Download Full Report: a Homegrown Threat
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Dzhokhar Tsarnaev Had Murdered Krystle Marie Campbell, Lingzi Lu, Martin Richard, and Officer Sean Collier, He Was Here in This Courthouse
United States Court of Appeals For the First Circuit No. 16-6001 UNITED STATES OF AMERICA, Appellee, v. DZHOKHAR A. TSARNAEV, Defendant, Appellant. APPEAL FROM THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF MASSACHUSETTS [Hon. George A. O'Toole, Jr., U.S. District Judge] Before Torruella, Thompson, and Kayatta, Circuit Judges. Daniel Habib, with whom Deirdre D. von Dornum, David Patton, Mia Eisner-Grynberg, Anthony O'Rourke, Federal Defenders of New York, Inc., Clifford Gardner, Law Offices of Cliff Gardner, Gail K. Johnson, and Johnson & Klein, PLLC were on brief, for appellant. John Remington Graham on brief for James Feltzer, Ph.D., Mary Maxwell, Ph.D., LL.B., and Cesar Baruja, M.D., amici curiae. George H. Kendall, Squire Patton Boggs (US) LLP, Timothy P. O'Toole, and Miller & Chevalier on brief for Eight Distinguished Local Citizens, amici curiae. David A. Ruhnke, Ruhnke & Barrett, Megan Wall-Wolff, Wall- Wolff LLC, Michael J. Iacopino, Brennan Lenehan Iacopino & Hickey, Benjamin Silverman, and Law Office of Benjamin Silverman PLLC on brief for National Association of Criminal Defense Lawyers, amicus curiae. William A. Glaser, Attorney, Appellate Section, Criminal Division, U.S. Department of Justice, with whom Andrew E. Lelling, United States Attorney, Nadine Pellegrini, Assistant United States Attorney, John C. Demers, Assistant Attorney General, National Security Division, John F. Palmer, Attorney, National Security Division, Brian A. Benczkowski, Assistant Attorney General, and Matthew S. Miner, Deputy Assistant Attorney General, were on brief, for appellee. July 31, 2020 THOMPSON, Circuit Judge. OVERVIEW Together with his older brother Tamerlan, Dzhokhar Tsarnaev detonated two homemade bombs at the 2013 Boston Marathon, thus committing one of the worst domestic terrorist attacks since the 9/11 atrocities.1 Radical jihadists bent on killing Americans, the duo caused battlefield-like carnage. -

The War on Terror As a Self-Inflicted Disaster Ian S
*ğĕĖġĖğĕĖğĥ 3065*/( 10-*$:3&1035 Our Own Strength Against Us The War on Terror as a Self-Inflicted Disaster Ian S. Lustick* April 2008 &YFDVUJWF4VNNBSZ The War on Terror is much more than a colos- serious terrorist threat cannot even be a topic of sal waste. It is the most potent threat Americans public discussion. Politicians, the news media, face to their liberties and security. With one rival government agencies, defense contractors, spectacular blow al-Qaeda managed to exploit lobbyists of all kinds, universities, and the enter- the fantasies of a “New American Century” ca- tainment industry battle ferociously to increase bal inside the Bush administration and sucker revenues and pump up reputations by posing as the American people and its leaders into a re- more committed to winning the War on Terror sponse that serves its interests. The overstated, than their competitors. Frustrated by their in- but publicly honored, “War on Terror” and the ability to find any evidence of serious terrorist catastrophic invasion of Iraq associated with it activities in the U.S., law enforcement and re- rescued the jihadi movement from oblivion by lated agencies escalate techniques of pre-emp- convincing most of the Muslim world that ji- tive prosecution and entrapment to justify their hadi propaganda about the “infidel Christians enormous budgets. and Jews” was actually correct. Terror is a problem, but the War on Terror, At home, Americans have been so bam- because it turns U.S. power against America, is boozled by the hysterical imagery of the War on a catastrophe. Terror that the absence of evidence of a truly *Ian S. -

Addressing the Evolving Threat to Domestic Security
CONGRESSIONAL TESTIMONY: FOUNDATION FOR DEFENSE OF DEMOCRACIES House Committee on Homeland Security, Subcommittee on Counterterrorism and Intelligence The Future of Counterterrorism: Addressing the Evolving Threat to Domestic Security THOMAS JOSCELYN Senior Fellow Foundation for Defense of Democracies Senior Editor FDD’s Long War Journal Washington, DC February 28, 2017 www.defenddemocracy.org Thomas Joscelyn February 28, 2017 Chairman King, Ranking Member Rice, and other members of the committee, thank you for inviting me to testify today. The terrorist threat has evolved greatly since the September 11, 2001 hijackings. The U.S. arguably faces a more diverse set of threats today than ever. In my written and oral testimony, I intend to highlight both the scope of these threats, as well as some of what I think are the underappreciated risks. My key points are as follows: • The U.S. military and intelligence services have waged a prolific counterterrorism campaign to suppress threats to America. It is often argued that because no large-scale plot has been successful in the U.S. since 9/11 that the risk of such an attack is overblown. This argument ignores the fact that numerous plots, in various stages of development, have been thwarted since 2001. Meanwhile, Europe has been hit with larger-scale operations. In addition, the U.S. and its allies frequently target jihadists who are suspected of plotting against the West. America’s counterterrorism strategy is mainly intended to disrupt potentially significant operations that are in the pipeline. • Over the past several years, the U.S. military and intelligence agencies claim to have struck numerous Islamic State (or ISIS) and al Qaeda “external operatives” in countries such as Afghanistan, Iraq, Libya, Pakistan, Syria, Yemen, and elsewhere. -

30 Terrorist Plots Foiled: How the System Worked Jena Baker Mcneill, James Jay Carafano, Ph.D., and Jessica Zuckerman
No. 2405 April 29, 2010 30 Terrorist Plots Foiled: How the System Worked Jena Baker McNeill, James Jay Carafano, Ph.D., and Jessica Zuckerman Abstract: In 2009 alone, U.S. authorities foiled at least six terrorist plots against the United States. Since Septem- ber 11, 2001, at least 30 planned terrorist attacks have Talking Points been foiled, all but two of them prevented by law enforce- • At least 30 terrorist plots against the United ment. The two notable exceptions are the passengers and States have been foiled since 9/11. It is clear flight attendants who subdued the “shoe bomber” in 2001 that terrorists continue to wage war against and the “underwear bomber” on Christmas Day in 2009. America. Bottom line: The system has generally worked well. But • President Obama spent his first year and a half many tools necessary for ferreting out conspiracies and in office dismantling many of the counterter- catching terrorists are under attack. Chief among them are rorism tools that have kept Americans safer, key provisions of the PATRIOT Act that are set to expire at including his decision to prosecute foreign ter- the end of this year. It is time for President Obama to dem- rorists in U.S. civilian courts, dismantlement of onstrate his commitment to keeping the country safe. Her- the CIA’s interrogation abilities, lackadaisical itage Foundation national security experts provide a road support for the PATRIOT Act, and an attempt map for a successful counterterrorism strategy. to shut down Guantanamo Bay. • The counterterrorism system that has worked successfully in the past must be pre- served in order for the nation to be successful In 2009, at least six planned terrorist plots against in fighting terrorists in the future. -

Hearing for Majid Khan
C05403115 o (b)(1) (b)(3) Verbatim Transcript of Combatant Status Review Tribnnal Hearing for ISN 10020 OPENING PRESIDENT: This hearing shall come to order. RECORDER: This Tribunal is being conducted at 08:42 on 15 April 2007 on board U.S. Naval Base Guantanarno Bay, Cuba. The following personnel are present: Colonel United States Air Force, President, Commander United States Navy, Member, Lieutenant Colonel United States Air Force, Member, Major United States Air Force, Personal Representative, Sergeant First Class United States Army, Reporter, Major_United States Air Force, Recorder. Lieutenant Colonel_is the Judge Advocate member ofthe Tribunal. OATH SESSION 1 RECORDER: All rise. PRESIDENT: The Recorder will be sworn. Do you, Major-swear or affirm that you will faithfully perform the duties as ~signed in this Tribunal, so help you God? RECORDER: I do. PRESIDENT: The Reporter will now be sworn. The Recorder will administer the oath. RECORDER: Do you, Sergeant First Class swear that you will faithfully discharge your duties as Reporter assigned in this Tribunal, so help you God? REPORTER: [ do. PRESIDENT: We'll take a briefrecess while the Detainee is brought into the room. RECORDER: The time is 08:43 on IS Apri12007. This Tribunal is now in recess. All rise. [All personnel depart the room.] CONVENING AUTHORITY RECORDER: [All personnel return into the room at 08:48.] All rise. PRESIDENT: This hearing will come to order. You may be seated. Good morning. DETAINEE: Good morning. How are you guys doing? ISN # 10020 Enclosure (3) Page1 of50 C05403115 PRESIDENT: Very good, fine, thank you. This Tribunal is convened by order ofthe Director, Combatant Status Review Tribunals under the provisions ofhis Order of 12 February 2007. -

True and False Confessions: the Efficacy of Torture and Brutal
Chapter 7 True and False Confessions The Efficacy of Torture and Brutal Interrogations Central to the debate on the use of “enhanced” interrogation techniques is the question of whether those techniques are effective in gaining intelligence. If the techniques are the only way to get actionable intelligence that prevents terrorist attacks, their use presents a moral dilemma for some. On the other hand, if brutality does not produce useful intelligence — that is, it is not better at getting information than other methods — the debate is moot. This chapter focuses on the effectiveness of the CIA’s enhanced interrogation technique program. There are far fewer people who defend brutal interrogations by the military. Most of the military’s mistreatment of captives was not authorized in detail at high levels, and some was entirely unauthorized. Many military captives were either foot soldiers or were entirely innocent, and had no valuable intelligence to reveal. Many of the perpetrators of abuse in the military were young interrogators with limited training and experience, or were not interrogators at all. The officials who authorized the CIA’s interrogation program have consistently maintained that it produced useful intelligence, led to the capture of terrorist suspects, disrupted terrorist attacks, and saved American lives. Vice President Dick Cheney, in a 2009 speech, stated that the enhanced interrogation of captives “prevented the violent death of thousands, if not hundreds of thousands, of innocent people.” President George W. Bush similarly stated in his memoirs that “[t]he CIA interrogation program saved lives,” and “helped break up plots to attack military and diplomatic facilities abroad, Heathrow Airport and Canary Wharf in London, and multiple targets in the United States.” John Brennan, President Obama’s recent nominee for CIA director, said, of the CIA’s program in a televised interview in 2007, “[t]here [has] been a lot of information that has come out from these interrogation procedures. -

