Fallout Exploit Kit and Raccoon Stealer White Paper
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Download Fact Sheet
Intella Process l Search l Filter l Produce. Simple. Fact Sheet Intella®: Smarter eDiscovery and Forensic Investigations Innovative, powerful, and simple – exactly the tools you need to conquer today’s data challenges and deliver world class results. Process. Search. Filter. Produce. Simple. Exponential Market Leading Industry’s Best Productivity Power Value & Pricing Key Features Customer Use Examples • Highly user-friendly interface and market-leading Intella has helped some of the world’s best known indexing speeds organizations to dramatically reduce the time, expense and • Insight Analysis feature lists the most notable user, personnel needed for their case loads. system and Internet artifacts, simplifying finding • A Fortune 500 retailer was able to bring e-discovery important data and improving examination time and functions in-house and save millions odue to Intella’s thoroughness of any investigation easy-to-use functionality. • Batch documents and assign to reviewers for subjective • The compliance department of a global financial coding for legal review institution conducts internal reviews of employee emails • Built-in instant messaging so co-workers can discuss and and files with surprising ease because of Intella’s low share documents within the tool during investigations resource/highly efficient architecture. • Automatic extraction of notable registry artifacts. This • A major international accounting and consulting firm can save the examiner many hours of manual artifact increased customer satisfaction by providing their -

TR-SBA-Research-0512-01: Fast and Efficient Browser Identification With
Fast and Efficient Browser Identification with JavaScript Engine Fingerprinting Technical Report TR-SBA-Research-0512-01 Martin Mulazzani∗, Philipp Reschl; Markus Huber∗, Manuel Leithner∗, Edgar Weippl∗ *SBA Research Favoritenstrasse 16 AT-1040 Vienna, Austria [email protected] Abstract. While web browsers are becoming more and more important in everyday life, the reliable detection of whether a client is using a specific browser is still a hard problem. So far, the UserAgent string is used, which is a self-reported string provided by the client. It is, however, not a security feature, and can be changed arbitrarily. In this paper, we propose a new method for identifying Web browsers, based on the underlying Javascript engine. We set up a Javascript confor- mance test and calculate a fingerprint that can reliably identify a given browser, and can be executed on the client within a fraction of a sec- ond. Our method is three orders of magnitude faster than previous work on browser fingerprinting, and can be implemented in just a few hun- dred lines of Javascript. Furthermore, we collected data for more than 150 browser and operating system combinations, and present algorithms to calculate minimal fingerprints for each of a given set of browsers to make fingerprinting as fast as possible. We evaluate the feasibility of our method with a survey and discuss the consequences for user privacy and security. This technique can be used to enhance state-of-the-art session management (with or without SSL), as it can make session hijacking considerably more difficult. 1 Introduction Today, the Web browser is a central component of almost every operating sys- tem. -

Free Email Software Download Best Free Email Client 2021
free email software download Best Free Email Client 2021. This article is all about best free email clients and how they can help you be more productive. We also talk about Clean Email, an easy-to-use email cleaner compatible with virtually all major email services. But before we go over the best email clients for 2021, we believe that we should first explain what advantages email clients have over web-based interfaces of various email services. Clean Email. Take control of your mailbox. What Is an Email Client and Why Should I Use One? If you’re like most people, you probably check your email at least once every day. And if you’re someone whose work involves communication with customers, clients, and coworkers, the chances are that you deal with emails all the time. Even though we spend so much time writing, forwarding, and managing emails, we hardly ever pause for a moment and think about how we could improve our emailing experience. We use clunky web interfaces that are not meant for professional use, we accept outdated applications as if alternatives didn’t exist, and we settle for the default email apps on our mobile devices even though app stores are full of excellent third-party email apps. Broadly speaking, an email client is a computer program used to access and manage a user’s email. But when we use the term email client in this article, we only mean those email clients that can be installed on a desktop computer or a mobile device—not web-based email clients that are hosted remotely and are accessible only from a web browser. -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -

