STAFFAN TUNIS REAL-TIME INDUSTRIAL ETHERNET in MACHINE AUTOMATION SYSTEMS Master of Science Thesis
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Introduction to Real-Time Ethernet II
the EXTENSION JULY–AUGUST A Technical Supplement to Control Network Volume 5 Issue 4 © 2004 Contemporary Control Systems, Inc. Introduction to Real-Time Ethernet II By Paula Doyle, a doctoral researcher with the Circuits and Systems Research Centre at the University of Limerick in Ireland INTRODUCTION IEEE 1588 defines two separate types of clocks: In “Real-Time Ethernet I”, we introduced the basic ordinary and boundary. Boundary clocks (BC) are concepts of Ethernet’s capacity to deliver a real-time employed in devices such as hubs or switches—where (RT) communication system. “Real-Time Ethernet II” more than one PTP communication path (port) exists. introduces some of the RT solutions available to Ordinary clocks exist in devices having a single port— e.g., normal network devices. Each BC port can act as industry today*: PROFInet, EtherCAT and ETHERNET Powerlink. It also provides an introduction to a single a master or ordinary clock in its own segment. standard, IEEE 1588 that is growing in popularity PTP is for networks that support multicasting but amongst RT Ethernet developers to provide sub- keep multicasts within a subnet and where each local microsecond synchronization accuracy of distributed clock fulfills exacting requirements. The grandmaster clocks over Ethernet. clock (GMC) is the best clock in the system—with the best inherent stability, accuracy, resolution, etc. * EtherNet/IP is included in the full article available at defined by the standard [2]. The Best Master Clock http://www.ccontrols.com/pdf/volume5n4.pdf Algorithm (BMC), run by every live node, determines IEEE 1588 clock quality. Within each subnet, the BMC determines the master clock; in a single-subnet system the master IEEE 1588 [1] specifies “A protocol to synchronize is the GMC. -

Ethercat – Ultra-Fast Communication Standard
EtherCAT – ultra-fast communication standard In 2003, Beckhoff introduces its EtherCAT tech- In 2007, EtherCAT is adopted as an IEC standard, EtherCAT: nology into the market. The EtherCAT Technology underscoring how open the system is. To this Group (ETG) is formed, supported initially by day, the specification remains unchanged; it has global standard 33 founder members. The ETG goes on to stan- only been extended and compatibility has been dardize and maintain the technology. The group is retained. As a result, devices from the early years, the largest fieldbus user organization in the world, even from as far back as 2003, are still interopera- for real-time with more than 5000 members (as of 2019) cur- ble with today’s devices in the same networks. rently. In 2005, the Safety over EtherCAT protocol Another milestone is achieved in 2016 Ethernet from the is rolled out, expanding the EtherCAT specification with EtherCAT P, which introduces the ability to to enable safe transmission of safety-relevant carry power (2 x 24 V) on a standard Cat.5 cable field to the I/Os control data. The low-footprint protocol uses a alongside EtherCAT data. This paves the way for so-called Black Channel, making it completely machines without control cabinets. independent of the communication system used. The launch of EtherCAT G/G10 in 2018 in- How it works The key functional principle of EtherCAT lies in how its nodes process Ethernet frames: each node reads the data addressed to it and writes its data back to Flexible topology the frame all while the frame is An EtherCAT network can sup- moving downstream. -

Ethercat the New Standard for Measurement Applications Central Backbone for Distributed Systems
C5.2 EtherCAT The new standard for measurement applications Central backbone for distributed systems Dr. Kessel, Jens-Achim ADDITIVE Soft- und Hardware für Technik und Wissenschaft GmbH Max-Planck-Str. 22b, 61381 Friedrichsdorf Abstract In the past years EtherCAT has become a world wide accepted new standard in automation and control. In November 2003 the EtherCAT Technology Group (ETG) was founded and it has grown up to about 900 members from 45 countries in January, 2009. EtherCAT was designed and developed as an open high performance Ethernet-based fieldbus system. The development goal of EtherCAT was to apply Ethernet technology to automation applications which require short data update times (also called cycle times) with low communication jitter (for synchronization purposes) and low hardware costs. Once the new standard was introduced for automation and control, it became interesting, too, to use Eth- erCAT also for distributed systems in measurement applications. This paper takes a focus on the special properties of EtherCAT with respect to the usability in measure- ment applications. It shows the capabilities of EtherCAT as a powerful backbone, replacing classical net- works based on CAN or ProfiBUS. In particular aspects of synchronisation and real-time-processing in combination with the compact data packaging are interesting for measurement applications with a big number of distributed analog channels. E.g. in applications where torque and speed of rotating parts are picked up just to measure, to detect or even to prevent oscillations, it is very important to synchronize the sampling of data at the distributed converter modules. Only this allows then to calculate exact phase in- formation from the measured signals and evaluate and prepare the data according to the requirements of an application on top. -

