Acceptable Use of Information Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interprofessional Learning in Rural South‐East New South Wales: an Opportunity to Collaborate Across Educational Institutions, Health Disciplines and Health Services
Interprofessional learning in rural south‐east New South Wales: an opportunity to collaborate across educational institutions, health disciplines and health services Pippa Craig1, Ian Goater2, Daniel Heard3, John Sullivan3, Eva Taylor4, Amanda Barnard5 1Inter‐Professional Learning, ANU Medical School, 2ANU Rural Clinical School, Bega, 3ANU Medical School, 4Tulgeen Disability Services, Bega, 5Rural Clinical School, ANU Medical School Dr Ian Goater has a MBBS Melbourne University 1976, MPH Monash University 1989, Fellowship Australasian College of Occupational Medicine 1989. Clinically Dr Goater initially worked in general practice and later as an occupational physician before becoming a rural general practitioner in 1999. He has been the Academic Coordinator, Bega Node, Rural Clinical School, ANU College of Medicine, Biology and Environment since 2004. Daniel Heard is a final year medical student at the Australian National University Medical School. Born in rural north Queensland and moving to Canberra as a teenager, as an undergraduate he completed a Bachelor of Science/Bachelor of Laws majoring in immunology and genetics at the ANU. He then worked for several years as an IT consultant to government, creating legal decision support systems to assist organisations to comply with complex areas of law. One of the systems he designed is the Australian Department of Immigration’s international award winning ‘Visa Wizard’, which is used by 2 million people a month to determine the Australian visa they should apply for. He has also worked as a freelance science journalist, writing pieces for the Australian Academy of Science’s ‘Nova—science in the news’ series and ‘Velocity’, the Australian Nuclear Science and Technology Organisation’s online science magazine. -

Medicine at Anu
MEDICINE AT ANU ANU College of Medicine, Biology & Environment We are the best uni in Australia* CONTENTS Welcome 2 Why study at ANU? 4 Why Canberra? 6 Your ANU experience 8 We are the Your future 10 Your opportunities 12 Your medical degree 14 Your application 16 Admissions information 18 best uni in Scholarships 20 Your research 22 * Our research areas 24 Australia * QS 2017 World University Rankings Medicine at ANU 1 WELCOME We have stood in your shoes All of the doctors teaching at The Australian National University (ANU) Medical School, myself included, know that choosing a medical school is a big deal. Having been through the process ourselves, and being still tied to our respective schools through alumni networks and the indelible memories of our impressionable years as a medical student, we are very aware of the critical importance of this decision. So it is not lightly that I recommend the ANU Medical School. It is in the full knowledge that this is a big deal for you. You are, after all, entrusting your indelible memories to us. But I can say, with confidence and great pride, that we are the right choice. You will find at the ANU Medical School the support you need to get through what will be a tough four years, and graduate as the kind of doctor you want to be. You will not be lost in the crowd here. Your teachers will be your mentors, your classmates will be your best friends, and your new city will be your home. The best of luck to you as you begin your journey to becoming a doctor. -