Web Browser Pioneer Backs New Way to Surf Internet (Update 2) 7 November 2010, by MICHAEL LIEDTKE , AP Technology Writer
Web browser pioneer backs new way to surf Internet (Update 2) 7 November 2010, By MICHAEL LIEDTKE , AP Technology Writer (AP) -- The Web has changed a lot since Marc Facebook's imprint also is all over RockMelt, Andreessen revolutionized the Internet with the although the two companies' only business introduction of his Netscape browser in the connection so far is Andreessen. He also serves on mid-1990s. That's why he's betting people are Facebook's board of directors. ready to try a different Web-surfing technique on a new browser called RockMelt. RockMelt only works if you have a Facebook account. That restriction still gives RockMelt plenty The browser, available for the first time Monday, is of room to grow, given Facebook has more than built on the premise that most online activity today 500 million users. revolves around socializing on Facebook, searching on Google, tweeting on Twitter and After Facebook users log on RockMelt with their monitoring a handful of favorite websites. It tries to Facebook account information, the person's minimize the need to roam from one website to the Facebook profile picture is planted in the browser's next by corralling all vital information and favorite left hand corner and a list of favorite friends can be services in panes and drop-down windows. displayed in the browser's left hand pane. There's also a built-in tool for posting updates in a pop-up "This is a chance for us to build a browser all over box. again," Andreessen said. "These are all things we would have done (at Netscape) if we had known The features extend beyond Facebook and Twitter. -

Spear Phishing Targeting Ics Supply Chain – Analysis
SPEAR PHISHING TARGETING ICS SUPPLY CHAIN – ANALYSIS January 20, 2021 MARKEL PICADO 1 Table of Contents Introduction ................................................................................................................................................... 3 Threat Analysis ............................................................................................................................................... 3 Distribution Strategy .................................................................................................................................. 4 Spear Phishing............................................................................................................................................ 5 Identity Theft ......................................................................................................................................... 5 Toolkit .................................................................................................................................................... 8 AgentTesla v3 Analysis ........................................................................................................................... 9 Attack Surface .......................................................................................................................................... 16 MITRE ATT&CK Mapping ..................................................................................................................... 17 Threat Actor Infrastructure ................................................................................................................ -

Downloadable Email Program for My Pc 32 Best Free Email Clients
downloadable email program for my pc 32 Best Free Email Clients. Here are 32 best free email client software . These let you manage and access all of your email accounts in one single place easily. All these email client software are completely free and can be downloaded to Windows PC. These free software offer various features, like: can be used with IMAP, SMTP, POP3 and Gmail, keeps your emails safe and secure, lets you open various emails simultaneously, provide protection from spam, lets you view your emails offline, manage and access all of your email accounts in one single place, supports PH, LDAP, IMAP4, POP3 and SMPT mail protocols etc. So, go through this list of free email client software and see which ones you like the most. Thunderbird. Thunderbird is a free and handy email client software for your computer. It can be used with IMAP, SMTP, POP3 and Gmail. It will also work with email accounts provided by MS Exchange Server. The user interface of Thunderbird is tabbed. It lets you open various emails simultaneously. Thunderbird keeps your emails safe and secure. It also has special filters for filtering the mail. Windows Live Mail. Windows Live Mail is a free email client for your computer. It works with various email accounts. It lets you access Yahoo, Gmail, Hotmail and emails from different servers which supports POP3 and SMTP. Its security features are excellent it will also provide protection from spam. You can also view your emails offline in this freeware. Zimbra Desktop. Zimbra Desktop is a free email client. -

