Fingerprinting Explained: How It Works & How to Block It
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -

Podcast Presentation
3/18/2009 Today’s Goals Podcasts: Understanding, 1. What is a podcast? Creating, and Deploying them 2. How do I get podcasts? 3. How do I play podcasts? 4. Why should I care about podcasts for Dr. Rick Jerz ediducation? 5. How do I produce my own audio podcasts? [email protected] 6. How do I deliver (deploy) my own podcasts? www.rjerz.com 1 © 2009 rjerz.com 2 © 2009 rjerz.com Demos 1) What is a Podcast? • It must be nothing, since the “podcast” is not in my dictionary. • It is something only children do. • It has something to do with fishing. • It is a radio talk show. • It a music file. • It is a TV program. • It is a lecture. 3 © 2009 rjerz.com 4 © 2009 rjerz.com Podcast Definition1 Rick’s Podcast Definition • Podcasting is a new format for distributing A method of obtaining (subscribing) audio and video content via the Internet. Actually, podcasting is just multimedia computer files (episodes), usually content enclosed into an RSS file. audio (mp3) or video (m4v), from a • RSS means Really Simple Syndication. RSS is a catalog (RSS feed, XML) on the special format based on XML. In fact, RSS Internet (website), and having them feeds are XML files containing data according to the RSS specification, and usually located automatically delivered to your on a website. computer and then to your iPod (or • XML: an HTML‐like file for handling data. other multimedia player) • HTML: Hyper Text Markup Language 1 ‐ http://www.rss‐specification.com/sitemap.htm 5 © 2009 rjerz.com 6 © 2009 rjerz.com 1 3/18/2009 2) How do I get podcasts? iTunes: An Aggregator -
![Browser Versions Carry 10.5 Bits of Identifying Information on Average [Forthcoming Blog Post]](https://docslib.b-cdn.net/cover/0737/browser-versions-carry-10-5-bits-of-identifying-information-on-average-forthcoming-blog-post-190737.webp)
Browser Versions Carry 10.5 Bits of Identifying Information on Average [Forthcoming Blog Post]
Browser versions carry 10.5 bits of identifying information on average [forthcoming blog post] Technical Analysis by Peter Eckersley This is part 3 of a series of posts on user tracking on the modern web. You can also read part 1 and part 2. Whenever you visit a web page, your browser sends a "User Agent" header to the website saying what precise operating system and browser you are using. We recently ran an experiment to see to what extent this information could be used to track people (for instance, if someone deletes their browser cookies, would the User Agent, alone or in combination with some other detail, be enough to re-create their old cookie?). Our experiment to date has shown that the browser User Agent string usually carries 5-15 bits of identifying information (about 10.5 bits on average). That means that on average, only one person in about 1,500 (210.5) will have the same User Agent as you. On its own, that isn't enough to recreate cookies and track people perfectly, but in combination with another detail like an IP address, geolocation to a particular ZIP code, or having an uncommon browser plugin installed, the User Agent string becomes a real privacy problem. User Agents: An Example of Browser Characteristics Doubling As Tracking Tools When we analyse the privacy of web users, we usually focus on user accounts, cookies, and IP addresses, because those are the usual means by which a request to a web server can be associated with other requests and/or linked back to an individual human being, computer, or local network. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -
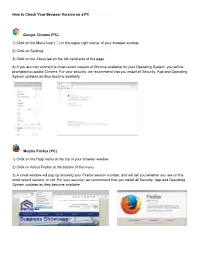
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked. -

Tutorial URL Manager Pro Tutorial
Tutorial URL Manager Pro Tutorial Version 3.3 Summer 2004 WWW http://www.url-manager.com Email mailto:[email protected] Copyright © 2004 Alco Blom All Rights Reserved - 1 - Tutorial Installation Requirements URL Manager Pro 3.3 requires Mac OS X 10.2 or higher. On Mac OS X 10.1 you can use URL Manager Pro 3.1.1. URL Manager Pro 2.8 is still available for Mac OS 8 users. The bundle size of URL Manager Pro 3.3 is around 8 MB, including this user manual and localizations for English, Japanese, German, French, Spanish and Italian, which are all included in the default package. Installing Installation is very easy, just move URL Manager Pro into the Applications folder. To start using URL Manager Pro, simply double-click the application icon. Optional: You may want to install the Add Bookmark Contextual Menu Item plug-in. The Add Bookmark plug-in can be installed using the URLs tab of the Preferences Window of URL Manager Pro. The plug-in will then be copied to: ~/Library/Contextual Menu Items/ Where ~ is the customary Unix shorthand to indicate the user's home directory. For more information, go to the Add Bookmark Web page or the Contextual Menu Item section in the Special Features chapter. The Bookmark Menu Extra While URL Manager Pro is running, it automatically adds the Bookmark Menu Extra to the menu bar. With the Bookmark Menu Extra you have access to your bookmarks from within any application, including your web browser. The Bookmark Menu Extra is located in the right part of your menu bar (see below). -

