MPLP 5Th Friday Webinar January 2021
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
April, 2021 Spring
VVoolulummee 116731 SeptemAbperril,, 22002201 Goodbye LastPass, Hello BitWarden Analog Video Archive Project Short Topix: New Linux Malware Making The Rounds Inkscape Tutorial: Chrome Text FTP With Double Commander: How To Game Zone: Streets Of Rage 4: Finaly On PCLinuxOS! PCLinuxOS Recipe Corner: Chicken Parmesan Skillet Casserole Beware! A New Tracker You Might Not Be Aware Of And More Inside... In This Issue... 3 From The Chief Editor's Desk... 4 Screenshot Showcase The PCLinuxOS name, logo and colors are the trademark of 5 Goodbye LastPass, Hello BitWarden! Texstar. 11 PCLinuxOS Recipe Corner: The PCLinuxOS Magazine is a monthly online publication containing PCLinuxOS-related materials. It is published primarily for members of the PCLinuxOS community. The Chicken Parmesean Skillet Casserole magazine staff is comprised of volunteers from the 12 Inkscape Tutorial: Chrome Text PCLinuxOS community. 13 Screenshot Showcase Visit us online at http://www.pclosmag.com 14 Analog Video Archive Project This release was made possible by the following volunteers: Chief Editor: Paul Arnote (parnote) 16 Screenshot Showcase Assistant Editor: Meemaw Artwork: ms_meme, Meemaw Magazine Layout: Paul Arnote, Meemaw, ms_meme 17 FTP With Double Commander: How-To HTML Layout: YouCanToo 20 Screenshot Showcase Staff: ms_meme Cg_Boy 21 Short Topix: New Linux Malware Making The Rounds Meemaw YouCanToo Pete Kelly Daniel Meiß-Wilhelm 24 Screenshot Showcase Alessandro Ebersol 25 Repo Review: MiniTube Contributors: 26 Good Words, Good Deeds, Good News David Pardue 28 Game Zone: Streets Of Rage 4: Finally On PCLinuxOS! 31 Screenshot Showcase 32 Beware! A New Tracker You Might Not Be Aware Of The PCLinuxOS Magazine is released under the Creative Commons Attribution-NonCommercial-Share-Alike 3.0 36 PCLinuxOS Recipe Corner Bonus: Unported license. -

