Protecting the Privacy of the World's Wealthiest Families
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
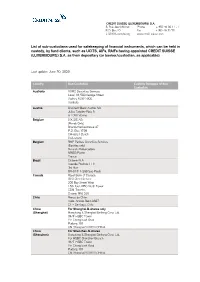
List of Sub-Custodians Used for Safekeeping of Financial Instruments
CREDIT SUISSE (LUXEMBOURG) S.A. 5, Rue Jean Monnet Phone + 352 46 00 11 - 1 P.O. Box 40 Fax + 352 46 32 70 L-2010 Luxembourg www.credit-suisse.com List of sub-custodians used for safekeeping of financial instruments, which can be held in custody, by fund clients, such as UCITS, AIFs, RAIFs having appointed CREDIT SUISSE (LUXEMBOURG) S.A. as their depositary (or banker/custodian, as applicable) Last update: June 30, 2020 Country Sub-Custodian Custody Delegate of Sub- Custodian Australia HSBC Securities Services Level 13, 580 George Street Sydney NSW 2000 Australia Austria UniCredit Bank Austria AG Julius Tandler-Platz 3 A-1090 Vienna Belgium SIX SIS AG (Bonds Only) Brandschenkestrasse 47 P.O. Box 1758 CH-8021 Zurich Switzerland Belgium BNP Paribas Securities Services (Equities only) 9 rue du Débarcadère 93500 Pantin France Brazil Citibank N.A. Avenida Paulista 1111 3rd floor BR-01311-290 Sao Paulo Canada Royal Bank of Canada GSS Client Service 200 Bay Street West 15th floor, RBC North Tower CDN-Toronto, Ontario M5J 2J5 Chile Banco de Chile Avda. Andrés Bello 2687 CL – Santiago, Chile China For Shanghai-B-shares only (Shanghai) Hongkong & Shanghai Banking Corp. Ltd. 34/F HSBC Tower Yin Cheng East Road Pudong 101 CN-Shanghai 200120 CHINA China For Shenzhen-B-shares (Shenzhen) Hongkong & Shanghai Banking Corp. Ltd. For HSBC Shenzhen Branch 34/F HSBC Tower Yin Cheng East Road Pudong 101 CN-Shanghai 200120 CHINA Colombia Cititrust Colombia S.A. Sociedad Fiduciaria Carrera 9A No. 99-02 First Floor Santa Fé de Bogotá D.C. -

Citibank Europe Plc Customer Information for the Purpose of Providing the Investment Services
CITIBANK EUROPE PLC CUSTOMER INFORMATION FOR THE PURPOSE OF PROVIDING THE INVESTMENT SERVICES Valid and effective from 1 April 2021 Citibank Europe plc, organizační složka Prague Czech Republic Citibank Europe plc, a company established and existing under the laws of Ireland, with its registered office at North Wall Quay 1, Dublin, Ireland, registered in the Company Register in the Irish Republic under No. 132781, conducting business in the Czech Republic through Citibank Europe plc, organizační složka, with its registered office at Bucharova 2641/14, Prague 5, Stodůlky, postal code 158 02, ID No. 28198131, incorporated in the Commercial Register administered by the Municipal Court in Prague, File Number A 59288. Member of Citigroup. The supervisory authority of Citibank Europe plc is the Central Bank of Ireland and to limited extent European Central Bank and Czech National Bank. Citibank Europe plc, a company established and existing under the laws of Ireland, with its registered office at North Wall Quay 1, Dublin, Ireland, registered in the Commercial Register in the Irish Republic under No. 132781, conducting its business in the Czech Republic through Citibank Europe plc, organizační složka, with its registered office at Praha 5, Stodůlky, Bucharova 2641/14, postal code: 158 02, Company ID No. 28198131, incorporated in the Commercial Register administered by the Municipal Court in Prague, File A 59288 (hereinafter “the Bank”). hereby announces to its customers, to whom it provides the investment services pursuant to the applicable legal regulations governing the capital market business, in particular Act No. 256/2004 Coll., on Undertaking on the Capital Market, as amended and Commission Delegated Regulation (EU) 2017/565 of 25 April 2016 (hereinafter the "Legal Regulations"), certain information that the Bank is obliged to communicate to its customers under the aforementioned Legal Regulations. -

