Getting Past the Ios Passcode Ios
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MYOB EXO Onthego Setup Guide
MYOB EXO OnTheGo Setup Guide Contents Introduction 1 Welcome to MYOB EXO OnTheGo! .......................................................... 1 Installation 2 Pre-Install Requirements .......................................................................... 2 Installing the EXO API .............................................................................................. 2 Installing EXO OnTheGo ............................................................................ 2 Setup 3 Setting up EXO Business ........................................................................... 3 Adding the EXO OnTheGo Licence ........................................................................... 3 Adding EXO OnTheGo Access and Devices .............................................................. 3 Logging in to EXO OnTheGo ...................................................................... 5 Setting up a Connection .......................................................................................... 5 Troubleshooting 7 Frequently Asked Questions ..................................................................... 7 Introduction Welcome to MYOB EXO OnTheGo! The MYOB EXO OnTheGo app communicates with MYOB EXO Business to provide access to the system from your mobile device. This document is intended to get you up and running with the app—it includes the following sections: • Installation – how to download and install the EXO OnTheGo app, and what you need beforehand. • Setup – how to set up EXO Business to use the EXO OnTheGo app, and -

5Tips for Securing Your Mobile Device for Telehealth
Tips for Securing your Mobile Device 5for Telehealth The Health Insurance Portability and Accountability Act (HIPAA) requires that providers protect your information and not share it without your permission. Telehealth providers are required by law to secure medical information that can be shared electronically by encrypting messages and adding other safeguards into the software they use. However, patients’ devices on the receiving end of care often do not always have these safeguards while some medical devices have been shown to be vulnerable to hackers. It is therefore the responsibility of the patient to secure personal devices. 01 Use a PIN or Passcode to secure device Securing your mobile device is important for ensuring that others do not have access to your confidential information and applications. To protect your iPad, iPhone, Android phone you need to set a passcode. It is a 4- to 6-digit PIN used to grant access to the device, like the code you use for an ATM bank card or a debit card. Securing your Apple (iPhone and iPad) and Android devices In addition to allowing you to secure your phone with a passcode, Newer Apple and Android devices also use biometrics called Touch ID and Face ID on Apple, and Face recognition, Irises, and Fingerprints on some Android devices. These tools use your Face, eyes, and fingerprints as unique identifiers to help secure your devices. Face ID and Face recognition use your facial features in order to unlock your device. Touch ID, which is no longer being used on newer versions of iPhone and iPad, and Fingerprints on Android is a fingerprinting tool. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

BY USING YOUR Iphone, Ipad OR Ipod TOUCH (“Ios DEVICE”), YOU ARE AGREEING to BE BOUND by the FOLLOWING TERMS
ENGLISH IMPORTANT: BY USING YOUR iPHONE, iPAD OR iPOD TOUCH (“iOS DEVICE”), YOU ARE AGREEING TO BE BOUND BY THE FOLLOWING TERMS: A. APPLE iOS SOFTWARE LICENSE AGREEMENT B. APPLE PAY SUPPLEMENTAL TERMS C. NOTICES FROM APPLE APPLE INC. iOS SOFTWARE LICENSE AGREEMENT Single Use License PLEASE READ THIS SOFTWARE LICENSE AGREEMENT (“LICENSE”) CAREFULLY BEFORE USING YOUR iOS DEVICE OR DOWNLOADING THE SOFTWARE UPDATE ACCOMPANYING THIS LICENSE. BY USING YOUR iOS DEVICE OR DOWNLOADING A SOFTWARE UPDATE, AS APPLICABLE, YOU ARE AGREEING TO BE BOUND BY THE TERMS OF THIS LICENSE. IF YOU DO NOT AGREE TO THE TERMS OF THIS LICENSE, DO NOT USE THE iOS DEVICE OR DOWNLOAD THE SOFTWARE UPDATE. IF YOU HAVE RECENTLY PURCHASED AN iOS DEVICE AND YOU DO NOT AGREE TO THE TERMS OF THE LICENSE, YOU MAY RETURN THE iOS DEVICE WITHIN THE RETURN PERIOD TO THE APPLE STORE OR AUTHORIZED DISTRIBUTOR WHERE YOU OBTAINED IT FOR A REFUND, SUBJECT TO APPLE’S RETURN POLICY FOUND AT http://www.apple.com/legal/sales_policies/. 1. General. (a) The software (including Boot ROM code, embedded software and third party software), documentation, interfaces, content, fonts and any data that came with your iOS Device (“Original iOS Software”), as may be updated or replaced by feature enhancements, software updates or system restore software provided by Apple (“iOS Software Updates”), whether in read only memory, on any other media or in any other form (the Original iOS Software and iOS Software Updates are collectively referred to as the “iOS Software”) are licensed, not sold, to you by Apple Inc. -

