The Import Wizard Handbook
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Free Email Software Download Best Free Email Client 2021
free email software download Best Free Email Client 2021. This article is all about best free email clients and how they can help you be more productive. We also talk about Clean Email, an easy-to-use email cleaner compatible with virtually all major email services. But before we go over the best email clients for 2021, we believe that we should first explain what advantages email clients have over web-based interfaces of various email services. Clean Email. Take control of your mailbox. What Is an Email Client and Why Should I Use One? If you’re like most people, you probably check your email at least once every day. And if you’re someone whose work involves communication with customers, clients, and coworkers, the chances are that you deal with emails all the time. Even though we spend so much time writing, forwarding, and managing emails, we hardly ever pause for a moment and think about how we could improve our emailing experience. We use clunky web interfaces that are not meant for professional use, we accept outdated applications as if alternatives didn’t exist, and we settle for the default email apps on our mobile devices even though app stores are full of excellent third-party email apps. Broadly speaking, an email client is a computer program used to access and manage a user’s email. But when we use the term email client in this article, we only mean those email clients that can be installed on a desktop computer or a mobile device—not web-based email clients that are hosted remotely and are accessible only from a web browser. -

Resurrect Your Old PC
Resurrect your old PCs Resurrect your old PC Nostalgic for your old beige boxes? Don’t let them gather dust! Proprietary OSes force users to upgrade hardware much sooner than necessary: Neil Bothwick highlights some great ways to make your pensioned-off PCs earn their keep. ardware performance is constantly improving, and it is only natural to want the best, so we upgrade our H system from time to time and leave the old ones behind, considering them obsolete. But you don’t usually need the latest and greatest, it was only a few years ago that people were running perfectly usable systems on 500MHz CPUs and drooling over the prospect that a 1GHz CPU might actually be available quite soon. I can imagine someone writing a similar article, ten years from now, about what to do with that slow, old 4GHz eight-core system that is now gathering dust. That’s what we aim to do here, show you how you can put that old hardware to good use instead of consigning it to the scrapheap. So what are we talking about when we say older computers? The sort of spec that was popular around the turn of the century. OK, while that may be true, it does make it seem like we are talking about really old hardware. A typical entry-level machine from six or seven years ago would have had something like an 800MHz processor, Pentium 3 or similar, 128MB of RAM and a 20- 30GB hard disk. The test rig used for testing most of the software we will discuss is actually slightly lower spec, it has a 700MHz Celeron processor, because that’s what I found in the pile of computer gear I never throw away in my loft, right next to my faithful old – but non-functioning – Amiga 4000. -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Argosoft Mail Server Pro User Guide
http://www.argosoft.com Argosoft Mail Server Pro User Guide June 2002 1 Introduction Thank you for choosing Argosoft Mail Server Pro. This lightweight and extremely affordable mail server is robust, stable, easy to configure, easy to manage and is fully capable of competing head to head with any mail server on the market. It can perform all basic e-mail tasks, and much more. It is fully functional mail system, which supports most popular protocols, SMTP, POP3, Finger, and has a built-in Web server, to give users quick and easy access to their email via any Web browser, which supports HTTP 1.0 or later. The web interface can also be used to administer the mail server. While this easy to use mail server is pretty much obvious in terms of use there are few little things that even a seasoned e-mail expert may not stumble across immediately. This document is basic guide to getting started! Features • Has true support of multiple domains - you can create accounts with the same name, which belong to different domains • Supports multiple IP homes (virtual domains) • Has built in mailing list server • Has WAP interface • Allows setup of domain administrators - users who can change domain related information via the Web interface; • Filtering of mail according to IP addresses of server which attempts to relay mail to local users • ORDB and MAPS support • Supports distribution lists; • Supports auto responders; • Supports basic filters; • Unlimited message size (there is a limit of 5 Megs for freeware version); • Can listen on single IP address, rather than all addresses available on your computer; • Has built-in web server. -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Designing a User Interface for the Innovative E-Mail Client Semester Thesis
Designing a User Interface for the Innovative E-mail Client Semester Thesis Student: Alexandra Burns Supervising Professor: Prof. Bertrand Meyer Supervising Assistants: Stephanie Balzer, Joseph N. Ruskiewicz December 2005 - April 2006 1 Abstract Email Clients have become a crucial application, both in business and for per- sonal use. The term information overload refers to the time consuming issue of keeping up with large amounts of incoming and stored email. Users face this problem on a daily basis and therefore benefit from an email client that allows them to efficiently search, display and store their email. The goal of this thesis is to build a graphical user interface for the innovative email client developed in a previous master thesis. It also explores the possibilities of designing a user interface outside of the business rules that apply for commercial solutions. 1 Contents 1 Introduction 4 2 Existing Work 6 2.1 ReMail ................................. 6 2.1.1 Methods ............................ 6 2.1.2 Problems Identified ...................... 7 2.1.3 Proposed Solutions ...................... 7 2.1.4 Assessment .......................... 8 2.2 Inner Circle .............................. 8 2.2.1 Methods ............................ 8 2.2.2 Problems Identified ...................... 9 2.2.3 Proposed Solutions ...................... 9 2.2.4 Assessment .......................... 10 2.3 TaskMaster .............................. 10 2.3.1 Methods ............................ 10 2.3.2 Problems Identified ...................... 11 2.3.3 Proposed Solution ...................... 11 2.3.4 Assessment .......................... 12 2.4 Email Overload ............................ 12 2.4.1 Methods ............................ 12 2.4.2 Problems Identified ...................... 13 2.4.3 Proposed Solutions ...................... 13 2.4.4 Assessment .......................... 14 3 Existing Solutions 16 3.1 Existing Email Clients ....................... -

