Frame Rules from Answer Types for Code Pointers
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

A Polymorphic Type System for Extensible Records and Variants
A Polymorphic Typ e System for Extensible Records and Variants Benedict R. Gaster and Mark P. Jones Technical rep ort NOTTCS-TR-96-3, November 1996 Department of Computer Science, University of Nottingham, University Park, Nottingham NG7 2RD, England. fbrg,[email protected] Abstract b oard, and another indicating a mouse click at a par- ticular p oint on the screen: Records and variants provide exible ways to construct Event = Char + Point : datatyp es, but the restrictions imp osed by practical typ e systems can prevent them from b eing used in ex- These de nitions are adequate, but they are not par- ible ways. These limitations are often the result of con- ticularly easy to work with in practice. For example, it cerns ab out eciency or typ e inference, or of the di- is easy to confuse datatyp e comp onents when they are culty in providing accurate typ es for key op erations. accessed by their p osition within a pro duct or sum, and This pap er describ es a new typ e system that reme- programs written in this way can b e hard to maintain. dies these problems: it supp orts extensible records and To avoid these problems, many programming lan- variants, with a full complement of p olymorphic op era- guages allow the comp onents of pro ducts, and the al- tions on each; and it o ers an e ective type inference al- ternatives of sums, to b e identi ed using names drawn gorithm and a simple compilation metho d. -

Generic Programming
Generic Programming July 21, 1998 A Dagstuhl Seminar on the topic of Generic Programming was held April 27– May 1, 1998, with forty seven participants from ten countries. During the meeting there were thirty seven lectures, a panel session, and several problem sessions. The outcomes of the meeting include • A collection of abstracts of the lectures, made publicly available via this booklet and a web site at http://www-ca.informatik.uni-tuebingen.de/dagstuhl/gpdag.html. • Plans for a proceedings volume of papers submitted after the seminar that present (possibly extended) discussions of the topics covered in the lectures, problem sessions, and the panel session. • A list of generic programming projects and open problems, which will be maintained publicly on the World Wide Web at http://www-ca.informatik.uni-tuebingen.de/people/musser/gp/pop/index.html http://www.cs.rpi.edu/˜musser/gp/pop/index.html. 1 Contents 1 Motivation 3 2 Standards Panel 4 3 Lectures 4 3.1 Foundations and Methodology Comparisons ........ 4 Fundamentals of Generic Programming.................. 4 Jim Dehnert and Alex Stepanov Automatic Program Specialization by Partial Evaluation........ 4 Robert Gl¨uck Evaluating Generic Programming in Practice............... 6 Mehdi Jazayeri Polytypic Programming........................... 6 Johan Jeuring Recasting Algorithms As Objects: AnAlternativetoIterators . 7 Murali Sitaraman Using Genericity to Improve OO Designs................. 8 Karsten Weihe Inheritance, Genericity, and Class Hierarchies.............. 8 Wolf Zimmermann 3.2 Programming Methodology ................... 9 Hierarchical Iterators and Algorithms................... 9 Matt Austern Generic Programming in C++: Matrix Case Study........... 9 Krzysztof Czarnecki Generative Programming: Beyond Generic Programming........ 10 Ulrich Eisenecker Generic Programming Using Adaptive and Aspect-Oriented Programming . -

Data Types and Variables
Color profile: Generic CMYK printer profile Composite Default screen Complete Reference / Visual Basic 2005: The Complete Reference / Petrusha / 226033-5 / Chapter 2 2 Data Types and Variables his chapter will begin by examining the intrinsic data types supported by Visual Basic and relating them to their corresponding types available in the .NET Framework’s Common TType System. It will then examine the ways in which variables are declared in Visual Basic and discuss variable scope, visibility, and lifetime. The chapter will conclude with a discussion of boxing and unboxing (that is, of converting between value types and reference types). Visual Basic Data Types At the center of any development or runtime environment, including Visual Basic and the .NET Common Language Runtime (CLR), is a type system. An individual type consists of the following two items: • A set of values. • A set of rules to convert every value not in the type into a value in the type. (For these rules, see Appendix F.) Of course, every value of another type cannot always be converted to a value of the type; one of the more common rules in this case is to throw an InvalidCastException, indicating that conversion is not possible. Scalar or primitive types are types that contain a single value. Visual Basic 2005 supports two basic kinds of scalar or primitive data types: structured data types and reference data types. All data types are inherited from either of two basic types in the .NET Framework Class Library. Reference types are derived from System.Object. Structured data types are derived from the System.ValueType class, which in turn is derived from the System.Object class. -