Electronic Access and User Agreement Please Read
ELECTRONIC ACCESS AND USER AGREEMENT PLEASE READ THIS ELECTRONIC ACCESS AND USER AGREEMENT (THE “AGREEMENT”) CAREFULLY. IT GOVERNS YOUR ACCESS TO AND USE OF ONE OR MORE ONLINE PLATFORMS FOR FOREIGN EXCHANGE TRADING AND RELATED INFORMATION OFFERED BY CITIBANK (THE “SYSTEM”). YOU MUST AGREE TO THE TERMS OF THIS AGREEMENT BEFORE BEING GRANTED ACCESS TO THE SYSTEM. This Agreement contains the terms and conditions under which You and Your employer (“Your Firm” which, if You are a third party trading adviser, investment manager or other agent (“Agent”), includes your principal) are provided with access to the System and permitted to use the products and services offered on the System, such as the information research, data, analytical tools, software, video, audio, graphics, pricing information and other content available on the System (“System Content”), and, where applicable, to transact and confirm foreign exchange and Bullion spot, forward, swaps and/or options transactions (“Transactions”), which may include use of proprietary and/or licensed Citibank algorithms (collectively, the “Algo Strategies” and each an “Algo Strategy”) as described and made available via the System or at www.citifx.com. For the purposes of this Agreement, Bullion shall mean gold, silver, platinum or palladium. This Agreement will amend and replace any previous agreement entered into by You or Your Firm covering Your use of and access to the System. References to “You” or “Your” are to both you as an individual or, if applicable, as an Agent and to Your Firm, unless expressly stated otherwise. References to “Citibank” are to Citibank, N.A. or its affiliated entities as identified in the Country Annex (as defined in Section 5 below) applicable to You. -

Settlement Instructions
SETTLEMENT INSTRUCTIONS BUYER/SELL Custodian DEAG / REAG SetClear ID / A/C Number at Market A/C Name Name Local Agent Executing Custodian Broker BIC Australia Citigroup Pty CITIAU3X CRLSUS3SCLR 2077070000 SETCLEAR PTE. Limited CHESS Code: LTD. - 20018 TRADEBOOK Austria Citibank N.A., CITIITMX CRLSUS3SCLR 7902299 SETCLEAR PTE Milan Branch Broker Code : LTD CIM TRADEBOOK Belgium Citibank Intl Plc. CITTGB2L CRLSUS3SCLR 0006005289 TRADEBOOK Brazil Concordia 95P REAG - for CNCVBRR1 CNPJ: Broker # 23 Corretora S.A sales 52.904.346/001- CVMCC 95P DEAG - for 08 purchases Canada Citibank Canada CITICATTXXX CRLSUS3SCLR 6015890002 SETCLEAR PTE. CUID: CITC LTD. - TRADEBOOK Cyprus Citibank CITIGRAA CRLSUS3SCLR 801819 TRADEBOOK International Plc, Greece Branch Czech Rep. Citibank Europe CITICZPX CRLSUS3SCLR 1090076957 TRADEBOOK plc, organizační složka Denmark Nordea Bank NDEADKKK CRLSUS3SCLR 0200010060180 Tradebook Denmark A/S 21 Estonia Nordea Bank HABAEE2X NDEAFIHH 99000546397 Nordea Bank Finland Plc. Danmark A/S - SetClear/ Tradebook Finland Nordea Bank NDEAFIHH CRLSUS3SCLR 0220001011256 Nordea Bank Finland Plc. 35 Danmark A/S - SetClear/ Tradebook France Citibank CITTGB2L CRLSUS3SCLR 0655945016 TRADEBOOK International Plc, SICV : 186 London Germany Citigroup Global CITIDEFF CRLSUS3SCLR 21488201 SETCLEAR PTE Markets Broker Code: LTD - Deutschland 7372 TRADEBOOK AG & Co. KGaA Page 1 of 3 BUYER/SELL Custodian DEAG / REAG SetClear ID / A/C Number at Market A/C Name Name Local Agent Executing Custodian Broker BIC Greece Citibank CITIGRAA CRLSUS3SCLR 801819 TRADEBOOK International Plc, Greece Branch Hong Kong Citibank, N.A. CITIHKHX CRLSUS3SCLR 1321760001 SetClear Pte Ltd Hong Kong CCASS ID: - Tradebook Branch C00010 Hungary Citibank Zrt. CITIHUHX CRLSUS3SCLR 7202274002 SETCLEAR PTE. LTD. TRADEBOOK Ireland Citibank N.A., CITIGB2L CRLSUS3SCLR 6011366408 SETCLEAR PTE London Branch Crest: ODOAD LTD Italy Citibank N.A., CRLSUS3SCLR CRLSUS3SCLR 1228569 Setclear PTE Milan Branch LTD TRADEBOOK Japan Citibank Japan CITIJPJT CRLSUS3SCLR 331192 SETCLEAR PTE Ltd. -

