Volume 3 2019-2020 Pages 1-101
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

December 19, 2017 Records, FOIA, and Privacy Branch Office of Environmental Information Environmental Protection Agency 1200
December 19, 2017 VIA ELECTRONIC MAIL Records, FOIA, and Privacy Branch Office of Environmental Information Environmental Protection Agency 1200 Pennsylvania Avenue NW (2822T) Washington, DC 20460 [email protected] Re: Freedom of Information Act Request Dear Freedom of Information Officer: Pursuant to the Freedom of Information Act (FOIA), 5 U.S.C. § 552, and the implementing regulations of the Environmental Protection Agency (EPA), 40 C.F.R. Part 2, American Oversight makes the following request for records. On December 15, Mother Jones and the New York Times reported that EPA signed a $120,000 no-bid contract with Definers Public Affairs to provide media services.1 Definers was founded by Joe Pounder and Matt Rhoades, two longtime Republican political operatives. Mr. Pounder and Mr. Rhoades previously founded America Rising, a Republican political opposition research firm. The Times also reported that since President Trump took office, at least 40 FOIA requests have been submitted to the EPA by Allan Blutstein, a vice president for both Definers and America Rising. Many of those requests sought records about EPA employees who had been critical of the Trump administration. Earlier today, it was reported that EPA had decided to cancel the contract with Definers Public Affairs.2 However, many questions remain about the initial decision to award a no-bid contract to 1 See Rebecca Leber et al., The EPA Hired a Major Republican Opposition Research Firm to Track Press Activity, MOTHER JONES (Dec. 15, 2017, 6:00 AM), http://www.motherjones.com/politics/2017/12/the-epa-hired-a-major-republican-opposition- research-firm-to-track-press-activity/; Eric Lipton & Lisa Friedman, E.P.A. -

December 19, 2017 SUBMITTED ELECTRONICALLY Honorable Arthur A. Elkins Jr. Inspector General EPA Office of Inspector General 1
December 19, 2017 SUBMITTED ELECTRONICALLY Honorable Arthur A. Elkins Jr. Inspector General EPA Office of Inspector General 1200 Pennsylvania Ave, NW (2410T) Washington, D.C. 20460 Re: Suggestions for Audits and Evaluations Dear Mr. Elkins, The mission of EPA’s Office of the Inspector General is to “prevent and detect fraud, waste, and abuse through independent oversight of the programs and operations of the Environmental Protection Agency.”1 We respectfully request that the Office of the Inspector General immediately open an investigation into EPA’s decision to award a $120,000 no-bid contract to Definers Public Affairs Corporation for “news analysis and brief service focusing on EPA work and other topics of interest to EPA,” as well as EPA’s interactions with key Definers affiliates and staff members.2 Although EPA reportedly intends to terminate its contract with Definers3 in light of widespread concern,4 a full investigation is essential to determine whether EPA’s multi- faceted interactions with Definers and its affiliates has led to improper uses of agency resources. In particular, EPA’s no-bid $120,000 contract award to Definers Public Affairs Corporation raises serious questions of potential “waste, fraud, and abuse”: the organization’s partisan character and on-going promotion of Administrator Pruitt suggest that inappropriate 1 EPA Office of Inspector General, About EPA’s Office of Inspector General, https://www.epa.gov/office- inspector-general/about-epas-office-inspector-general#who_what_why. 2 https://www.usaspending.gov/Transparency/Pages/AwardSummary.aspx?AwardID=59978626. 3 See, e.g., https://www.washingtonpost.com/news/energy-environment/wp/2017/12/19/epa-to-end- controversial-contract-with-conservative-media-monitoring-firm/?utm_term=.6e3f99ccd0da; https://twitter.com/PounderFile/status/943172637202755584. -