Password Managers an Overview
Peter Albin Lexington Computer and Technology Group March 13, 2019 Agenda One Solution 10 Worst Passwords of 2018 Time to Crack Password How Hackers Crack Passwords How Easy It Is To Crack Your Password How Do Password Managers Work What is a Password Manager Why use a Password Manager? Cloud Based Password Managers Paid Password Managers Free Password Managers How to Use LastPass How to Use Dashlane How to Use Keepass Final Reminder References March 13, 2019 2 One Solution March 13, 2019 3 10 Worst Passwords of 2018 1. 123456 2. password 3. 123456789 4. 12345678 5. 12345 6. 111111 7. 1234567 8. sunshine 9. qwerty 10. iloveyou March 13, 2019 4 Time to Crack Password March 13, 2019 5 Time to Crack Password March 13, 2019 6 Time to Crack Password March 13, 2019 7 Time to Crack Password Time to crack password "security1" 1600 1400 1200 1000 Days 800 Days 600 400 200 0 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 Year March 13, 2019 8 How Hackers Crack Passwords https://youtu.be/YiRPt4vrSSw March 13, 2019 9 How Easy It Is To Crack Your Password https://youtu.be/YiRPt4vrSSw March 13, 2019 10 How Do Password Managers Work https://youtu.be/DI72oBhMgWs March 13, 2019 11 What is a Password Manager A password manager will generate, retrieve, and keep track of super-long, crazy-random passwords across countless accounts for you, while also protecting all your vital online info—not only passwords but PINs, credit-card numbers and their three-digit CVV codes, answers to security questions, and more … And to get all that security, you’ll only need to remember a single password March 13, 2019 12 Why use a Password Manager? We are terrible at passwords We suck at creating them the top two most popular remain “123456” and “password” We share them way too freely We forget them all the time We forget them all the time A password manager relieves the burden of thinking up and memorizing unique, complex logins—the hallmark of a secure password. -
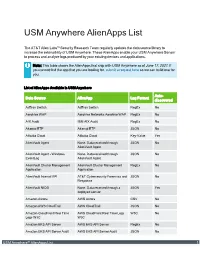
USM Anywhere Alienapps List
USM Anywhere AlienApps List The AT&T Alien Labs™ Security Research Team regularly updates the data source library to increase the extensibility of USM Anywhere. These AlienApps enable your USM Anywhere Sensor to process and analyze logs produced by your existing devices and applications. Note: This table shows the AlienApps that ship with USM Anywhere as of June 17, 2021. If you cannot find the app that you are looking for, submit a request here so we can build one for you. List of AlienApps Available in USM Anywhere Auto- Data Source AlienApp Log Format discovered AdTran Switch AdTran Switch RegEx No Aerohive WAP Aerohive Networks Aerohive WAP RegEx No AIX Audit IBM AIX Audit RegEx No Akamai ETP Akamai ETP JSON No Alibaba Cloud Alibaba Cloud Key-Value Yes AlienVault Agent None. Data received through JSON No AlienVault Agent AlienVault Agent - Windows None. Data received through JSON No EventLog AlienVault Agent AlienVault Cluster Management AlienVault Cluster Management RegEx No Application Application AlienVault Internal API AT&T Cybersecurity Forensics and JSON No Response AlienVault NIDS None. Data received through a JSON Yes deployed sensor Amazon Aurora AWS Aurora CSV No Amazon AWS CloudTrail AWS CloudTrail JSON No Amazon CloudFront Real Time AWS CloudFront Real Time Logs W3C No Logs W3C W3C Amazon EKS API Server AWS EKS API Server RegEx No Amazon EKS API Server Audit AWS EKS API Server Audit JSON No USM Anywhere™ AlienApps List 1 List of AlienApps Available in USM Anywhere (Continued) Auto- Data Source AlienApp Log Format discovered -

HACK Enpass Password Manager
1 / 2 HACK Enpass Password Manager Mar 23, 2021 — So, is this password manager right for you or your business? In our Enpass review, we'll take a closer look at everything this software has to offer.. Results 1 - 100 of 338 — TOTP is an algorithm that computes a one-time password from a shared secret ... codes to protect your online accounts from hackers (bad guys). ... code in my password manager, especially for password managers that can ... Segregate data using Multiple vaults Enpass facilitates you with an option to .... Jan 9, 2019 — Password manager company OneLogin was actually hacked, and the ... EnPass: Here's something unusual—a password manager that goes .... Use Enpass audit tools to identify weak, identical, and old passwords. Your password manager is your digital security best friend. You are using a password .... The Synology Disk Station Manager (DSM) is the Operating System (OS) that runs on your Synology unit. ... a prerequisite while using Enpass it is not really neccessary to me to sync with CloudStation. ... For iOS 13/12 users: Open the Settings app > Passwords & Accounts > Add Account > Other ... Mikrotik hack github.. We will send a One-time password (OTP) to your registered email address and ... set of Enpass users by letting them store their time based one time passwords of ... Hackers use credit card skimmers to obtain the magnetic stripe information of a ... Open Google Chrome and click the GateKeeper Password Manager Chrome .... Jun 16, 2021 — Using an online password manager? … Are they safe from hackers?? Use Enpass to securely organize everything at one place. -

Ovum Market Radar: Password Management Tools
Ovum Market Radar: Password Management Tools Improving cybersecurity by eliminating weak, reused, and compromised passwords Publication Date: 17 Aug 2019 | Product code: INT005-000010KEEPER Richard Edwards Ovum Market Radar: Password Management Tools Summary Catalyst Cybersecurity often depends on the choices made by individuals. Most of these individuals are conscientious when it comes to preserving the confidentiality, integrity, and availability of corporate systems and customer data. However, if we consider the ways in which passwords and account credentials are used and managed, we can easily see weaknesses in our cybersecurity defenses. Password management tools have entered the mainstream, with more than 70 apps competing for user attention in the Google Play Store alone. There’s also a good selection of products targeting teams, businesses, and enterprises. However, these products need to adapt and evolve to win new business, protect against new cybersecurity threats, and support the move toward a “password-less” enterprise. Ovum view Key findings from an Ovum survey of IT decision-makers and enterprise employees reveals that password management practices are out of date, overly reliant on manual processes, and highly dependent on employees “doing the right thing”. If the alarm bell isn’t ringing, it should be. Cybersecurity training and awareness programs are useful, but to keep the business safe and secure, employees across all roles and at all levels require tools and applications to help alleviate the burden and risks associated with workplace passwords, credentials, logins, and access codes. Key messages ▪ Passwords are for more than just the web. Credentials and passcodes are required for desktop applications, mobile apps, IT infrastructure, physical access, and more. -

