
Certificates for cs.washington.edu 1 Certificates for GMail Important fields: Testing SSL Configuration (1) 3 Client completed verification of received certificate chain Testing SSL Configuration (2) 4 Received certificate chain (two certificates) Size of received certificate chain Testing SSL Configuration (3) 5 Issued session identifier (Session-ID) for stateful TLS resume. Example from “High Performance Browser Networking” Where to Use SSL? 6 Login page? Where else? What about JavaScript includes? Image includes? Why not encrypt everything? Where to Use SSL? 7 Some browsers may not support SSL SSL may decrease performance somewhat. If users are downloading large, public files, there may be a system burden to encrypt these each time. You will probably want the home page accessible via HTTP, so that users don't have to remember to type https to get to it. Firesheep (2010) 8 Assume you are using the facebook.com site over an unsecured Wi-Fi network such as in shopping malls and coffee shops. When you visit the Facebook site, you are required to enter the username and password. When you send that request and on successful login, Facebook sends you an authentication token in the clear which is then sent every time you browse Facebook pages Firesheep 9 Facebook Switches to HTTPS in 2012 10 Lab-2 11 Part 1 Part 2 Black-box fuzzing is far C programming is tricky from easy Bounds are far from obvious even when Very little insight into reasoning about a short program behavior function Makes you appreciate Makes you appreciate programming in Java or having access to C# where array accesses source code! are checked at runtime! Lab-2: Survey 12 Part 1 Part 2 A. -

Open Ajax" to Drive Collaborative Innovation to Make the Web Easier to Use
TECH TITANS PROPOSE OPEN SOURCE PROJECTS FOR BROWSER-BOOSTING AJAX TECHNOLOGY "Open Ajax" to Drive Collaborative Innovation to Make the Web Easier to Use Armonk, NY, February 1, 2006 . Prominent computer industry vendors and Internet-based businesses today announced that they are making it easier for an open-source community to form and popularize Ajax. Ajax is a fast-growing open client technology that businesses are incorporating into their external and internal Web sites to simplify the browsing experience, and make it easier for users to shop, work, plan, correspond and navigate online. Ajax makes it unnecessary to manually refresh one's browser to send or receive information over the Web. Instead, information is automatically updated and available on demand, allowing you to "drag and drop" or input information and get a response without refreshing the browser, much like you would do on a PC desktop. It can reduce the steps needed to complete a transaction over the Web or create a competitive edge for enterprise companies and Web designers, for example. The initial supporting members of the new initiative -- dubbed Open Ajax -- include BEA, Borland, the Dojo Foundation, Eclipse Foundation, Google, IBM, Laszlo Systems, Mozilla Corporation, Novell, Openwave Systems, Oracle, Red Hat, Yahoo, Zend and Zimbra. They intend to promote Ajax's promise of universal compatibility with any computer device, application, desktop or operating system, and easy incorporation into new and existing software programs. Ajax -- short for Asynchronous JavaScript and XML -- is a type of "Rich Internet Application." It enables Web innovations, including: * The ability to update portions of a Web page without refreshing the entire screen. -

FTP Server PURE-FTPD 1
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Digital library of Brno University of Technology VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ ÚSTAV INFORMAČNÍCH SYSTÉMŮ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INFORMATION SYSTEMS SOFTWARE PRE PODPORU WEBHOSTINGU BAKALÁŘSKÁ PRÁCE BACHELOR´S THESIS AUTOR PRÁCE MIROSLAV HULA AUTHOR BRNO 2009 VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ ÚSTAV INFORMAČNÍCH SYSTÉMŮ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INFORMATION SYSTEMS SOFTWARE PRO PODPORU WEBHOSTINGU WEBHOSTING MANAGEMENT SOFTWARE BAKALÁŘSKÁ PRÁCE BACHELOR´S THESIS AUTOR PRÁCE MIROSLAV HULA AUTHOR VEDOUCÍ PRÁCE Ing. PETR WEISS SUPERVISOR BRNO 2009 Abstrakt Cieľom práce je vytvoriť software pre podporu webhostingu, čo znamená, vytvoriť systém umožňujúci užívateľom vytváranie si vlastných subdomén v doméne, využívanie emailovej služby, zabezpečenie prístupu k FTP serveru a k databázovému serveru. Obsluha služieb užívateľom musí prebiehať pomocou grafického užívateľského rozhrania podobne, ako aj samotná registrácia do tohto systému. Klúčové slová GNU/Linux, Apache HTTP Server, MySQL Server, PHP: Hypertext Preprocessor, SMTP server, POP3/IMAP Server, FTP Server, webhosting, virtuálni užívatelia Abstract The main goal of this thesis is to create a software tool to support webhosting, it means to create a system that provides email services, services of an FTP server and database server, and allows users to create their own subdomains within the domain. Moreover, the system must provide a graphical interface for its users. Keywords GNU/Linux, Apache HTTP Server, MySQL Server, PHP: Hypertext Preprocessor, SMTP server, POP3/IMAP Server, FTP Server, webhosting, virtual users Citácia Miroslav Hula: Software pre podporu webhostingu, bakalářská práce, Brno, FIT VUT v Brně, 2009 Software pre podporu webhostingu Prehlásenie Čestne prehlasujem, že som túto bakalársku prácu vypracoval samostatne pod vedením pána Ing. -

