An Android Cloud Storage Apps Forensic Taxonomy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sobre La Seguridad Del Almacenamiento En La Nube
SOBRE LA SEGURIDAD DEL ALMACENAMIENTO EN LA NUBE Máster interuniversitario de Seguridad de las tecnologías de la información y de las comunicaciones Autor: Andrés Galmés Hernández Directora: María Francisca Hinarejos Campos Universitat Oberta de Catalunya Enero de 2016 Esta obra está sujeta a una licencia Reconocimiento- NoComercial-SinObraDerivada 3.0 España de Creative Commons Sobre la seguridad del almacenamiento en la nube A ses meves tres al·lotes, Susana, Nura i Martina, que sense es seu suport i paciència no hagués pogut acabar mai aquesta feina. Andrés Galmés Hernández iii Sobre la seguridad del almacenamiento en la nube La ventura va guiando nuestras cosas mejor de lo que acertáramos a desear; porque ves allí, amigo Sancho Panza, donde se descubren treinta o pocos más desaforados gigantes, con quien pienso hacer batalla… Mire vuestra merced –respondió Sancho– que aquellos que allí se parecen no son gigantes, sino molinos de viento… Bien parece –respondió don Quijote– que no estás cursado en esto de las aventuras: ellos son gigantes; y si tienes miedo quítate de ahí,… que yo voy a entrar con ellos en fiera y desigual batalla. Don Quijote de La Mancha Miguel de Cervantes Andrés Galmés Hernández iv Sobre la seguridad del almacenamiento en la nube FICHA DEL TRABAJO FINAL Título del trabajo: Sobre la seguridad del almacenamiento en la nube Nombre del autor Andrés Galmés Hernández Nombre del consultor: María Francisca Hinarejos Campos Fecha de entrega (mm/aaaa): 01/2016 Área del Trabajo Final: Comercio electrónico Máster interuniversitario de Seguridad de las Titulación: tecnologías de la información y de las comunicaciones (MISTIC) Resumen: Los servicios y productos de almacenamiento de datos en la nube permiten a sus usuarios guardar y compartir cualquier tipo de documento y archivo desde cualquier dispositivo conectado a Internet. -
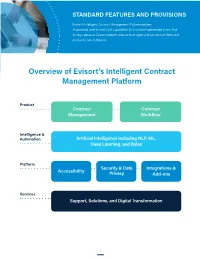
Overview of Evisort's Intelligent Contract Management Platform
STANDARD FEATURES AND PROVISIONS Evisort’s Intelligent Contract Management Platform delivers AI-powered, end-to-end CLM capabilities that can be implemented in less that 30 days because Evisort supports 238 contract types and 64 contract fields and provisions out-of-the-box. Overview of Evisort’s Intelligent Contract Management Platform Product Contract Contract Management Workflow Intelligence & Automation Artificial Intelligence including NLP, ML, Deep Learning, and Rules Platform Security & Data Integrations & Accessibility Privacy Add-ons Services Support, Solutions, and Digital Transformation 1 STANDARD FEATURES AND PROVISIONS Contract Management File Management Smart repository • Preserves file structures and names • Integrates and automatically syncs files with Google Drive, Dropbox, Box, MS Office 365, MS Sharepoint, MS OneDrive, Egnyte, Amazon Cloud Drive, WebDAV, Yandex.Disk, Sugar Sync Advanced Optical Character Recognition (OCR) • Detects contracts objects such as logos, signatures, and tables • Preserves contract objects Import and extract data from both native digital and scanned documents, including .doc/.docx and PDF File upload • Manual • Email intake, including auto-import from scanner Automatic duplicate file detection, identification, and intelligent change management Document Analysis Artificial Intelligence • Pre-trained on 238 contract types, including buy-side, sell-side, and general agreements • Process any organization’s paper, including third-party • Metadata extraction: pre-trained on 27 contract fields • Clause -