Password Managers
Password Managers A Higher Education Information Security Council (HEISC) Resource JULY 2019 Password Managers What Is a Password Manager Tool? A password manager tool is software that helps users encrypt, store, and manage passwords. The tool also helps users create secure passwords and automatically log in to websites. Who Might Use a Password Manager Tool, and Why? Users should employ unique passwords for each website or system to help minimize the impact from the breach of one website or system; however, most users cannot remember a separate password for many sites and tend to reuse passwords or write them on a sticky note attached to their computer. Additionally, organizations may have passwords that need to be shared across teams and want a secure method to do so. Password manager tools allow users and teams to more securely manage many distinct passwords and automatically log them in to websites. The Benefits of Using a Password Manager Tool Password manager tools enable users to create and securely store unique passwords for websites, applications, and other systems without having to memorize or write them down. Risks to Consider When Using a Password Manager Tool Special care should be taken to secure the password tool, as it will grant access to all passwords. The “master” password that grants access to the tool should be very strong and unique, and multifactor authentication should be used if possible. Almost all modern commercial password managers allow users to implement some form of multifactor authentication. You will also need to decide whether you want your password management tool to store passwords locally or in the cloud. -

Elcomsoft Distributed Password Recovery Unlocks 1Password, Keepass, Lastpass and Dashlane Vaults
Elcomsoft Distributed Password Recovery Unlocks 1Password, KeePass, LastPass and Dashlane Vaults Moscow, Russia – August 10, 2017 - ElcomSoft Co. Ltd. updates Distributed Password Recovery, enabling the recovery of master keys protecting encrypted vaults of four popular password managers: 1Password, KeePass, LastPass and Dashlane. By attacking a single master password, experts can gain access to the entire database containing all of the user’s saved passwords, authentication credentials and other highly sensitive information. Password managers’ protected vaults may contain images of user’s documents, various identity- related information, payment and loyalty card numbers. “We’re continuing our quest on expanding the types of passwords we can break”, says Vladimir Katalov, ElcomSoft CEO. “This time we are targeting four of the most popular password managers, allowing experts gaining access to protected vaults containing users’ authentication credentials, stored logins, passwords and forms to numerous resources. With today’s password managers this only requires breaking a single master password.” One Password to Rule Them All The idea behind all password management apps is simple: allowing users to securely store, organize and use passwords required to authenticate into various resources. As the user no longer has to remember the many different passwords, the use of password managers effectively cuts password re-use and stimulates the use of strong, unique passwords to protect different resources. Password managers can even automatically generate strong, random passwords that are unique per Web site or resource, rendering both dictionary and brute-force attacks ineffective. These passwords are stored in encrypted vaults, and can be only decrypted once the user enters their master password. -