First Pryority Bank Apple Pay®
First Pryority Bank Apple Pay® An Easier Way to Pay Don’t search for your wallet, use your smartphone to pay! Apple Pay® is a type of mobile payment system that allows users to complete transactions using their compatible Apple device. Apple Pay® for your First Pryority Bank Visa® Debit Card is easy, private, and secure. Once you’ve added your First Pryority Bank Visa® Debit Card to Apple Pay®, you can pay securely with your Touch ID or passcode at hundreds of thousands of stores and participating apps. Disclosure *Apple, the Apple Logo, iPhone, and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Apple Pay and Touch ID are trademarks of Apple Inc. Frequently Asked Questions How does it work? When you add your First Pryority Bank Visa® Debit Card in your eligible iPhone®, iPad®, Apple Watch®, or Mac®, a unique digital account number is assigned, encrypted, and securely stored, instead of using your actual card number. When you make a purchase, your actual card number is not shared by Apple with merchants or transmitted with a payment. In addition, when paying with Apple Pay®, the cashier never sees your name, card number or three-digit security code, so it is very private. To pay, just hold your iPhone near a participating merchant’s contactless reader. A vibration and beep let you know your payment has been accepted. You can also use Apple Pay on your phone, iPad Air, iPad Mini, and Apple Watch with shopping apps. Look for a contactless reader bearing these icons: What Apple devices are compatible with Apple -

Iphone - Ipad - Watch - TV Ipod - Airpods -Homepod App and Itunes January 2020
iDevices SIG iPhone - iPad - Watch - TV iPod - AirPods -HomePod App and iTunes January 2020 Happy New Year 1 Modern Life 2 Modern Life 3 Modern Life 4 A Message from our Sponsor Welcome to the iDevices SIG. We appreciate your interest in our program today. As information, participation in SIG activities requires you to be a member of the Computer Club. If you are not a CC member, you are welcome to attend today’s presentation as a guest, but you must join the club if you wish to come again. You can join online via the Sun City website ticketing program or in person at the Members Services office in the Social Center. And now back to our regularly scheduled program… 5 iDevice SIG Meeting Notes Posted on the Computer Club’s web page. Click to view or download meeting notes 6 Do you want to receive SIG emails? • Log on to Sun City website • Select ‘My Memberships’ • Put a check mark by the SIGs you want 7 Click here for the main Support Page Click here for the Support Site Map iPhone https://support.apple.com/iphone iPad https://support.apple.com/ipad Watch https://support.apple.com/watch Apple ID https://support.apple.com/apple-id iTunes https://support.apple.com/itunes Apple TV https://support.apple.com/apple-tv Apple Music https://support.apple.com/music iPod https://support.apple.com/ipod AirPods https://support.apple.com/airpods Apple Pay https://support.apple.com/apple-pay iCloud https://support.apple.com/icloud Apps https://support.apple.com/apps Manuals https://support.apple.com/en_US/manuals And don’t forget the Books app for -

Download Ios 12 Eta Download Ios 12 Eta
download ios 12 eta Download ios 12 eta. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67d363cfac2d15fe • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download iOS 12 Beta 1 IPSW for iPhone and iPad. iOS 12 beta 1 IPSW firmware can now be downloaded for installation on iPhone 5s, SE, 6, 6s, Plus, 7, 8, X, and iPad Mini 2 and above, as well as iPod Touch 6G. Introduced at WWDC 2018, it’s available for those on the Apple Developer Program. iOS 12 is the latest update from Apple for iDevices and boasts a number of new features. Its public release is slated for fall, 2018. You can download iOS 12 beta 1 ISPW firmware file for your device right now. iOS 12 Beta 1 IPSW Download Is Now Available for iPhone X, 8, 7+, 7, 6s, 6, SE, 5s, iPod & iPad. Interested in trying out this early beta of iOS 12? Well then, follow the steps we’ve listed below. -