Static Typing Where Possible, Dynamic Typing When Needed: the End of the Cold War Between Programming Languages
Intended for submission to the Revival of Dynamic Languages Static Typing Where Possible, Dynamic Typing When Needed: The End of the Cold War Between Programming Languages Erik Meijer and Peter Drayton Microsoft Corporation Abstract Advocates of dynamically typed languages argue that static typing is too rigid, and that the softness of dynamically lan- This paper argues that we should seek the golden middle way guages makes them ideally suited for prototyping systems with between dynamically and statically typed languages. changing or unknown requirements, or that interact with other systems that change unpredictably (data and application in- tegration). Of course, dynamically typed languages are indis- 1 Introduction pensable for dealing with truly dynamic program behavior such as method interception, dynamic loading, mobile code, runtime <NOTE to="reader"> Please note that this paper is still very reflection, etc. much work in progress and as such the presentation is unpol- In the mother of all papers on scripting [16], John Ousterhout ished and possibly incoherent. Obviously many citations to argues that statically typed systems programming languages related and relevant work are missing. We did however do our make code less reusable, more verbose, not more safe, and less best to make it provocative. </NOTE> expressive than dynamically typed scripting languages. This Advocates of static typing argue that the advantages of static argument is parroted literally by many proponents of dynami- typing include earlier detection of programming mistakes (e.g. cally typed scripting languages. We argue that this is a fallacy preventing adding an integer to a boolean), better documenta- and falls into the same category as arguing that the essence of tion in the form of type signatures (e.g. -

Software II: Principles of Programming Languages
Software II: Principles of Programming Languages Lecture 6 – Data Types Some Basic Definitions • A data type defines a collection of data objects and a set of predefined operations on those objects • A descriptor is the collection of the attributes of a variable • An object represents an instance of a user- defined (abstract data) type • One design issue for all data types: What operations are defined and how are they specified? Primitive Data Types • Almost all programming languages provide a set of primitive data types • Primitive data types: Those not defined in terms of other data types • Some primitive data types are merely reflections of the hardware • Others require only a little non-hardware support for their implementation The Integer Data Type • Almost always an exact reflection of the hardware so the mapping is trivial • There may be as many as eight different integer types in a language • Java’s signed integer sizes: byte , short , int , long The Floating Point Data Type • Model real numbers, but only as approximations • Languages for scientific use support at least two floating-point types (e.g., float and double ; sometimes more • Usually exactly like the hardware, but not always • IEEE Floating-Point Standard 754 Complex Data Type • Some languages support a complex type, e.g., C99, Fortran, and Python • Each value consists of two floats, the real part and the imaginary part • Literal form real component – (in Fortran: (7, 3) imaginary – (in Python): (7 + 3j) component The Decimal Data Type • For business applications (money) -

Should Your Specification Language Be Typed?
Should Your Specification Language Be Typed? LESLIE LAMPORT Compaq and LAWRENCE C. PAULSON University of Cambridge Most specification languages have a type system. Type systems are hard to get right, and getting them wrong can lead to inconsistencies. Set theory can serve as the basis for a specification lan- guage without types. This possibility, which has been widely overlooked, offers many advantages. Untyped set theory is simple and is more flexible than any simple typed formalism. Polymorphism, overloading, and subtyping can make a type system more powerful, but at the cost of increased complexity, and such refinements can never attain the flexibility of having no types at all. Typed formalisms have advantages too, stemming from the power of mechanical type checking. While types serve little purpose in hand proofs, they do help with mechanized proofs. In the absence of verification, type checking can catch errors in specifications. It may be possible to have the best of both worlds by adding typing annotations to an untyped specification language. We consider only specification languages, not programming languages. Categories and Subject Descriptors: D.2.1 [Software Engineering]: Requirements/Specifica- tions; D.2.4 [Software Engineering]: Software/Program Verification—formal methods; F.3.1 [Logics and Meanings of Programs]: Specifying and Verifying and Reasoning about Pro- grams—specification techniques General Terms: Verification Additional Key Words and Phrases: Set theory, specification, types Editors’ introduction. We have invited the following -

A Core Calculus of Metaclasses
A Core Calculus of Metaclasses Sam Tobin-Hochstadt Eric Allen Northeastern University Sun Microsystems Laboratories [email protected] [email protected] Abstract see the problem, consider a system with a class Eagle and Metaclasses provide a useful mechanism for abstraction in an instance Harry. The static type system can ensure that object-oriented languages. But most languages that support any messages that Harry responds to are also understood by metaclasses impose severe restrictions on their use. Typi- any other instance of Eagle. cally, a metaclass is allowed to have only a single instance However, even in a language where classes can have static and all metaclasses are required to share a common super- methods, the desired relationships cannot be expressed. For class [6]. In addition, few languages that support metaclasses example, in such a language, we can write the expression include a static type system, and none include a type system Eagle.isEndangered() provided that Eagle has the ap- with nominal subtyping (i.e., subtyping as defined in lan- propriate static method. Such a method is appropriate for guages such as the JavaTM Programming Language or C#). any class that is a species. However, if Salmon is another To elucidate the structure of metaclasses and their rela- class in our system, our type system provides us no way of tionship with static types, we present a core calculus for a requiring that it also have an isEndangered method. This nominally typed object-oriented language with metaclasses is because we cannot classify both Salmon and Eagle, when and prove type soundness over this core. -

First-Class Type Classes
First-Class Type Classes Matthieu Sozeau1 and Nicolas Oury2 1 Univ. Paris Sud, CNRS, Laboratoire LRI, UMR 8623, Orsay, F-91405 INRIA Saclay, ProVal, Parc Orsay Universit´e, F-91893 [email protected] 2 University of Nottingham [email protected] Abstract. Type Classes have met a large success in Haskell and Is- abelle, as a solution for sharing notations by overloading and for spec- ifying with abstract structures by quantification on contexts. However, both systems are limited by second-class implementations of these con- structs, and these limitations are only overcomed by ad-hoc extensions to the respective systems. We propose an embedding of type classes into a dependent type theory that is first-class and supports some of the most popular extensions right away. The implementation is correspond- ingly cheap, general and integrates well inside the system, as we have experimented in Coq. We show how it can be used to help structured programming and proving by way of examples. 1 Introduction Since its introduction in programming languages [1], overloading has met an important success and is one of the core features of object–oriented languages. Overloading allows to use a common name for different objects which are in- stances of the same type schema and to automatically select an instance given a particular type. In the functional programming community, overloading has mainly been introduced by way of type classes, making ad-hoc polymorphism less ad hoc [17]. A type class is a set of functions specified for a parametric type but defined only for some types. -

Type Systems for Programming Languages1 (DRAFT)
Type Systems for Programming Languages1 (DRAFT) Robert Harper School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213-3891 E-mail: [email protected] WWW: http://www.cs.cmu.edu/~rwh Spring, 2000 Copyright c 1995-2000. All rights reserved. 1These are course notes Computer Science 15–814 at Carnegie Mellon University. This is an incomplete, working draft, not intended for publication. Citations to the literature are spotty at best; no results presented here should be considered original unless explicitly stated otherwise. Please do not distribute these notes without the permission of the author. ii Contents I Type Structure 1 1 Basic Types 3 1.1 Introduction . 3 1.2 Statics . 3 1.3 Dynamics . 4 1.3.1 Contextual Semantics . 4 1.3.2 Evaluation Semantics . 5 1.4 Type Soundness . 7 1.5 References . 8 2 Function and Product Types 9 2.1 Introduction . 9 2.2 Statics . 9 2.3 Dynamics . 10 2.4 Type Soundness . 11 2.5 Termination . 12 2.6 References . 13 3 Sums 15 3.1 Introduction . 15 3.2 Sum Types . 15 3.3 References . 16 4 Subtyping 17 4.1 Introduction . 17 4.2 Subtyping . 17 4.2.1 Subsumption . 18 4.3 Primitive Subtyping . 18 4.4 Tuple Subtyping . 19 4.5 Record Subtyping . 22 4.6 References . 24 iii 5 Variable Types 25 5.1 Introduction . 25 5.2 Variable Types . 25 5.3 Type Definitions . 26 5.4 Constructors, Types, and Kinds . 28 5.5 References . 30 6 Recursive Types 31 6.1 Introduction . 31 6.2 G¨odel’s T .............................. -

CSE341, Fall 2011, Lecture 18 Summary
CSE341, Fall 2011, Lecture 18 Summary Standard Disclaimer: This lecture summary is not necessarily a complete substitute for attending class, reading the associated code, etc. It is designed to be a useful resource for students who attended class and are later reviewing the material. The most important difference between Racket and ML is that ML has a type system that rejects many programs \before they run" meaning they are not ML programs at all. (Ruby and Java have an analogous difference.) The purpose of this lecture is to give some perspective on what it means to use a type system for static checking (i.e., static typing) rather than detecting type errors at run-time (i.e., dynamic typing). Software developers often have vigorous opinions about whether they prefer their languages to have static typing or dynamic typing. We will first discuss what static checking is, focusing on (1) the fact that different programming languages check different properties statically and (2) that static checking is inherently approximate. This discussion will give us the background to discuss various advantages and disadvantages of static checking with clear facts and arguments rather than subjective preferences. What is Static Checking? What is usually meant by \static checking" is anything done to reject a program after it (successfully) parses but before it runs. If a program does not parse, we still get an error, but we call such an error a \syntax error" or \parsing error." In contrast, an error from static checking, typically a \type error," would include things like undefined variables or using a number instead of a pair. -
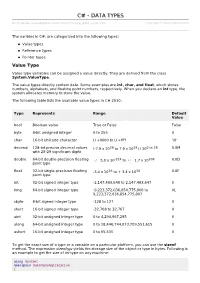
C## -- DDAATTAA TTYYPPEESS Copyright © Tutorialspoint.Com
CC## -- DDAATTAA TTYYPPEESS http://www.tutorialspoint.com/csharp/csharp_data_types.htm Copyright © tutorialspoint.com The varibles in C#, are categorized into the following types: Value types Reference types Pointer types Value Type Value type variables can be assigned a value directly. They are derived from the class System.ValueType. The value types directly contain data. Some examples are int, char, and float, which stores numbers, alphabets, and floating point numbers, respectively. When you declare an int type, the system allocates memory to store the value. The following table lists the available value types in C# 2010: Type Represents Range Default Value bool Boolean value True or False False byte 8-bit unsigned integer 0 to 255 0 char 16-bit Unicode character U +0000 to U +ffff '\0' decimal 128-bit precise decimal values (-7.9 x 1028 to 7.9 x 1028) / 100 to 28 0.0M with 28-29 significant digits double 64-bit double-precision floating + / − 5.0 x 10-324 to + / − 1.7 x 10308 0.0D point type float 32-bit single-precision floating -3.4 x 1038 to + 3.4 x 1038 0.0F point type int 32-bit signed integer type -2,147,483,648 to 2,147,483,647 0 long 64-bit signed integer type -9,223,372,036,854,775,808 to 0L 9,223,372,036,854,775,807 sbyte 8-bit signed integer type -128 to 127 0 short 16-bit signed integer type -32,768 to 32,767 0 uint 32-bit unsigned integer type 0 to 4,294,967,295 0 ulong 64-bit unsigned integer type 0 to 18,446,744,073,709,551,615 0 ushort 16-bit unsigned integer type 0 to 65,535 0 To get the exact size of a type or a variable on a particular platform, you can use the sizeof method. -

Common Lisp Object System
Common Lisp Object System by Linda G. DeMichiel and Richard P. Gabriel Lucid, Inc. 707 Laurel Street Menlo Park, California 94025 (415)329-8400 [email protected] [email protected] with Major Contributions by Daniel Bobrow, Gregor Kiczales, and David Moon Abstract The Common Lisp Object System is an object-oriented system that is based on the concepts of generic functions, multiple inheritance, and method combination. All objects in the Object System are instances of classes that form an extension to the Common Lisp type system. The Common Lisp Object System is based on a meta-object protocol that renders it possible to alter the fundamental structure of the Object System itself. The Common Lisp Object System has been proposed as a standard for ANSI Common Lisp and has been tentatively endorsed by X3J13. Common Lisp Object System by Linda G. DeMichiel and Richard P. Gabriel with Major Contributions by Daniel Bobrow, Gregor Kiczales, and David Moon 1. History of the Common Lisp Object System The Common Lisp Object System is an object-oriented programming paradigm de- signed for Common Lisp. Over a period of eight months a group of five people, one from Symbolics and two each from Lucid and Xerox, took the best ideas from CommonLoops and Flavors, and combined them into a new object-oriented paradigm for Common Lisp. This combination is not simply a union: It is a new paradigm that is similar in its outward appearances to CommonLoops and Flavors, and it has been given a firmer underlying semantic basis. The Common Lisp Object System has been proposed as a standard for ANSI Common Lisp and has been tentatively endorsed by X3J13.