Security Now! #668 - 06-19-18 Lazy FPU State Restore
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shared Source Licensing Program for the Windows Embedded Compact (Formerly Windows CE) Platform
9/6/2020 Shared Source Initiative | Licensing Program for the Windows Embedded Compact Platform Search Microsoft.com PRODUCTS STORE DOWNLOADS SUPPORT United States Shared Source Initiative > Windows Embedded Compact Source Licensing Program Shared Source Licensing Program for the Windows® Embedded Compact (formerly Windows CE) Platform Shared Source Licensing Programs Overview Microsoft offers a Shared Source licensing program for the Windows Embedded Compact (formerly Windows CE) platform. This program is applicable to the Windows Embedded Compact and Windows Embedded CE products. The Windows Embedded Shared Source program helps OEMs and developers speed development, reduce troubleshooting and code debugging time, receive assistance in remote device support and gain a deeper technical understanding of Windows Embedded Compact software. Public/Sample Source code is built at no additional cost into the purchased copies of the Windows Embedded Compact Platform Builder toolkit and provides access to nearly 4 million lines of code. Depending on a partner’s needs and qualifications, deeper levels of Shared Source code access (Private and Premium) are available. How to Participate Public/Sample Shared Source Public/Sample Shared Source code is available at no additional cost with each purchased copy of the Windows Embedded Compact 7 Platform Builder toolkit. Private Shared Source Private Shared Source Code is an optional component of the Windows Embedded Compact 7 Platform Builder toolkit that can be installed during the setup process. The toolkit user must electronically accept the terms and conditions of the Shared Source licensing agreement (EULA) before the Private source code can be installed. Premium Derivatives Program Microsoft also offers Premium access to advanced Windows Embedded Compact 7 source code through the Premium Derivatives licensing program. -

Open Source Mit Vorsicht Zu Geniessen
Achim Patzner, Dr. Walter Speth, active BIT1, Bonn Open Source mit Vorsicht zu geniessen Seit Richard Stallman in den 80ern die Free Software Foundation ins Leben gerufen hat, geistert der Begriff der freien Software durch die Branche und wird allzu oft voreilig als lizenzfrei und/oder kostenfrei missverstanden. Das Gegenteil kann der Fall sein: Die Wahl für eine Open Source Plattform kann Herstellern ein Lizenzmodell aufoktroyieren, das mit den Unternehmenszielen nicht vereinbar ist. Zeit für eine Richtigstellung: Nach der "public domain software" und der bereits genannten "free software" kam im Siegeszug von Linux und mit der Veröffentlichung der Quellen des Netscape-Browsers im Mozilla-Projekt Anfang 1998 die "open source software" und mittlerweile aus dem Hause Microsoft auch noch den Begriff der "shared software" (man hat verstanden, dass derartige Campagnen durchaus Marketing-Charakter tragen). Die Free Software Foundation distanziert sich übrigens vom Begriff "open source Software"2. Allerdings steht gerade dieser Begriff für das kollektive Erstellen von Software-Projekten, aber weniger wegen eines speziellen philosophischen Ansatzes, sondern weil er zu einer Zeit geprägt wurde, in der die hohe Durchdringung der weltweiten Vernetzung die Kommunikation innerhalb der Entwicklergemeinschaft ermöglichte und weil Linux als augenscheinlicher Vertreter für Open-Source-Produkte den Kondensationskern für das Bewusstsein von kostenfreier Software darstellte. Richard Stallman wollte "Freiheit für Software", er wollte aber nicht Software im Sinne von Freibier (so seine eigene Formulierung). Die Freiheit besteht im wesentlichen darin, dass der Hersteller sein geistiges Erzeugnis, die Sourcen verfügbar macht. Deren Nutzung ist allerdings durchaus im rechtlichen Rahmen der mitgelieferten Lizenzvereinbarung zu sehen. Es geht also weder darum, Software - 2 - ohne lizenzrechtliche Einschränkungen nutzen zu können, noch geht es darum, die Anwender mit lizenzfreier Software zu versorgen. -

