Two Years of Pawn Storm Examining an Increasingly Relevant Threat
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
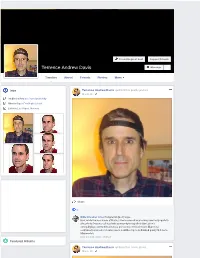
Terrence Andrew Davis Message
Friend Request Sent Suggest Friends Terrence Andrew Davis Message Timeline About Friends Photos More Intro Terrence Andrew Davis updated his profile picture. March 10 · Studied at Arizona State University Went to Agua Fria High School Lives in Las Vegas, Nevada Share 1 BibleStreamer Israel TempleBot (God) Says... trust rendezvous silicosis affiliating Hiss's screechier phoning ravelled populist's slingshot's Deanna callings left's anonymity's respelled fabrication's exemplifying casters friendliness's quiescence refusal russet filigreeing southwest paramedic's townhouse's debilities taproots flunked gauzy Moldavia Minnesota's May 24 at 11:46pm · Edited Featured Albums Terrence Andrew Davis updated his cover photo. March 10 · English (US) · Español · Português (Brasil) · Français (France) · Deutsch Privacy · Terms · Advertising · Ad Choices · Cookies · More Facebook © 2017 Share 1 Share Terrence Andrew Davis December 30, 2015 · What's a good tombstone, God? God says... Isidro's brigantine's prediction's Quinton's guile musician Coppola's leukocyte's whippoorwill's stokes finished ibexes Earlene's marrows magnetically Krishnamurti yahoos futz George's staccato's platypuses eloquence's finery's wiggly gouges engages Leningrad's Shackleton Mon mistaken Amoco alcoholic Share Terrence Andrew Davis December 30, 2015 · God says... swelter's legibly streptococcal lobster's deleting cowlick's schoolmistress itemization snowsuit's sawdust goings scanners ancestor crystals whined Pele noise's Royal exhausting nationalized trotted hollowing symbolizes impecunious stutters Chukchi territorial snug wiped candlesticks faeces oligarchic Share Terrence Andrew Davis December 30, 2015 · CIA agents will sandpaper their SS tatoos. Share Terrence Andrew Davis December 30, 2015 · http://science.slashdot.org/…/exploding-munitions-caught-on… God says.. -

Hacking the Web
Hacking the Web (C) 2009-2020 Arun Viswanathan Ellis Horowitz Marco Papa 1 Table of Contents } General Introduction } Authentication Attacks } Client-Side Attacks } Injection Attacks } Recent Attacks } Privacy Tools 2 (C) 2009-2020 Arun Viswanathan Ellis Horowitz Marco Papa Why secure the Web? } The Web has evolved into an ubiquitous entity providing a rich and common platform for connecting people and doing business. } BUT, the Web also offers a cheap, effective, convenient and anonymous platform for crime. } To get an idea, the Web has been used for the following types of criminal activities (source: The Web Hacking Incidents Database (WHID) http://projects.webappsec.org/w/page/13246995/Web-Hacking-Incident-Database) } Chaos (Attack on Russian nuclear power websites amid accident rumors (5Jan09) } Deceit (SAMY XSS Worm – Nov 2005) } Extortion (David Aireys domain hijacked due to a CSRF (cross site request forgery) flaw in Gmail – 30Dec2007) } Identity Theft (XSS on Yahoo! Hot jobs – Oct 2008) } Information Warfare (Israeli Gaza War - Jan 2009 / Balkan Wars – Apr 2008 ) } Monetary Loss (eBay fraud using XSS) } Physical Pain (Hackers post on epilepsy forum causes migraines and seizures – May 2008) } Political Defacements (Hacker changes news release on Sheriffs website – Jul 2008) (Obama, Oreilly and Britneys Twitter accounts hacked and malicious comments posted – Jan 09) } Chinese Gaming sites hacked (Dec. 2011) 3 Copyright(C) 2009 (c) -20092020- 2019Arun Arun Viswanathan Viswanathan Ellis HorowitzEllis Horowitz Marco Marco Papa Papa -

Chess Horizons
FREE ENTRY FOR GMs & IMs 78th New England Open September 1 – 3, 2018 Location: Crowne Plaza Boston - Newton 20 USCF 320 Washington St. Grand Prix 3‐day and 2‐day options available! Newton, MA 02458 Points Prizes: $4,000 b/120 paid entries, 75% guaranteed Championship $650 – 300 – 250, top U2400 $225, top U2200 $225 U2000 $400 – 200 – 150 U1800 $400 – 200 – 150 U1600 $300 – 150 – 100, top U1400 $150, top U1200 $150 Time Control: 40/100, SD/30 d10 (2‐day rounds 1‐3 are G/45 d5) Sections: Championship Section (rated 1800+) – 3‐day only – FIDE Rated U2000 Section – 3‐day or 2‐day U1800 Section – 3‐day or 2‐day U1600 Section – 3‐day or 2‐day Round Times: 3‐day section – Saturday 11 AM & 5 PM, Sunday 11 AM & 5 PM, Monday 10 AM & 3: 5 PM 2‐day section – Sunday 1 : 0 AM, 1: 0 PM, : 0 PM, & 5 PM; Monday 10 AM & 3: 5 PM :00 :30 :00 :30 :30 4 Byes: Limit 2 byes, rounds 1‐5 in1 0 Championship Section, rounds 1‐6 in0 3 0 :30 U2000:30 to U16004 sections. Players must commit to byes in rounds 4‐6 before round 2. Entry Fee: Byes in rounds 4-6 are irrevocable. 3‐day section ‐ $75 online by 11:59 PM on 8/3 , $85 onsite 2‐day section ‐ $74 online by 11:59 PM on 8/3 , $85 onsite 0 Onsite Registration: 3‐day – Saturday 9/ from 8:0 30 to 9:30 AM; 2‐day – Sunday 9/ from 8:30 to 9:30 AM Other Information: 1 2 ‐ There is no 2‐day schedule for the Championship Section. -

