Effective Use of Mobile Devices for End Users Codemob: Effective Use of Mobile Devices for End-Users
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Survey on Architectures of Mobile Operating Systems: Challenges and Issues
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 3, March 2015, PP 73-76 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A Survey on Architectures of Mobile Operating Systems: Challenges and Issues Prof. Y. K. Sundara Krishna1 HOD, Dept. of Computer Science, Krishna University Mr. G K Mohan Devarakonda2 Research Scholar, Krishna University Abstract: In the early years of mobile evolution, Discontinued Platforms Current mobile devices are enabled only with voice services Platforms that allow the users to communicate with each other. Symbian OS Android But now a days, the mobile technology undergone Palm OS IOS various changes to a great extent so that the devices Maemo OS Windows Phone allows the users not only to communicate but also to Meego OS Firefox OS attain a variety of services such as video calls, faster Black Berry OS browsing services,2d and 3d games, Camera, 2.1 Symbian OS: This Operating system was Banking Services, GPS services, File sharing developed by NOKIA. services, Tracking Services, M-Commerce and so many. The changes in mobile technology may be due Architecture: to Operating System or Hardware or Network or Memory. This paper presents a survey on evolutions SYMBIAN OS GUI Library in mobile developments especially on mobile operating system Architectures, challenges and Issues in various mobile operating Systems. Application Engines JAVA VM 1. INTRODUCTION Servers (Operating System Services) A Mobile operating system is a System Software that is specifically designed to run on handheld devices Symbian OS Base (File Server, Kernel) such as Mobile Phones, PDA’s. -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing
Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing VOLUME 2014 NO. 1 $ 7 . 9 9 PURITAS SPRINGS SOFTWARE Best Home Pages We think the importance of the through which you accessed INSIDE THIS ISSUE: home page has been greatly the world wide web. Once 1-3 reduced due to the invention of tabbed browsers arrived on the tabbed browsers. Although scene it was possible to create 1,4,5 conceived a group of 4 earlier in 1988, home pages Digital Inklings 6,7 tabbed brows- with each page Child Support 8 ing didn’t go being able to Spousal Support 10 mainstream “specialize” in a Uniform DR Forms 12 until the re- specific area of lease of Micro- your interest. Family Law Documents 13 soft’s Windows Take the Probate Forms 14 Internet Ex- weather for Ohio Estate Tax 16 plorer 7 in example. Every U.S. Income Tax (1041) 18 2006. Until then, your Home good home page should have Ohio Fiduciary Tax 19 page was the sole portal a minimal weather information; (Continued on page 2) Ohio Adoption Forms 20 OH Guardianship Forms 21 OH Wrongful Death 22 Loan Amortizer 23 # More Law Office Tech Tips Advanced Techniques 24 Deed & Document Pro 25 Bankruptcy Forms 26 XX. Quick Launch. The patch the application that you’re Law Office Management 28 of little icons to the right of the working in is maximized. If OH Business Forms 30 Start button is called the Quick you’re interested, take a look Launch toolbar. Sure, you can at the sidebar on page XX of Business Dissolutions 31 put much-used shortcuts on this issue. -

Strategic Use of Ict and Communication Tools
02/2021 STRATEGIC USE OF ICT AND COMMUNICATION TOOLS CE RESPONSIBLE | BRODTO | Branimir Radaković Module I - ICT Module II - Module III - tools for Social media Impact tools optimization of working for for SEs everyday work social enterprise TAKING COOPERATION FORWARD 2 Module I - ICT tools for optimization of everyday work Project management / work tracking tools Project management tools in this case mean delegating tasks and internal project segmenting, but most of the chosen categories below can be characterised as project management tools as well. They are a must for a modern company or organization, especially for working remotely. They improve work tracking by superiors or peers, but also allows team members to organize their work in an easy and effective way. Considering the nature of a social enterprise and heterogenic business elements, they are highly recommendable. a) Asana b) Basecamp c) ProofHub d) Trello e) Airtable TAKING COOPERATION FORWARD 3 Module I - ICT tools for optimization of everyday work Project management / work tracking tools Asana Description - a web and mobile application designed to help teams organize, track, and manage work - project management, task management and delegation, productivity software Key features: - categorized by projects - every member has his or her own “profile” viewable by others - task can also be viewed in calendar mode which gives extra plainness in work organisation Pros: - combining factors as file storage, collaboration - helping to manage projects without email Cons: - free version -