Böngésző Programok 23. Tétel
23.tétel 1.0 Böngész ő programok használata, összehasonlítása. Az információ keresés technikái. Bogdán;Sleisz Böngész ő programok (Használata, összehasonlítása. Az információ keresés technikái) 23. tétel Az Internet kialakulása 20. század második felére helyezhet ő. Az ARPA rendszerb ől fejl ődött tovább az USA-ban, azóta folyamatosan fejlesztgetik a különböz ő protokollokat, illetve technológiákat, az adatforgalom sebességének növelése érdekében. Komoly tévhitet képez a világban, hogy az Internet az a böngész őben megjeleníthet ő weboldalak összessége. Nagy tévedés, ugyanis ez csak a HTTP protokoll által szolgáltatott tartalom, amely a teljes internetes adatforgalomnak kevesebb, mint az 1/10-ét képezi. Az internetet úgy kell elképzelni, mint egy hardvereszközt, ami az egész világot lefedi, a rajta elérhet ő szolgáltatásokat pedig nevezzük "szoftvereknek". Kétségkívül az egyik legelterjedtebb szolgáltatás ("szoftver") a 80-as port -on kommunikáló HTTP protokoll, amihez tartozik egy kommunikációs nyelv is. A HTTP protokoll célja hagyományos esetben- a távoli "szerveren/kiszolgálón" elhelyezked ő weboldal letöltése a helyi számítógépre. 1. A böngész ő a HTTP kommunikációs nyelven megfogalmazott kérést küld a szerver felé, hogy szeretnénk megjeleníteni a kért weboldalt 2. A szerver válaszol. Többféle üzenetet küldhet vissza a böngész őnek, és minden üzenethez tartozik egy azonosító szám is, úgynevezett Status Code. A legismertebb visszatérési érték talán a Not Found (a keresett weboldal nem található), melynek Status Code-ja a 404. Ilyet könnyedén el őidézhetünk, ha pl. nem létez ő oldalt próbálunk letölteni. A leggyakoribb azonban, ha a 200-as üzenetet kapjuk vissza, vagyis megjelenik az oldal. 3. Ezek után a böngész ő elkezdi letölteni a kért oldal forráskódját . A forráskód egy olyan leíró kód nagyrészt HTML nyelven, amely leírja, hogyan néz ki a weboldal. -

The Artist's Emergent Journey the Metaphysics of Henri Bergson, and Also Those by Eric Voegelin Against Gnosticism2
Vol 1 No 2 (Autumn 2020) Online: jps.library.utoronto.ca/index.php/nexj Visit our WebBlog: newexplorations.net The Artist’s Emergent Journey Clinton Ignatov—The McLuhan Institute—[email protected] To examine computers as a medium in the style of Marshall McLuhan, we must understand the origins of his own perceptions on the nature of media and his deep-seated religious impetus for their development. First we will uncover McLuhan’s reasoning in his description of the artist and the occult origins of his categories of hot and cool media. This will prepare us to recognize these categories when they are reformulated by cyberneticist Norbert Wiener and ethnographer Sherry Turkle. Then, as we consider the roles “black boxes” play in contemporary art and theory, many ways of bringing McLuhan’s insights on space perception and the role of the artist up to date for the work of defining and explaining cyberspace will be demonstrated. Through this work the paradoxical morality of McLuhan’s decision to not make moral value judgments will have been made clear. Introduction In order to bring Marshall McLuhan into the 21st century it is insufficient to retrieve his public persona. This particular character, performed in the ‘60s and ‘70s on the global theater’s world stage, was tailored to the audiences of its time. For our purposes today, we’ve no option but an audacious attempt to retrieve, as best we can, the whole man. To these ends, while examining the media of our time, we will strive to delicately reconstruct the human-scale McLuhan from what has been left in both his public and private written corpus. -