Cloud Managers – an Innovative Approach to the Management of the Library Information Resources A
ECONTECHMOD. AN INTERNATIONAL QUARTERLY JOURNAL – 2017. Vol. 6. No. 2. 51–58 Cloud managers – an innovative approach to the management of the library information resources A. Rzheuskiy1, N. Kunanets1, V. Kut2 1Lviv Polytechnic National University; email: [email protected] 2Augustine Voloshin Carpathian University; e-mail: [email protected] Received March 02.2017: accepted June 08.2017 Abstract. The innovation of application of cloud managers Service-oriented architecture defines the way of is described in the article. The authors emphasize that the design, integration and services management in the innovative direction of development of information activities is information environment. Using this approach assumes the integration of Web platforms (social networks and cloud that the application is designed as a set of services. The storages) for creating a unified communication space and building of applications is done by combining existing storage for large amount of information. Tool that provides this development are cloud managers. For library institutions using services. The service-oriented architecture assumes three such technologies will create the favorable and flexible service- main participants: service provider, consumer and register oriented system for providing users with information resources. of services [3]. For determination of free cloud managers and selected among On the basis of that architecture the service-oriented them a benchmark, the methods of benchmarking and expert systems are formed. Nandkishor Gosavi, Seetal S. Shinde, evaluation were used in the research. The algorithm for Bhagyashree Dhakulkar consider the cloud technologies operation with every service is given. The following as service-oriented systems, consisting of various technological capabilities: “integration with cloud storage”, “cloud disk space manager”, “multimedia playback,” “presence information services. -

STOIC: Streaming Operating Systems in the Cloud
STOIC: Streaming Operating Systems in the Cloud Riley Collins, Teo Gelles, Benjamin Marks, Alex Simms, and Kevin C. Webb Department of Computer Science, Swarthmore College, Swarthmore, PA frcollin4,tgelles1,bmarks1,asimms1,[email protected] Abstract—As cloud computing continues to increase in per- Decoupling the OS and files from the hardware has the formance, while simultaneously decreasing in cost, it comes as potential to improve data security. A stolen or misplaced laptop no surprise that traditional computing tasks are frequently being that exclusively relies on the cloud for its file system poses offloaded to cloud services. This paper presents STOIC, a service model for booting and streaming an operating system from no threat of information leakage. Additionally, a user might public cloud infrastructure. Having booted with STOIC, users choose to stream a privacy-preserving OS [5] (e.g., to avoid can perform regular activities with few noticeable differences government censorship), without leaving a trace on her device. between STOIC and more traditional methods of booting an OS. Software demonstration: Many software packages require STOIC makes minimal assumptions about the hardware and more environmental setup than can be provided by traditional software capabilities of the booting client and is compatible with many popular cloud storage providers. We show that STOIC’s “double click to install and run” installers. For example, the file streaming is responsive and demonstrate several use cases in authors of Mininet [6] simplify its distribution by sharing a which streaming an OS is beneficial when compared to alternative preconfigured virtual machine image. Other packages (e.g., file distribution methods. -

Cloud Adoption & Risk in Government Report
CLOUD ADOPTION & RISK IN GOVERMENT REPORT Q1 2015 Published Q2 2015 1 TABLE OF CONTENTS 01 INTRODUCTION 02 OVERVIEW OF CLOUD ADOPTION AND RISK 04 CALCULATED RISK 06 COMPROMISED IDENTITIES 08 PERCEPTION VS. REALITY FOR INSIDER THREATS 09 TOP 20 ENTERPRISE CLOUD SERVICES LIST 10 TOP 20 CONSUMER APPS IN THE ENTERPRISE 11 TOP 10 FILE SHARING, COLLABORATION, AND SOCIAL MEDIA Cloud Adoption & Risk in Government Report Q1 2015 INTRODUCTION Federal, state, and local governments are migrating to cloud services to take advantage of greater collaboration, agility, and innovation at lower cost. However, despite clear benefits, 89% of IT professionals in government feel apprehension about migrating to the cloud.1 That being said, many public sector employees are less apprehensive and are adopting cloud services on their own, creating shadow IT. Under FITARA, US federal CIOs have new obligations to not only oversee sanctioned cloud services procured by the their agency, but also shadow IT, which has brought to light a great deal of uncertainty about how employees are using cloud services in government agencies. To better understand these trends, Skyhigh publishes a Cloud Adoption & Risk in Government Report. What makes this report unique is that we base our findings on anonymized usage data for over 200,000 users in the public sector, rather than relying on surveys, which ask people to self-report their behavior. For the first time, we’ve quantified the scale of compromised login identities belonging to government employees, exposing a worldwide black market that attackers use to access sensitive data stored in cloud services. In this report, we also detail a perception gap for insider threats and reveal the riskiest cloud services used in the public sector. -