Homeland Security Implications of Radicalization
THE HOMELAND SECURITY IMPLICATIONS OF RADICALIZATION HEARING BEFORE THE SUBCOMMITTEE ON INTELLIGENCE, INFORMATION SHARING, AND TERRORISM RISK ASSESSMENT OF THE COMMITTEE ON HOMELAND SECURITY HOUSE OF REPRESENTATIVES ONE HUNDRED NINTH CONGRESS SECOND SESSION SEPTEMBER 20, 2006 Serial No. 109–104 Printed for the use of the Committee on Homeland Security Available via the World Wide Web: http://www.gpoaccess.gov/congress/index.html U.S. GOVERNMENT PRINTING OFFICE 35–626 PDF WASHINGTON : 2008 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 COMMITTEE ON HOMELAND SECURITY PETER T. KING, New York, Chairman DON YOUNG, Alaska BENNIE G. THOMPSON, Mississippi LAMAR S. SMITH, Texas LORETTA SANCHEZ, California CURT WELDON, Pennsylvania EDWARD J. MARKEY, Massachusetts CHRISTOPHER SHAYS, Connecticut NORMAN D. DICKS, Washington JOHN LINDER, Georgia JANE HARMAN, California MARK E. SOUDER, Indiana PETER A. DEFAZIO, Oregon TOM DAVIS, Virginia NITA M. LOWEY, New York DANIEL E. LUNGREN, California ELEANOR HOLMES NORTON, District of JIM GIBBONS, Nevada Columbia ROB SIMMONS, Connecticut ZOE LOFGREN, California MIKE ROGERS, Alabama SHEILA JACKSON-LEE, Texas STEVAN PEARCE, New Mexico BILL PASCRELL, JR., New Jersey KATHERINE HARRIS, Florida DONNA M. CHRISTENSEN, U.S. Virgin Islands BOBBY JINDAL, Louisiana BOB ETHERIDGE, North Carolina DAVE G. REICHERT, Washington JAMES R. LANGEVIN, Rhode Island MICHAEL MCCAUL, Texas KENDRICK B. MEEK, Florida CHARLIE DENT, Pennsylvania GINNY BROWN-WAITE, Florida SUBCOMMITTEE ON INTELLIGENCE, INFORMATION SHARING, AND TERRORISM RISK ASSESSMENT ROB SIMMONS, Connecticut, Chairman CURT WELDON, Pennsylvania ZOE LOFGREN, California MARK E. -
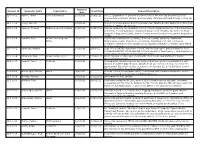
Requests Report
Received Request ID Requester Name Organization Closed Date Request Description Date 12-F-0001 Vahter, Tarmo Eesti Ajalehed AS 10/3/2011 3/19/2012 All U.S. Department of Defense documents about the meeting between Estonian president Arnold Ruutel (Ruutel) and Secretary of Defense Richard Cheney on July 19, 1991. 12-F-0002 Jeung, Michelle - 10/3/2011 - Copies of correspondence from Congresswoman Shelley Berkley and/or her office from January 1, 1999 to the present. 12-F-0003 Lemmer, Thomas McKenna Long & Aldridge 10/3/2011 11/22/2011 Records relating to the regulatory history of the following provisions of the Department of Defense Federal Acquisition Regulation Supplement (DFARS), the former Defense Acquisition Regulation (DAR), and the former Armed Services Procurement Regulation (ASPR). 12-F-0004 Tambini, Peter Weitz Luxenberg Law 10/3/2011 12/12/2011 Documents relating to the purchase, delivery, testing, sampling, installation, Office maintenance, repair, abatement, conversion, demolition, removal of asbestos containing materials and/or equipment incorporating asbestos-containing parts within its in the Pentagon. 12-F-0005 Ravnitzky, Michael - 10/3/2011 2/9/2012 Copy of the contract statement of work, and the final report and presentation from Contract MDA9720110005 awarded to the University of New Mexico. I would prefer to receive these documents electronically if possible. 12-F-0006 Claybrook, Rick Crowell & Moring LLP 10/3/2011 12/29/2011 All interagency or other agreements with effect to use USA Staffing for human resources management. 12-F-0007 Leopold, Jason Truthout 10/4/2011 - All documents revolving around the decision that was made to administer the anti- malarial drug MEFLOQUINE (aka LARIAM) to all war on terror detainees held at the Guantanamo Bay prison facility as stated in the January 23, 2002, Infection Control Standard Operating Procedure (SOP). -

HOUSE of REPRESENTATIVES—Wednesday, November 28, 2012
November 28, 2012 CONGRESSIONAL RECORD—HOUSE, Vol. 158, Pt. 11 15575 HOUSE OF REPRESENTATIVES—Wednesday, November 28, 2012 The House met at noon and was Mrs. SCHMIDT. I am honored today to 15 further requests for 1-minute called to order by the Speaker. to have Reverend Ken Johnson as our speeches on each side of the aisle. f guest chaplain. f Too often, we don’t recognize true PRAYER heroes among us. But I want to tell you REMEMBERING SERGEANT Reverend Kenneth Johnson, Seaman the story of Ken Johnson and Phil Ful- CHANNING ‘‘BO’’ HICKS United Methodist Church, Seaman, ton, two pastors in Adams County. You (Mr. GOWDY asked and was given Ohio, offered the following prayer: see, they believed that our students permission to address the House for 1 Most gracious Heavenly Father, we and our Nation need to understand the minute.) thank You for blessing the United morals of our country. And the best ex- Mr. GOWDY. Mr. Speaker, the politi- States, and we humbly ask You, Lord, ample of that is the Ten Command- cians set the policies, and others carry for your continued blessings. ments. those policies out. At least that’s the Thank You, Lord, for the honorable So they went out and they gathered way it happens in this country. It Members of the House of Representa- money together—not public money, hasn’t always been like that. Political tives. Help each Member and their fam- but donations—to put the Ten Com- leaders of yesterday also led the armies ilies with their daily struggles in life. -