Instrumentalizing the Sources of Attraction. How Russia Undermines Its Own Soft Power
INSTRUMENTALIZING THE SOURCES OF ATTRACTION. HOW RUSSIA UNDERMINES ITS OWN SOFT POWER By Vasile Rotaru Abstract The 2011-2013 domestic protests and the 2013-2015 Ukraine crisis have brought to the Russian politics forefront an increasing preoccupation for the soft power. The concept started to be used in official discourses and documents and a series of measures have been taken both to avoid the ‘dangers’ of and to streamline Russia’s soft power. This dichotomous approach towards the ‘power of attraction’ have revealed the differences of perception of the soft power by Russian officials and the Western counterparts. The present paper will analyse Russia’s efforts to control and to instrumentalize the sources of soft power, trying to assess the effectiveness of such an approach. Keywords: Russian soft power, Russian foreign policy, public diplomacy, Russian mass media, Russian internet Introduction The use of term soft power is relatively new in the Russian political circles, however, it has become recently increasingly popular among the Russian analysts, policy makers and politicians. The term per se was used for the first time in Russian political discourse in February 2012 by Vladimir Putin. In the presidential election campaign, the then candidate Putin drew attention to the fact that soft power – “a set of tools and methods to achieve foreign policy goals without the use of arms but by exerting information and other levers of influence” is used frequently by “big countries, international blocks or corporations” “to develop and provoke extremist, separatist and nationalistic attitudes, to manipulate the public and to directly interfere in the domestic policy of sovereign countries” (Putin 2012). -

Background Setup
1.5.09 [email protected] Mechanical Turk/Browser Ballot Findings Background To compliment the testing and research done by Critical and Patrick Finch in Europe, I conducted a series of tests on Amazon’s Mechanical Turk to try out various aspects of the EC's Ballot design. The goal is to determine both how to design the ballot in the most neutral way possible, and for Mozilla to determine the most successful summary and image for the Firefox section of the ballot. I used MT because it’s a very fast and cheap way to get a design in front of many eyes. And the responses that came back were very good; users spent an average of 2.8 minutes on a five- minute test, and gave complete answers to free-form questions. A few drawbacks of the test were: • Users tended to be more highly-technical than average • Users tended to have heard of Firefox and already have a favorable opinion about it • MT did not provide a way to filter results by country, and many users were in North America as a result Because of the above problems, the MT tests are not the best sample of users that are similar to those seeing the ballot in Europe. However, their answers still provided some insight into why people use what browsers, what factors would make them switch, and what presentations of Firefox’s brand and motto would be most compelling. Setup The MT tests were given in three phases. In all of these test, various demographics questions such as what browser the user was running and where they live were asked. -
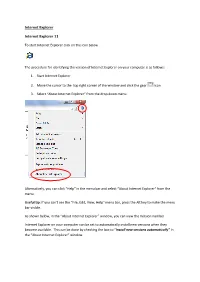
Internet Explorer
Internet Explorer Internet Explorer 11 To start Internet Explorer click on the icon below The procedure for identifying the version of Internet Explorer on your computer is as follows: 1. Start Internet Explorer 2. Move the cursor to the top right corner of the window and click the gear icon 3. Select “About Internet Explorer” from the drop down menu. Alternatively, you can click “Help” in the menu bar and select “About Internet Explorer“ from the menu. Useful tip: If you can’t see the “File, Edit, View, Help” menu bar, press the Alt key to make the menu bar visible. As shown below, in the “About Internet Explorer” window, you can view the Version number. Internet Explorer on your computer can be set to automatically install new versions when they become available. This can be done by checking the box to “Install new versions automatically” In the “About Internet Explorer” window. Internet Explorer 9 To view the “About” page in Internet Explorer: 1. At the top right of the program window, click the gear icon 2. Select “About Internet Explorer” in the drop down menu. The version number will be displayed in the “About Internet Explorer” window, see example below. Updating your Internet Explorer Browser Microsoft updates Internet Explorer using its Windows update feature. If you are regularly installing the latest Windows updates from Microsoft then you should be on the latest version of Internet Explorer. Note Windows 10 automatically updates Internet Explorer. Follow the procedure below to manually trigger an update of the Internet Explorer Browser: 1. Open the Control Panel.