Bitwarden Security Assessment Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
April, 2021 Spring
VVoolulummee 116731 SeptemAbperril,, 22002201 Goodbye LastPass, Hello BitWarden Analog Video Archive Project Short Topix: New Linux Malware Making The Rounds Inkscape Tutorial: Chrome Text FTP With Double Commander: How To Game Zone: Streets Of Rage 4: Finaly On PCLinuxOS! PCLinuxOS Recipe Corner: Chicken Parmesan Skillet Casserole Beware! A New Tracker You Might Not Be Aware Of And More Inside... In This Issue... 3 From The Chief Editor's Desk... 4 Screenshot Showcase The PCLinuxOS name, logo and colors are the trademark of 5 Goodbye LastPass, Hello BitWarden! Texstar. 11 PCLinuxOS Recipe Corner: The PCLinuxOS Magazine is a monthly online publication containing PCLinuxOS-related materials. It is published primarily for members of the PCLinuxOS community. The Chicken Parmesean Skillet Casserole magazine staff is comprised of volunteers from the 12 Inkscape Tutorial: Chrome Text PCLinuxOS community. 13 Screenshot Showcase Visit us online at http://www.pclosmag.com 14 Analog Video Archive Project This release was made possible by the following volunteers: Chief Editor: Paul Arnote (parnote) 16 Screenshot Showcase Assistant Editor: Meemaw Artwork: ms_meme, Meemaw Magazine Layout: Paul Arnote, Meemaw, ms_meme 17 FTP With Double Commander: How-To HTML Layout: YouCanToo 20 Screenshot Showcase Staff: ms_meme Cg_Boy 21 Short Topix: New Linux Malware Making The Rounds Meemaw YouCanToo Pete Kelly Daniel Meiß-Wilhelm 24 Screenshot Showcase Alessandro Ebersol 25 Repo Review: MiniTube Contributors: 26 Good Words, Good Deeds, Good News David Pardue 28 Game Zone: Streets Of Rage 4: Finally On PCLinuxOS! 31 Screenshot Showcase 32 Beware! A New Tracker You Might Not Be Aware Of The PCLinuxOS Magazine is released under the Creative Commons Attribution-NonCommercial-Share-Alike 3.0 36 PCLinuxOS Recipe Corner Bonus: Unported license. -

Ovum Market Radar: Password Management Tools
Ovum Market Radar: Password Management Tools Improving cybersecurity by eliminating weak, reused, and compromised passwords Publication Date: 17 Aug 2019 | Product code: INT005-000010KEEPER Richard Edwards Ovum Market Radar: Password Management Tools Summary Catalyst Cybersecurity often depends on the choices made by individuals. Most of these individuals are conscientious when it comes to preserving the confidentiality, integrity, and availability of corporate systems and customer data. However, if we consider the ways in which passwords and account credentials are used and managed, we can easily see weaknesses in our cybersecurity defenses. Password management tools have entered the mainstream, with more than 70 apps competing for user attention in the Google Play Store alone. There’s also a good selection of products targeting teams, businesses, and enterprises. However, these products need to adapt and evolve to win new business, protect against new cybersecurity threats, and support the move toward a “password-less” enterprise. Ovum view Key findings from an Ovum survey of IT decision-makers and enterprise employees reveals that password management practices are out of date, overly reliant on manual processes, and highly dependent on employees “doing the right thing”. If the alarm bell isn’t ringing, it should be. Cybersecurity training and awareness programs are useful, but to keep the business safe and secure, employees across all roles and at all levels require tools and applications to help alleviate the burden and risks associated with workplace passwords, credentials, logins, and access codes. Key messages ▪ Passwords are for more than just the web. Credentials and passcodes are required for desktop applications, mobile apps, IT infrastructure, physical access, and more. -