Conferring of Awards 10, 11, 12 & 13 December 2019
CONFERRING OF AWARDS 10, 11, 12 & 13 DECEMBER 2019 Australian National Anthem Advance Australia Fair Australians all let us rejoice, For we are young and free; We’ve golden soil and wealth for toil; Our home is girt by sea; Our land abounds in nature’s gifts Of beauty rich and rare; In history’s page let every stage Advance Australia Fair. In joyful strains then let us sing, Advance Australia Fair. CONFERRING OF AWARDS Summer 2019 Llewellyn Hall The Australian National University Tuesday 10 December Wednesday 11 December Thursday 12 December Friday 13 December Chancellor: Professor the Honourable Gareth Evans AC QC BA LLB (Hons) Melb, MA Oxon, HonLLD Melb, Carleton, Syd FASSA Pro-Chancellor: Ms Naomi Flutter MPP Harvard, LLB (Hons), Bec (Hons), GDLP ANU Vice-Chancellor: Professor Brian P. Schmidt AC FAA FRS 2011 Nobel Laureate Physics BSc (Physics) Arizona, BSc (Astronomy) Arizona, MA (Astronomy) Harvard, PhD Harvard Esquire Bedel: Dr Ian Walker BA DipEd Syd, MA Macq, PhD UNSW University Marshal and Esquire Bedel: Ms Lorena Kanellopoulos DipHRM, GradCertMgt, MMgt ANU Mr Jake Francis Published by The Australian National University Conferring of Awards December 2019 1 CHANCELLOR’S MESSAGE TO GRADUANDS Today’s ceremony marks the culmination of years of research and study. ANU owes much to the intellectual and cultural contribution of our student body. In return, we work to build on our high standards in research and education. The ANU was created as part of a great nation building exercise in its day. That mandate continues and you share a vital part in it. -

International Undergraduate Student Guide Vice-Chancellor’S Message Vice-Chancellor’S Message
2010 INTERNATIONAL UNDERGRADUATE STUDENT GuiDE VICE-Chancellor’s Message Vice-Chancellor’s message I am very pleased you are exploring all that Our links with leading universities in Asia, Australia’s national university has to offer. Europe, the UK and the United States provide Your decision about which university to opportunities for collaboration and exchange attend is an important one. It needs to be that enrich the experience of our students, as well informed as possible. This guide is and broaden research avenues for staff. designed to help you make a sound choice. Our study programs cater to high-achieving To begin your introduction to The Australian students; to students who want industry National University (ANU) I’d like to experience as part of their degree; and to emphasise some of the things that set our students looking for the opportunity to University apart. study in two disciplines, through our popular double degree programs. All ANU students ANU is consistently ranked as Australia’s top graduate with a distinctive degree from a university and among the best universities respected university. in the world. The researchers and educators who made this possible are the same As Australia’s national university, ANU people who will teach you and shape the also offers the special focus that stems intellectual climate in which you will learn. from its unique relationship with the Australian government and its national and With fewer students and more academics, international roles. and many of our students living in university accommodation, our campus I encourage you to explore the 2010 affords a highly supportive, interactive and International Undergraduate Student Guide social learning environment. -