C3000 Microsoft Outlook User Manual
C3000 Microsoft Outlook User Manual Rel. 1.7 SP2 18-11-2008 © 2008 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and accurate at the time of printing, Avaya Inc. can assume no liability for any errors. Changes and corrections to the information in this document may be incorporated in future releases. For full legal page information, please see the complete document, Avaya Legal Page for Software Documentation, Document number 03-600758. To locate this document on the website, simply go to http://www.avaya.com/support and search for the document number in the search box. Documentation disclaimer Avaya Inc. is not responsible for any modifications, additions, or deletions to the original published version of this documentation unless such modifications, additions, or deletions were performed by Avaya. Customer and/or End User agree to indemnify and hold harmless Avaya, Avaya's agents, servants and employees against all claims, lawsuits, demands and judgments arising out of, or in connection with, subsequent modifications, additions or deletions to this documentation to the extent made by the Customer or End User. Link disclaimer Avaya Inc. is not responsible for the contents or reliability of any linked Web sites referenced elsewhere within this documentation, and Avaya does not necessarily endorse the products, services, or information described or offered within them. We cannot guarantee that these links will work all of the time and we have no control over the availability of the linked pages. Warranty Avaya Inc. provides a limited warranty on this product. -

Server Administration
Server administration Remo Suppi Boldrito PID_00148466 GNUFDL • PID_00148466 Server administration Copyright © 2009, FUOC. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License" GNUFDL • PID_00148466 Server administration Index Introduction............................................................................................... 5 1. Domain name system (DNS)............................................................ 7 1.1. Cache names server .................................................................... 7 1.2. Forwarders ................................................................................... 10 1.3. Configuration of an own domain .............................................. 11 2. NIS (YP)................................................................................................. 14 2.1. ¿How do we initiate a local NIS client in Debian? ..................... 14 2.2. What resources must be specified in order to use NIS? .............. 15 2.3. How should we execute a master NIS server? ............................ 16 2.4. How should we configure a server? ............................................ 17 3. Remote connection services: telnet and ssh............................... 19 3.1. Telnet and telnetd -

Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM
Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM Sign In Sign-Up We have copied this page for reference in case it disappears from the web. The copyright notice appears at the end. If you want the latest version go to the original page: http://www.expita.com/nomime.html Turning Off HTML or MIME to use a Remailer System. Index (5 topics) Introduction E-mail client programs (Turning Off HTML or MIME to use a Remailer System) Suggestions for HTML users Examples of HTML/MIME messages References What is wrong with sending HTML or MIME messages? There are now six main reasons for NOT doing this: 1. Many E-mail and Usenet News reader programs, usually the mail and news reader programs that come with browser packages, allow users to include binary attachments (MIME or other encoding) or HTML (normally found on web pages) within their E-mail messages. This makes URLs into clickable links and it means that graphic images, formatting, and even color coded text can also be included in E-mail messages. While this makes your E-mail interesting and pretty to look at, it can cause problems for other people who receive your E- mail because they may use different E-mail programs, different computer systems, and different application programs whose files are often not fully compatible with each other. Any of these can cause trouble with in-line HTML (or encoded attachments). Most of the time all they see is the actual HTML code behind the message. And if someone replies to the HTML formatted message, the quoting can render the message even more unreadable.