BOARD LEGISLATIVE COMMITTEE Friday, March 9, 2018 12:30 P.M
BOARD LEGISLATIVE COMMITTEE Friday, March 9, 2018 12:30 p.m. EBRPD – Administrative Headquarters 2950 Peralta Oaks Court Oakland, California 94605 The following agenda items are listed for Committee consideration. In accordance with the Board Operating Guidelines, no official action of the Board will be taken at this meeting; rather, the Committee’s purpose shall be to review the listed items and to consider developing recommendations to the Board of Directors. A copy of the background materials concerning these agenda items, including any material that may have been submitted less than 72 hours before the meeting, is available for inspection on the District’s website (www. ebparks.org), the Headquarters reception desk, and at the meeting. Public Comment on Agenda Items If you wish to testify on an item on the agenda, please complete a speaker’s form and submit it to the recording secretary. Your name will be called when the item is announced for discussion. Accommodations and Access District facilities and meetings comply with the Americans with Disabilities Act. If special accommodations are needed for you to participate, please contact the Clerk of the Board at 510-544-2020 as soon as possible, but preferably at least three working days prior to the meeting. AGENDA TIME ITEM STATUS STAFF 12:30 I. STATE LEGISLATION / OTHER MATTERS A. NEW LEGISLATION R Doyle/Pfuehler 1. AB 1945 – Greenhouse Gas Reduction Fund (Garcia D-Coachella) 2. AB 2053 – Harmful Algal Bloom Task Force (Quirk D-Hayward) 3. AB 2061 – Clean Energy Trucks (Frazier D- Discovery Bay) 4. AB 2137 – Riverside County Regional Park and Open Space District General Manager Powers (Mayes R-Yucca Valley) 5. -
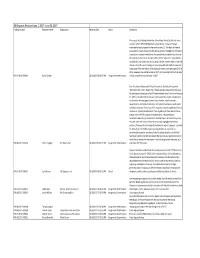
FOIA Requests Received in June, 2017
All Requests Received June 1, 2017 ‐ June 30, 2017 Tracking Number Requester Name Organization Received Date Status Description We request the following information for work performed by Wastren under contract number EPS71508 (Madison County Mines). 1. Square Footage excavated for each property for the entire contract. 2. The depth of material excavated from each property for the entire contract. Typically this information is available in a spread sheet format. If a spreadsheet is available that includes the requested information, that will suffice for this request. If a spreadsheet is not available, any documents such as emails, billings, reports, maps or logs that discuss or describe square footage of areas excavated and depth of excavation is requested. The information we're looking for covers a two year span (2015 & 2016). However, the contract ended in 2017, so it's possible that the final report EPA‐R7‐2017‐009015 Russ Gulledge 06/30/2017 08:06:55 PM Assignment Determination or final spreadsheet may be dated in 2017. Dear Freedom of Information Officer: Pursuant to the federal Freedom of Information Act, 5 U.S.C. § 552, I hereby request access to the following: All calendars and schedules of the EPA administrator Scott Pruitt from February 17, 2017 to the date that this request is processed. My request includes but is not limited to meeting agenda sheets, day calendars, travel itineraries, appointments, and Outlook calendars. This request encompasses both digital and physical records. Please search for responsive records regardless of format, medium, or physical characteristics. If you regard any of these documents as exempt from the FOIA’s disclosure requirements, I request that you nonetheless exercise your discretion to disclose them. -

Purveying Fake News
1 GOVERNANCE IN AN EMERGING NEW WORLD Convened by George P. Shultz with James Cunningham, David Fedor, and James Timbie Table of Contents FALL SERIES, ISSUE 318 Introduction ..........................................................................................................................................................................5 What Is to Be Done? Safeguarding Democratic Governance in the Age of Network Platforms Niall Ferguson ................................................................................................................................................................................................8 Protecting Democracy in an Era of Cyber Information War Joseph S. Nye ..............................................................................................................................................................................................37 Observations from the Roundtable ................................................................................................................................. 47 GOVERNANCE IN AN EMERGING NEW WORLD The Information Challenge to Democracy A Letter from the Conveners Sharp changes are afoot throughout the globe. Demographics are shifting, technology is advancing at unprecedented rates, and these changes are being felt everywhere. How should we develop strategies to deal with this emerging new world? We can begin by understanding it. First, there is the changing composition of the world population, which will have a profound impact on societies. Developed -
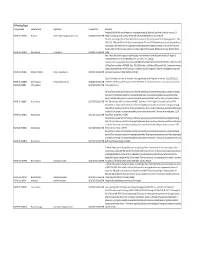
EPA June All Pending Report 20170705
All Pending Report Tracking Number Requester Name Organization Received Date Description Available SEMS‐ARCHIVE records/reports for the property located at 338 North Canal Street, South San Francisco, CA EPA‐R9‐2017‐009006 Brian Kim Partner Engineering & Science, Inc. 06/30/2017 07:06:00 PM 94080, reportedly operated by DECCA XAGON with EPA ID‐CAD980390272 and SITE ID‐901729 This firm is performing a Phase I Environmental Site Assessment for the property located at the following addresses: 1432, 1436, 1520, 1540, and 1560 East 6th Street, Corona, California 1451 and 1575 Magnolia Avenue, Corona, California We are requesting any information from your departments pertaining to contaminated ground water or soil records. Please feel free to contact me if you have any questions or concerns regarding this request. We thank you for your attention to this EPA‐R9‐2017‐008963 Laura Botzong EFI Global, Inc. 06/30/2017 01:06:00 PM matter. Hello, I would like to order a copy of a Superfund document for Beckman Porterville Superfund site (EPA Registry ID 110042043598) with the Docid = 88074084 which I saw listed on this webpage https://yosemite.epa.gov/r9/sfund/r9sfdocw.nsf/f8728d1c79f1b30f882574260072d053/c285337130bc1e7f882573ec00675 160!OpenDocument Docid = 88074084; Date ‐ 9/21/1993; Author ‐ Jeff Zelikson/EPA Region 9; Title ‐ Superfund preliminary closeout rpt, long term RA (final RA construction completion, final OU completion). Please do not hesitate to contact me if EPA‐R9‐2017‐008961 Barbara A. Murphy Hargis + Associates, Inc. 06/30/2017 -

Campaign Cybersecurity Playbook
DEFENDING DIGITAL DEMOCRACY NOVEMBER 2017 The Cybersecurity Campaign Playbook Contents Welcome ......................................................................................2 Authors and Contributors ................................................................................................... 3 The Playbook Approach ......................................................................................................4 Introduction ................................................................................4 The Vulnerable Campaign Environment .............................................................................6 The Threats Campaigns Face .............................................................................................. 7 Managing Cyber Risk .................................................................8 Securing Your Campaign ............................................................9 Top-Five Checklist .....................................................................11 Steps to Securing Your Campaign .......................................... 12 Step 1: The Human Element .............................................................................................. 12 Step 2: Communication ......................................................................................................14 Step 3: Account Access and Management ....................................................................... 16 Step 4: Incident Response Planning................................................................................. -

Adventures in the Word Trade DAVID SKINNER on the Demise of the American Heritage Dictionary’S Usage Panel
A HIGH-CULTURECOMMUNITY JOSEPH HOROWITZ DECEMBER 10, 2018 • $5.99 Adventures in the Word Trade DAVID SKINNER on the demise of the American Heritage Dictionary’s usage panel WEEKLYSTANDARD.COM Contents December 10, 2018 • Volume 24, Number 14 2 The Scrapbook Alex Trebek’s microaggression, ‘inclusion’ that excludes, & more 5 Casual Dennis Byrne’s no-name generation 6 Editorials Putin Poses a Test • The Second Time as Farce 9 Comment A cutthroat competitor like any other BY CHRISTINE ROSEN President Trump’s precarious position BY FRED BARNES 6 There’s no such thing as an overnight transformation BY HILIP ERZIAN P T ALEX WONG / GETTY Articles 14 The ACLU’s J’Accuse BY KC JOHNSON & STUART TAYLOR JR. The group comes out against equal treatment before the law 16 Nevertheless, She Persisted BY DOMINIC GREEN Theresa May’s Brexit deal means the end of sovereignty and democracy 19 No Easy Repeat BY RICHARD E. BURR Trump will struggle to win Michigan again 14 GAGE SKIDMORE! Features 21 Going High (Culture) BY JOSEPH HOROWITZ Orchestras and universities are working together to feed our hunger for community and a shared American identity 25 How He Played the Game BY DANIEL MCGRAW Ex-NFL receiver Anthony Gonzalez’s impressive political debut in the suburbs of Cleveland, Akron, and Canton 16 Books & Arts 28 Defining Characteristic BY DAVID SKINNER Now that the American Heritage Dictionary’s ‘usage panel’ has been shuttered, a look back at the dictionary’s evolution 38 Strange Saddles BY JOHN PODHORETZ Watching the Coen brothers’ new Western on screens large and small 39 High-Altitude Hideout BY TONY MECIA A Bond villain’s Alpine lair now houses a museum for 007 42 Celebration of a Curious Character BY DAN ALBAN Ricky Jay, 1946-2018 44 Parody Presidential report card 25 COVER BY HAL MAYFORTH THE SCRAPBOOK Criminally Negligent n late September, FedEx driver rumpuses and altercations when those that America is still a racist nation. -