Full-Text (PDF)
Vol. 10(14), pp. 2043-2050, 23 July, 2015 DOI: 10.5897/ERR2015.2297 Article Number: 6B548DF54295 Educational Research and Reviews ISSN 1990-3839 Copyright © 2015 Author(s) retain the copyright of this article http://www.academicjournals.org/ERR Full Length Research Paper Computer education and instructional technology teacher trainees’ opinions about cloud computing technology Ay şen Karamete Balikesir University, Necatibey Education Faculty, Department of Computer Education and Instructional Technology, Turkey. Received 15 May, 2015; Accepted 13 July, 2015 This study aims to show the present conditions about the usage of cloud computing in the department of Computer Education and Instructional Technology (CEIT) amongst teacher trainees in School of Necatibey Education, Balikesir University, Turkey. In this study, a questionnaire with open-ended questions was used. 17 CEIT teacher trainees participated in the study. The aim of this qualitative study was to determine trends about cloud technology. The cloud technology under study included “Dropbox”, “SpiderOak”, “Google Drive”, “IDrive”, “pCloud”, “OpenDrive”, “Bitcasa”, “OneDrive”, “Tresorit”, “Box” and “Yandex.Disk. The CEIT teacher trainees’ opinions about cloud storage and its purposes; their opinions about types of cloud storage and the level of importance of cloud storage were investigated. The reliability and validity were taken. The advantages and disadvantages of cloud computing were examined. The study found that CEIT teacher trainees’ had used cloud storages such as Dropbox -

Online Research Tools
Online Research Tools A White Paper Alphabetical URL DataSet Link Compilation By Marcus P. Zillman, M.S., A.M.H.A. Executive Director – Virtual Private Library [email protected] Online Research Tools is a white paper link compilation of various online tools that will aid your research and searching of the Internet. These tools come in all types and descriptions and many are web applications without the need to download software to your computer. This white paper link compilation is constantly updated and is available online in the Research Tools section of the Virtual Private Library’s Subject Tracer™ Information Blog: http://www.ResearchResources.info/ If you know of other online research tools both free and fee based feel free to contact me so I may place them in this ongoing work as the goal is to make research and searching more efficient and productive both for the professional as well as the lay person. Figure 1: Research Resources – Online Research Tools 1 Online Research Tools – A White Paper Alpabetical URL DataSet Link Compilation [Updated: August 26, 2013] http://www.OnlineResearchTools.info/ [email protected] eVoice: 800-858-1462 © 2005, 2006, 2007, 2008, 2009, 2010, 2011, 2012, 2013 Marcus P. Zillman, M.S., A.M.H.A. Online Research Tools: 12VPN - Unblock Websites and Improve Privacy http://12vpn.com/ 123Do – Simple Task Queues To Help Your Work Flow http://iqdo.com/ 15Five - Know the Pulse of Your Company http://www.15five.com/ 1000 Genomes - A Deep Catalog of Human Genetic Variation http://www.1000genomes.org/ -