Longitudinal Characterization of Browsing Habits
Please cite this paper as: Luca Vassio, Idilio Drago, Marco Mellia, Zied Ben Houidi, and Mohamed Lamine Lamali. 2018. You, the Web, and Your Device: Longitudinal Charac- terization of Browsing Habits. ACM Trans. Web 12, 4, Article 24 (November 2018), 30 1 pages. https://doi.org/10.1145/3231466 You, the Web and Your Device: Longitudinal Characterization of Browsing Habits LUCA VASSIO, Politecnico di Torino IDILIO DRAGO, Politecnico di Torino MARCO MELLIA, Politecnico di Torino ZIED BEN HOUIDI, Nokia Bell Labs MOHAMED LAMINE LAMALI, LaBRI, Université de Bordeaux Understanding how people interact with the web is key for a variety of applications – e.g., from the design of eective web pages to the denition of successful online marketing campaigns. Browsing behavior has been traditionally represented and studied by means of clickstreams, i.e., graphs whose vertices are web pages, and edges are the paths followed by users. Obtaining large and representative data to extract clickstreams is however challenging. The evolution of the web questions whether browsing behavior is changing and, by consequence, whether properties of clickstreams are changing. This paper presents a longitudinal study of clickstreams in from 2013 to 2016. We evaluate an anonymized dataset of HTTP traces captured in a large ISP, where thousands of households are connected. We rst propose a methodology to identify actual URLs requested by users from the massive set of requests automatically red by browsers when rendering web pages. Then, we characterize web usage patterns and clickstreams, taking into account both the temporal evolution and the impact of the device used to explore the web. -

Web Browsing and Communication Notes
digital literacy movement e - learning building modern society ITdesk.info – project of computer e-education with open access human rights to e - inclusion education and information open access Web Browsing and Communication Notes Main title: ITdesk.info – project of computer e-education with open access Subtitle: Web Browsing and Communication, notes Expert reviwer: Supreet Kaur Translator: Gorana Celebic Proofreading: Ana Dzaja Cover: Silvija Bunic Publisher: Open Society for Idea Exchange (ODRAZI), Zagreb ISBN: 978-953-7908-18-8 Place and year of publication: Zagreb, 2011. Copyright: Feel free to copy, print, and further distribute this publication entirely or partly, including to the purpose of organized education, whether in public or private educational organizations, but exclusively for noncommercial purposes (i.e. free of charge to end users using this publication) and with attribution of the source (source: www.ITdesk.info - project of computer e-education with open access). Derivative works without prior approval of the copyright holder (NGO Open Society for Idea Exchange) are not permitted. Permission may be granted through the following email address: [email protected] ITdesk.info – project of computer e-education with open access Preface Today’s society is shaped by sudden growth and development of the information technology (IT) resulting with its great dependency on the knowledge and competence of individuals from the IT area. Although this dependency is growing day by day, the human right to education and information is not extended to the IT area. Problems that are affecting society as a whole are emerging, creating gaps and distancing people from the main reason and motivation for advancement-opportunity. -

One Page Series: Mac OS X -- Ipv6 and Browsing the Web Via Firefox, Camino, Opera and Safari
One Page Series: Mac OS X -- IPv6 and Browsing the Web Via Firefox, Camino, Opera and Safari [If you haven t already done so, begin with One Page Series: Mac OS X -- Enabling Native IPv6 Via Stateless Autoconfiguration ] If you don t already have Firefox on your Mac, you can download it for free from http://www.mozilla.com/firefox/ If you don t already have Camino on your Mac, you can download it for free from http://caminobrowser.org/ If you don t already have Opera on your Mac, you can download it for free from http://www.opera.com/ Safari is another option, bundled for free with Mac OS X. You can find Safari in your Mac s Applications folder. Browsing the IPv6 Web With Firefox (or Camino) Firefox (and Camino) are both IPv6 aware, but need one tweak to work properly with IPv6. Launch Firefox (or Camino) and go to about:config Filter on ipv6 Click on network.dns.disableIPv6 to set the value for that preference item to false You only need to adjust this setting once -- it will be remembered from then on Now try using IPv6 by going to http://ipv6.google.com/ You should see a dancing Google Browsing the IPv6 Web With Opera Opera is all set to work with IPv6 web sites, just launch Opera and stick in an IPv6 URL and Opera will go to that site. Browsing the IPv6 Web With Safari There is one key thing to know about Safari and IPv6, and that is that in some versions of OS X and Safari, it likes IPv4 more than it likes IPv6. -

RSA Adaptive Authentication (On-Premise) 7.2 Integration Guide
RSA® Adaptive Authentication (On-Premise) 7.2 Integration Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm Trademarks RSA, the RSA Logo, BSAFE and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries. All other trademarks used herein are the property of their respective owners. For a list of EMC trademarks, go to www.emc.com/legal/emc-corporation-trademarks.htm#rsa. License agreement This software and the associated documentation are proprietary and confidential to EMC, are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice below. This software and the documentation, and any copies thereof, may not be provided or otherwise made available to any other person. No title to or ownership of the software or documentation or any intellectual property rights thereto is hereby transferred. Any unauthorized use or reproduction of this software and the documentation may be subject to civil and/or criminal liability. This software is subject to change without notice and should not be construed as a commitment by EMC. Note on encryption technologies This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulations should be followed when using, importing or exporting this product. Distribution Use, copying, and distribution of any EMC software described in this publication requires an applicable software license.