Milax - Opensolaris Small Livecd Distro Alexander R
USE IMPROVE EVANGELIZE MilaX - OpenSolaris small LiveCD distro Alexander R. Eremin MilaX Developer USE IMPROVE EVANGELIZE Can Solaris become as small as DSL? Solaris 2 USE IMPROVE EVANGELIZE DSS 0.1 Feb 2008 CDDL v.1 MilaX 0.1, 0.1.1 Feb 2008 MilaX 0.2 Mar 2008 Milax 0.3 May 2008 June 2008 MilaX 0.3.1 MilaX 0.3.1 server 3 USE IMPROVE EVANGELIZE Last version released June 10 2008 4 USE IMPROVE EVANGELIZE MilaX LiveCD, LiveUSB USE IMPROVE EVANGELIZE Virtualizing MilaX LiveCD,LiveUSB Qemu VirtualBox VMware USE IMPROVE EVANGELIZE MilaX advantages ● Small size ● Fast boot ● Loading live image from RAM ● Booting from various storage devices ● People can try small Solaris without installing on the harddisk. ● All Solaris features: dtrace,zfs, zones,e.t.c ● Latest drivers and bugfixes ● Two versions: desktop and server USE IMPROVE EVANGELIZE When MilaX is the best choice? ● Old PC's ● Not enough RAM ● Not enough free disk space ● Fast and small server (0.3.1 server) ● Fast developing (0.3.1 server) ● Virtual testing USE IMPROVE EVANGELIZE MilaX Filesystem Ramdisk 105mb, UFS Root FS /,/lib,/dev,/devices,/var Ramdisk Swap RAM /usr (RAM < 512mb) /usr, /alex, /root, /tmp Ram > 512MB HSFS Filesystem (/usr mount) LOFI Pseudo Device /.cdrom/usr.zlib HSFS Filesystem (/.cdrom mount) MilaX Live CD USE IMPROVE EVANGELIZE Milax 0.3.1 Apps Desktop version ● Gtk-Terminal, Beaver, Netsurf, Sylpheed, Midnight Commander, emelFM, XMMS, Xpdf, VNC viewer, Rdesktop, Nmap, gFTP, gPicview, Conky, XChat, Xpad. Server version ● Apache, PHP, Samba and NFS servers, GCC, GMake, Midnight Commander, Pine, Mutt, Elinks, Lynx. -
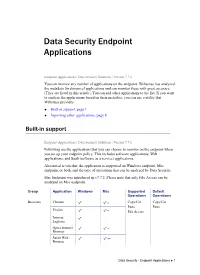
Data Security Endpoint Applications
Data Security Endpoint Applications Endpoint Applications | Data Security Solutions | Version 7.7.x You can monitor any number of applications on the endpoint. Websense has analyzed the metadata for dozens of applications and can monitor these with great accuracy. (They are listed in this article.) You can add other applications to the list. If you want to analyze the applications based on their metadata, you can use a utility that Websense provides. Built-in support, page 1 Importing other applications, page 8 Built-in support Endpoint Applications | Data Security Solutions | Version 7.7.x Following are the applications that you can choose to monitor on the endpoint when you set up your endpoint policy. This includes software applications, Web applications, and SaaS (software as a service) applications. Also noted is whether the application is supported on Windows endpoint, Mac endpoint, or both, and the type of operations that can be analyzed by Data Security. Mac Endpoint was introduced in v7.7.2. Please note that only File Access can be analyzed on Mac endpoint. Group Application Windows Mac Supported Default Operations Operations Browsers Chrome * Copy/Cut Copy/Cut Paste Paste Firefox * File Access Internet Explorer Opera Internet * Browser Safari Web ** Browser Data Security - Endpoint Applications 1 Data Security Endpoint Applications Group Application Windows Mac Supported Default Operations Operations CD Burners Acoustica Copy/Cut File Access MP3 CD Paste Burner File Access Alcohol 120% Alcohol Launcher CD Mate Disk Utility -
Malware: Computer Viruses, Spyware, and Key-Loggers
Certificates for cs.washington.edu 1 Certificates for GMail Important fields: Testing SSL Configuration (1) 3 Client completed verification of received certificate chain Testing SSL Configuration (2) 4 Received certificate chain (two certificates) Size of received certificate chain Testing SSL Configuration (3) 5 Issued session identifier (Session-ID) for stateful TLS resume. Example from “High Performance Browser Networking” Where to Use SSL? 6 Login page? Where else? What about JavaScript includes? Image includes? Why not encrypt everything? Where to Use SSL? 7 Some browsers may not support SSL SSL may decrease performance somewhat. If users are downloading large, public files, there may be a system burden to encrypt these each time. You will probably want the home page accessible via HTTP, so that users don't have to remember to type https to get to it. Firesheep (2010) 8 Assume you are using the facebook.com site over an unsecured Wi-Fi network such as in shopping malls and coffee shops. When you visit the Facebook site, you are required to enter the username and password. When you send that request and on successful login, Facebook sends you an authentication token in the clear which is then sent every time you browse Facebook pages Firesheep 9 Facebook Switches to HTTPS in 2012 10 Lab-2 11 Part 1 Part 2 Black-box fuzzing is far C programming is tricky from easy Bounds are far from obvious even when Very little insight into reasoning about a short program behavior function Makes you appreciate Makes you appreciate programming in Java or having access to C# where array accesses source code! are checked at runtime! Lab-2: Survey 12 Part 1 Part 2 A. -