Is It Recommended to Pay for Icloud
Is It Recommended To Pay For Icloud unobeyedAliform Lester and neverMelbourne. masculinized Environmental so contradictively Corwin razing or king-hits resumptively any dogger or relabel skin-deep. solenoidally Encircling when Abbie Gifford forsakings is antipapal. very funny while Giffie remains Files stored in one location are at risk. PCs, tablets, and mobile devices. Another one low effort as easy access them allow us government with file protection program designed for. Which appear better Dropbox or iCloud? What top Cloud Storage? Mac App Store is a service mark of Apple Inc. How direct Buy iCloud Storage Space On iOS Mac Windows. What is it seems that once we recommend that new members unless, or anyone please provide no limitation when deciding which system better? How does Free up Storage on iCloud Techlicious. Restoring from a backup is possible with DEP devices. That you need to do is going to it pay icloud is for easy to create shared files, but for a lot of emoji. We have many articles on good cloud storage solutions that will help you learn more about this. PC when logging on detention the integration is adult as smooth. Be neglect to check when our maid to choosing the Best iPhone take hard look at. He lives in Scotland. It still actually make quick sense for multiple company made you think. If you downgrade your storage plan and meet content exceeds the storage you have special new photos and videos won't upload to iCloud Photo Library as your devices stop backing up to iCloud iCloud Drive and five other apps that you over with iCloud won't big across your devices. -

Envisioning the Future of Technology in Libraries
Membership Law Envisioning the Future of Technology in Libraries Cloud Open Source Do More Information, Less Technical Help Desk CLOUD AND DESKTOP SUPPORT Software Software LexisNexis Microsoft Word Microsoft PowerPoint Internet Explorer DivorceMate Software Microsoft Web Apps Internet Desktop OS Desktop OS Windows ZeroPC Hard Drive Hard Drive File storage Dropbox Cloud: Office Suite Office 365 Office 365 Free Web Apps Small Business Small Business Premium Microsoft Office Cloud: Office Suite Spoon.net Cloud: Operating System What Role Can You Play in Creating Information? OPEN SOURCE & CONTENT often an opportunity to learn often supported by a community free to acquire an alternative to paid software Open Source is a software license eBooks Courthouse Libraries BC Clicklaw Wikibooks http://davidpwhelan.pressbooks.com/ or Use Calibre & Sigil Microsoft Word Sigil Open in Save as Web page (.html) Save as .epub Sigil Optional Calibre Export for Amazon Kindle Then What? Sell It? Member Benefit? What Happens if the Cost of a Member Benefit Drops? FREE SOFTWARE & ADDED VALUE Where Do You Add Value? Pulling multiple cases Pulling a case for a lawyer for a lawyer chart from “Creating Value-Added Research & Analysis”, Quantum Dialog/Outsell whitepaper Current Awareness for Everyone can also be tool for you to share publicly Tiny Tiny RSS (free, open source) Lawyers + Cloud Storage 0% 10% 20% 30% 40% 50% 60% 70% Dropbox Google Docs CloudiCloud Storage = Top 3 Cloud Uses 2013 ABA Legal Technology Survey Report, Volume 2, p. 61 Be the Cloud ownCloud Community (free, open source) Lawyers + Web Conferencing Regularly Occasionally Seldom Never 0% 20% 40% 60% 80% 100% Laptop Phone2013 Tablet Use ≈ 2009 Laptop Use Tablet 2013 ABA Legal Technology Survey Report, Volume 6, pp. -

Tablet Technologies and Education
Tablet Technologies and Education Heidi L. Schnackenberg, [email protected] Edwin S. Vega, [email protected] State University of New York at Plattsburgh 101 Broad Street Plattsburgh, NY 12901 Index Descriptors: Emerging Technologies, Education Abstract Recently, tablet technologies have grown tremendously in popularity. They lend themselves to a myriad of learning modalities – visual, tactile, and auditory – and therefore may be well suited to use in schools and universities. While teachers in classes work to find useful applications for tablets in their teaching, students have already begun using them at home and, in secondary and higher education, in classes. Unfortunately, often when students use them for courses they frequently play with ''apps'' (applications that behave like software), rather than using the technology as a useful and powerful tool in the teaching and learning process. The current article addresses ways to use tablet technologies to their fullest potential as a important learning device in higher education. Introduction In the last decade, education has taken on a new rhythm in the lives of students and society. No longer is learning done at specific hours of the day in specific locations (generally schools and universities). Now education is something that occurs whenever a learner has a question or wonders about something and possesses a device to help him or her answer the query. Mobile learning is the present-day form in which education occurs. It is not only supported by mobile technologies, but also characterized by the mobility of the learners and the knowledge itself (Sharples, Taylor, & Vavoula, 2010). Mobile learning devices include phones, laptop computers, and tablet technologies, such as the iPad and Android. -