Science, Health & Medicine
SCIENCE, HEALTH & MEDICINE ANU Colleges of Science Health & Medicine CONTENTS Introduction 2 Biology 22 Medical research 34 How we work together 4 X marks the When neurons go wrong conservation hotspot Strong international 6 Physics 36 connections Chemistry 24 Crystal-clear future for Fighting bacteria quantum computing World-class facilities 8 with funky peptides Population health 38 Our alumni 10 Clinical research 26 Working together for Excellence in teaching 12 Working together Indigenous health and learning for weight loss Psychology 40 Undergraduate studies 14 Earth sciences 28 The fact of the matter Rocky start solves Science communication 42 Postgraduate 16 a mystery coursework Us and science: Environment and society 30 it’s complicated Postgraduate research 18 How the water runs Science, medicine 44 Astronomy and 20 Mathematics 32 and health at a glance astrophysics The explosive impact Contact us Back cover Telescopic view on history of maths b 1 Our academics produce research that changes lives, and life as we know it. Collecting rock samples from among the red dust of Central Our students learn from these world-class researchers, Australia. as do Australia’s policy-makers, with our expertise and influence extending to our Canberra neighbours—leaders Scanning the night sky under cover of darkness at Siding in government and industry—and beyond. Spring Observatory. We are proud of our standing, our history and our Sitting with patients in the doctor’s office. achievements. In the past 70 years we have produced four At a lab bench, and in front of the classroom. Nobel Laureates, some of Australia’s most pre-eminent scientists and thousands of graduates with a world-class You’ll find our researchers at the forefront of scientific practice education in science, environment, medicine and health. -
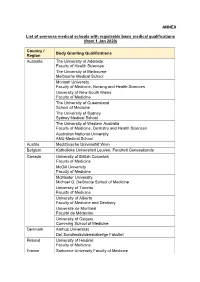
ANNEX List of Overseas Medical Schools with Registrable Basic
ANNEX List of overseas medical schools with registrable basic medical qualifications (from 1 Jan 2020) Country / Body Granting Qualifications Region Australia The University of Adelaide Faculty of Health Sciences The University of Melbourne Melbourne Medical School Monash University Faculty of Medicine, Nursing and Health Sciences University of New South Wales Faculty of Medicine The University of Queensland School of Medicine The University of Sydney Sydney Medical School The University of Western Australia Faculty of Medicine, Dentistry and Health Sciences Australian National University ANU Medical School Austria Medizinische Universität Wien Belgium Katholieke Universiteit Leuven, Faculteit Geneeskunde Canada University of British Columbia Faculty of Medicine McGill University Faculty of Medicine McMaster University Michael G. DeGroote School of Medicine University of Toronto Faculty of Medicine University of Alberta Faculty of Medicine and Dentistry Université de Montréal Faculté de Médecine University of Calgary Cumming School of Medicine Denmark Aarhus Universitet Det Sundhedsvidenskabelige Fakultet Finland University of Helsinki Faculty of Medicine France Sorbonne University Faculty of Medicine Country / Body Granting Qualifications Region Germany Ruprecht-Karls-Universität Heidelberg Medizinische Fakultät Heidelberg Ludwig-Maximilians-Universität München Medizinische Fakultät Charité-Universitätsmedizin Berlin Hong Kong The Chinese University of Hong Kong Special Faculty of Medicine Administrative The University of Hong Kong Region, -

Melbourne Health Research Week 2015 Letter from the Executive Director of Research Welcome to Research Week 2015
Melbourne Health Research28 May – 4 June 2015Week Melbourne Health Research Week 2015 Letter from the Executive Director of Research Welcome to Research Week 2015. In this increasingly popular annual event we showcase the advances in health and medical research described through exploration of the research question. This year’s program provides a sample of the abundant number of Melbourne Health research activities. Dr Leonie Walsh, Lead Scientist for Victoria, will open the event at the opening plenary session on Thursday 28 May. Titled “A Brain Storm – RMH Neuroscience Newsmakers”, this session focuses on one of Melbourne Health’s strengths. Each of the three presenters, Helmut Butzkueven, Mark Walterfang and Bruce Campbell, are leaders in their disciplines and we take this opportunity to acknowledge and celebrate the outstanding recent highlights of their work. Activities continue throughout the week with a range of research education and information sessions. The research symposium will have parallel sessions of original research, along with poster viewing, and we encourage you to attend these events to learn more about our research, and support those presenting their work. This year we will host a hypothetical “Developing new therapies: Pipelines or Pipedreams?” which promises to be enlightening and entertaining. The closing plenary on 4 June will showcase the cardiology research at MH, to be presented by Tomos Walters, followed by our prize-giving session. I would like to thank the efforts of those involved in reviewing abstracts and posters and the session chairs during Research Week. Your time and expertise is greatly appreciated. I would also like to thank the Research Week Committee for compiling an exciting program and for all the work that goes into making this event such a success. -