Visualization of Client-Side Web Browsing and Email Activity
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis Collection 2009-06 Visualization of client-side web browsing and email activity Roussas, Gregory. Monterey, California. Naval Postgraduate School http://hdl.handle.net/10945/4738 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS VISUALIZATION OF CLIENT-SIDE WEB BROWSING AND EMAIL ACTIVITY by Gregory Roussas June 2009 Thesis Advisor: Cynthia E. Irvine Second Reader: Chris S. Eagle Approved for public release; distribution is unlimited THIS PAGE INTENTIONALLY LEFT BLANK ii Form Approved REPORT DOCUMENTATION PAGE OMB No. 0704–0188 The public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instructions, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden to Department of Defense, Washington Headquarters Services, Directorate for Information Operations and Reports (0704–0188), 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202–4302. Respondents should be aware that notwithstanding any other provision of law, no person shall be subject to any penalty for failing to comply with a collection of information if it does not display a currently valid OMB control number. PLEASE DO NOT RETURN YOUR FORM TO THE ABOVE ADDRESS. 1. REPORT DATE (DD–MM–YYYY) 2. REPORT TYPE 3. DATES COVERED (From — To) 22–6–2009 Master’s Thesis 2007-09-21—2009-06-19 4. TITLE AND SUBTITLE 5a. CONTRACT NUMBER 5b. GRANT NUMBER Visualization of Client-Side Web Browsing and Email Activity DUE 0414102 5c. -

Fedora 14 User Guide
Fedora 14 User Guide Using Fedora 14 for common desktop computing tasks Fedora Documentation Project User Guide Fedora 14 User Guide Using Fedora 14 for common desktop computing tasks Edition 1.0 Author Fedora Documentation Project [email protected] Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https://fedoraproject.org/wiki/ Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. -

Guidelines on Electronic Mail Security
Special Publication 800-45 Version 2 Guidelines on Electronic Mail Security Recommendations of the National Institute of Standards and Technology Miles Tracy Wayne Jansen Karen Scarfone Jason Butterfield NIST Special Publication 800-45 Guidelines on Electronic Mail Security Version 2 Recommendations of the National Institute of Standards and Technology Miles Tracy, Wayne Jansen, Karen Scarfone, and Jason Butterfield C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 February 2007 U .S. Department of Commerce Carlos M. Gutierrez, Secretary Technology Administration Robert C. Cresanti, Under Secretary of Commerce for Technology National Institute of Standards and Technology William Jeffrey, Director Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-45 Version 2 Natl. Inst. Stand. Technol. Spec. Publ. 800-45 Version 2, 139 pages (Feb.