Microsoft's Shared Source Initiative As an Alternative to Open
How open is open? Microsoft’s Shared Source Initiative as an Alternative to Open Source Software Anne-Kathrin Kuehnel Department of Law and Criminology, University of Wales Aberystwyth Email: [email protected] Introduction: “Judging a Book by its Cover” There are few certainties in life: everybody is playing football but, in the end, Germany wins. The murderer is always the butler. Or the gardener. It never rains in “Midsomer Murders”. Until recently, one of these used to be “Open Source good, Microsoft bad.” But now, it would appear that times have, indeed, changed and nothing in the software industry is as perceived and traditional wisdom would have it: Microsoft is opening up some of its source code. Over the past few years, Microsoft has promoted a project called “Shared Source Initiative” which allows access to source code to certain customers (e.g. research institutions and independent software vendors) on a restricted basis. Furthermore, it has also introduced some licenses which appear to give unrestricted access to source code and seem to closely resemble ‘traditional’ Open Source licenses. Given that availability of source code is a prime characteristic of Open Source Software it could be argued that Microsoft has embraced the Open Source Software philosophy. And indeed, one of Microsoft’s sharpest critics, Lawrence Lessig, is openly praising Microsoft for its Shared Source Initiative for opening up some of their source code.1 Rumour also has it that Microsoft has at least been thinking about submitting some of their licenses to the Open Source Initiative for certification.2 Does this mean that Microsoft has (finally) seen the light and embraced the Open Source philosophy? If Open Source Software was only defined by the accessibility of source code, the availability of source code would equal open source. -
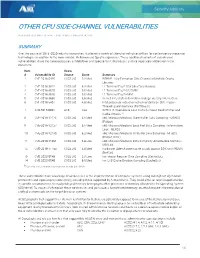
Other Cpu Side-Channel Vulnerabilities
Security Advisory OTHER CPU SIDE-CHANNEL VULNERABILITIES PUBLISHED: DECEMBER 14, 2018 | LAST UPDATE: FEBRUARY 18, 2020 SUMMARY Over the course of 2018 -2020 industry researchers disclosed a variety of side-channel vulnerabilities for contemporary processor technologies in addition to the more notable Meltdown and Spectre exposures. These additional variants of side-channel vulnerabilities share the same exposures as Meltdown and Spectre for A10 products and are separately addressed in this document. Item Score # Vulnerability ID Source Score Summary 1 CVE-2018-0495 CVSS 3.0 5.1 Med ROHNP - Key Extraction Side Channel in Multiple Crypto Libraries 2 CVE-2018-3615 CVSS 3.0 6.3 Med L1 Terminal Fault-SGX (aka Foreshadow) 3 CVE-2018-3620 CVSS 3.0 5.6 Med L1 Terminal Fault-OS/SMM 4 CVE-2018-3646 CVSS 3.0 5.6 Med L1 Terminal Fault-VMM 5 CVE-2018-3665 CVSS 3.0 5.6 Med Kernel: FPU state information leakage via lazy FPU restore 6 CVE-2018-5407 CVSS 3.0 4.8 Med Intel processor side-channel vulnerability on SMT/Hyper- Threading architectures (PortSmash) 7 A10-2019-0001 A10 Low SPOILER: Speculative Load Hazards Boost Rowhammer and Cache Attacks (i) 8 CVE-2018-12126 CVSS 3.0 6.5 Med x86: Microarchitectural Store Buffer Data Sampling - MSBDS (Fallout) 9 CVE-2018-12127 CVSS 3.0 6.5 Med x86: Microarchitectural Load Port Data Sampling - Information Leak - MLPDS 10 CVE-2018-12130 CVSS 3.0 6.2 Med x86: Microarchitectural Fill Buffer Data Sampling - MFBDS (Fallout, RIDL) 11 CVE-2019-11091 CVSS 3.0 3.8 Low x86: Microarchitectural Data Sampling Uncacheable Memory - MDSUM 12 CVE-2019-11184 CVSS 3.0 4.8 Med hardware: Side-channel cache attack against DDIO with RDMA (NetCat) 13 CVE-2020-0548 CVSS 3.0 2.3 Low hw: Vector Register Data Sampling (CacheOut) 14 CVE-2020-0549 CVSS 3.0 6.5 Med hw: L1D Cache Eviction Sampling (CacheOut) (i) Can only affect vThunder deployments on Intel Core CPUs. -