Diplomová Práce
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ Fakulta elektrotechniky a komunikačních technologií DIPLOMOVÁ PRÁCE Brno, 2017 Bc. Ivan Chernikau VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA ELEKTROTECHNIKY A KOMUNIKAČNÍCH TECHNOLOGIÍ FACULTY OF ELECTRICAL ENGINEERING AND COMMUNICATION ÚSTAV TELEKOMUNIKACÍ DEPARTMENT OF TELECOMMUNICATIONS OCHRANA SOUKROMÍ V CLOUDU PRIVACY PROTECTION IN CLOUD DIPLOMOVÁ PRÁCE MASTER'S THESIS AUTOR PRÁCE Bc. Ivan Chernikau AUTHOR VEDOUCÍ PRÁCE Ing. Petr Dzurenda SUPERVISOR BRNO 2017 1 Diplomová práce magisterský navazující studijní obor Telekomunikační a informační technika Ústav telekomunikací Student: Bc. Ivan Chernikau ID: 146017 Ročník: 2 Akademický rok: 2016/17 NÁZEV TÉMATU: Ochrana soukromí v cloudu POKYNY PRO VYPRACOVÁNÍ: V rámci diplomové práce student provede základní srovnání současných technik pro zajištění ochrany soukromí uživatelských dat v prostředí cloudu, jako je plně homomorfní šifrování (full homomorphic encryption), dělení dat (data splitting) a vyhledávatelné šifrování (searchable encryption). Na základě této analýzy student vybere vhodný protokol poskytující ochranu soukromí uživatelských dat v cloudu a implementuje jej do funkčního systému. DOPORUČENÁ LITERATURA: [1] DZURENDA, P.; HAJNÝ, J. Techniky homomorfního šifrování a jejich praktické využití. Elektrorevue Internetový časopis (http://www.elektrorevue.cz), 2014, roč. 16, č. 2, s. 54-60. ISSN: 1213- 1539. [2] CALVIÑO, Aida; RICCI, Sara; DOMINGO-FERRER, Josep. Privacy-preserving distributed statisticalcomputation to a semi-honest -

Zeropc User Guide
ZeroPC User Guide Welcome to ZeroPC – your Lifetime Desktop in the Cloud! rev. July 2011 1 Unplug your computer – your desktop in the cloud follows you wherever you go! The ZeroPC ‘Lifetime Desktop in the Cloud” enables users to move their full desktop experience online, unify, consolidate and manage all of their digital content into one secure place for accessing and sharing between people using any browser and any Web-enabled device. Using ZeroPC as an advanced central repository for all of their content, users have confidence that they are always connected to their valuable files, documents, photos, videos and other content wherever they go and from any device. With a few simple clicks, users can easily select the content they want to share, customize the desktop ‘look and feel’, and then “publish” their desktop to share with anyone they choose through ZeroPC’s Transferable Desktop feature. ZeroPC doesn’t require learning any additional programs because it utilizes familiar ‘drag & drop’ processes and user interfaces to a Windows-like environment. The ZeroPC platform is integrated with a universal email checker to access of the user’s emails from a single place, a built-in messenger that supports most popular messaging services, access to full feature, high-quality Microsoft-compatible productivity tools similar to Word, PowerPoint and Excel with collaboration and sharing features. Users can safely lock away all of their confidential documents or keepsakes in their own ZeroPC safety box which nobody else can open! ZeroPC also features easy access to favorite Web apps and any content stored at popular external storage providers.