FAR from HOME – Part 2 Active Foreign Surveillance of US Mobile Users
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Liberty Cable Negligence & Malpractice Intaling Cables
_____________________________________________________________________________ Ticket: # 1898235 - Liberty Cable Negligence & Malpractice intaling cables Date: 9/1/2017 12:05:20 PM City/State/Zip: San Juan, Puerto Rico 00926 Company Complaining About: Liberty Cable _____________________________________________________________________________ Description Liberty Cable install cable in 2 Sky Tower Bldg., which is negligent & Incompetent. 1st., they drill Cold Join. I told them it was wrong. Hence they move it in top of the cold join. The cable holds water between cable and wall hence humidity in Apt., is bound cause extensive damage in this hurricane season. I asked administration why they do not want to hold Liberty Cable responsible. No answer.., this is not transparent and I asked administration and board if they they were paid or gift. It is the only reason I can think for them to Hinder. _____________________________________________________________________________ Ticket: # 1917159 - Complaint against WKAQ Channel 2 and WAPA Channel 4 Date: 9/12/2017 12:15:44 PM City/State/Zip: San Juan, Puerto Rico 00907 Company Complaining About: Wkaq Channel 2 (telemundo) Wapa Channel 4 _____________________________________________________________________________ Description During the broadcast of emergency information by the Governor of Puerto Rico and the government of the territory of Puerto Rico during the passing of Hurricane IRMA Category 5, WKAQ Channel 2 and WAPA Channel 4 refused and cut the transmission when the governor was going to deliver -

Netvigator Application Confidential
Do not pay cash to a sales person outside of a designated HKT Shop CONFIDENTIAL CONSUMER NETVIGATOR APPLICATION FORM ID: PCDRE THINGS TO KNOW BEFORE YOU BUY 1. Your Application and Service Guide set out the NETVIGATOR Services, Extra Services and/or Now TV services to which you have subscribed ("Services"), the applicable charges including your monthly charges for the Services as well as usage based and administrative and other charges which are payable in certain circumstances (such as for installation, moving and lost equipment), and the legal entity or entities responsible for providing those Services. Additional information about your Services and our shop addresses can be found on our website at http://www.hkt.com, http://nowtv.now.com/ (for Now TV services), or our Consumer Service Hotline at 1000. 2. Your Commitment Period (if any) for the Services is described in your Application in Section B. You can terminate your subscription to any Services within the Commitment Period by giving us not less than 30 days' prior written notice. If you terminate before the expiry of the Commitment Period, you will have to pay the Early Termination Charge described in Section E below (unless a Cooling-off Period is applicable), and (where applicable) compensate us for the value of any premium received by you. If you terminate your NETVIGATOR Services, your subscription to any Now TV services will also be terminated at the same time. 3. When the Commitment Period of Now TV services expires, we will continue to provide them on a month-to-month basis at the same monthly rate. -
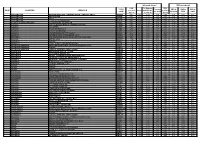
ZONE COUNTRIES OPERATOR TADIG CODE Calls
Calls made abroad SMS sent abroad Calls To Belgium SMS TADIG To zones SMS to SMS to SMS to ZONE COUNTRIES OPERATOR received Local and Europe received CODE 2,3 and 4 Belgium EUR ROW abroad (= zone1) abroad 3 AFGHANISTAN AFGHAN WIRELESS COMMUNICATION COMPANY 'AWCC' AFGAW 0,91 0,99 2,27 2,89 0,00 0,41 0,62 0,62 3 AFGHANISTAN AREEBA MTN AFGAR 0,91 0,99 2,27 2,89 0,00 0,41 0,62 0,62 3 AFGHANISTAN TDCA AFGTD 0,91 0,99 2,27 2,89 0,00 0,41 0,62 0,62 3 AFGHANISTAN ETISALAT AFGHANISTAN AFGEA 0,91 0,99 2,27 2,89 0,00 0,41 0,62 0,62 1 ALANDS ISLANDS (FINLAND) ALANDS MOBILTELEFON AB FINAM 0,08 0,29 0,29 2,07 0,00 0,09 0,09 0,54 2 ALBANIA AMC (ALBANIAN MOBILE COMMUNICATIONS) ALBAM 0,74 0,91 1,65 2,27 0,00 0,41 0,62 0,62 2 ALBANIA VODAFONE ALBVF 0,74 0,91 1,65 2,27 0,00 0,41 0,62 0,62 2 ALBANIA EAGLE MOBILE SH.A ALBEM 0,74 0,91 1,65 2,27 0,00 0,41 0,62 0,62 2 ALGERIA DJEZZY (ORASCOM) DZAOT 0,74 0,91 1,65 2,27 0,00 0,41 0,62 0,62 2 ALGERIA ATM (MOBILIS) (EX-PTT Algeria) DZAA1 0,74 0,91 1,65 2,27 0,00 0,41 0,62 0,62 2 ALGERIA WATANIYA TELECOM ALGERIE S.P.A. -