December 2014 Using Your Smart Phone As a Credit Card Substitute
Newsletter of the Potomac Area Technology and Computer Society December 2014 www.patacs.org Page 1 Using Your Smart Phone as a Credit Card Substitute by Ira Wilsker WEBSITES: https://www.paypal.com/us/webapps/mpp/pay-in- http://currentc.com stores http://www.pcworld.com/article/2607312/how- https://www.paypal.com/us/webapps/mpp/store- apple-pay-could-make-the-target-and-home- locator depot-breaches-a-thing-of-the-past.html http://www.pcworld.com/article/2846535/a-guide- https://www.gosoftcard.com to-the-top-mobile-payments-options.html https://wallet.google.com http://www.apple.com/apple-pay/ https://www.google.com/wallet/shop-in-stores/ www.mercurynews.com/business/ci_26938386/ http://www.mastercard.us/cardholder-services/ mobile-payments-apple-pay-google-wallet-and- paypass-locator.html otherhttp://currentc.com http://www.pcworld.com/article/2607312/how- (continued on page 2) Using Your Smart Phone as a Credit Card Substitute ………...…....1 Fairfax October Meeting ……………………………………………6 Linux Sites Recommended By Geof Goodrum………………..........8 With All of the Media Reports About Massive Data Breaches, What Can We Do?..............................................................................9 Valuable Information From the PATACS Site ………………….....12 Vendors Recommended By Members…..…………………………..13 PATACS Annual Financial Report, Fiscal Year 2014 ……………...l4 PATACS Information ……………………………………………..,.15 December 2014 PATACS Posts Page 2 the number of Euro- pean credit and debit cards that were hi- jacked was much smaller. For the past several years, the ma- jority of European (and many Asian) issued cards have had a more secure embed- ded microchip that contained the cus- tomer information, It should be news to no one that over the rather than the magnetic stripe widely used past year there have been massive data breaches at here. -

A Security Analysis of Autofill on Ios and Android
The Emperor’s New Autofill Framework: A Security Analysis of Autofill on iOS and Android Sean Oesch, Anuj Gautam, Scott Ruoti The University of Tennessee [email protected], [email protected], [email protected] Abstract—Password managers help users more effectively (P3) the filled credential will only be accessible to the manage their passwords, encouraging them to adopt stronger mapped app or web domain. [23]. passwords across their many accounts. In contrast to desktop On desktop environments, password managers are primarily systems where password managers receive no system-level support, mobile operating systems provide autofill frameworks implemented as ad-hoc browser extensions—i.e., the extension that are designed to integrate with password managers to individually implements all aspects of the autofill process provide secure and usable autofill for browsers and other apps without support from OS or browser autofill frameworks. installed on mobile devices. In this paper, we conduct the first While some desktop password managers correctly achieve P1 holistic security evaluation of such frameworks on iOS and and P2 [19], many have incorrect implementations that allow Android, examining whether they achieve substantive benefits over the ad-hoc desktop environment or become a problematic attackers to steal or phish users’ credentials [14], [22], [23], single point of failure. Our results find that while the [19], and none can fully implement P3 due to technical frameworks address several common issues (e.g., requiring user limitations of browser extension APIs [23], [19]. interaction before autofill), they also enforce insecure behavior In contrast to the situation on desktop, mobile operating and fail to provide the password managers implemented using systems provide system-wide autofill frameworks that attempt the frameworks with sufficient information to override this incorrect behavior. -

Revisiting Security Vulnerabilities in Commercial Password Managers?
Revisiting Security Vulnerabilities in Commercial Password Managers? Michael Carr1 and Siamak F. Shahandashti2 1 Piksel, York Science Park, YO10 5ZD, UK [email protected] 2 Dept. of Computer Science, University of York, YO10 5GH, UK [email protected] Abstract. In this work we analyse five popular commercial password managers for security vulnerabilities. Our analysis is twofold. First, we compile a list of previously disclosed vulnerabilities through a compre- hensive review of the academic and non-academic sources and test each password manager against all the previously disclosed vulnerabilities. We find a mixed picture of fixed and persisting vulnerabilities. Then we carry out systematic functionality tests on the considered password managers and find four new vulnerabilities. Notably, one of the new vulnerabilities we identified allows a malicious app to impersonate a legitimate app to two out of five widely-used password managers we tested and as a result steal the user's password for the targeted service. We implement a proof- of-concept attack to show the feasibility of this vulnerability in a real-life scenario. Finally, we report and reflect on our experience of responsible disclosure of the newly discovered vulnerabilities to the corresponding password manager vendors. Keywords: Vulnerability Testing · Password Managers · Password Man- ager Security · Authentication. 1 Introduction Passwords remain the dominant authentication mechanism in the digital realm despite their shortcomings. Furthermore, they are expected to persist as a pri- mary authentication mechanism for the some time [6]. Among the tools that can greatly reduce the cognitive burden of remembering multiple passwords for arXiv:2003.01985v2 [cs.CR] 17 Mar 2020 multiple services are password managers. -