AKD Canopen Manual English
RGM® CAN-BUS Communication Edition: A, October 2017 Original Documentation For safe and proper use, follow these instructions. Keep them for future reference. RGM CANopen | Record of Document Revisions Revision Remarks A, 10/2017 Launch version Technical changes which improve the performance of the device may be made without prior notice! Printed in the United States of America This document is the intellectual property of Kollmorgen. All rights reserved. No part of this work may be reproduced in any form (by photocopying, microfilm or any other method) or stored, processed, copied or distributed by electronic means without the written permission of Kollmorgen. 2 Kollmorgen | kdn.Kollmorgen.com | October 2017 RGM CANopen | 1 Table of Contents 1 Table of Contents 1 Table of Contents 3 2 About This Manual 18 2.1 Overview and Scope 18 2.1.0.1 Copyrights 18 2.1.0.2 Document Validity 18 2.2 Product Warnings 18 2.3 References 18 2.3.1 Defining Documents 18 2.3.1.1 CiA 301: CANopen Application Layer and Communication Profile 18 2.3.1.2 CiA 402 Part 1: Device Profile for Drives and Motion Control, General Definitions 18 2.3.1.3 CiA 402 Part 2: Device Profile for Drives and Motion Control, Operation Modes and Application Data 18 2.3.1.4 CiA 402 Part 3: Device Profile for Drives and Motion Control, PDO Mapping 19 2.3.1.5 IEC 61800-7-1: Adjustable Speed Power Drive Systems 19 2.3.1.6 IEC 61800-7: ETG Implementation Guideline for the CiA402 Drive Profile 19 2.4 Object Description Conventions 19 Transmit PDO Communication Parameters - Index 0x1800 -

AKD Ethercat Manual English
AKD™ EtherCAT Communication Edition: A, July 2010 Valid for Hardware Revision A Part Number 903-200005-00 Original Documentation Keep all manuals as a product component during the life span of the product. Pass all manuals to future users and owners of the product. Kollmorgen Record of Document Revisions: Revision Remarks -, 11/2009 Beta launch version -, 12/2009 Minor formatting changes A, 07/2010 FBUS.PARAM04 added, part number added, page format, release information Hardware Revision (HR) Hardware Revision Firmware WorkBench A M_01-03-zz-zzz 1.2.0.zzzzz EnDat is a registered trademark of Dr. Johannes Heidenhain GmbH EtherCAT is a registered trademark of EtherCAT Technology Group HIPERFACE is a registered trademark of Max Stegmann GmbH WINDOWS is a registered trademark of Microsoft Corporation AKD is a registered trademark of Kollmorgen™ Corporation Current patents: US Patent 5,646,496 (used in control card R/D and 1 Vp-p feedback interface) US Patent 5,162,798 (used in control card R/D) US Patent 6,118,241 (used in control card simple dynamic braking) Technical changes which improve the performance of the device may be made without prior notice! Printed in the United States of America This document is the intellectual property of Kollmorgen™. All rights reserved. No part of this work may be reproduced in any form (by photocopying, microfilm or any other method) or stored, processed, copied or dis- tributed by electronic means without the written permission of Kollmorgen™. 2 Kollmorgen | July 2010 AKD EtherCAT | Table of Contents Table -

Ethercat Communication Manual
Specialized Vision Sensor for Positioning FZM1 Series EtherCAT Communication Manual Cat. No. Q179-E1-01 Trademarks and Copyrights • EtherCAT is a registered trademark of Beckhoff Automation GmbH (Germany). EtherCAT technology is protected by patents. • Other system names and product names that appear in this manual are the trademarks or registered trademarks of the relevant companies. © OMRON, 2010 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form, or by any means, mechanical, electronic, photocopying, recording, or otherwise, without the prior written permission of OMRON. No patent liability is assumed with respect to the use of the information contained herein. Moreover, because OMRON is constantly striving to improve its high-quality products, the information contained in this manual is subject to change without notice. Every precaution has been taken in the preparation of this manual. Nevertheless, OMRON assumes no responsibility for errors or omissions. Neither is any liability assumed for damages resulting from the use of the information contained in this publication. Contents 1 What Is EtherCAT?.....................................................................................................1 1-1 Outlines of EtherCAT .......................................................................................................1 Features of EtherCAT ..................................................................................................1 EtherCAT Mechanism -