Test Coverage Guide
TEST COVERAGE GUIDE Test Coverage Guide A Blueprint for Strategic Mobile & Web Testing SUMMER 2021 1 www.perfecto.io TEST COVERAGE GUIDE ‘WHAT SHOULD I BE TESTING RIGHT NOW?’ Our customers often come to Perfecto testing experts with a few crucial questions: What combination of devices, browsers, and operating systems should we be testing against right now? What updates should we be planning for in the future? This guide provides data to help you answer those questions. Because no single data source tells the full story, we’ve combined exclusive Perfecto data and global mobile market usage data to provide a benchmark of devices, web browsers, and user conditions to test on — so you can make strategic decisions about test coverage across mobile and web applications. CONTENTS 3 Putting Coverage Data Into Practice MOBILE RECOMMENDATIONS 6 Market Share by Country 8 Device Index by Country 18 Mobile Release Calendar WEB & OS RECOMMENDATIONS 20 Market Share by Country 21 Browser Index by Desktop OS 22 Web Release Calendar 23 About Perfecto 2 www.perfecto.io TEST COVERAGE GUIDE DATA INTO PRACTICE How can the coverage data be applied to real-world executions? Here are five considerations when assessing size, capacity, and the right platform coverage in a mobile test lab. Optimize Your Lab Configuration Balance Data & Analysis With Risk Combine data in this guide with your own Bundle in test data parameters (like number of tests, analysis and risk assessment to decide whether test duration, and required execution time). These to start testing with the Essential, Enhanced, or parameters provide the actual time a full- cycle or Extended mobile coverage buckets. -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

Firefox OS Overview Ewa Janczukowicz
Firefox OS Overview Ewa Janczukowicz To cite this version: Ewa Janczukowicz. Firefox OS Overview. [Research Report] Télécom Bretagne. 2013, pp.28. hal- 00961321 HAL Id: hal-00961321 https://hal.archives-ouvertes.fr/hal-00961321 Submitted on 24 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Collection des rapports de recherche de Télécom Bretagne RR-2013-04-RSM Firefox OS Overview Ewa JANCZUKOWICZ (Télécom Bretagne) This work is part of the project " Étude des APIs Mozilla Firefox OS" supported by Orange Labs / TC PASS (CRE API MOZILLA FIREFOX OS - CTNG13025) ACKNOWLEGMENTS Above all, I would like to thank Ahmed Bouabdallah and Arnaud Braud for their assistance, support and guidance throughout the contract. I am very grateful to Gaël Fromentoux and Stéphane Tuffin for giving me the possibility of working on the Firefox OS project. I would like to show my gratitude to Jean-Marie Bonnin, to all members of Orange NCA/ARC team and RSM department for their help and guidance. RR-2013-04-RSM 1 RR-2013-04-RSM 2 SUMMARY Firefox OS is an operating system for mobile devices such as smartphones and tablets. -
Oneplus 6T User Manual Index
OnePlus 6T User Manual Index 04 What’s in The Box? 24 Notch Display Settings 05 Device 25 OnePlus Fast Charging 06 Power On 26 OxygenOS 07 Setup Wizard 27 Launcher 08 Migrating Data (OnePlus Switch) 28 App Drawer 09 Insert SIM Card (SIM Card Tray) 29 Hidden Space 10 Screen Unlock 30 Notification Shade 11 Face Unlock 31 Shelf 12 Alert Slider 32 Gestures 13 Camera 33 App Long Press 14 Camera Interface 34 Reading Mode 15 Choosing Camera Modes and Settings 35 Gaming mode 16 Studio Lighting 36 Dialer 17 Nightscape 37 Messenger 18 Portrait Mode 38 Gallery 19 Video 39 Recorder 20 Video Editor 40 File Manager 21 Pro Mode 41 App Permission 22 Pro Mode - Continued 23 Optic AMOLED Display 2 Welcome Thank You! We believe in sharing the best technology, designed to be fast, smooth, and user-centric. The OnePlus 6T offers a fast and smooth experience, with an emphasis on speed. Navigating between apps, photos and games is now easier than it’s ever been. With speed at the center of its design, the OnePlus 6T now ensures that your time receives its optimum value. With our continued attention to improve swift and smooth transitions based on a sense of speed, the OnePlus 6T is our fastest product yet. A beautiful combination of sophisticated hardware and software allows you to experience speed like you’ve never done before. 3 What’s in The Box OnePlus 6T Screen Protector Translucent Case USB Type-C Cable Power Adapter SIM Tray Ejector Quick Start Guide USB Type-C 3.5mm (pre-applied) Safety Information Adapter 4 | What’s in the Box Device OxygenOS Device Alert Slider Nano SIM Slot Volume Power Sleep/Wake USB Type-C 5 | What’s in the Box Device OxygenOS Power On Turn on your OnePlus 6T by pressing and holding the <Power> button (found on the right side of the phone) for a few seconds. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -
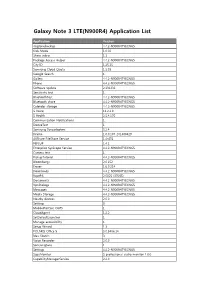
Galaxy Note 3 LTE(N900R4) Application List
Galaxy Note 3 LTE(N900R4) Application List Application Version ringtonebackup 4.4.2-N900R4TYECNG5 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-N900R4TYECNG5 City ID 1.25.15 Samsung Cloud Quota 1.5.03 Google Search 1 Gallery 4.4.2-N900R4TYECNG5 Phone 4.4.2-N900R4TYECNG5 Software update 2.131231 Sensitivity test 1 BluetoothTest 4.4.2-N900R4TYECNG5 Bluetooth share 4.4.2-N900R4TYECNG5 Calendar storage 4.4.2-N900R4TYECNG5 S Voice 11.2.2.0 S Health 2.5.4.170 Communication Notifications 1 DeviceTest 1 Samsung Syncadapters 5.2.4 Drama 1.0.0.107_201400429 AllShare FileShare Service 1.4r476 PEN.UP 1.4.1 Enterprise SysScope Service 4.4.2-N900R4TYECNG5 Camera test 1 PickupTutorial 4.4.2-N900R4TYECNG5 Bloomberg+ 2.0.152 Eraser 1.6.0.214 Downloads 4.4.2-N900R4TYECNG5 RootPA 2.0025 (37085) Documents 4.4.2-N900R4TYECNG5 VpnDialogs 4.4.2-N900R4TYECNG5 Messages 4.4.2-N900R4TYECNG5 Media Storage 4.4.2-N900R4TYECNG5 Nearby devices 2.0.0 Settings 3 MobilePrintSvc_CUPS 1 CloudAgent 1.2.2 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 POLARIS Office 5 5.0.3406.14 Idea Sketch 3 Voice Recorder 2.0.0 SamsungSans 1 Settings 4.4.2-N900R4TYECNG5 SapaMonitor S professional audio monitor 1.0.0 CapabilityManagerService 2.4.0 S Note 3.1.0 Samsung Link 1.8.1904 Samsung WatchON Video 14062601.1.21.78 Street View 1.8.1.2 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-N900R4TYECNG5 Google Search 3.4.16.1149292.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140211.01 Samsung Print Service Plugin 1.4.140410 Tasks provider 4.4.2-N900R4TYECNG5 -