Insight Manufacturers, Publishers and Suppliers by Product Category
Manufacturers, Publishers and Suppliers by Product Category 2/15/2021 10/100 Hubs & Switch ASANTE TECHNOLOGIES CHECKPOINT SYSTEMS, INC. DYNEX PRODUCTS HAWKING TECHNOLOGY MILESTONE SYSTEMS A/S ASUS CIENA EATON HEWLETT PACKARD ENTERPRISE 1VISION SOFTWARE ATEN TECHNOLOGY CISCO PRESS EDGECORE HIKVISION DIGITAL TECHNOLOGY CO. LT 3COM ATLAS SOUND CISCO SYSTEMS EDGEWATER NETWORKS INC Hirschmann 4XEM CORP. ATLONA CITRIX EDIMAX HITACHI AB DISTRIBUTING AUDIOCODES, INC. CLEAR CUBE EKTRON HITACHI DATA SYSTEMS ABLENET INC AUDIOVOX CNET TECHNOLOGY EMTEC HOWARD MEDICAL ACCELL AUTOMAP CODE GREEN NETWORKS ENDACE USA HP ACCELLION AUTOMATION INTEGRATED LLC CODI INC ENET COMPONENTS HP INC ACTI CORPORATION AVAGOTECH TECHNOLOGIES COMMAND COMMUNICATIONS ENET SOLUTIONS INC HYPERCOM ADAPTEC AVAYA COMMUNICATION DEVICES INC. ENGENIUS IBM ADC TELECOMMUNICATIONS AVOCENT‐EMERSON COMNET ENTERASYS NETWORKS IMC NETWORKS ADDERTECHNOLOGY AXIOM MEMORY COMPREHENSIVE CABLE EQUINOX SYSTEMS IMS‐DELL ADDON NETWORKS AXIS COMMUNICATIONS COMPU‐CALL, INC ETHERWAN INFOCUS ADDON STORE AZIO CORPORATION COMPUTER EXCHANGE LTD EVGA.COM INGRAM BOOKS ADESSO B & B ELECTRONICS COMPUTERLINKS EXABLAZE INGRAM MICRO ADTRAN B&H PHOTO‐VIDEO COMTROL EXACQ TECHNOLOGIES INC INNOVATIVE ELECTRONIC DESIGNS ADVANTECH AUTOMATION CORP. BASF CONNECTGEAR EXTREME NETWORKS INOGENI ADVANTECH CO LTD BELDEN CONNECTPRO EXTRON INSIGHT AEROHIVE NETWORKS BELKIN COMPONENTS COOLGEAR F5 NETWORKS INSIGNIA ALCATEL BEMATECH CP TECHNOLOGIES FIRESCOPE INTEL ALCATEL LUCENT BENFEI CRADLEPOINT, INC. FORCE10 NETWORKS, INC INTELIX -

The Case of Interaction Problems Between Password Managers and Websites
They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites Nicolas HuamanC ∗ Sabrina Amft∗ Marten OltroggeC Yasemin Acary ∗ Sascha FahlC ∗ CCISPA Helmholtz Center for Information Security ∗Leibniz University Hannover yMax Planck Institute for Security and Privacy Abstract—Password managers are tools to support users with previous research on PWMs mostly focuses on PWM security the secure generation and storage of credentials and logins issues and usability and adoption challenges. Multiple studies used in online accounts. Previous work illustrated that building researched the security of different PWM types, finding that password managers means facing various security and usability challenges. For strong security and good usability, the interaction both browser-based and locally installed PWMs are vulner- between password managers and websites needs to be smooth and able to problems such as key theft or secret recovery from effortless. However, user reviews for popular password managers temporary files, as well as weaknesses within typical features suggest interaction problems for some websites. Therefore, to the such as autofill [64]. Other research focused on the usability best of our knowledge, this work is the first to systematically iden- of PWMs and were able to show that user adoption of PWMs tify these interaction problems and investigate how 15 desktop password managers, including the ten most popular ones, are is motivated by convenience of usage and usability [59]. affected. We use a qualitative analysis approach to identify 39 While security benefits can also be a driving factor for PWM interaction problems from 2,947 user reviews and 372 GitHub adoption, in the majority of cases these where only mentioned issues for 30 password managers.