Enabling Dynamic Analysis of Legacy Embedded Systems in Full Emulated Environment Ta-Lun Yen Txone Iot/ICS Security Research Labs (Trend Micro) $(Whoami)
Enabling dynamic analysis of Legacy Embedded Systems in full emulated environment Ta-Lun Yen TXOne IoT/ICS Security Research Labs (Trend Micro) $(whoami) ● @evanslify ● Researcher @ TXOne Networks (Trend Micro), 2019/11-present ● Reverse Engineering, protocol analysis, wireless, hardware 2 2021-07-12 Outline ● Our goals & Background of Windows CE6 ● CE6 Bootloader & power-on initialization ● Inside CE6 Application Loader & Memory management ● Reconstructing extracted binaries to dynamic execution ● Conclusion 3 2021-07-12 Our goal ● Emulate CE6 image from device with QEMU ● We don’t want to buy every hardware for research – We ended up buying one actually (for comparison) ● Serial ports & debugger is not present on every hardware 4 2021-07-12 Background of Windows CE6 5 2021-07-12 Horrors from the ancient ● WinCE hasn’t been actively exploited (yet…) ● However, it runs everywhere – In cars, Parking meters, aircraft IFEs, subway turnstiles, medical devices, power plants... 6 2021-07-12 Difference between {NT, CE} ● Microsoft Shared Source Initiative: (partial) source code ● Loosely adheres to NT APIs and behavior ● Real-time OS 7 2021-07-12 Difference between {NT, CE} ● While having different APIs and behaviors between CE and NT... ● Some exploits and techniques might work on both CE & NT – ...with some efforts, e.g MS17-010 [1] [1] https://www.fracturelabs.com/posts/2017/exploiting-ms17-010-on-windows-embedded-7- devices/ 8 2021-07-12 Current methods to study CE6 firmware ● File extraction – https://github.com/nlitsme/eimgfs (was dumprom) -

Incorporating the Commons: a Political Economic Analysis
INCORPORATING THE COMMONS: A POLITICAL ECONOMIC ANALYSIS OF CORPORATE INVOLVEMENT IN FREE AND OPEN SOURCE SOFTWARE by BENJAMIN J. BIRKINBINE A DISSERTATION Presented to the School of Journalism and Communication and the Graduate School of the University of Oregon in partial fulfillment of the requirements for the degree of Doctor of Philosophy September 2014 DISSERTATION APPROVAL PAGE Student: Benjamin J. Birkinbine Title: Incorporating the Commons: A Political Economic Analysis of Corporate Involvement in Free and Open Source Software This dissertation has been accepted and approved in partial fulfillment of the requirements for the Doctor of Philosophy degree in the School of Journalism and Communication by: Dr. Janet Wasko Chairperson Dr. Biswarup Sen Core Member Dr. Gabriela Martinez Core Member Eric Priest, J.D. Institutional Representative and J. Andrew Berglund Dean of the Graduate School Original approval signatures are on file with the University of Oregon Graduate School. Degree awarded September 2014 ii DISSERTATION ABSTRACT Benjamin J. Birkinbine Doctor of Philosophy School of Journalism and Communication September 2014 Title: Incorporating the Commons: A Political Economic Analysis of Corporate Involvement in Free and Open Source Software Free (libre) and open source software (FLOSS) emerged in the 1980s as a radical alternative to proprietary software. Fighting back against what FLOSS enthusiasts viewed as overly restrictive intellectual property protections placed on proprietary software, FLOSS was designed with the intent of granting users the right to study, modify, adapt, or otherwise tinker with the source code of software. As such, FLOSS users were able to collaborate in producing software that could be distributed freely and widely to others, who could, in turn, make changes to the software. -

Table of Contents
Table of Contents Preface . ix 1. Open Source Licensing, Contract, and Copyright Law . 1 Basic Principles of Copyright Law 1 Contract and Copyright 3 Open Source Software Licensing 4 Issues with Copyrights and Patents 7 The Open Source Definition 8 Warranties 11 2. The MIT, BSD, Apache, and Academic Free Licenses . 14 The MIT (or X) License 14 The BSD License 15 The Apache License, v1.1 and v2.0 17 The Academic Free License 24 Application and Philosophy 30 3. The GPL, LGPL, and Mozilla Licenses . 34 GNU General Public License 35 GNU Lesser General Public License 49 The Mozilla Public License 1.1 (MPL 1.1) 62 Application and Philosophy 81 4. Qt, Artistic, and Creative Commons Licenses . 85 The Q Public License 85 Artistic License (Perl) 90 Creative Commons Licenses 98 vii 5. Non-Open Source Licenses . 114 Classic Proprietary License 114 Sun Community Source License 120 Microsoft Shared Source Initiative 144 6. Legal Impacts of Open Source and Free Software Licensing . 147 Entering Contracts 148 Statutory Developments Related to Software Contracts 150 The Self-Enforcing Nature of Open Source and Free Software Licenses 151 The Global Scope of Open Source and Free Software Licensing 153 The “Negative Effects” of Open Source and Free Software Licensing 154 Community Enforcement of Open Source and Free Software Licenses 158 Compatible and Incompatible Licensing: Multiple and Cross Licensing 159 7. Software Development Using Open Source and Free Software Licenses . 164 Models of Open Source and Free Software Development 164 Forking 171 Choosing an Open Source or Free Software License 174 Drafting Open Source Licenses 176 Appendix: Creative Commons Attribution-NoDerivs License . -

