Characters, Tokens, Statements, and Steps: What the SAS¨ Supervisor Sees in Your Program Rick Aster, Valley Forge, PA
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jupyter Reference Guide
– 1 – Nicholas Bowman, Sonja Johnson-Yu, Kylie Jue Handout #15 CS 106AP August 5, 2019 Jupyter Reference Guide This handout goes over the basics of Jupyter notebooks, including how to install Jupyter, launch a notebook, and run its cells. Jupyter notebooks are a common tool used across different disciplines for exploring and displaying data, and they also make great interactive explanatory tools. Installing Jupyter To install Jupyter, run the following command inside your Terminal (replace python3 with py if you’re using a Windows device): $ python3 -m pip install jupyter Launching a notebook A Jupyter notebook is a file that ends in the extension .ipynb, which stands for “interactive Python notebook.” To launch a Python notebook after you’ve installed Jupyter, you should first navigate to the directory where your notebook is located (you’ll be there by default if you’re using the PyCharm terminal inside a project). Then run the following command inside your Terminal (if this doesn’t work, see the “Troubleshooting” section below): $ jupyter notebook This should open a window in your browser (Chrome, Firefox, Safari, Edge, etc.) that looks like Figure 1. Jupyter shows the files inside the current directory and allows you to click on any Python notebook files within that folder. Figure 1: After running the jupyter notebook command, you should see a window that lists the Python notebooks inside the current directory from which you ran the command. The picture above shows the Lecture 25 directory. – 2 – To launch a particular notebook, click on its file name. This should open a new tab with the notebook. -

AMPERSAND an International Journal of General and Applied Linguistics
AMPERSAND An International Journal of General and Applied Linguistics AUTHOR INFORMATION PACK TABLE OF CONTENTS XXX . • Description p.1 • Abstracting and Indexing p.2 • Editorial Board p.2 • Guide for Authors p.4 ISSN: 2215-0390 DESCRIPTION . Serving the breadth of the general and applied linguistics communities, Ampersand offers a highly- visible, open-access home for authors. An international, peer-reviewed journal, Ampersand welcomes submissions in applied and historical linguistics, phonetics, phonology, pragmatics, semantics, sociolinguistics and syntax. Ampersand provides authors with an open-access venue to disseminate a wide range of linguistic research in an equally wide range of formats, prioritizing rapid peer review and publication so that researchers can share their work in its most current and innovative form. In response to the global thrust toward open source, open data and open access in science, Ampersand offers the opportunity for authors to make their research freely available to everyone, opening their work to a wider audience and increased readership. Ampersand caters to a comprehensive audience, ranging from language researchers, linguists, teachers, educationalists, practitioners to those with a general interest in language and linguistics. The journal aims to encourage the free exchange of information between researchers by being a forum for the constructive discussion and debate of issues in both theoretical and applied research. The journal welcomes all types of submission format: traditional 'full' research articles, short communications, opinion pieces, book reviews, case studies and literature reviews. Ampersand also offers the opportunity to publish special issues or sections to reflect current interest and research in topical or developing areas. The journal fully supports authors wanting to present their research in an innovative fashion through the use of modern multimedia in the award-winning 'article of the future' format on ScienceDirect?. -
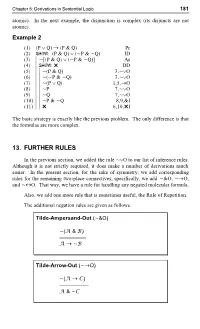
Tilde-Arrow-Out (~→O)
Chapter 5: Derivations in Sentential Logic 181 atomic). In the next example, the disjunction is complex (its disjuncts are not atomic). Example 2 (1) (P ´ Q) → (P & Q) Pr (2) •: (P & Q) ∨ (~P & ~Q) ID (3) |~[(P & Q) ∨ (~P & ~Q)] As (4) |•: ¸ DD (5) ||~(P & Q) 3,~∨O (6) ||~(~P & ~Q) 3,~∨O (7) ||~(P ∨ Q) 1,5,→O (8) ||~P 7,~∨O (9) ||~Q 7,~∨O (10) ||~P & ~Q 8,9,&I (11) ||¸ 6,10,¸I The basic strategy is exactly like the previous problem. The only difference is that the formulas are more complex. 13. FURTHER RULES In the previous section, we added the rule ~∨O to our list of inference rules. Although it is not strictly required, it does make a number of derivations much easier. In the present section, for the sake of symmetry, we add corresponding rules for the remaining two-place connectives; specifically, we add ~&O, ~→O, and ~↔O. That way, we have a rule for handling any negated molecular formula. Also, we add one more rule that is sometimes useful, the Rule of Repetition. The additional negation rules are given as follows. Tilde-Ampersand-Out (~&O) ~(d & e) ––––––––– d → ~e Tilde-Arrow-Out (~→O) ~(d → f) –––––––––– d & ~f 182 Hardegree, Symbolic Logic Tilde-Double-Arrow-Out (~±O) ~(d ± e) –––––––––– ~d ± e The reader is urged to verify that these are all valid argument forms of sentential logic. There are other valid forms that could serve equally well as the rules in question. The choice is to a certain arbitrary. The advantage of the particular choice becomes more apparent in a later chapter on predicate logic. -