A Security Analysis of Autofill on Ios and Android
The Emperor’s New Autofill Framework: A Security Analysis of Autofill on iOS and Android Sean Oesch, Anuj Gautam, Scott Ruoti The University of Tennessee [email protected], [email protected], [email protected] Abstract—Password managers help users more effectively (P3) the filled credential will only be accessible to the manage their passwords, encouraging them to adopt stronger mapped app or web domain. [23]. passwords across their many accounts. In contrast to desktop On desktop environments, password managers are primarily systems where password managers receive no system-level support, mobile operating systems provide autofill frameworks implemented as ad-hoc browser extensions—i.e., the extension that are designed to integrate with password managers to individually implements all aspects of the autofill process provide secure and usable autofill for browsers and other apps without support from OS or browser autofill frameworks. installed on mobile devices. In this paper, we conduct the first While some desktop password managers correctly achieve P1 holistic security evaluation of such frameworks on iOS and and P2 [19], many have incorrect implementations that allow Android, examining whether they achieve substantive benefits over the ad-hoc desktop environment or become a problematic attackers to steal or phish users’ credentials [14], [22], [23], single point of failure. Our results find that while the [19], and none can fully implement P3 due to technical frameworks address several common issues (e.g., requiring user limitations of browser extension APIs [23], [19]. interaction before autofill), they also enforce insecure behavior In contrast to the situation on desktop, mobile operating and fail to provide the password managers implemented using systems provide system-wide autofill frameworks that attempt the frameworks with sufficient information to override this incorrect behavior. -

Insight Manufacturers, Publishers and Suppliers by Product Category
Manufacturers, Publishers and Suppliers by Product Category 2/15/2021 10/100 Hubs & Switch ASANTE TECHNOLOGIES CHECKPOINT SYSTEMS, INC. DYNEX PRODUCTS HAWKING TECHNOLOGY MILESTONE SYSTEMS A/S ASUS CIENA EATON HEWLETT PACKARD ENTERPRISE 1VISION SOFTWARE ATEN TECHNOLOGY CISCO PRESS EDGECORE HIKVISION DIGITAL TECHNOLOGY CO. LT 3COM ATLAS SOUND CISCO SYSTEMS EDGEWATER NETWORKS INC Hirschmann 4XEM CORP. ATLONA CITRIX EDIMAX HITACHI AB DISTRIBUTING AUDIOCODES, INC. CLEAR CUBE EKTRON HITACHI DATA SYSTEMS ABLENET INC AUDIOVOX CNET TECHNOLOGY EMTEC HOWARD MEDICAL ACCELL AUTOMAP CODE GREEN NETWORKS ENDACE USA HP ACCELLION AUTOMATION INTEGRATED LLC CODI INC ENET COMPONENTS HP INC ACTI CORPORATION AVAGOTECH TECHNOLOGIES COMMAND COMMUNICATIONS ENET SOLUTIONS INC HYPERCOM ADAPTEC AVAYA COMMUNICATION DEVICES INC. ENGENIUS IBM ADC TELECOMMUNICATIONS AVOCENT‐EMERSON COMNET ENTERASYS NETWORKS IMC NETWORKS ADDERTECHNOLOGY AXIOM MEMORY COMPREHENSIVE CABLE EQUINOX SYSTEMS IMS‐DELL ADDON NETWORKS AXIS COMMUNICATIONS COMPU‐CALL, INC ETHERWAN INFOCUS ADDON STORE AZIO CORPORATION COMPUTER EXCHANGE LTD EVGA.COM INGRAM BOOKS ADESSO B & B ELECTRONICS COMPUTERLINKS EXABLAZE INGRAM MICRO ADTRAN B&H PHOTO‐VIDEO COMTROL EXACQ TECHNOLOGIES INC INNOVATIVE ELECTRONIC DESIGNS ADVANTECH AUTOMATION CORP. BASF CONNECTGEAR EXTREME NETWORKS INOGENI ADVANTECH CO LTD BELDEN CONNECTPRO EXTRON INSIGHT AEROHIVE NETWORKS BELKIN COMPONENTS COOLGEAR F5 NETWORKS INSIGNIA ALCATEL BEMATECH CP TECHNOLOGIES FIRESCOPE INTEL ALCATEL LUCENT BENFEI CRADLEPOINT, INC. FORCE10 NETWORKS, INC INTELIX -

The Case of Interaction Problems Between Password Managers and Websites
They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites Nicolas HuamanC ∗ Sabrina Amft∗ Marten OltroggeC Yasemin Acary ∗ Sascha FahlC ∗ CCISPA Helmholtz Center for Information Security ∗Leibniz University Hannover yMax Planck Institute for Security and Privacy Abstract—Password managers are tools to support users with previous research on PWMs mostly focuses on PWM security the secure generation and storage of credentials and logins issues and usability and adoption challenges. Multiple studies used in online accounts. Previous work illustrated that building researched the security of different PWM types, finding that password managers means facing various security and usability challenges. For strong security and good usability, the interaction both browser-based and locally installed PWMs are vulner- between password managers and websites needs to be smooth and able to problems such as key theft or secret recovery from effortless. However, user reviews for popular password managers temporary files, as well as weaknesses within typical features suggest interaction problems for some websites. Therefore, to the such as autofill [64]. Other research focused on the usability best of our knowledge, this work is the first to systematically iden- of PWMs and were able to show that user adoption of PWMs tify these interaction problems and investigate how 15 desktop password managers, including the ten most popular ones, are is motivated by convenience of usage and usability [59]. affected. We use a qualitative analysis approach to identify 39 While security benefits can also be a driving factor for PWM interaction problems from 2,947 user reviews and 372 GitHub adoption, in the majority of cases these where only mentioned issues for 30 password managers. -

Android Password Managers and Vault Applications: an Investigation on Data Remanence in Main Memory
Android Password Managers and Vault Applications: An Investigation on Data Remanence in Main Memory Peter Sabev and Milen Petrov Faculty of Mathematics and Informatics, Sofi a University “St. Kliment Ohridski”, 5 James Bourchier Blvd., 1164, Sofi a, Bulgaria, {petar.sabev, milenp}@fmi.uni-sofi a.bg, Abstract. An application defi ning itself as password management / secure vault software should meet a number of security requirements in order to provide an adequate data protection. The data entrusted to such application is its most valuable asset that the application is responsible to protect. To check to what degree the popular Android password managers / vault applications are protecting their data loaded into main memory, we analyze the runtime behavior of two of them from security perspective. More specifi cally, we suggest a main memory inspection procedure helpful for evaluation of the extent of how secure a given software application is in regards to prevention of secrets exposure. Then we apply this procedure to conduct a digital investigation in a forensically sound manner by focusing on data remanence in main memory. In conclusion, we summarize the investigation results by showing what part of the data entrusted to applications examined remains exposed in clear text in main memory. Keywords: Android Password Managers, Vault Applications, Main Memory Inves- tigation, Data Remanence, Security Analysis, Garbage Collection. 1 Introduction An application defi ning itself as a password management / secure vault software should be built upon a strong security architecture, effi cient security mechanisms and strong defense techniques in order to provide a secure environment. It must not only allowing for secure storage, processing and management of sensitive data, but also allowing for a much higher level of security compared to a general- purpose software application. -
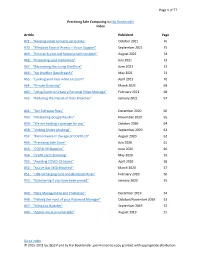
Practicing Safe Computing by Hal Bookbinder Index
Page 1 of 77 Practicing Safe Computing by Hal Bookbinder Index Article Published Page #71: “Keeping email contacts up to date” October 2021 76 #70: “Windows Ease of Access – Vision Support” September 2021 75 #69: “Even an 8-year-old Yahoo breach can bite!” August 2021 74 #68: “Protecting your credentials” July 2021 73 #67: ”Recovering files using OneDrive” June 2021 72 #66: “Yet Another Data Breach!” May 2021 71 #65: “Looking your best while on Zoom” April 2021 70 #64: “Private Browsing” March 2021 69 #63: “Using Zoom to Create a Personal Video Message” February 2021 68 #62: “Reducing the Impact of Data Breaches” January 2021 67 #61: “Ten Software Fixes” December 2020 66 #60: “Misleading Google Results” November 2020 65 #59: “We are holding a package for you” October 2020 64 #58: “Vishing (Voice phishing)” September 2020 63 #57: “Ransomware in the age of COVID-19” August 2020 62 #56: “Practicing Safe Zoom” July 2020 61 #55: “COVID-19 Statistics” June 2020 60 #54: “Credit card skimming” May 2020 59 #53: “Avoiding COVID-19 Scams” April 2020 58 #52: “You've Got DNA Matches!” March 2020 57 #51: “USB recharging cord and Bluetooth Risks” February 2020 56 #50: “Discovering if you have been pwned” January 2020 55 #49: “Data Management and Protection” December 2019 54 #48: “Making the most of your Password Manager” October/November 2019 53 #47: “Windows Updates” September 2019 52 #46: “Apples are also vulnerable” August 2019 51 Go to Index © 2015-2021 by JGSCV and by Hal Bookbinder, permission to copy granted with appropriate attribution. -

Convenient Password Manager
Distributed Computing Convenient Password Manager Bachelor’s Thesis Noé Heim [email protected] Distributed Computing Group Computer Engineering and Networks Laboratory ETH Zürich Supervisors: Simon Tanner, Roland Schmid Prof. Dr. Roger Wattenhofer June 8, 2020 Acknowledgements I would like to thank Simon Tanner and Roland Schmid, for always offering their support, when I was faced with difficulties, and guiding me through my very first scientific research project. Further, I would like to thank Prof. Dr. Roger Wattenhofer for encouraging me with his enthusiasm for this project. I’m grateful that I had the opportunity to work with and learn from so knowl- edgeable people. Lastly, I would like to thank my family and friends, who supported me and motivated me as I approached the end of this thesis. i Abstract Password managers are a useful aid for remembering and securely storing pass- words. As it is crucial to provide adequate security given the sensitive data they contain, many password managers offer two-factor and multi-factor authentica- tion. However, most of them use a single database which can introduce security risks. In this thesis, we attempt to extend PolyPass, a distributed password man- ager, with Bluetooth communication. Our goal is to increase the reliability of the password manager, as well as the ease of access to passwords. To achieve said goal, the communication had to be restructured. The Bluetooth communication is still problematic, since their messages are not reliably delivered, which renders the password manager -

Reconsidering the Usability of Password Managers
BYPASS: RECONSIDERING THE USABILITY OF PASSWORD MANAGERS TINA SAFAIE A THESIS IN THE DEPARTMENT OF CONCORDIA INSTITUTE FOR INFORMATION SYSTEMS ENGINEERING PRESENTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF APPLIED SCIENCE IN INFORMATION SYSTEMS SECURITY CONCORDIA UNIVERSITY MONTRÉAL,QUÉBEC,CANADA APRIL 2021 © TINA SAFAIE, 2021 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Tina Safaie Entitled: ByPass: Reconsidering the Usability of Password Managers and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science in Information Systems Security complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the final examining committee: Dr. Walter Lucia Chair Dr. Mohammad Mannan Supervisor Dr. Amr Youssef Supervisor Dr. Elizabeth Stobert Supervisor Dr. Jermey Clark Examiner Dr. Walter Lucia Examiner Approved Dr. Mohammad Mannan, Graduate Program Director Chair of Department or Graduate Program Director April 2021 Dr. Mourad Debbabi, Acting Dean Gina Cody School of Engineering and Computer Science ABSTRACT ByPass: Reconsidering the Usability of Password Managers Tina Safaie Since passwords are an unavoidable mechanism for authenticating to online services, ex- perts often recommend using a password manager for better password security. However, adoption of password managers is low due to poor usability, the difficulty of migrating ac- counts to a manager, and users’ sense that a manager will not add value. In this work, we present ByPass, a novel password manager that is placed between the user and the web- site for secure and direct communication between the manager and websites. -

PDF Bitwarden Security White Paper V0.2
SECURITY PAPER 0 Bitwarden Security Whitepaper - October 2020 Overview of Bitwarden Security and Compliance Program 2 Bitwarden Security Principles 3 User Data Protection 3 Master Password 3 Overview of the Master Password Hashing, Key Derivation, and Encryption Process 7 User Account Creation 7 User Login | User Authentication | Access to User Vault Data 9 Additional User Data Protection when enabling Two-step login 10 Changing User Password 11 Rotating Your Accounts Encryption Key 11 Data Protection in Transit 12 Data Protection at Rest 12 How Vault Items Are Secured 13 Vault Health Reports 13 Importing Passwords and Other Secrets into Bitwarden 13 Sharing Data between Users 14 Access Controls and Managing Bitwarden Collections 15 Event Logs 15 SIEM Integration and External Systems 15 Account Protection and Avoiding Lockout 16 Bitwarden Cloud Platform and Web Application Security 16 Bitwarden Architecture Overview 16 Security Updates and Patching 17 Bitwarden Access Controls 17 Software Lifecycle and Change Management 18 Control of Production Systems 19 Bitwarden Platform Key Management Procedures 19 Data Types and Data Retention 19 Logging, Monitoring, and Alert Notification 20 Business Continuity / Disaster Recovery 20 Threat Prevention and Response 21 Auditability and Compliance 21 HTTP Security Headers 22 Threat Model and Attack Surface Analysis Overview 22 Bitwarden Clients 22 HTTPS TLS and Web Browser Crypto End-to-End Encryption 23 Code Assessments 23 Conclusion 23 (c) Bitwarden, Inc. CONFIDENTIAL 1 Bitwarden Security Whitepaper - October 2020 Overview of Bitwarden Security and Compliance Program With remote work on the rise and internet usage higher than ever before, the demand to create and maintain dozens (if not hundreds) of online accounts with logins and passwords is staggering. -

How-To – Manage Your Passwords
CartONG – 23 boulevard du musée, 73000 Chambéry – France www.cartong.org | [email protected] HOW-TO – MANAGE YOUR PASSWORDS This How-to applies to all CartONG’s staff, interns, service civiques, board and individual consultants. General 1/ The use of Bitwarden as a password management system is mandatory 2/ Shared accounts are prohibited. I. What is a secured password? To be secured, a password should be difficult for a computer program to hack. Passwords have: . To be long enough (min. of 12 characters) . To be complex (i.e. using special characters, figures, upper and lower cases, etc.) . To NOT be easily identifiable (e.g. not based on a date such as birthday) . The same password shouldn’t be used twice and passwords need to be changed regularly To test the strength of your passwords you can use: http://www.passfault.com/ In case of a password provided or managed by a partner is not following the above rules, the partner need to be inform at least once in writing by the PM. To generate highly complexed passwords, different solutions exist such as: . Every time that is possible: use a non-human-generated password. The web application, mobile app and browser extension of Bitwarden are offering such a service. Use passphrases such as “Myst!fyFrostlike07DisorderChessReverse15Portal”, use the first letters of each word in a given sentence (W@yft%10lra? for “Where are you found these ten lovely red apples?”), use a schema on your keyboard, etc. II. Other general password management rules All staff have to use Bitwarden as the password management system to store ALL their professional passwords (individual ones, shared ones, passwords shared by partners, etc.). -

An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices
University of Tennessee, Knoxville TRACE: Tennessee Research and Creative Exchange Doctoral Dissertations Graduate School 5-2021 An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices Timothy Oesch [email protected] Follow this and additional works at: https://trace.tennessee.edu/utk_graddiss Part of the Information Security Commons, Other Computer Engineering Commons, and the Other Computer Sciences Commons Recommended Citation Oesch, Timothy, "An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices. " PhD diss., University of Tennessee, 2021. https://trace.tennessee.edu/utk_graddiss/6670 This Dissertation is brought to you for free and open access by the Graduate School at TRACE: Tennessee Research and Creative Exchange. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of TRACE: Tennessee Research and Creative Exchange. For more information, please contact [email protected]. To the Graduate Council: I am submitting herewith a dissertation written by Timothy Oesch entitled "An Analysis of Modern Password Manager Security and Usage on Desktop and Mobile Devices." I have examined the final electronic copy of this dissertation for form and content and recommend that it be accepted in partial fulfillment of the equirr ements for the degree of Doctor of Philosophy, with a major in Computer Engineering. Scott I. Ruoti, Major Professor We have read this dissertation and recommend its acceptance: Kent Seamons, Jinyuan Sun, Doowon Kim, Scott I. Ruoti Accepted for the Council: Dixie L. Thompson Vice Provost and Dean of the Graduate School (Original signatures are on file with official studentecor r ds.) An Analysis of Password Manager Security and Usage on Desktop and Mobile Devices A Dissertation Presented for the Doctor of Philosophy Degree The University of Tennessee, Knoxville Timothy Sean Oesch May 2021 © by Timothy Sean Oesch, 2021 All Rights Reserved.