Pangu 9 Internals
Pangu 9 Internals Tielei Wang & Hao Xu & Xiaobo Chen Team Pangu Agenda ✤ iOS Security Overview ✤ Pangu 9 Overview ✤ Userland Exploits ✤ Kernel Exploits & Kernel Patching ✤ Persistent Code Signing Bypass ✤ Conclusion Who We Are ✤ A security research team based in Shanghai, China ✤ Have broad research interests, but known for releasing jailbreak tools for iOS 7.1, iOS 8, and iOS 9 ✤ Regularly present research at BlackHat, CanSecWest, POC, RuxCon, etc. ✤ Run a mobile security conference named MOSEC (http://mosec.org) with POC in Shanghai iOS Security Overview ✤ Apple usually releases a white paper to explain its iOS security architecture ✤ Secure Booting Chain ✤ Mandatary Code Signing ✤ Restricted Sandbox ✤ Exploit Mitigation (ASLR, DEP) ✤ Data Protection ✤ Hypervisor and Secure Enclave Processor Agenda ✤ iOS Security Overview ✤ Pangu 9 Overview ✤ Userland Exploits ✤ Kernel Exploits & Kernel Patching ✤ Persistent Code Signing Bypass ✤ Conclusion What Jailbreak is “iOS jailbreaking is the removing of software restrictions imposed by iOS, Apple's operating system, on devices running it through the use of software exploits” –Wikipedia ✤ Jailbreak has to rely on kernel exploits to achieve the goal, because many software restrictions are enforced by the kernel Kernel Attack Surfaces Difficulty Gaining of the Privilege root with special entitlements root, no sandbox mobile, no sandbox mobile, less restrictive sandbox mobile, container sandbox Amount of Kernel Attack Surface Gained Our Preference Difficulty Gaining of the Privilege root with special -
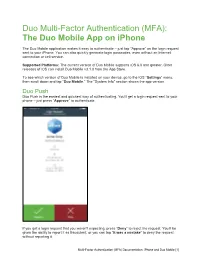
(MFA): the Duo Mobile App on Iphone
Duo Multi-Factor Authentication (MFA): The Duo Mobile App on iPhone The Duo Mobile application makes it easy to authenticate – just tap “Approve” on the login request sent to your iPhone. You can also quickly generate login passcodes, even without an Internet connection or cell service. Supported Platforms: The current version of Duo Mobile supports iOS 6.0 and greater. Older releases of iOS can install Duo Mobile v3.1.0 from the App Store. To see which version of Duo Mobile is installed on your device, go to the iOS “Settings” menu, then scroll down and tap “Duo Mobile.” The "System Info" section shows the app version. Duo Push Duo Push is the easiest and quickest way of authenticating. You'll get a login request sent to your phone – just press “Approve” to authenticate. If you get a login request that you weren't expecting, press “Deny” to reject the request. You’ll be given the ability to report it as fraudulent, or you can tap “It was a mistake” to deny the request without reporting it. Multi-Factor Authentication (MFA) Documentation: iPhone and Duo Mobile [1] Touch ID Duo Mobile for iOS also supports Touch ID for Duo Push-based logins; an additional layer of security to verify your users’ identities. If you're using a Touch ID capable iOS device, you'll see a Touch ID prompt each time you authenticate via Duo Mobile (if required by your administrator). If you're not able to scan your fingerprint using the TouchID sensor you can also approve the Duo authentication request using the device's passcode (the same one you use on the iOS lock screen). -

Ios SDK Release Notes for Ios 8.0 Beta 5
iOS SDK Release Notes for iOS 8.0 Beta 5 Important: This is a preliminary document for an API or technology in development. Apple is supplying this information to help you plan for the adoption of the technologies and programming interfaces described herein for use on Apple‑branded products. This information is subject to change, and software implemented according to this document should be tested with final operating system software and final documentation. Newer versions of this document may be provided with future betas of the API or technology. Contents: Introduction Bug Reporting Notes and Known Issues Introduction iOS SDK 8.0 provides support for developing iOS apps. It is packaged with a complete set of Xcode tools, compilers, and frameworks for creating apps for iOS and OS X. These tools include the Xcode IDE and the Instruments analysis tool, among many others. With this software you can develop apps for iPhone, iPad, or iPod touch running iOS 8. You can also test your apps using the included iOS Simulator, which supports iOS 8. iOS SDK 8.0 requires a Mac computer running OS X v10.9.3 (Mavericks) or later. This version of iOS is intended for installation only on devices registered with the Apple Developer Program. Attempting to install this version of iOS in an unauthorized manner could put your device in an unusable state. For more information and additional support resources, visit http://developer.apple.com/programs/ios/. Bug Reporting For issues not mentioned in the Notes and Known Issues section, please file bugs through the Apple Developer website (https://developer.apple.com/bug‑reporting/ios/). -

Mactans: Injecting Malware Into Ios Devices Via Malicious Chargers
MACTANS: INJECTING MALWARE INTO IOS DEVICES VIA MALICIOUS CHARGERS BILLY LAU, YEONGJIN JANG, CHENGYU SONG, TIELEI WANG, PAK HO CHUNG, AND PAUL ROYAL GEORGIA INSTITUTE OF TECHNOLOGY, ATLANTA, GA, USA [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] 1. ABSTRACT Apple iOS devices are considered by many to be more secure than other mobile offerings. In evaluating this belief, we investigated the extent to which security threats were considered when performing everyday activities such as charging a device. The results were alarming: despite the plethora of defense mechanisms in iOS, we successfully injected arbitrary software into current- generation Apple devices running the latest iOS software. All users are affected, as our approach requires neither a jailbroken device nor user interaction. In this paper, we show how an iOS device can be compromised within one minute of being plugged into a malicious charger. We first examine Apple’s existing security mechanisms to protect against arbitrary software installation, and then describe how USB capabilities can be leveraged to bypass these defense mechanisms. To demonstrate persistence of the resulting infection, we detail how an attacker can hide their software in the same way Apple hides its own built-in applications. To demonstrate practical application of these vulnerabilities, we built a proof-of-concept malicious charger, called Mactans, using a BeagleBoard. This hardware was selected to demonstrate the ease with which innocent-looking but malicious USB chargers can be constructed. While Mactans was built with a limited amount of time and a small budget, we also briefly consider what more motivated, well-funded adversaries could accomplish. -

Touch ID™ Frequently Asked Questions What Is Touch ID? Touch
Touch ID™ Frequently Asked Questions What is Touch ID? Touch ID is the biometric fingerprint authentication technology available with Apple devices such as iPhone 5s, iPhone 6 and 6S, iPad Air 2, iPad mini 3, or newer. Why use Touch ID? Touch ID is meant as a quick and convenient way to access your account. It's a seamless way to use your fingerprint as your credentials. How do I Enable or Disable Touch ID? To manually Enable or Disable Touch ID, go to the application Settings and click on Touch ID. On the Touch ID Settings screen, swipe the Touch ID button. A confirmation prompt will display. How secure is Touch ID? Every fingertip is unique, so it is rare that even a small section of two separate fingerprints are alike to register for Touch ID. If my phone has multiple fingerprints registered, will they be able to access my account? Yes, all saved fingerprints on your device will have access to your account. How do I keep my phone further protected? We recommend you add a passcode or security lock to your phone to further secure access when the device is not in use. In addition, keep your phone software up to date, including your Service 1st application. If the device doesn't recognize my fingerprint, can I still view my account? Yes, you will always have the option to log in using your account number/User ID and password. When the Touch ID prompt comes up click Cancel and enter your account credentials to log in. Can an account be Enabled for Touch ID on multiple devices? Yes, an account may be setup on multiple devices.