AMA ACT Welcomes the ANU Medical School Students
February 2012 Canberra Doctor is proudly brought to you by the AMA (ACT) Limited Circulation: 1,900 in ACT & region AMA ACT welcomes the ANU Medical School students The annual AMA ACT welcoming reception for new medical students at the ANU Medical School was held at “Barocca” on Thursday 9 February. AMA President, Dr Steve Hambleton, with AMSA President, Mr James Churchill and Mr Mark Russell ANU Medical School representative to the AMA ACT Advisory Council Host AMA ACT President, Dr Iain Dunlop and Chair of the Advisory Council, Dr Andrew Miller with new students. The event was generously sponsored by Investec. Dr Iain Stewart | Dr Malcolm Thomson | Dr Nicholas Kenning | Dr Damien Hoon | Dr Karen Falk | Dr Mike McKewen Dr Robert Greenough | Dr Fred Lomas | Dr Paul Sullivan National Capital 24-hour guarantee on Ultrasound Diagnostic Imaging and CT appointments* Just another way we can provide a better service *Provided doctor not required. Excludes interventional procedures, MSK Ultrasound & cardiac CT A member of the I-Med Network Woden 6214 2222 Deakin 6124 1900 Tuggeranong 6293 2922 Geils Court 6122 7878 February 2012 Volume 24, No. 1 The State of the Territory Beginnings only 20 hours of CPD annually, and attended negotiations. You In the same vein, consultation Last week 91 new medical stu- ‘qualification’ in Chinese Medicine should note that the AMA ACT is has commenced on the ACT dents began training at ANU as merely evidence of 5 years of the truly independent party at the Palliative Care Strategy and Services Medical School. I met many of practice since 2002 and no require- table. -

Annual Report 2011 Annual Report 2011 Annual Report
THE AUSTRALIAN NATIONAL UNIVERSITY THE AUSTRALIAN NATIONAL ANNUAL REPORT 2011 ANNUAL REPORT 2011 ANU in 2011 | Annual Report 2011 1 2 Annual Report 2011 | ANU in 2011 ANNUAL REPORT 2011 Further information about ANU www.anu.edu.au Course and other academic information: Registrar, Division of Registrar and Student Services The Australian National University Canberra ACT 0200 T +61 2 6125 3339 F +61 2 6125 0751 General information: Director, Marketing Office The Australian National University Canberra ACT 0200 T +61 2 6125 2252 Published by: The Australian National University twitter.com/anumedia facebook.com/TheAustralianNationalUniversity youtube.com/anuchannel ISSN 1327-7227 April 2012 MO_12011 4 Annual Report 2011 | ANU in 2011 CONTENTS ANU IN 2011 An introduction from the Vice-Chancellor 8 2011 snapshot 10 Annual results and sources of income 13 Education 15 Research 27 Government initiatives 34 Community engagement 38 International relations 40 Infrastructure development 43 REVIEW OF OPERATIONS Staff 48 Governance and Freedom of Information 51 Academic structure of the University 52 Functions of the University’s statutory officers 57 Freedom of Information 58 Governance 55 ANU Council and University Officers 60 University Officers 62 Officers for Ceremonial Occasions 66 Council and Council Committees 67 Risk management 70 Indemnities 73 Access 74 A safe, healthy and sustainable work environment 78 The environment 81 FINANCIAL INFORMATION Audit report 86 Statement by the Council 89 Financial statements 90 Glossary 152 ANU in 2011 | Annual Report 2011 5 6 Annual Report 2011 | ANU in 2011 VICE-CHANCELLOR ANU in 2011 | Annual Report 2011 7 8 Annual Report 2011 | ANU in 2011 ANU IN 2011 ANU in 2011 | Annual Report 2011 9 AN INTRODUCTION FROM THE VICE-CHANCELLOR This plan defines two broad goals for the University: to be Australia’s national university and Australia’s finest university. -
Annual Report 2009 FURTHER INFORMATION ABOUT ANU Detailed Information About ANU Is Available from the University’S Website
ANNUAL REPORT 2009 FURTHER INFORMATION ABOUT ANU Detailed information about ANU is available from the University’s website: www.anu.edu.au For course and other academic information, contact: Registrar, Division of Registrar and Student Services The Australian National University Canberra ACT 0200 T: +61 2 6125 3339 F: +61 2 6125 0751 For general information, contact: Director, Marketing Office The Australian National University Canberra ACT 0200 T: +61 2 6125 2252 F: +61 2 6125 5568 Published by: The Australian National University Produced by: ANU Marketing Office The Australian National University Printed by: University Printing Service The Australian National University ISSN 1327-7227 June 2010 ANU ANNUAL REPORT 2009 ii CONTENTS PART 1 / ANU IN 2009 An Introduction by the Vice-Chancellor 2 ANU College Profile 6 Annual Results and Sources of Income 8 Education 9 Research 18 Community Engagement 23 International Relations 25 Infrastructure Development 27 PART 2 / REVIEW OF OPERATIONS Staff 32 Governance and Freedom of Information 35 ANU Council and University Officers 44 Council and Council Committees 52 Risk Management 55 Indemnities 56 Access 57 A Safe, Healthy and Sustainable Environment 60 The Environment 62 PART 3 / FINANCIAL INFORMATION Audit Report 67 Statement by Directors 69 Financial Statements 70 ANU ANNUAL REPORT 2009 iii PART 1 | ANU IN 2009 iv ANU ANNUAL REPORT 2009 v PART 1 ANU IN 2009 AN INTRODUCTION FROM THE VICE-CHANCELLOR Vice-Chancellor Professor Ian Chubb AC The Australian National University (ANU) was established in 1946. It was to be different from other Australian universities established by that time. The primary objective of ANU was to inject a substantial culture of research into Australia at a time when there was little but a need that was great. -