Lone Wolf Terrorism and Open Source Jihad: an Explanation and Assessment
1 LONE WOLF TERRORISM AND OPEN SOURCE JIHAD: AN EXPLANATION AND ASSESSMENT Claire Wiskind, (Research Assistant, ICT) Summer 2016 ABSTRACT Al Qaeda and Daesh publish English language magazines to appeal to Western supporters and encourage them to join their cause as a fighter or as a lone wolf terrorist. A key feature of Al Qaeda’s magazine, Inspire, is a section titled Open Source Jihad, which provides aspiring jihadists with step-by-step instructions to carry out lone terror attacks in the West. By examining ten attack types that have been published over the past six years, this paper explains Open Source Jihad, presents cases where these types of attacks have been carried out, and assesses the threat presented by the easy access to Open Source Jihad. * The views expressed in this publication are solely those of the author(s) and do not necessarily reflect the views of the International Institute for Counter-Terrorism (ICT). 2 Table of Contents INTRODUCTION ................................................................................................ 3 Lone Wolf Terrorism ......................................................................................... 3 English Language Literature: Dabiq and Inspire .............................................. 7 Open Source Jihad .......................................................................................... 9 OPEN SOURCE JIHAD ATTACK INSTRUCTIONS ..................................... 12 Attacks carried out .......................................................................................... -

Military Commissions: a Place Outside the Law’S Reach
MILITARY COMMISSIONS: A PLACE OUTSIDE THE LAW’S REACH JANET COOPER ALEXANDER* “We have turned our backs on the law and created what we believed was a place outside the law’s reach.” Colonel Morris D. Davis, former chief prosecutor of the Guantánamo military commissions1 Ten years after 9/11, it is hard to remember that the decision to treat the attacks as the trigger for taking the country to a state of war was not inevitable. Previous acts of terrorism had been investigated and prosecuted as crimes, even when they were carried out or planned by al Qaeda.2 But on September 12, 2001, President Bush pronounced the attacks “acts of war,”3 and he repeatedly defined himself as a “war president.”4 The war * Frederick I. Richman Professor of Law, Stanford Law School. I would like to thank participants at the 2011 Childress Lecture at Saint Louis University School of Law and a Stanford Law School faculty workshop for their comments, and Nicolas Martinez for invaluable research assistance. 1 Ed Vulliamy, Ten Years On, Former Chief Prosecutor at Guantanamo Slams ‘Camp of Torture,’ OBSERVER, Oct. 30, 2011, at 29. 2 Previous al Qaeda attacks that were prosecuted as crimes include the 1993 bombing of the World Trade Center, the Manila Air (or Bojinka) plot to blow up a dozen jumbo jets, and the 1998 embassy bombings in East Africa. Mary Jo White, Prosecuting Terrorism in New York, MIDDLE E.Q., Spring 2001, at 11, 11–14; see also Christopher S. Wren, U.S. Jury Convicts 3 in a Conspiracy to Bomb Airliners, N.Y. -

BOSTON MARATHON BOMBING I. INTRODUCTION on 15 April 2013
BOSTON MARATHON BOMBING I. INTRODUCTION On 15 April 2013 the whole world was shocked by the news of an explosion that occur in Boston. Two bombs occured near the finish line on the spectator side of the Boston Marathon. The explosion killed 3 people, who were spectator and injured many other who attended. The 3 victims who were killed and they are Krystle Campbell, the second victim was an 8 years old child name Martin Richard, and the last victim is a woman name Lu Lingzi who was a Chinese citizen. Around 134 were wounded and 15 of them were seriously injured. Citing from dailymail reports on Tuesday, April 16, 2013 which clearly stated that there were actually seven bombs planted on the occasion . However, only two of them exploded near the finish line with a gap of about 12 seconds. The location of the explosion is only 50 - 100 meters from the finish line. Officers came straight towards the location of the explosion and search for any suspicious objects . At the scene , there were a lot of bags and the equipment of the athlete marathon runner who were abandoned simply because they were rushing to save themselves . The scene was indeed very chaotic. This bombing was sudden, there were no threat before the incident and people were very much unaware that this incident was likely to happen. Therefore, according to the principle of war, this fall under the category of “surprise”. “Surprise” principle of war means, as the name suggest, a sudden attack. This means that this incident was done at a time or place or in a manner at which the other party/target is unprepared.