How the Past Affects the Future: the Story of the Apostrophe1
HOW THE PAST AFFECTS THE FUTURE: THE STORY OF THE APOSTROPHE1 Christina Cavella and Robin A. Kernodle I. Introduction The apostrophe, a punctuation mark which “floats above the line, symbolizing something missing in the text” (Battistella, 1999, p. 109), has been called “an unstable feature of written English” (Gasque, 1997, p. 203), “the step-child of English orthography” (Barfoot, 1991, p. 121), and “an entirely insecure orthographic squiggle” (Barfoot, 1991, p. 133). Surely the apostrophe intends no harm; why then the controversy and apparent emotionalism surrounding it? One major motivation for investigating the apostrophe is simply because it is so often misused. A portion of the usage problem can perhaps be attributed to the chasm dividing spoken and written language, as the apostrophe was originally intended to indicate missing letters, which may or may not have actually been enunciated. To understand what has been called “the aberrant apostrophe,” (Crystal, 1995, p. 203) and the uncertainty surrounding its usage, an examination of its history is essential, for it is this “long and confused” (Crystal, 1995, p. 203) history that is partially responsible for the modern-day misuses of the apostrophe. This paper will trace the history of the apostrophe, examining the purpose(s) for which the apostrophe has been utilized in the past as well as presenting its current use. An overview of contemporary rules of usage is then included, along with specific examples of apostrophe misuse and a recommendation on how to teach apostrophe usage to non- native speakers of English. Finally, an attempt is made to predict the apostrophe’s future. -

Introducing Sentential Logic (SL) Part I – Syntax
Introducing Sentential Logic (SL) Part I – Syntax 1. As Aristotle noted long ago, some entailments in natural language seem to hold by dint of their “logical” form. Consider, for instance, the example of Aristotle’s being a logician above, as opposed to the “material” entailment considering the relative locations of Las Vegas and Pittsburgh. Such logical entailment provides the basic motivation for formal logic. So-called “formal” or “symbolic” logic is meant in part to provide a (perhaps idealized) model of this phenomenon. In formal logic, we develop an artificial but highly regimented language, with an eye perhaps of understanding natural language devices as approximating various operations within that formal language. 2. We’ll begin with a formal language that is commonly called either Sentential Logic (SL) or, more high- falutinly, “the propositional calculus.” You’re probably already quite familiar with it from an earlier logic course. SL is composed of Roman capital letters (and subscripted capital letters), various operators (or functors), and left and right parentheses. The standard operators for SL include the tilde (~), the ampersand (&), the wedge (v), and the arrow (→). Other operators, such as the double arrow, the stroke and the dagger, can easily be added as the need arises. The Syntax of S.L 3. A syntax for a language specifies how to construct meaningful expressions within that language. For purely formal languages such as SL, we can understand such expressions as well-formed formulas (wffs). The syntax of SL is recursive. That means that we start with basic (or atomic) wffs, and then specify how to build up more complex wffs from them. -

Trademarks 10 Things You Should Know to Protect Your Product and Business Names
Trademarks 10 things you should know to protect your product and business names 1. What is a trademark? A trademark is a brand name for a product. It can be a word, phrase, logo, design, or virtually anything that is used to identify the source of the product and distinguish it from competitors’ products. More than one trademark may be used in connection with a product; for example, COCA-COLA® and DIET COKE® are both trademarks for beverages. A trademark represents the goodwill and reputation of a product and its source. Its owner has the right to prevent others from trading on that goodwill by using the same or a similar trademark on the same or similar products in a way that is likely to cause confusion as to the source, origin, or sponsorship of the products. A service mark is like a trademark, except it is used to identify and distinguish services rather than products. For example, the “golden arches” mark shown below is a service mark for restaurant services. The terms “trademark” and “mark” are often used interchangeably to refer to either a trademark or service mark. 2. How should a mark be used? Trademarks must be used properly to maintain their value. Marks should be used as adjectives, but not as nouns or verbs. 4 | knobbe.com For example, when referring to utilizing the FACEBOOK® website, do not say that you “Facebooked” or that you were “Facebooking.” To prevent loss of trademark or service mark rights, the generic name for the product should appear after the mark, and the mark should appear visually different from the surrounding text. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -
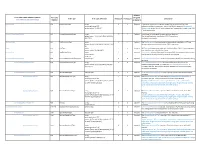
Form 1094-C Schema to Form Crosswalk
Element Form 1094-C XML Schema Elements Form Line Required eFile Type eFile Type Definition minOccurs maxOccurs Description Form1094CUpstreamDetailType Number or Optional SubmissionId N/A SubmissionIdType string 1 1 Required A sequential number (non-negative integer) that uniquely identifies each maxLength value="10" submission within a transmission - every Form 1094-C requires a SubmissionId. pattern value="[1-9][0-9]*" SubmissionId should start at 1 and increment by 1 sequentially for each Form 1094- C in the transmission. OriginalUniqueSubmissionId N/A UniqueSubmissionIdType string 0 1 Optional Global type for the Original Unique Submission Identifier. pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- The UniqueSubmission Identifier for 1094-C is as follows: 9]{0,15}"/> ReceiptId|SubmissionId TestScenarioId N/A TestScenarioIdType string 0 1 Optional The TestScenarioId is only applicable to transmissions submitted to AATS and pattern ([1-9]|[1-9][0-9])C{0,1}-([0-9]|[1-9][0- identifies which test scenario the Form 1094-C represents. 9]) TaxYr N/A YearType string 1 1 Required IRS TaxYr is the tax year for which the data on the Form 1094-C is being submitted. pattern value="[1-9][0-9]{3}"/ Base type for a year in the format of YYYY. CorrectedInd N/A DigitBooleanType string 1 1 Required CorrectedInd indicates if the record is an original (0) or a correction (1) to a record enumerations: that the IRS has already received, processed, and accepted. "0" or" 1" CorrectedSubmissionInfoGrp N/A CorrectedSubmissionInfoGrpType complexType 0 1 Optional CorrectedSubmissionInfoGrp contains Information to identify the submission being corrected. CorrectedUniqueSubmissionId N/A UniqueSubmissionIdType string 1 1 Required CorrectedUniqueSubmissionId is the unique submission identifier of the pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- submission being corrected. -

Beginner's Guide to Asterisk
Getting Started With Open Source Telephony A Beginners Guide to Asterisk Steve Sokol Asterisk Marketing Lead, Digium Justin Hester Lead Asterisk Technical Instructor, Digium Agenda • Summary of Asterisk • Basics and Distributions • Resources • Asterisk is a toolkit • Distros are more complete • Training classes package with GUI • Digium and Asterisk • Getting started using Asterisk • AstriCon 2016 • Architecture - Linux + Asterisk • Difference between CLI and GUI • Versioning Getting Started with Asterisk Getting Started with Asterisk • Find it • Install it • Configure it What is Asterisk? An Open Source Communications Platform • Software, written in C, that you put on an ordinary operating system—transforming that system into a communications engine. Software – A communications platform A system through which communications flow, from one endpoint to another. What is Asterisk - Platform Open Source Communications Platform Software - Extensible Architecture A simple core with only a few responsibilities Module Management Reading Configuration CORE System Timing CORE Channel Management Software – Modular Architecture Modules app_dial.so • Use the native modules • Use Asterisk’s APIs to control and extend Asterisk – AMI, AGI, and ARI Preparing for Asterisk – Set up a host machine • Old physical hardware – Laptop, rackmount or tower system • Virtual machine – e.g. VirtualBox (on your Mac, Windows or Linux laptop!) www.virtualbox.org • Cloud server – e.g. www.digitalocean.com or aws.amazon.com Finding Asterisk – Choose your path ‘Source’ or ‘Plain Vanilla’ AsteriskNOW, a PBX ‘distro’. www.asterisk.org/downloads Choosing Asterisk - Source • Install a Linux operating system • Set up networking • Configure software repositories • Install Asterisk dependencies • Download and install Asterisk, DAHDI, LibPRI from provided scripts. And you will have an unconfigured, pristine, ready to configure “Asterisk Configuration Framework”. -

Appraisal Institute Trademark Usage Manual
