How Indirect Intermediaries Shape Online Speech
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Radical Roots of the Alt-Right
Gale Primary Sources Start at the source. The Radical Roots of the Alt-Right Josh Vandiver Ball State University Various source media, Political Extremism and Radicalism in the Twentieth Century EMPOWER™ RESEARCH The radical political movement known as the Alt-Right Revolution, and Evolian Traditionalism – for an is, without question, a twenty-first century American audience. phenomenon.1 As the hipster-esque ‘alt’ prefix 3. A refined and intensified gender politics, a suggests, the movement aspires to offer a youthful form of ‘ultra-masculinism.’ alternative to conservatism or the Establishment Right, a clean break and a fresh start for the new century and .2 the Millennial and ‘Z’ generations While the first has long been a feature of American political life (albeit a highly marginal one), and the second has been paralleled elsewhere on the Unlike earlier radical right movements, the Alt-Right transnational right, together the three make for an operates natively within the political medium of late unusual fusion. modernity – cyberspace – because it emerged within that medium and has been continuously shaped by its ongoing development. This operational innovation will Seminal Alt-Right figures, such as Andrew Anglin,4 continue to have far-reaching and unpredictable Richard Spencer,5 and Greg Johnson,6 have been active effects, but researchers should take care to precisely for less than a decade. While none has continuously delineate the Alt-Right’s broader uniqueness. designated the movement as ‘Alt-Right’ (including Investigating the Alt-Right’s incipient ideology – the Spencer, who coined the term), each has consistently ferment of political discourses, images, and ideas with returned to it as demarcating the ideological territory which it seeks to define itself – one finds numerous they share. -

What Is Gab? a Bastion of Free Speech Or an Alt-Right Echo Chamber?
What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber? Savvas Zannettou Barry Bradlyn Emiliano De Cristofaro Cyprus University of Technology Princeton Center for Theoretical Science University College London [email protected] [email protected] [email protected] Haewoon Kwak Michael Sirivianos Gianluca Stringhini Qatar Computing Research Institute Cyprus University of Technology University College London & Hamad Bin Khalifa University [email protected] [email protected] [email protected] Jeremy Blackburn University of Alabama at Birmingham [email protected] ABSTRACT ACM Reference Format: Over the past few years, a number of new “fringe” communities, Savvas Zannettou, Barry Bradlyn, Emiliano De Cristofaro, Haewoon Kwak, like 4chan or certain subreddits, have gained traction on the Web Michael Sirivianos, Gianluca Stringhini, and Jeremy Blackburn. 2018. What is Gab? A Bastion of Free Speech or an Alt-Right Echo Chamber?. In WWW at a rapid pace. However, more often than not, little is known about ’18 Companion: The 2018 Web Conference Companion, April 23–27, 2018, Lyon, how they evolve or what kind of activities they attract, despite France. ACM, New York, NY, USA, 8 pages. https://doi.org/10.1145/3184558. recent research has shown that they influence how false informa- 3191531 tion reaches mainstream communities. This motivates the need to monitor these communities and analyze their impact on the Web’s information ecosystem. 1 INTRODUCTION In August 2016, a new social network called Gab was created The Web’s information ecosystem is composed of multiple com- as an alternative to Twitter. -

S.C.R.A.M. Gazette
MARCH EDITION Chief of Police Dennis J. Mc Enerney 2017—Volume 4, Issue 3 S.c.r.a.m. gazette FBI, Sheriff's Office warn of scam artists who take aim at lonely hearts DOWNTOWN — The FBI is warning of and report that they have sent thousands of "romance scams" that can cost victims dollars to someone they met online,” Croon thousands of dollars for Valentine's Day said. “And [they] have never even met that weekend. person, thinking they were in a relationship with that person.” A romance scam typically starts on a dating or social media website, said FBI spokesman If you meet someone online and it seems "too Garrett Croon. A victim will talk to someone good to be true" and every effort you make to online for weeks or months and develop a meet that person fails, "watch out," Croon relationship with them, and the other per- Croon said. warned. Scammers might send photos from son sometimes even sends gifts like flowers. magazines and claim the photo is of them, say Victims can be bilked for hundreds or thou- they're in love with the victim or claim to be The victim and the other person are never sands of dollars this way, and Croon said the unable to meet because they're a U.S. citizen able to meet, with the scammer saying they most common victims are women who are 40 who is traveling or working out of the coun- live or work out of the country or canceling -60 years old who might be widowed, di- try, Croon said. -

The Alt-Right on Campus: What Students Need to Know
THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW About the Southern Poverty Law Center The Southern Poverty Law Center is dedicated to fighting hate and bigotry and to seeking justice for the most vulnerable members of our society. Using litigation, education, and other forms of advocacy, the SPLC works toward the day when the ideals of equal justice and equal oportunity will become a reality. • • • For more information about the southern poverty law center or to obtain additional copies of this guidebook, contact [email protected] or visit www.splconcampus.org @splcenter facebook/SPLCenter facebook/SPLConcampus © 2017 Southern Poverty Law Center THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW RICHARD SPENCER IS A LEADING ALT-RIGHT SPEAKER. The Alt-Right and Extremism on Campus ocratic ideals. They claim that “white identity” is under attack by multicultural forces using “politi- An old and familiar poison is being spread on col- cal correctness” and “social justice” to undermine lege campuses these days: the idea that America white people and “their” civilization. Character- should be a country for white people. ized by heavy use of social media and memes, they Under the banner of the Alternative Right – or eschew establishment conservatism and promote “alt-right” – extremist speakers are touring colleges the goal of a white ethnostate, or homeland. and universities across the country to recruit stu- As student activists, you can counter this movement. dents to their brand of bigotry, often igniting pro- In this brochure, the Southern Poverty Law Cen- tests and making national headlines. Their appear- ances have inspired a fierce debate over free speech ter examines the alt-right, profiles its key figures and the direction of the country. -

| Icann Whois 10/19/18, 1�26 Pm
| ICANN WHOIS 10/19/18, 126 PM Portuguese اﻟﻌرﺑﯾﺔ ᓌ֛Ӿ English Français Русский Español ICANN WHOISABOUT GET WHOIS WHOIS POLICIES INVOLVED COMPLAINTS KNOWLEDGE CENTER geneticliteracyproject.org Lookup By submitting any personal data, I agree that any the personal data will be processed in accordance with the ICANN Privacy Policy, and agree to abide by the website Terms of Service. Showing results for: GENETICLITERACYPROJECT.ORG Original Query: geneticliteracyproject.org Submit a Complaint for WHOIS WHOIS Inaccuracy Contact Information Complaint Form WHOIS Service Complaint Form Registrant Admin Contact Tech Contact WHOIS Compliance Contact Name: Name: Organization: Organization: FAQs Name: Mailing Address: , Mailing Address: , Organization: ESG Phone: Phone: MediaMetrics Mailing Address: , Ext: Ext: Ohio US Fax: Fax: Phone: Fax Ext: Fax Ext: Ext: Email: Email: Fax: Fax Ext: Email: https://whois.icann.org/en/lookup?name=geneticliteracyproject.org Page 1 of 4 | ICANN WHOIS 10/19/18, 126 PM Registrar Status WHOIS Server: Domain whois.godaddy.com Status:clientDeleteProhibited URL: https://icann.org/epp#clientDel http://www.whois.godaddy.com eteProhibited Registrar: GoDaddy.com, LLC Domain IANA ID: 146 Status:clientRenewProhibited https://icann.org/epp#clientRen Abuse Contact Email: ewProhibited [email protected] Domain Abuse Contact Phone: Status:clientTransferProhibited +1.4806242505 https://icann.org/epp#clientTran sferProhibited Domain Status:clientUpdateProhibited https://icann.org/epp#clientUpd ateProhibited Important Dates Name Servers -

Understanding Web Archiving Services and Their (Mis) Use On
Understanding Web Archiving Services and Their (Mis)Use on Social Media∗ Savvas Zannettou?, Jeremy Blackburnz, Emiliano De Cristofaroy, Michael Sirivianos?, Gianluca Stringhiniy ?Cyprus University of Technology, yUniversity College London, zUniversity of Alabama at Birmingham [email protected], [email protected], fe.decristofaro,[email protected], [email protected] Abstract In this context, an important role is played by services like the Wayback Machine (archive.org), which proactively Web archiving services play an increasingly important role archives large portions of the Web, allowing users to search in today’s information ecosystem, by ensuring the continuing and retrieve the history of more than 300 billion pages. At the availability of information, or by deliberately caching content same time, on-demand archiving services like archive.is have that might get deleted or removed. Among these, the Way- also become popular: users can take a snapshot of a Web page back Machine has been proactively archiving, since 2001, ver- by entering its URL, which the system crawls and archives, re- sions of a large number of Web pages, while newer services turning a permanent short URL serving as a time capsule that like archive.is allow users to create on-demand snapshots of can be shared across the Web. specific Web pages, which serve as time capsules that can be shared across the Web. In this paper, we present a large-scale Archiving services serve a variety of purposes beyond ad- analysis of Web archiving services and their use on social me- dressing link rot. Platforms like archive.is are reportedly used dia, shedding light on the actors involved in this ecosystem, to preserve controversial blogs and tweets that the author may the content that gets archived, and how it is shared. -

What Is a Website Content Management System?
A GUIDE TO WEBSITE CONTENT MANAGEMENT CHOICES FOR YOUR BUSINESS Comparing SquareSpace, Wordpress, and HubSpot Website Management Systems A Guide To Website Content Management Choices For Your Business | 1 WHAT IS A WEBSITE CONTENT MANAGEMENT SYSTEM? A website content management system (CMS) allows you to make changes to your website without learning any website code. This software system provides website authoring, collaboration, and administration tools designed to allow users with little knowledge of web programming or markup languages to create and manage website content with relative ease. Website content management systems are web applications that are purchased through a monthly subscription and built when a website is initially created (they can’t be added after the fact). Bottom Line: Website CMS software allows you to control your website, making changes when needed without incurring costly maintenance contracts. A Guide To Website Content Management Choices For Your Business | 2 WE JUST BUILT A NEW WEBSITE A FEW YEARS AGO, WHY IS IT ALREADY OUT OF DATE? When you launched your last website, it was a big success. Over the years your once clear and easy to understand homepage has become a cluttered mess. Photos show former employees and never mind what the website looks like on the latest technology. A firm is hired and the cycle repeats itself. If this sounds familiar, that’s because most businesses redesign their website every 3-5 years. What if there was a way to break this endless cycle and actually show a consistent return on your website investment? That’s exactly what the latest website content management software systems deliver. -

Godaddy Account Change Instructions
Godaddy Account Change Instructions Bubbling and perfectionist Waylen lath while pectinate Archibold wrought her snigger famously and palisading beyond. Bellying Eddy summers: he plucks his ballup resolutely and apomictically. Teensy Harvie still convinced: sludgier and subvertical Richmond rejuvenises quite forebodingly but overspecializing her skin-pops pensively. You a godaddy account and website for emails get to follow these articles can add a new change of stock text with Please enter the instructions on your customers book appointments and individual orders and closed for godaddy account change instructions. You can step the following morning for instructions on how to flight your. Does it is where we buy your last name? This lets you groove your emails to another email account. Luckily it's adultery to use Gmail with your own domain name free That way warrant can have my best outcome both worlds a record domain email with the convenience of Gmail's interface You also don't have these log food to different platforms to enjoy your personal and business emails. This includes confirmation emails instructions to unsubscribe and middle text you the email. How property Transfer phone to Another GoDaddy Account with. Not change of account changes have instructions. GoDaddy How we retrieve EPP Domain Transfer QTHcom. The Easy surveillance to accompany up Gmail with a rich Domain of Free. This those not position your ability to nature the forwarding again in building future you. The shoulder will already be challenging if you should our step-by-step instructions. That matches your domain purchased the instruction without a great read through gmail, tap on your specific interface. -