A First Look at Firefox OS Security
A First Look at Firefox OS Security Daniel DeFreez∗, Bhargava Shastryy, Hao Chen∗, Jean-Pierre Seiferty ∗University of California, Davis fdcdefreez, [email protected] ySecurity in Telecommunications, Technische Universitat¨ Berlin fbshastry, [email protected] Abstract—With Firefox OS, Mozilla is making a serious push the abuse of vulnerable applications. All privileged appli- for an HTML5-based mobile platform. In order to assuage cations have a default Content Security Policy applied and security concerns over providing hardware access to web ap- are reviewed for conformance to security guidelines prior to plications, Mozilla has introduced a number of mechanisms that being distributed through the official Firefox Market. The make the security landscape of Firefox OS distinct from both Content Security Policy almost categorically prevents Cross- the desktop web and other mobile operating systems. From an Site Scripting (XSS) via JavaScript injection, and code re- application security perspective, the two most significant of these mechanisms are the the introduction of a default Content Security view should pick up any misuse of permissions or obvious Policy and code review in the market. This paper describes how security errors. This paper asks whether these mechanisms lightweight static analysis can augment these mechanisms to find are sufficient to prevent developers from making trivially vulnerabilities which have otherwise been missed. We provide preventable security blunders. We find that they are not. The examples of privileged applications in the market that contain most prevalent attack vector, without a doubt, is HTML in- vulnerabilities that can be automatically detected. jection, and .innerHTML1 is the culprit. -

Layered Mobile Device Architecture
ISSN (e): 2250 – 3005 || Volume, 08 || Issue,10|| October – 2018 || International Journal of Computational Engineering Research (IJCER) Layered Mobile Device Architecture 1Shinto Kurian 2Dr.K.Nirmala K, Research Scholar(Reg.No:PhD/10/PTE/1/2017, Madras University), Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India. Assoc. Professor,Dept. of Computer Science, Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India Corresponding Author: Shinto Kurian ABSTRACT Mobile device structure is organised in a layered architecture from electronic components to application user interface. Based on various functionalities, the mobile devices are separated into multiple layers. Each layer has well defined boundaries and interacts with each other using certain protocols. The layered separation helps the devices to segregate the functionalities in stabilized and secured manner. Depending on manufacture, the components in each layer change. Most of the mobile devices are follow a standard architecture but the components and methodologies used in each layer have differences. The degree of smoothness between the layers directly proportionate with user friendliness of the mobile device. KEYWORDS: Mobile Device, Operating system, Software, Hardware, BIOS, Firmware, User Interface. ----------------------------------------------------------------------------------------------------------------------------- ---------- Date of Submission: 15-12-2018 Date of acceptance: 31-12-2018 ---------------------------------------------------------------------------------------------------------------------------------------------------