Citigroup Inc. 399 Park Avenue New York, NY 10043 March 8, 2012
Citigroup Inc. 399 Park Avenue New York, NY 10043 March 8, 2012 Dear Stockholder: We cordially invite you to attend Citi’s annual stockholders’ meeting. The meeting will be held on Tuesday, April 17, 2012, at 9AM (CDT) at the Hilton Anatole, 2201 North Stemmons Freeway in Dallas, Texas. Directions to the 2012 Annual Meeting are provided on page 114 of this proxy statement. At the meeting, stockholders will vote on a number of important matters. Please take the time to carefully read each of the proposals described in the attached proxy statement. Lastly, I have concluded that after 16 years on Citi’s board and three as chairman, the time has come for me to take my leave. The Board of Directors and I have complete confidence in the management team, the actions they have taken to strengthen Citi, and the course they have charted for one of the world’s truly great financial institutions. We would also like to recognize our retiring directors, Alain J.P. Belda and Timothy C. Collins for their many contributions. Alain’s leadership and wisdom over the past 15 years have been an invaluable asset for Citi. Tim joined the board at a critical moment in Citi’s history and his insights and guidance during this period have been extremely important as well. Thank you for your support of Citi. Sincerely, Richard D. Parsons Chairman of the Board Citigroup Inc. 399 Park Avenue New York, NY 10043 Notice of Annual Meeting of Stockholders Dear Stockholder: Citi’s annual stockholders’ meeting will be held on Tuesday, April 17, 2012, at 9AM (CDT) at the Hilton Anatole, 2201 North Stemmons Freeway in Dallas, Texas. -

Brown Brothers Harriman Global Custody Network Listing
BROWN BROTHERS HARRIMAN GLOBAL CUSTODY NETWORK LISTING Brown Brothers Harriman (Luxembourg) S.C.A. has delegated safekeeping duties to each of the entities listed below in the specified markets by appointing them as local correspondents. The below list includes multiple subcustodians/correspondents in certain markets. Confirmation of which subcustodian/correspondent is holding assets in each of those markets with respect to a client is available upon request. The list does not include prime brokers, third party collateral agents or other third parties who may be appointed from time to time as a delegate pursuant to the request of one or more clients (subject to BBH's approval). Confirmations of such appointments are also available upon request. COUNTRY SUBCUSTODIAN ARGENTINA CITIBANK, N.A. BUENOS AIRES BRANCH AUSTRALIA CITIGROUP PTY LIMITED FOR CITIBANK, N.A AUSTRALIA HSBC BANK AUSTRALIA LIMITED FOR THE HONGKONG AND SHANGHAI BANKING CORPORATION LIMITED (HSBC) AUSTRIA DEUTSCHE BANK AG AUSTRIA UNICREDIT BANK AUSTRIA AG BAHRAIN* HSBC BANK MIDDLE EAST LIMITED, BAHRAIN BRANCH FOR THE HONGKONG AND SHANGHAI BANKING CORPORATION LIMITED (HSBC) BANGLADESH* STANDARD CHARTERED BANK, BANGLADESH BRANCH BELGIUM BNP PARIBAS SECURITIES SERVICES BELGIUM DEUTSCHE BANK AG, AMSTERDAM BRANCH BERMUDA* HSBC BANK BERMUDA LIMITED FOR THE HONGKONG AND SHANGHAI BANKING CORPORATION LIMITED (HSBC) BOSNIA* UNICREDIT BANK D.D. FOR UNICREDIT BANK AUSTRIA AG BOTSWANA* STANDARD CHARTERED BANK BOTSWANA LIMITED FOR STANDARD CHARTERED BANK BRAZIL* CITIBANK, N.A. SÃO PAULO BRAZIL* ITAÚ UNIBANCO S.A. BULGARIA* CITIBANK EUROPE PLC, BULGARIA BRANCH FOR CITIBANK N.A. CANADA CIBC MELLON TRUST COMPANY FOR CIBC MELLON TRUST COMPANY, CANADIAN IMPERIAL BANK OF COMMERCE AND BANK OF NEW YORK MELLON CANADA RBC INVESTOR SERVICES TRUST FOR ROYAL BANK OF CANADA (RBC) CHILE* BANCO DE CHILE FOR CITIBANK, N.A. -

Citibank, N.A. 2018 Resolution Plan Public Section July 1, 2018
Citibank, N.A. 2018 Resolution Plan Public Section July 1, 2018 Citibank, N.A. Resolution Plan Public Section Table of Contents A. Introduction and Description of Resolution Strategy ....................................................................... 1 A.1. Multiple Acquirer Strategy ....................................................................................................... 2 A.2. Resulting Organization upon Completion of Resolution Process ............................................ 3 A.3. Citi’s Actions to Improve CBNA’s Resolvability ......................................................................... 4 B. Description of Core Business Lines ................................................................................................... 7 B.1. Banking CBLs ............................................................................................................................ 7 B.2. Markets & Securities Services CBLs ......................................................................................... 8 B.3. Global Consumer Banking CBLs ............................................................................................... 8 C. Background Information on Material Entities ................................................................................ 10 C.1. Banking Entities and Branches ............................................................................................... 12 C.2. Service MEs ........................................................................................................................... -

External Risk Events Report April 2021
RISK EVENTS REPORT April 2021 TABLE OF CONTENTS • Introduction • Overview • Risk Events by Category • Significant Management Changes 1233 20th Street NW, Suite 450 For more information contact: Washington, DC 20036 Claude Hanley, Partner Capitalperform.com Tel: 703-861-8623 @CPG_DC [email protected] RISK EVENTS REPORT APRIL 2021 RISK EVENTS REPORT SUMMARY Capital Performance Group tracks events at financial institutions and financial technology firms across the country which could have risk implications for the industry. This sample report focuses on events at large banks in the United States as well as selected nonbank financial companies, fintechs, and payments companies. Within each risk type, events are sub-divided into three categories based on the relative significance of the event or the size of the fine or penalty levied against the institution in question: H I G H M E D I U M L O W PRIORITY PRIORITY PRIORITY The report contains a recap of legislative actions, proposed regulatory rules and enforcement actions among U.S. regulatory agencies involved in financial oversight. Risk events are organized under eight types of risk for easy review: 1. Market/Interest Rate Risk – changes or potential changes to rates 2. Liquidity – changes to markets or regulations that could impact an institution’s ability to fund its assets 3. Operational – when the failure of a system, process, or person results in a loss or penalty 4. Credit – instances of increased charge-offs or nonperforming loans in a particular credit segment 5. Fiduciary & Suitability – when an institution fails to act in the best interest of either shareholders or clients 6. -

Citi Private Bank Pricing, Commissions and Fees
Citi Private Bank Pricing, Commissions and Fees Table of Contents CGMI Account Type and Settlement Options ................2 Equity and Option Pricing .................................................2 Fixed Income Pricing ...........................................................3 Mutual Funds and Money Market Funds ........................ 4 Foreign Exchange (FX) ....................................................... 4 Structured Notes ................................................................. 4 Alternative Investments ................................................... 4 Margin .................................................................................... 4 Account or Transaction Related Fees ........................... 5 ERISA Maintenance and Termination Fees ................... 5 Citi Private Bank is a business of Citigroup Inc. (“Citigroup”), which provides its clients access to a broad array of products and services available through bank and non-bank affiliates of Citigroup. Not all products and services are provided by all affiliates or are available at all locations. In the U.S., investment products and services are provided by Citigroup Global Markets Inc. (“CGMI”), member FINRA and SIPC, and also Citi Private Advisory, LLC (“Citi Advisory”), member of FINRA and SIPC. CGMI accounts are carried by Pershing LLC, member FINRA, NYSE, SIPC. CGMI, Citi Advisory and Citibank, N.A. are affiliated companies under the common control of Citigroup. © 2021 Citigroup Inc. All Rights Reserved. Citi, Citi and Arc Design and other -