Tencent and China Mobile's Dilemma
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AIS Electronic Library (AISeL) Association for Information Systems AIS Electronic Library (AISeL) Pacific Asia Conference on Information Systems PACIS 2014 Proceedings (PACIS) 2014 FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA Jun Wu School of Economics and Management, Beijing University of Posts and Telecommunications, [email protected] Qingqing Wan School of Economics and Management, Beijing University of Posts and Telecommunications, [email protected] Follow this and additional works at: http://aisel.aisnet.org/pacis2014 Recommended Citation Wu, Jun and Wan, Qingqing, "FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA" (2014). PACIS 2014 Proceedings. 265. http://aisel.aisnet.org/pacis2014/265 This material is brought to you by the Pacific Asia Conference on Information Systems (PACIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in PACIS 2014 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact [email protected]. FROM WECHAT TO WE FIGHT: TENCENT AND CHINA MOBILE’S DILEMMA Jun Wu, School of Economics and Management, Beijing University of Posts and Telecommunications, Beijing, China, [email protected] Qingqing Wan, School of Economics and Management, Beijing University of Posts and Telecommunications, Beijing, China, [email protected] Abstract With the coming of mobile internet era, Giants in the different industry begin to compete face by face. This teaching case presents the event of charging for WeChat in China context to delineate the new challenges that Online Service Provider and Mobile Network Operator will face. -

Global Pay TV Fragments
Global pay TV fragments The top 503 pay TV operators will reach 853 million subscribers from the 1.02 billion global total by 2026. The top 50 operators accounted for 64% of the world’s pay TV subscribers by end-2020, with this proportion dropping to 62% by 2026. Pay TV subscribers by operator ranking (million) 1200 1000 143 165 38 45 800 74 80 102 102 600 224 215 400 200 423 412 0 2020 2026 Top 10 11-50 51-100 101-200 201+ Excluded from report The top 50 will lose 20 million subscribers over the next five years. However, operators beyond the top 100 will gain subscribers over the same period. Simon Murray, Principal Analyst at Digital TV Research, said: “Most industries consolidate as they mature. The pay TV sector is doing the opposite – fragmenting. Most of the subscriber growth will take place in developing countries where operators are not controlled by larger corporations.” By end-2020, 13 operators had more than 10 million pay TV subscribers. China and India will continue to dominate the top pay TV operator rankings, partly as their subscriber bases climb but also due to the US operators losing subscribers. Between 2020 and 2026, 307 of the 503 operators (61%) will gain subscribers, with 13 showing no change and 183 losing subscribers (36%). In 2020, 28 pay TV operators earned more than $1 billion in revenues, but this will drop to 24 operators by 2026. The Global Pay TV Operator Forecasts report covers 503 operators with 726 platforms [132 digital cable, 116 analog cable, 279 satellite, 142 IPTV and 57 DTT] across 135 countries. -

China Mobile (Hong Kong) Limited
SECURITIES AND EXCHANGE COMMISSION WASHINGTON, DC 20549 FORM 20-F ® © REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 OR ®X© ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the Ñscal year ended December 31, 2000 OR ® © TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission Ñle number 1-14696 China Mobile (Hong Kong) Limited (Exact Name of Registrant as SpeciÑed in Its Charter) N/A (Translation of Registrant's Name into English) Hong Kong, China (Jurisdiction of Incorporation or Organization) 60th Floor, The Center 99 Queen's Road Central Hong Kong, China (Address of Principal Executive OÇces) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Ordinary shares, par value HK$0.10 per share New York Stock Exchange, Inc.* * Not for trading, but only in connection with the listing on the New York Stock Exchange, Inc. of American depositary shares representing the ordinary shares. Securities registered or to be registered pursuant to Section 12(g) of the Act: None (Title of Class) Securities for which there is a reporting obligation pursuant to Section 15(d) of the Act: None (Title of Class) Indicate the number of outstanding shares of each of the issuer's classes of capital or common stock as of the close of the period covered by the annual report. As of December 31, 2000, 18,605,312,241 ordinary shares, par value HK$0.10 per share, were issued and outstanding. -