Ethercat Sensor Communication Unit
E3X-ECT EtherCAT Sensor Communication Unit Operation Manual E413E1 OMRON, 2012 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form, or by any means, mechanical, electronic, photocopying, recording, or otherwise, without the prior written permission of OMRON. No patent liability is assumed with respect to the use of the information contained herein. Moreover, because OMRON is con- stantly striving to improve its high-quality products, the information contained in this manual is subject to change without notice. Every precaution has been taken in the preparation of this manual. Nevertheless, OMRON assumes no responsibility for errors or omissions. Neither is any liability assumed for damages resulting from the use of the information contained in this publication. E3X-ECT EtherCAT Sensor Communication Units Operation Manual Revised February 2012 Introduction Thank you for purchasing a E3X-ECT EtherCAT Sensor communication Unit. This manual contains information you need to know to use the EtherCAT Slave Unit. Before use, please make sure that you thoroughly read the manual and have a full understanding of the products functions and performance. After you finished reading this manual, please keep it in a convenient place. Intended Readers This manual is intended for the following individuals. Those having electrical knowledge (certified electricians or individuals having equivalent knowledge) and also being qualified for one of the following: • Introducing FA equipment • Designing FA systems • Managing FA sites E3X-ECT EtherCAT Sensor Communication Unit Instraction Manual 1 How to Read the Manual Page Structure This manual's page structure consists of the following. -

Sercos III Slave for Am437x — Communication Development Platform
TI Designs Sercos III Slave For AM437x — Communication Development Platform TI Designs Design Features Industrial Ethernet for Industrial Automation exists in • Sercos III Slave Firmware for PRU-ICSS With more than 20 industrial standards. Some of the well- Sercos MAC-Compliant Register Interface established real-time Ethernet protocols like EtherCAT, • Board Support Package and Industrial Software EtherNet/IP, PROFINET, Sercos III, and PowerLink Development Kit Available From TI and Third-Party require dedicated MAC hardware support in terms of Stack Provider FPGA or ASICs. The Programmable Real-Time Unit inside the Industrial Communication Subsystem (PRU- • Development Platform Includes Schematics, BOM, ICSS), which exists as a hardware block inside the User’s Guide, Application Notes, White Paper, Sitara processors family, replaces FPGA or ASICS Software, Demo, and More with a single chip solution. This TI design describes • PRU-ICSS Supports Other Industrial the Sercos III slave solution firmware for PRU-ICSS. Communication Standards (For Example, EtherCAT, PROFINET, EtherNet/IP, Ethernet Design Resources POWERLINK, Profibus) • PRU-ICSS Firmware is Sercos III Conformance TIDEP0039 Design Folder Tested TMDXIDK437X Tools Folder AM4379 Product Folder Featured Applications TIDEP0001 Tools Folder • Factory Automation and Process Control TIDEP0003 Tools Folder • Motor Drives TIDEP0008 Tools Folder TIDEP0010 Tools Folder • Digital and Analog I/O Modules TIDEP0028 Tools Folder • Industrial Communication Gateways • Sensors, Actuators, and Field Transmitters ASK Our E2E Experts WEBENCH® Calculator Tools Sitara AM437x ARM Cortex-A9 PRU-ICSS processor PHY Sercos III application/profile/ Slave MAC stack PHY An IMPORTANT NOTICE at the end of this TI reference design addresses authorized use, intellectual property matters and other important disclaimers and information. -

Industrial Ethernet Technologies Page 1 © Ethercat Technology Group, January 2011
Industrial Ethernet Technologies Page 1 © EtherCAT Technology Group, January 2011 Industrial Ethernet Technologies: Overview Approaches Modbus/TCP Ethernet/IP Powerlink PROFINET SERCOS III EtherCAT Summary © EtherCAT Technology Group Industrial Ethernet Technologies Editorial Preface: This presentation intends to provide an overview over the most important Industrial Ethernet Technologies. Based on published material it shows the technical principles of the various approaches and tries to put these into perspective. The content given represents my best knowledge of the systems introduced. Since the company I work for is member of all relevant fieldbus organizations and supports all important open fieldbus and Ethernet standards, you can assume a certain level of background information, too. The slides were shown on ETG Industrial Ethernet Seminar Series in Europe, Asia and North America as well as on several other occasions, altogether attended by several thousand people. Among those were project engineers and developers that have implemented and/or applied Industrial Ethernet technologies as well as key representatives of some of the supporting vendor organizations. All of them have been encouraged and invited to provide feedback in case they disagree with statements given or have better, newer or more precise information about the systems introduced. All the feedback received so far was included in the slides. You are invited to do the same: provide feedback and – if necessary – correction. Please help to serve the purpose of this slide set: a fair and technology driven comparison of Industrial Ethernet Technologies. Nuremberg, January 2011 Martin Rostan, [email protected] Industrial Ethernet Technologies Page 2 © EtherCAT Technology Group, January 2011 Industrial Ethernet Technologies: Overview Approaches Modbus/TCP Ethernet/IP Powerlink PROFINET SERCOS III EtherCAT Summary © EtherCAT Technology Group Industrial Ethernet Technologies All Industrial Ethernet Technologies introduced in this presentation are supported by user and vendor organizations. -
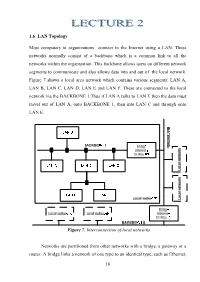
16 1.6 . LAN Topology Most Computers in Organizations Connect to the Internet Using a LAN. These Networks Normally Consist of A
1.6 . LAN Topology Most computers in organizations connect to the Internet using a LAN. These networks normally consist of a backbone which is a common link to all the networks within the organization. This backbone allows users on different network segments to communicate and also allows data into and out of the local network. Figure 7 shows a local area network which contains various segments: LAN A, LAN B, LAN C, LAN D, LAN E and LAN F. These are connected to the local network via the BACKBONE 1.Thus if LAN A talks to LAN E then the data must travel out of LAN A, onto BACKBONE 1, then into LAN C and through onto LAN E. Figure 7. Interconnection of local networks Networks are partitioned from other networks with a bridge, a gateway or a router. A bridge links a network of one type to an identical type, such as Ethernet, 16 or Token Ring to Token Ring. A gateway connects two dissimilar types of networks and routers operate in a similar way to gateways and can either connect to two similar or dissimilar networks. The key operation of a gateway, bridge or router is that they only allow data traffic through that is intended for another network, which is outside the connected network. This filters traffic and stops traffic, not intended for the network, from clogging-up the backbone. Most modern bridges, gateways and routers are intelligent and can automatically determine the topology of the network. Spanning-tree bridges have built-in intelligence and can communicate with other bridges. -

Industrial Ethernet Communication Protocols
WHITE PAPER Industrial Ethernet Communication Protocols Contents Executive Summary . 1 Industrial Slave Equipment �������������������������������������������������������������������������������������������������������������������������1 Industrial Automation Components . 2 Legacy Industrial Communication Protocols. 2 PROFIBUS �������������������������������������������������������������������������������������������������������������������������������������������������������3 CAN- ����������������������������������������������������������������������������������������������������������������������������������������������������������������3 Modbus . 3 CC-Link . 3 Descriptions of Industrial Ethernet Communication Protocols. 3 Ethernet/IP ����������������������������������������������������������������������������������������������������������������������������������������������������6 PROFINET . 6 EtherCAT. 6 SERCOS III �������������������������������������������������������������������������������������������������������������������������������������������������������7 CC-Link IE �������������������������������������������������������������������������������������������������������������������������������������������������������7 Powerlink �������������������������������������������������������������������������������������������������������������������������������������������������������7 Modbus /TCP . 8 Future Trends �������������������������������������������������������������������������������������������������������������������������������������������������8 -

Rexroth Indramotion MLC/MLP Indralogic XLC 11VRS Field Busses
Electric Drives Linear Motion and and Controls Hydraulics Assembly Technologies Pneumatics Service Bosch Rexroth AG DOK-IM*ML*-FB******V11-AP01-EN-P Rexroth IndraMotion MLC/MLP IndraLogic XLC 11VRS Field Busses Title Rexroth IndraMotion MLC/MLP IndraLogic XLC 11VRS Field Busses Type of Documentation Application Manual Document Typecode DOK-IM*ML*-FB******V11-AP01-EN-P Internal File Reference RS-f7acbd514ebfbbb90a6846a0006e7c2d-1-en-US-5 Purpose of Documentation This documentation describes the field busses and their diagnostic function blocks for the IndraLogic XLC L25/ L45/ L65/ VEP systems and IndraMotion MLC/MLP L25/ L45/ L65/ VEP systems. It constitutes the basis for the online help. Record of Revision Edition Release Date Notes 120-3300-B317/EN -01 11.2010 First edition Copyright © Bosch Rexroth AG 2010 Copying this document, giving it to others and the use or communication of the contents thereof without express authority, are forbidden. Offenders are liable for the payment of damages. All rights are reserved in the event of the grant of a patent or the registration of a utility model or design (DIN 34-1). Validity The specified data is for product description purposes only and may not be deemed to be guaranteed unless expressly confirmed in the contract. All rights are reserved with respect to the content of this documentation and the availa‐ bility of the product. Published by Bosch Rexroth AG Bgm.-Dr.-Nebel-Str. 2 • 97816 Lohr a. Main, Germany Phone +49 (0)93 52/40-0 • Fax +49 (0)93 52/40-48 85 http://www.boschrexroth.com/ System IndraLogic & Basis Motion Logic GLo / HBu / vha / PiGe Note This document has been printed on chlorine-free bleached paper.