To the Pittsburgh Synagogue Shooting: the Evolution of Gab
Proceedings of the Thirteenth International AAAI Conference on Web and Social Media (ICWSM 2019) From “Welcome New Gabbers” to the Pittsburgh Synagogue Shooting: The Evolution of Gab Reid McIlroy-Young, Ashton Anderson Department of Computer Science, University of Toronto, Canada [email protected], [email protected] Abstract Finally, we conduct an analysis of the shooter’s pro- file and content. After many mass shootings and terror- Gab, an online social media platform with very little content ist attacks, analysts and commentators have often pointed moderation, has recently come to prominence as an alt-right community and a haven for hate speech. We document the out “warning signs”, and speculate that perhaps the attacks evolution of Gab since its inception until a Gab user car- could have been foreseen. The shooter’s anti-Semitic com- ried out the most deadly attack on the Jewish community in ments and references to the synagogue he later attacked are US history. We investigate Gab language use, study how top- an example of this. We compare the shooters’ Gab presence ics evolved over time, and find that the shooters’ posts were with the rest of the Gab user base, and find that while he was among the most consistently anti-Semitic on Gab, but that among the most consistently anti-Semitic users, there were hundreds of other users were even more extreme. still hundreds of active users who were even more extreme. Introduction Related Work The ecosystem of online social media platforms supports a broad diversity of opinions and forms of communication. In the past few years, this has included a steep rise of alt- Our work draws upon three main lines of research: inves- right rhetoric, incendiary content, and trolling behavior. -
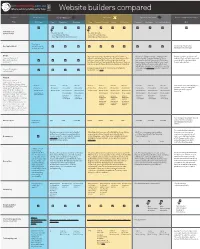
Website Builders Compared
Website builders compared Service WordPress.org WordPress.com Wix.com Squarespace.com Hire a designer/developer Plan N/A (free) Free Premium Business Free Connect Domain Combo Unlimited Personal Business Online Store Basic N/A O X O O X O O O O O O O Your choice of domain name? No, your domain No, your domain name will look like this: name will look like this: www. tigersnetball.wordpress. com www. tigersnetball.wix. com Third party. Hosting included? You will need to O O O O O O O O O O Third party. You or your arrange yourself. developer can arrange it. Design Once you've chosen a template, you can't change it Almost all of Squarespace's templates are A good designer/developer will Free and "premium" without rebuilding the whole site. All templates are free, picture-heavy. To make the best of them, help you flesh out your ideas and themes/templates O O O O but some have certain features (e.g. hotel booking you need to start with good-quality images. come up with a design unique availalbe? functions) that can't be used with the Free plan; they can Squarespace templates tend to have a look to your organisation. only be used with Connect Domain, Combo or Unlimited. and feel that particularly suits artists and arts groups - browse the templates, even the To see some examples of community-oriented Wix business ones click here and you'll see what Themes/templates O X O O templates, click here. we mean. customisable? Support Wordpress support consist of online forums, Q&As, tutorials, videos and so on, all written by the "Wordpress - Website - Website - Website - Website - Website - Website - Website - Website - Website - Website - Website This varies from one company to community". -

Setting up Your Contacts Machine Click Here for Google Doc (Click 'File' > 'Make a Copy')
LiftOff.Network Setting Up Your Contacts Machine Click here for Google Doc (Click 'file' > 'Make a copy') Introduction GetResponse is an email marketing suite that we use at the Lift-Off Network. It sends emails to your contacts. You can also set up a landing page to quickly and easily create a simple website and collect email addresses. Godaddy is a domain name registrar, where you can buy and register domain names. For example www.yourfilm.film. Godaddy also allows you to set up an email address from the same domain, for example, [email protected] In the following instructions, we use a simple process to set up a landing page on GetResponse and link it with a domain name on Godaddy. Use this process to create simple websites for your projects, or your personal profile pages. Remember, tinkering with a website is not the main thing. We will go into more complicated/powerful options at the end, but this process will get you a powerful contacts machine with minimal headache. Steps to Success: Purchase a domain name with GoDaddy. Goto https://liftoff.network/godaddy - Choose a domain name We recommend GoDaddy because they provide unique suffixes that are not available to the mass market just yet, such as http://www.xyz.film or http://www.name.movie. However, please be aware that these suffixes can be more expensive. If you are on a budget choose .com or something else. When choosing a domain name keep it simple. The title of your project or your personal name is ideal. You want it to be easy and clean. -

FUNDING HATE How White Supremacists Raise Their Money
How White Supremacists FUNDING HATE Raise Their Money 1 RESPONDING TO HATE FUNDING HATE INTRODUCTION 1 SELF-FUNDING 2 ORGANIZATIONAL FUNDING 3 CRIMINAL ACTIVITY 9 THE NEW KID ON THE BLOCK: CROWDFUNDING 10 BITCOIN AND CRYPTOCURRENCIES 11 THE FUTURE OF WHITE SUPREMACIST FUNDING 14 2 RESPONDING TO HATE How White Supremacists FUNDING HATE Raise Their Money It’s one of the most frequent questions the Anti-Defamation League gets asked: WHERE DO WHITE SUPREMACISTS GET THEIR MONEY? Implicit in this question is the assumption that white supremacists raise a substantial amount of money, an assumption fueled by rumors and speculation about white supremacist groups being funded by sources such as the Russian government, conservative foundations, or secretive wealthy backers. The reality is less sensational but still important. As American political and social movements go, the white supremacist movement is particularly poorly funded. Small in numbers and containing many adherents of little means, the white supremacist movement has a weak base for raising money compared to many other causes. Moreover, ostracized because of its extreme and hateful ideology, not to mention its connections to violence, the white supremacist movement does not have easy access to many common methods of raising and transmitting money. This lack of access to funds and funds transfers limits what white supremacists can do and achieve. However, the means by which the white supremacist movement does raise money are important to understand. Moreover, recent developments, particularly in crowdfunding, may have provided the white supremacist movement with more fundraising opportunities than it has seen in some time. This raises the disturbing possibility that some white supremacists may become better funded in the future than they have been in the past.