Mobile Phones, Social Transformation, and the Reproduction of Power in the Philippines a Dissertation Submitted
TEXTING CAPITAL: Mobile Phones, Social Transformation, and the Reproduction of Power in the Philippines A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy at George Mason University By Cecilia S. Uy-Tioco Master of Arts The New School University, 2004 Master of Arts New York University, 1996 Bachelor of Arts Ateneo de Manila University, 1992 Director: Timothy Gibson, Associate Professor Department of Communication Summer Semester 2013 George Mason University Fairfax, VA This work is licensed under a creative commons attribution-noderivs 3.0 unported license. ii DEDICATION For my mom, Joy Uy-Tioco, who encouraged me to be curious, intellectually and otherwise, and to the memory of my dad, George Uy-Tioco, who would have loved mobile phones, text messaging, and the Internet. +AMDG iii ACKNOWLEDGEMENTS It would have been impossible to complete this degree without the support of friends, family, professors, and colleagues. I must start by thanking my dissertation chair, Tim Gibson, who has been incredibly encouraging, generous, and supportive, while being firm and constructively critical. If I could be half the professor he is, I would consider myself a success. I too am a charter member of the Tim Gibson fan club. Throughout my time at the CS program Paul Smith has always challenged me and pushed me to think more critically, and for that I am most grateful. It was during a directed reading course with Mark Sample that I really began to study new media and I am grateful for his support and insights. My scholarship has been enriched by courses and conversations with various faculty members at the GMU CS program particularly, Debra Lattanzi Shutika, Roger Lancaster, Dina Copelman, Jean-Paul Dumont, Denise Albanese, Hugh Gusterson, Debra Berghoffen, Johanna Bockman, Ellen Todd, and Scott Trafton. -

Roaming User Guide
Data Roaming Tips Singtel helps you stay seamlessly connected with data roaming overseas while avoiding bill shock from unexpected roaming charges. The information below can help you make smart data roaming decisions, allowing you to enjoy your trip with peace of mind. 1. Preferred Network Operators and LTE Roaming ...................................................................................... 2 2. USA Data Roaming Plan Coverage .......................................................................................................... 13 3. Network Lock .............................................................................................................................................. 14 4. My Roaming Settings................................................................................................................................. 16 5. Data Roaming User Guide ......................................................................................................................... 16 1. Preferred Network Operators and LTE Roaming The following table lists our preferred operators offering Singtel data roaming plans and indicates their handset display names. Country Roaming Plans Operator Handset Display Albania Daily Vodafone (LTE) VODAFONE AL / voda AL / AL-02 / 276-02 Anguilla Daily Cable & Wireless C&W / 365 840 Antigua and Daily Cable & Wireless C&W / 344 920 Barbuda CLARO Argentina / CTIARG / AR310 / Claro (LTE) Claro AR Argentina Daily Telefonica (LTE) AR 07 / 722 07 / unifon / movistar Armenia Daily VEON (LTE) -

Share Swap Between Telefónica and China Unicom
La Dirección Estratégica de la Empresa. Teoría y Aplicaciones L.A. Guerras y J.E. Navas Thomson-Civitas, 2007, 4th edition www.guerrasynavas.com SHARE SWAP BETWEEN TELEFÓNICA AND CHINA UNICOM Miriam Delgado Verde Universidad Complutense de Madrid In 2005, Telefónica and China Unicom entered into a strategic alliance with the aim to operate jointly in the telecommunications industry. Initially, it took the form of a minority holding by the Spanish company in its Far Eastern counterpart when Telefónica purchased 5.38% of the Chinese operator’s capital. This initial operation was reinforced in September 2009 with a share swap between both companies, whereby Telefónica’s investment rose to 8.06% of China Unicom’s capital, whereas the latter acquired 0.9% of the Spanish telephone company. Through this new operation, Telefónica acquired a further 694 million shares, up to the aforementioned percentage, whilst China Unicom undertook to acquire 40.7 million shares in the Spanish company, which meant an investment by each party of one billion dollars (around 700 million euros at the prevailing rate of exchange). The partners agreed to keep possession of the shares for at least a year, although the agreement included joint operations over the following three years, unless either one of the parties should discharge the contract with six months’ prior notice. These joint operations included shared procurement, the development of common platforms for mobile phone services and the provision of services to multinational customers. One of the agreement’s clauses laid down a restriction on any investment in the share capital of each other’s rival companies. -