Director, Research School of Biology
INFORMATION FOR PROSPECTIVE ANUCANDIDATES wants you INFORMATION FOR PROSPECTIVE CANDIDATES Director, Research School of Biology ANU COLLEGE OF SCIENCEa The Australian National University INFORMATION FOR PROSPECTIVE CANDIDATES Welcome to ANU Thank you for considering the position of Director, Research School of Finance, Actuarial Studies and For over 72 years, the Australian National University has Contributing to the strategic vision of the University is StatisticsbeenHEADING the educational at the home Australian to some TO of the most NationalGO remarkable HERE the role of Director, Research School of Biology within people from across the world: visionaries, influential leaders, the ANU College of Science. As a member of the College Universityresearchers and individuals(ANU). creating impact and change Executive team, your strategic leadership will contribute to nationally, regionally and globally. advancing the University’s reputation as one of the world’s great universities. This, coupled with our role as the national university means we have a responsibility to be ambitious, bold and transformative We are looking for people who find true joy in research, in our approaches to teaching and learning. We are poised to in following an idea to see where it will lead because it is provide the next generation of leaders and global citizens with exciting. For teachers who know what it is to truly inspire the skills required for the challenges and jobs of the future. others, who take huge satisfaction in the moments where students finally understand a difficult concept or solve a The University is set in beautiful grounds close to the heart of great problem. We seek people with passion, who want to the city of Canberra and Parliament House. -

Annual Report 2017
THE AUSTRALIAN NATIONAL UNIVERSITY THE AUSTRALIAN NATIONAL ANNUAL REPORT 2017 ANNUAL REPORT 2017 We acknowledge the Traditional Owners and Elders past, present and emerging of all the lands on which The Australian National University operates. Naturam primum cognoscere rerum First, to learn the nature of things The Australian National University (ANU) was established by an Act of the Federal Parliament in 1946. Its founding mission was to be of enduring significance in the postwar life of the nation, to support the development of national unity and identity, to improve Australia’s understanding of itself and its neighbours, and to contribute to economic development and social cohesion. Today, ANU is a celebrated place of intensive research, education and policy engagement, focused on issues of national and international importance. ANU is a: > centre of outstanding academic talent and research excellence > home to a group of students drawn from across the nation and around the world > leading contributor to public policy formation and debate > partner to the Australian Government and parliament > global university that consistently ranks among the world’s finest education and research institutions. Annual Report 2017 1 Further information about ANU www.anu.edu.au Annual Report available online at http://www.anu.edu.au/about/plans-reviews Course and other academic information Student Recruitment The Australian National University Canberra ACT 2600 T +61 2 6125 3466 http://www.anu.edu.au/study General information Director, Strategic Communications