Application Form
APPLICATION FORM WILLIAM BLAIR SICAV (the "Company") 31, Zone d'Activités Bourmicht, L-8070 Bertrange, Luxembourg 1 APPLICATION FORM Please complete, sign and return to: Citibank Europe plc, Luxembourg Branch 31, Zone d'Activités Bourmicht L-8070 Bertrange Luxembourg Fax: +352 45 14 14 852 As the Company's Custodian and Paying Agent, Central Administration Agent, Registrar and Transfer Agent Note If this form is sent by fax it must subsequently be forwarded by post within five business days. This subscription form should be read in conjunction with the latest Prospectus of the Company. Telegraphic transfer information For any payment in a currency other than the share class currency, the administrator will carry out a foreign exchange transac- tion. For US dollars – USD Pay to Citibank, N.A. New York ABA no. 021 0000 89 Swift code CITIUS33 For the account of Citibank Europe plc, Luxembourg Branch Account no 10957463 For further credit 0252636001 William Blair SICAV TA Collecting FFC WBF deal reference For the Euro, and any Pay to Citibank, N.A. London component currency Swift code CITIGB2L of the Euro For the account of Citibank Europe plc, Luxembourg Branch Account GB46 CITI 1850 0808 5436 31 For further credit 0252636003 William Blair SICAV TA Collecting FFC WBF deal reference For British Pound – GBP Pay to Citibank, N.A. London Sort code 18-50-08 Swift code CITIGB2L For the account of Citibank Europe plc, Luxembourg Branch Account no 557935 For further credit 0252636002 William Blair SICAV TA Collecting FFC WBF deal reference For Swiss Francs – CHF Pay to Citibank, N.A. -

Europe Strategy
Europe Strategy 1 April 2020 A new European investment paradigm Europe has moved from ‘containment’ to the ‘mitigation’ stage in relation to COVID-19 in most countries. We expect phased lockdowns in the months ahead, so as to ease pressures on national healthcare systems. Jeffrey Sacks Head - EMEA Investment Central bank and government financial support programes are necessary Strategy and have further to go. Implementation – ensuring that the individuals and +44.207 508 7325 companies most in need receive timely and sufficient support – will be very [email protected] challenging. Shan Gnanendran, CFA GDP contractions will be severe in the second quarter, with no powerful EMEA Investment Strategy recoveries to follow immediately. However, we are confident that support +44.207 508 0458 measures will help preserve long-term economic and corporate health. [email protected] More bond market stability – supported by liquidiity from the European Central Bank and the Bank of England – will help stabilise the outlook for regional equities. Equities are likely to have a prolonged consolidation phase within wide trading ranges. We expect selective buying opportunities, particularly in companies with strong balance sheets. The virus’s impact will likely reinforce some of our recommendations from the start of the year. These include staying invested, diversifying sensibly, and embracing higher volatility. Our long-term Unstoppable Trends like fintech and cybersecurity still offer attractive equity potential. Figure 1: Country sector performance – 1 month and YTD Source: Bloomberg as of March 31th 2020. Indices are unmanaged. An investor cannot invest directly in an index. They are shown for illustrative purposes only. -

Global Strategy Quadrant March 15, 2018
Global Strategy Quadrant March 15, 2018 Steven Wieting Chief Investment Fear of the Month Club Strategist +1-212-559-0499 Stay brave, stay bullish, but stay diversified across regions and asset classes [email protected] US equity prices rose more than earnings in the last two years. This has set the stage for Malcolm Spittler some valuation compression amid strong earnings growth in 2018. Nonetheless, we expect Maya Issa US corporate profits to rise about 20% year-on-year in the 1Q 2018 reporting period Global Investment which begins in less than a month. This should support recovery in US equities. Strategy Across the world, share prices are now trailing behind earnings gains. As such, the Citi Ken Peng Private Bank Global Investment Committee maintained our 4% overweight in Global Catherine Cheung Equities, concentrated in non-US markets, with global valuations at a discount to the US. Asia Investment Strategy US President Donald Trump campaigned in 2016 on tax cuts and domestic protectionism, and is now poised to deliver on both. As cross-border trade has long risen as a proportion Jeffrey Sacks of world economic activity, trade disruptions would now pose a larger economic risk. Shan Gnanendran EMEA Investment There is much room to negotiate and mitigate impact, as recent exceptions from steel and Strategy aluminum tariffs for particular countries illustrate. But how far some world leaders may go in retaliatory trade measures against the US is unclear. The next few months might see Jorge Amato heightened concerns, particularly in relation to trade between the US and China.