Annual Report 2018 1 CORPORATE PROFILE (CONTINUED)
CONTENTS 1 Corporate Profile 3 Statement from the Chairman 4 Statement from the Group Managing Director 8 PCCW in Numbers 10 Significant Events in 2018 12 Awards 18 Board of Directors 24 Corporate Governance Report 42 Management’s Discussion and Analysis 53 Financial Information 224 Investor Relations CORPORATE PROFILE PCCW Limited is a global company headquartered in Hong Kong which holds interests in telecommunications, media, IT solutions, property development and investment, and other businesses. The Company holds a majority interest in the HKT Trust and HKT Limited, Hong Kong’s premier telecommunications service provider and leading operator in fixed-line, broadband and mobile communication services. Beyond connectivity, HKT provides innovative smart living and business services to individuals and enterprises. PCCW also owns a fully integrated multimedia and entertainment group in Hong Kong, PCCW Media. PCCW Media operates the largest local pay-TV operation, Now TV, and is engaged in the provision of OTT (over-the-top) video service under the Viu brand in Hong Kong and other places in the region. Through HK Television Entertainment Company Limited, PCCW also operates a domestic free television service in Hong Kong. Also wholly-owned by the Group, PCCW Solutions is a leading information technology outsourcing and business process outsourcing provider in Hong Kong and mainland China. In addition, PCCW holds a majority interest in Pacific Century Premium Developments Limited, and other overseas investments. Employing over 23,600 staff, PCCW maintains a presence in Hong Kong, mainland China as well as other parts of the world. PCCW shares are listed on The Stock Exchange of Hong Kong Limited (SEHK: 0008) and traded in the form of American Depositary Receipts (ADRs) on the OTC Markets Group Inc. -

Mobile Banking and Payment in China
MOBILE COMMERCE Mobile Banking and Payment in China Wai-Ming To and Linda S.L. Lai, Macao Polytechnic Institute, China Of the more than 500 million Internet users in China as of June 2013, more than 400 million accessed the Web using mobile devices. This article investigates the development of mobile banking and payment systems in China. hina has developed into an Internet prompt payment, continue to increase. Hence, hot spot.1 In 2008, China surpassed China’s fast-growing mobile market, combined the US in number of Internet users, a with its large and growing consumer economy, number projected to reach 690 million means that it now is poised to become a global Cin 2017. 2 China is also one of the fastest growing force in mobile banking and payments. However, mobile markets in the world, with approximately a number of significant issues prevent wide-scale 451 million cellphone owners. Many of these us- adoption of this technology. ers have not yet availed themselves of 3G mobile services.3 Recent Developments Given the country’s sustained economic As Figure 1 shows, the number of online bank- growth and its 7 to 8 percent gross domestic ing users increased from 40.3 million in 2007 to product (GDP) increase in the past five years, 221.5 million in 2012, and the number of online business activities and volumes in China will payment users increased from 33.2 million to likely continue their rapid development. Online 220.7 million during the same period. The num- banking and payment systems have also rapidly ber of online banking and online payment users developed in the past few years.4 At the same increased further to 240.8 and 244.4 million, time, online retailing transactions and business- respectively, during the first half of 2013. -

Ooredoo at a Glance 2021 (Read-Only)
Ooredoo at a Glance Disclaimer • Ooredoo (Parent company Ooredoo Q.S.C.) and the group of companies which it forms part of (“Ooredoo Group”) cautions investors that certain statements contained in this document state Ooredoo Group management's intentions, hopes, beliefs, expectations, or predictions of the future and, as such, are forward-looking statements. • Ooredoo Group management wishes to further caution the reader that forward-looking statements are not historical facts and are only estimates or predictions. Actual results may differ materially from those projected as a result of risks and uncertainties including, but not limited to: • Our aBility to manage domestic and international growth and maintain a high level of customer service • Future sales growth • Market acceptance of our product and service offerings • Our aBility to secure adequate financing or equity capital to fund our operations • Network expansion • Performance of our network and equipment • Our aBility to enter into strategic alliances or transactions • Cooperation of incumBent local exchange carriers in provisioning lines and interconnecting our equipment • Regulatory approval processes • Changes in technology • Price competition • Other market conditions and associated risks • This presentation does not constitute an offering of securities or otherwise constitute an invitation or inducement to any person to underwrite, suBscriBe for or otherwise acquire or dispose of securities in any company within the Ooredoo Group. • The Ooredoo Group undertakes no oBligation