Received by NSD/FARA Registration Unit 10/3J /2018 04'26-00 PM Received by NSD/FARA Registration Unit 10/31/2018 04:26:00 PM
Received by NSD/FARA Registration Unit 10/3J /2018 04'26-00 PM ' ' OMB No. 1124-6(302; Expires May 31,2610 U.S. Department of Justice Supplemental Statement Washington, dc 20530 Pursuant to the Foreign Agents Registration Act of 1938, as amended BB B! For Six Month Period Ending 9/30/2018 (Insert date) I - REGISTRANT 1. (a) Name of Registrant (b) Registration No. DC1 Group AZ, L.L.C 6278 (c) Business Address(es) of Registrant 1828 L Street, NW Suite 400 Washington, DC 20036 2. Has there been a change in the information previously furnished in connection with the following? (a) If an individual: (1) Residence address(es) Yes □ No □ (2) Citizenship Yes □ No □ (3) Occupation Yes □ No □ (b) If an organization: (1) Name Yes □ NoJg| (2) Ownership or control Yes □ No 0 (3) Branch offices Yes □ No 0 (c) Explain fully all changes, if any, indicated in Items (a) and (b) above. IFTHE REGISTRANT is AN INDIVIDUAL, OMIT RESPONSE TO ITEMS 3, 4, AND 5(a). 3. If you have previously filed Exhibit Cl, state whether any changes therein have occurred during this 6 month reporting period. Yes □ No J3 [f yes, have you filed an amendment to the Exhibit C? Yes □ No □ If no, please attach the required amendment. I The Exhibit C, for which no printed form is provided, consists of a true copy of the charter, articles of incorporation, association, and by laws of a registrant that Is an organization. (A waiver of the requirement to file an Exhibit C may be obtained for good cause upon written application to the Assistant Attorney General, National Security Division, (J.S. -

FY 2018 Bureau Log Generated by EFTS at Tue May 15 14:18:03 EDT 2018 923 Records in This Log
5/15/2018 https://efoia.ios.doi.gov/efts/printlog.jsp?FY=2018 FY 2018 Bureau Log generated by EFTS at Tue May 15 14:18:03 EDT 2018 923 records in this log. =========================================================================================================================================== = FOIA Number Request Date Receipt Date Completion Date Requester Name Bureau Status =========================================================================================================================================== = Subject =========================================================================================================================================== = OS-2018-00007 October 02, 2017 October 02, 2017 Townsend Margaret OS Open 1. All records mentioning, including, and/or referencing when the final reports shall be published in the Federal Register and on agency websites per M-17-24, ¿Guidance for Section 2 of Executive Order 13783, Titled ¿Promoting Energy Independence and Economic Growth¿¿ issued May 8, 2017 (¿OMB Memo¿); 2. All records of the final reports submitted pursuant to the OMB Memo that were to be finalized and provided to OMB per M-17-24 by September 24, 2017; (CONTINUED BELOW) OS-2018-00002 September 28, 2017 October 02, 2017 Saeger Chris OS Open Access to and copies of digital correspondence involving any of the following officials between September 13, 2017, and September 28, 2017: Secretary Ryan Zinke, Chief of Staff Scott Hommel, Deputy Assistant Secretary for Land and Minerals Management Katherine MacGregor, Press Secretary Heather Swift. Specifically, I request (continued below) OS-2018-00010 October 02, 2017 October 02, 2017 Saeger Chris OS Open Access to and copies of all AQD-91 forms submitted by Secretary Ryan Zinke or any other individual in the Immediate Office of the Secretary at any point since and including March 1, 2017. OS-2018-00004 August 17, 2017 October 02, 2017 February 27, 2018 Valentine Gary OS Completed Copy of the appraisal report SJRRP Reach 3. -

'18 PR Buyer's Guide & Crisis Communications Magazine
Communications & New Media Jan. 2018 I Vol. 32 No. 1 January 2018 | www.odwyerpr.com Vol. 32 No. 1 Jan. 2018 EDITORIAL BE A SOCIAL MEDIA SURVIVOR IN 2018 6 20 A primer on how to successfully MILLENNIALS ARE MOST protect your priceless reputation. MOTVATED BY ADS DON’T TRY TO COVER UP Younger consumers trust advertis- ing more than older generations. 8 DATA BREACHES Uber’s example shows what not 22 to do in the face of cyber crime. PRINT MEDIA MORE 10 RELIABLE THAN DIGITAL CRAFTING THE CRISIS Print is seen as safer, more secure RESPONSE PLAN and more trustworthy than digital. 8 Effective crisis comms can protect 24 your reputation and employees. GENERATION GAP IN PR PROS’ EXPECTATIONS COLD FEET SYNDROME Millennials have new views on Why some sellers pull out of compensation and leadership. 9 26 deals at the last minute. SOCIAL MEDIA BRINGS ARE PRESS CONFERENCES NEW RESPONSIBILITIES STILL RELEVANT? 42 WWW.ODWYERPR.COM An increase in media channels Even in a social media world, the 9 Daily, up-to-the-minute PR news results in more work for reporters. 28 press conference still matters. REVIEW OF 2017 MAKE CONSUMER MEDIA O’Dwyer’s takes a look at some PART OF B2B PUBLICITY of the stories that affected the PR Succesful branding for B2B clients landscape last year. 10 29 takes more than just trade press. PROFILES OF CRISIS COMMUNICATING IN A COMMUNICATIONS FIRMS DIVERSE WORLD How to navigate a world where 30 the old rules no longer apply. 12 PEOPLE IN PR THE END OF THE SILOED 37 CRISIS RESPONSE WASHINGTON In an organization, dealing with a REPORT EDITORIAL CALENDAR 2018 crisis has become everyone’s job. -
Election Cyber Incident Communications Coordination Guide for the Election Infrastructure Government Coordinating Council
Election Cyber Incident Communications Coordination Guide For the Election Infrastructure Government Coordinating Council DEFENDING DIGITAL DEMOCRACY FEBRUARY 2018 Defending Digital Democracy Project Belfer Center for Science and International Affairs Harvard Kennedy School 79 JFK Street Cambridge, MA 02138 www.belfercenter.org/D3P Statements and views expressed in this document are solely those of the authors and do not imply endorsement by Harvard University, the Harvard Kennedy School, or the Belfer Center for Science and International Affairs. Design & Layout by Andrew Facini Cover photo: A view of the podiums during a news conference in the Rose Garden at the White House, Monday, April 2, 2012. (AP Photo/Charles Dharapak) Copyright 2018, President and Fellows of Harvard College DEFENDING DIGITAL DEMOCRACY FEBRUARY 2018 Election Cyber The Cybersecurity Incident Communications CoordinationCampaign Playbook Guide For the Election Infrastructure Government Coordinating Council Contents Defending Digital Democracy Project: About Us ........................................................................................... 2 Authors and Contributors ................................................................................................................................ 3 Acknowledgments ............................................................................................................................................ 4 How to Use this Communications Guide ......................................................................................................