Open Source Software: Risks and Rewards V2.0, 03 August 2005
Open Source Software: Risks and Rewards v2.0, 03 August 2005 Author(s)Gary Hein Conclusion Open source software (OSS) brings new opportunities and risks to information technology (IT) vendors and customers. Software commoditization is being profoundly affected from the infrastructure layer and moving up to the application layer. As a result, OSS is changing the strategies and business models of hardware and software vendors and system integrators. Customers should understand the risks and rewards of OSS, and should formulate strategies that bring OSS benefits to their IT departments while mitigating the business and legal risks. Synopsis Open source software (OSS) is more than just free software. It’s a development process, a distribution model, and a set of new software licenses. And, as characterized by OSS proponents, it’s a movement. OSS projects, such as Linux and Apache HTTP server, are commoditizing enterprise and Internet infrastructure, and thus pose threats for some vendors while creating new market opportunities for others. OSS brings more to information technology (IT) than just free software. It grants freedom from vendor lock-in and application churn, freedom to inspect, modify, and improve source code, and the freedom to influence or contribute to projects key to a company’s survival. But these freedoms come at a price. Although OSS is free, it isn’t always less expensive to implement due to migration, support, training, and maintenance costs. OSS projects add new twists to business risks such as vendor viability and stability, and legal issues remain uncertain as many popular licenses have yet to be tested in a court of law. -

The Paradox of Source Code Secrecy
KATYAL FORMATTED 6/24/19 11:31 PM THE PARADOX OF SOURCE CODE SECRECY Sonia K. Katyal† INTRODUCTION ............................................................ 102 I. SOURCE CODE SECRECY AND COPYRIGHT ............... 109 A. Code: An Introductory (and Incomplete) History .................................................................. 111 B. The Birth of Source Code Secrecy ................ 114 C. The Copyrightability of Software .................. 117 1. Early Accommodations of Trade Secrecy ... 119 2. Copyrighting Code................................... 122 D. The Continuing Overlap Between Copyright and Trade Secrecy ............................................. 125 II. THE SHIFTING BOUNDARIES OF SOFTWARE PATENTABILITY ................................................... 129 A. Patentability vs. Secrecy .............................. 131 B. The Rise and Fall of Software Patentability ... 136 1. The Opening of the Window of Patentability .............................................................. 137 2. Narrowing the Window of Patentability ..... 141 III. TRADE SECRECY AS DESTINATION .......................... 145 A. The Lingering Monopoly of Trade Secrecy ..... 146 B. Judicial Accommodation in Kewanee ........... 149 C. Rethinking Complementarity in Software ..... 151 † Haas Distinguished Chair and Chancellor’s Professor of Law, University of California at Berkeley. Many, many thanks to the following for comments and conversation: Ken Bamberger, Ash Bhagwat, Andrew Bradt, Ari Chivikula, Ryan Calo, Christian Chessman, Danielle Citron, -

Incorporating the Digital Commons:Corporate Involvement in Free and Open Source Software
INCORPORATING THE DIGITAL COMMONS DIGITAL THE INCORPORATING INCORPORATING THE CDSMS DIGITAL COMMONS he concept of ‘the commons’ has been used as a framework to understand resources shared by a community rather than a private BENJAMIN J. BIRKINBINE T entity, and it has also inspired social movements working against the enclosure of public goods and resources. One such resource is free (libre) and open source software (FLOSS). FLOSS emerged as an alternative to proprietary software in the 1980s. However, both the products and production processes of FLOSS have become incorporated into capitalist INCORPORATING THE production. For example, Red Hat, Inc. is a large publicly traded company whose business model relies entirely on free software, and IBM, Intel, Cisco, Samsung, Google are some of the largest contributors to Linux, the DIGITAL COMMONS open-source operating system. This book explores the ways in which FLOSS has been incorporated into digital capitalism. Just as the commons have been used as a motivational frame for radical social movements, it has also Corporate Involvement in Free served the interests of free-marketeers, corporate libertarians, and states to expand their reach by dragging the shared resources of social life onto and Open Source Software digital platforms so they can be integrated into the global capitalist system. The book concludes by asserting the need for a critical political economic understanding of the commons that foregrounds (digital) labour, class struggle, and uneven power distribution within the digital commons as well as between FLOSS communities and their corporate sponsors. BENJAMIN J. BIRKINBINE J. BENJAMIN COMMUNICATION STUDIES | POLITICAL ECONOMY | MEDIA INDUSTRIES CDSMS CRITICAL DIGITAL AND SOCIAL MEDIA STUDIES THE AUTHOR Benjamin J. -

Commercializing Open Source Software: Do Property Rights Still Matter?
Columbia Law School Scholarship Archive Faculty Scholarship Faculty Publications 2006 Commercializing Open Source Software: Do Property Rights Still Matter? Ronald J. Mann Columbia Law School, [email protected] Follow this and additional works at: https://scholarship.law.columbia.edu/faculty_scholarship Part of the Computer Law Commons, and the Intellectual Property Law Commons Recommended Citation Ronald J. Mann, Commercializing Open Source Software: Do Property Rights Still Matter?, 20 HARV. J. L. & TECH. 1 (2006). Available at: https://scholarship.law.columbia.edu/faculty_scholarship/739 This Article is brought to you for free and open access by the Faculty Publications at Scholarship Archive. It has been accepted for inclusion in Faculty Scholarship by an authorized administrator of Scholarship Archive. For more information, please contact [email protected]. HarvardJournal of Law & Technology Volume 20, Number 1 Fall 2006 COMMERCIALIZING OPEN SOURCE SOFTWARE: Do PROPERTY RIGHTS STILL MATTER? Ronald J Mann* TABLE OF CONTENTS I. IN TRO DU CTIO N .................................................................................. 1 11. THE LANDSCAPE .......................................................................... 5 A. The ProprietarySoftware Model .............................................. 5 1. Formation and Maturation of the Proprietary Software Industry ......................................................................... 5 2. Software Licensing Under Proprietary Models .................... 8 3. -

Invisispec: Making Speculative Execution Invisible in the Cache Hierarchy
InvisiSpec: Making Speculative Execution Invisible in the Cache Hierarchy Mengjia Yany, Jiho Choiy, Dimitrios Skarlatos, Adam Morrison∗, Christopher W. Fletcher, and Josep Torrellas University of Illinois at Urbana-Champaign ∗Tel Aviv University fmyan8, jchoi42, [email protected], [email protected], fcwfletch, [email protected] yAuthors contributed equally to this work. Abstract— Hardware speculation offers a major surface for the attacker’s choosing. Different types of attacks are possible, micro-architectural covert and side channel attacks. Unfortu- such as the victim code reading arbitrary memory locations nately, defending against speculative execution attacks is chal- by speculating that an array bounds check succeeds—allowing lenging. The reason is that speculations destined to be squashed execute incorrect instructions, outside the scope of what pro- the attacker to glean information through a cache-based side grammers and compilers reason about. Further, any change to channel, as shown in Figure 1. In this case, unlike in Meltdown, micro-architectural state made by speculative execution can leak there is no exception-inducing load. information. In this paper, we propose InvisiSpec, a novel strategy to 1 // cache line size is 64 bytes defend against hardware speculation attacks in multiprocessors 2 // secret value V is 1 byte 3 // victim code begins here: Fig. 1: Spectre variant 1 at- by making speculation invisible in the data cache hierarchy. 4 uint8 A[10]; tack example, where the at- InvisiSpec blocks micro-architectural covert and side channels 5 uint8 B[256∗64]; tacker obtains secret value V through the multiprocessor data cache hierarchy due to specula- 6 // B size : possible V values ∗ line size 7 void victim ( size t a) f stored at address X.