Trademark Usage Manual for Appraisal Institute Copyright © 2020 Appraisal Institute. All rights reserved. Printed in the United States of America. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopy, recording or otherwise, without the prior written consent of the publisher. TRADEMARK USAGE MANUAL FOR APPRAISAL INSTITUTE Table of Contents I. Introduction 1 II. Trademarks, Service Marks, Collective Service Marks and Collective Membership Marks 1 III. Trade Names are Different from Trademarks 2 IV. Proper Trademark Usage 3 A. Always Use Trademarks as Proper Adjectives ............................................................................... 3 B. Make the Trademark Stand Out .................................................................................................... 3 C. Only One Trademark Should Appear on the Same Label or Name Plate ....................................... 4 D. Use of Appraisal Institute Trademarks ........................................................................................... 4 1. Signature Requirements and Restrictions ................................................................................ 4 2. Membership Designation Requirements and Restrictions ........................................................ 5 3. Proper Use of Letter Designations ........................................................................................... 5 4. Emblem Requirements and Restrictions ................................................................................. -
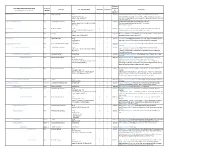
Form 1094-C Form to Schema Crosswalk
Element Form 1094-C XML Schema Elements Form Line Required eFile Type eFile Type Definition minOccurs maxOccurs Description Form1094CUpstreamDetailType Number or Optional* SubmissionId N/A SubmissionIdType string 1 1 Required A sequential number (non-negative integer) that uniquely identifies each maxLength value="10" submission within a transmission - every Form 1094-C requires a SubmissionId. pattern value="[1-9][0-9]*" SubmissionId should start at 1 and increment by 1 sequentially for each Form 1094- C in the transmission. OriginalUniqueSubmissionId N/A UniqueSubmissionIdType string 0 1 Optional Global type for the Original Unique Submission Identifier. pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- The UniqueSubmission Identifier for 1094-C is as follows: 9]{0,15}"/> ReceiptId|SubmissionId TestScenarioId N/A TestScenarioIdType string 0 1 Optional The TestScenarioId is only applicable to transmissions submitted to AATS and pattern ([1-9]|[1-9][0-9])C{0,1}-([0-9]|[1- identifies which test scenario the Form 1094-C represents. 9][0-9]) TaxYr N/A YearType string 1 1 Required IRS TaxYr is the tax year for which the data on the Form 1094-C is being submitted. pattern value="[1-9][0-9]{3}"/ Base type for a year in the format of YYYY. CorrectedInd N/A DigitBooleanType string 1 1 Required CorrectedInd indicates if the submission is an original (0) or a correction (1) to a enumerations: submission that the IRS has already received, processed, and accepted. "0" or" 1" CorrectedSubmissionInfoGrp N/A CorrectedSubmissionInfoGrpType complexType 0 1 Optional CorrectedSubmissionInfoGrp contains Information to identify the submission being corrected. CorrectedUniqueSubmissionId N/A UniqueSubmissionIdType string 1 1 Required CorrectedUniqueSubmissionId is the unique submission identifier of the pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- submission being corrected. -
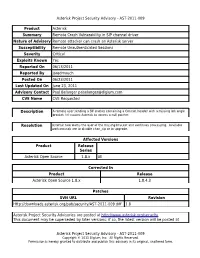
AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP Channel Driver Natu
Asterisk Project Security Advisory - AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP channel driver Nature of Advisory Remote attacker can crash an Asterisk server Susceptibility Remote Unauthenticated Sessions Severity Critical Exploits Known Yes Reported On 06/13/2011 Reported By jaredmauch Posted On 06/23/2011 Last Updated On June 23, 2011 Advisory Contact Paul Belanger [email protected] CVE Name CVE Requested Description A remote user sending a SIP packet containing a Contact header with a missing left angle bracket (<) causes Asterisk to access a null pointer. Resolution Asterisk now warns the user of the missing bracket and continues processing. Available workarounds are to disable chan_sip or to upgrade. Affected Versions Product Release Series Asterisk Open Source 1.8.x All Corrected In Product Release Asterisk Open Source 1.8.x 1.8.4.3 Patches SVN URL Revision Http://downloads.asterisk.org/pub/security/AST-2011-009.diff 1.8 Asterisk Project Security Advisories are posted at http://www.asterisk.org/security This document may be superseded by later versions; if so, the latest version will be posted at Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. All Rights Reserved. Permission is hereby granted to distribute and publish this advisory in its original, unaltered form. Asterisk Project Security Advisory - AST-2011-009 http://downloads.digium.com/pub/security/AST-2011-009.pdf and http://downloads.digium.com/pub/security/AST-2011-009.html Revision History Date Editor Revisions Made 06/20/2011 Kinsey Moore Initial Release Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc.