Workspace Environment Management Service
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Content Moderation Help Card
Content Moderation Help Card Content Moderation Content Moderation allows you to approve or decline content before it is posted to your website. Click Content Moderation and select Moderated Groups to begin the setup process. You can configure Content Moderation two ways. 1. Choose workspaces that are always moderated (e.g., sections, site homepages). Content added to workspaces specified in a Content Group will require approval for all editors when you activate the Moderate All Editors checkbox for the Content Group. 2. Set combinations of workspaces and editors requiring moderation (e.g., the PTO section and user Eric Sparks). Creating Content Groups Adding Moderated Users You use Content Groups to define workspaces subject to Content Moderation. If you only wish to moderate some editors, you will need to add them as To create a Content Group... Moderated Users. Whenever a moderated user edits content in a workspace 1. In Site Manager, select Content Moderation from the Content Browser. specified in any of the Content Groups, that user will only be able to send 2. Select Moderated Groups. content for approval. 3. On the Content Groups tab, click New Content To add Moderated Users... Group. 1. In the Moderated Groups workspace, click Moderated Users. 4. Add a Name and a Description for your group and click 2. Click Add Group or Add User. Save. 3. Use Search to locate groups or users you wish to moderate. You can To add workspaces and moderators... filter groups by category. 1. Click on the name of your Content Group. 4. Click Select to the right of each group or user name. -

Crypto Ransomware Analysis and Detection Using
CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR by ASHWINI BALKRUSHNA KARDILE Presented to the Faculty of the Graduate School of The University of Texas at Arlington in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE IN COMPUTER SCIENCE THE UNIVERSITY OF TEXAS AT ARLINGTON December 2017 Copyright © by Ashwini Balkrushna Kardile 2017 All Rights Reserved ii Acknowledgements I would like to thank Dr. Ming for his timely guidance and motivation. His insights for this research were valuable. I would also like to thank my committee members Dr. David Levine and Dr. David Kung for taking out time from their schedule and attending my dissertation. I am grateful to John Podolanko; it would not have been possible without his help and support. Thank you, John, for helping me and foster my confidence. I would like to thank my colleagues for supporting me directly or indirectly. Last but not the least; I would like to thank my parents, my family and my friends for encouraging me and supporting me throughout my research. November 16, 2017 iii Abstract CRYPTO RANSOMWARE ANALYSIS AND DETECTION USING PROCESS MONITOR Ashwini Balkrushna Kardile, MS The University of Texas at Arlington, 2017 Supervising Professor: Jiang Ming Ransomware is a faster growing threat that encrypts user’s files and locks the computer and holds the key required to decrypt the files for ransom. Over the past few years, the impact of ransomware has increased exponentially. There have been several reported high profile ransomware attacks, such as CryptoLocker, CryptoWall, WannaCry, Petya and Bad Rabbit which have collectively cost individuals and companies well over a billion dollars according to FBI. -

Microsoft Software License Terms for a Virtual Hard Disk Image of Evaluation Copies of the Microsoft Products Identified in Exhibit A
MICROSOFT SOFTWARE LICENSE TERMS FOR A VIRTUAL HARD DISK IMAGE OF EVALUATION COPIES OF THE MICROSOFT PRODUCTS IDENTIFIED IN EXHIBIT A These license terms are an agreement between Microsoft Corporation (or based on where you live, one of its affiliates) and you. Please read them. They apply to the evaluation software named above, which includes the media on which you received it, if any. The terms also apply to any Microsoft Internet-based services for this software. BY ACCESSING OR USING THE SOFTWARE, YOU ACCEPT THIS AGREEMENT. IF YOU DO NOT ACCEPT THIS AGREEMENT, YOU MAY NOT ACCESS OR USE THE SOFTWARE. AS DESCRIBED BELOW, USING SOME FEATURES ALSO OPERATES AS YOUR CONSENT TO THE TRANSMISSION OF CERTAIN STANDARD COMPUTER INFORMATION FOR INTERNET-BASED SERVICES. If you comply with this agreement, you have the rights below. 1. ACCESS AND USE RIGHTS. The terms of this agreement supersede the terms of any Microsoft software license term agreement that you may encounter in this software. You may use the Virtual Hard Disk (VHD) formats, including Microsoft Virtual PC or Microsoft Virtual Server. You may use the software only to demonstrate and internally evaluate it. You may not use the software in a live operating environment. The software is licensed as a single piece of software. You may not separate its component parts. You may access or use on more than one device. The Exceptions and Additional Terms for Particular Products as included in Exhibit A. 2. INTERNET-BASED SERVICES. Microsoft may provide Internet-based services with the software. It may change or cancel them at any time. -

Starting from Gabry.125Q + Questions in Other Dumps Starting from Last
Starting from Gabry.125q + questions in other dumps Number : 70-518 Passing Score : 800 Time Limit : 120 min File Version : 10.0 http://www.gratisexam.com/ Starting from last one of Garby.125q + questions from other dumps The questions in the sections: - Investigate (16) - From Other Dumps (19) - From Other Dumps 70-511? (5) require further investigation (though other answers given maybe questionable as well) In Short: Find your own answers! Some Q&A's seem duplicates, but they are mostly slight variations. Q36, Q37 and Q142 Q49, Q89 and Q143 Q76 and Q141 Q99 and Q130 (copies exist in Exam B for easy comparison) Sections 1. Investigate 2. From Other Dumps 3. From Other Dumps 70-511? Exam A QUESTION 1 You are designing a .NET Framework 4 solution. The solution contains a Windows Presentation Foundation (WPF) application and a Windows Communication Foundation (WCF) Web service. The WPF application uses the WCF Web service to store data in a Microsoft SQL Server 2008 database. You have the following requirements: Ensure that the WPF application functions while users' computers are offline. Minimize the time spent sending data to the WCF Web service. Minimize disk space requirements for data storage. You need to recommend an approach for synchronizing data between the WPF application and the database. Which two actions should you recommend? (Each correct answer presents part of the solution. Choose two.) A. Store data in custom business objects. Serialize data locally by using custom serialization. B. Create a local caching solution that periodically checks for Internet connectivity, uses local memory, and batches changes to the WCF Web service. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

WEKA Manual for Version 3-7-8
WEKA Manual for Version 3-7-8 Remco R. Bouckaert Eibe Frank Mark Hall Richard Kirkby Peter Reutemann Alex Seewald David Scuse January 21, 2013 ⃝c 2002-2013 University of Waikato, Hamilton, New Zealand Alex Seewald (original Commnd-line primer) David Scuse (original Experimenter tutorial) This manual is licensed under the GNU General Public License version 3. More information about this license can be found at http://www.gnu.org/licenses/gpl-3.0-standalone.html Contents ITheCommand-line 11 1Acommand-lineprimer 13 1.1 Introduction . 13 1.2 Basic concepts . 14 1.2.1 Dataset . 14 1.2.2 Classifier . 16 1.2.3 weka.filters . 17 1.2.4 weka.classifiers . 19 1.3 Examples . 23 1.4 Additional packages and the package manager . .24 1.4.1 Package management . 25 1.4.2 Running installed learning algorithms . 26 II The Graphical User Interface 29 2LaunchingWEKA 31 3PackageManager 35 3.1 Mainwindow ............................. 35 3.2 Installing and removing packages . 36 3.2.1 Unofficalpackages ...................... 37 3.3 Usingahttpproxy.......................... 37 3.4 Using an alternative central package meta data repository . 37 3.5 Package manager property file . 38 4SimpleCLI 39 4.1 Commands . 39 4.2 Invocation . 40 4.3 Command redirection . 40 4.4 Command completion . 41 5Explorer 43 5.1 The user interface . 43 5.1.1 Section Tabs . 43 5.1.2 Status Box . 43 5.1.3 Log Button . 44 5.1.4 WEKA Status Icon . 44 3 4 CONTENTS 5.1.5 Graphical output . 44 5.2 Preprocessing . 45 5.2.1 Loading Data . -

Tinkertool System 7 Reference Manual Ii
Documentation 0642-1075/2 TinkerTool System 7 Reference Manual ii Version 7.5, August 24, 2021. US-English edition. MBS Documentation 0642-1075/2 © Copyright 2003 – 2021 by Marcel Bresink Software-Systeme Marcel Bresink Software-Systeme Ringstr. 21 56630 Kretz Germany All rights reserved. No part of this publication may be redistributed, translated in other languages, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the publisher. This publication may contain examples of data used in daily business operations. To illustrate them as completely as possible, the examples include the names of individuals, companies, brands, and products. All of these names are fictitious and any similarity to the names and addresses used by an actual business enterprise is entirely coincidental. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. The publisher may make improvements and/or changes in the product(s) and/or the program(s) described in this publication at any time without notice. Make sure that you are using the correct edition of the publication for the level of the product. The version number can be found at the top of this page. Apple, macOS, iCloud, and FireWire are registered trademarks of Apple Inc. Intel is a registered trademark of Intel Corporation. UNIX is a registered trademark of The Open Group. Broadcom is a registered trademark of Broadcom, Inc. Amazon Web Services is a registered trademark of Amazon.com, Inc. -
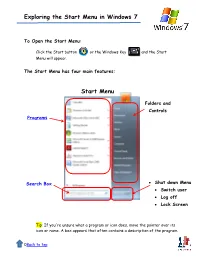
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

Sinhronizacija Podatkovnih Virov Z Uporabo Sinhronizacijskega Ogrodja Microsoft Sync Framework
UNIVERZA V LJUBLJANI FAKULTETA ZA RAČUNALNIŠTVO IN INFORMATIKO Martin Breskvar Sinhronizacija podatkovnih virov z uporabo sinhronizacijskega ogrodja Microsoft Sync Framework DIPLOMSKO DELO NA UNIVERZITETNEM ŠTUDIJU Mentor: doc. dr. Matija Marolt Ljubljana, 2011 I Z J A V A O A V T O R S T V U diplomskega dela Spodaj podpisani Martin Breskvar, z vpisno številko 63030139 sem avtor diplomskega dela z naslovom: Sinhronizacija podatkovnih virov z uporabo sinhronizacijskega ogrodja Microsoft Sync Framework. S svojim podpisom zagotavljam, da: sem diplomsko delo izdelal samostojno pod mentorstvom doc. dr. Matije Marolta so elektronska oblika diplomskega dela, naslov (slov., angl.), povzetek (slov., angl.) ter ključne besede (slov., angl.) identični s tiskano obliko diplomskega dela soglašam z javno objavo elektronske oblike diplomskega dela v zbirki „Dela FRI“ V Ljubljani, dne 15.9.2011 Podpis avtorja: ZAHVALA Na tem mestu se zahvaljujem mentorju doc. dr. Matiji Maroltu za nasvete, predloge in potrpežljivost pri nastajanju tega diplomskega dela. Zahvaljujem se Mateji za neumorno vzpodbudo ter vsem ostalim, ki so me nesebično podpirali v času mojega študija. Iskrena hvala. To delo je posvečeno moji mami. Kazalo 1 Uvod ......................................................................................................................... 1 1.1 Motivacija in namen diplomskega dela ...................................................................... 2 1.2 Predvideni rezultati in možnost njihove uporabe ..................................................... -

Eclipse Project Briefing Materials
[________________________] Eclipse project briefing materials. Copyright (c) 2002, 2003 IBM Corporation and others. All rights reserved. This content is made available to you by Eclipse.org under the terms and conditions of the Common Public License Version 1.0 ("CPL"), a copy of which is available at http://www.eclipse.org/legal/cpl-v10.html The most up-to-date briefing materials on the Eclipse project are found on the eclipse.org website at http://eclipse.org/eclipse/ 200303331 1 EclipseEclipse ProjectProject 200303331 3 Eclipse Project Aims ■ Provide open platform for application development tools – Run on a wide range of operating systems – GUI and non-GUI ■ Language-neutral – Permit unrestricted content types – HTML, Java, C, JSP, EJB, XML, GIF, … ■ Facilitate seamless tool integration – At UI and deeper – Add new tools to existing installed products ■ Attract community of tool developers – Including independent software vendors (ISVs) – Capitalize on popularity of Java for writing tools 200303331 4 Eclipse Overview Another Eclipse Platform Tool Java Workbench Help Development Tools JFace (JDT) SWT Team Your Tool Plug-in Workspace Development Debug Environment (PDE) Their Platform Runtime Tool Eclipse Project 200303331 5 Eclipse Origins ■ Eclipse created by OTI and IBM teams responsible for IDE products – IBM VisualAge/Smalltalk (Smalltalk IDE) – IBM VisualAge/Java (Java IDE) – IBM VisualAge/Micro Edition (Java IDE) ■ Initially staffed with 40 full-time developers ■ Geographically dispersed development teams – OTI Ottawa, OTI Minneapolis, -

Mediabeacon 20 Administrator Manual
MediaBeacon 20 Administrator Manual 10 - 2020 MediaBeacon Contents 1. Copyright Notice............................................................................................................................................ 4 2. Welcome.........................................................................................................................................................6 3. WebUI Configuration......................................................................................................................................7 3.1. Workspace Configuration...................................................................................................................... 7 3.1.1. Admin Mode.................................................................................................................................8 3.1.2. Admin Only Menu Commands......................................................................................................9 3.2. Manage Workspace Dialog.................................................................................................................. 10 3.2.1. Dialog Sections.......................................................................................................................... 11 3.3. Using Workspaces............................................................................................................................... 18 Workspaces Overview.........................................................................................................................18