Cyber-Conflict Between the United States of America and Russia CSS
CSS CYBER DEFENSE PROJECT Hotspot Analysis: Cyber-conflict between the United States of America and Russia Zürich, June 2017 Version 1 Risk and Resilience Team Center for Security Studies (CSS), ETH Zürich Cyber-conflict between the United States of America and Russia Authors: Marie Baezner, Patrice Robin © 2017 Center for Security Studies (CSS), ETH Zürich Contact: Center for Security Studies Haldeneggsteig 4 ETH Zürich CH-8092 Zurich Switzerland Tel.: +41-44-632 40 25 [email protected] www.css.ethz.ch Analysis prepared by: Center for Security Studies (CSS), ETH Zürich ETH-CSS project management: Tim Prior, Head of the Risk and Resilience Research Group; Myriam Dunn Cavelty, Deputy Head for Research and Teaching; Andreas Wenger, Director of the CSS Disclaimer: The opinions presented in this study exclusively reflect the authors’ views. Please cite as: Baezner, Marie; Robin, Patrice (2017): Hotspot Analysis: Cyber-conflict between the United States of America and Russia, June 2017, Center for Security Studies (CSS), ETH Zürich. 2 Cyber-conflict between the United States of America and Russia Table of Contents 1 Introduction 5 2 Background and chronology 6 3 Description 9 3.1 Tools and techniques 9 3.2 Targets 10 3.3 Attribution and actors 10 4 Effects 11 4.1 Social and internal political effects 11 4.2 Economic effects 13 4.3 Technological effects 13 4.4 International effects 13 5 Consequences 14 5.1 Improvement of cybersecurity 14 5.2 Raising awareness of propaganda and misinformation 15 5.3 Observation of the evolution of relations between the USA and Russia 15 5.4 Promotion of Confidence Building Measures 16 6 Annex 1 17 7 Glossary 18 8 Abbreviations 19 9 Bibliography 19 3 Cyber-conflict between the United States of America and Russia Executive Summary Effects Targets: US State institutions and a political The analysis found that the tensions between the party. -

I Make This Pledge to You Alone, the Castle Walls Protect Our Back That I Shall Serve Your Royal Throne
AMERA M. ANDERSEN Battlefield of Life “I make this pledge to you alone, The castle walls protect our back that I shall serve your royal throne. and Bishops plan for their attack; My silver sword, I gladly wield. a master plan that is concealed. Squares eight times eight the battlefield. Squares eight times eight the battlefield. With knights upon their mighty steed For chess is but a game of life the front line pawns have vowed to bleed and I your Queen, a loving wife and neither Queen shall ever yield. shall guard my liege and raise my shield Squares eight times eight the battlefield. Squares eight time eight the battlefield.” Apathy Checkmate I set my moves up strategically, enemy kings are taken easily Knights move four spaces, in place of bishops east of me Communicate with pawns on a telepathic frequency Smash knights with mics in militant mental fights, it seems to be An everlasting battle on the 64-block geometric metal battlefield The sword of my rook, will shatter your feeble battle shield I witness a bishop that’ll wield his mystic sword And slaughter every player who inhabits my chessboard Knight to Queen’s three, I slice through MCs Seize the rook’s towers and the bishop’s ministries VISWANATHAN ANAND “Confidence is very important—even pretending to be confident. If you make a mistake but do not let your opponent see what you are thinking, then he may overlook the mistake.” Public Enemy Rebel Without A Pause No matter what the name we’re all the same Pieces in one big chess game GERALD ABRAHAMS “One way of looking at chess development is to regard it as a fight for freedom. -

UC Santa Cruz Electronic Theses and Dissertations
UC Santa Cruz UC Santa Cruz Electronic Theses and Dissertations Title Unbecoming Silicon Valley: Techno Imaginaries and Materialities in Postsocialist Romania Permalink https://escholarship.org/uc/item/0vt9c4bq Author McElroy, Erin Mariel Brownstein Publication Date 2019 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA SANTA CRUZ UNBECOMING SILICON VALLEY: TECHNO IMAGINARIES AND MATERIALITIES IN POSTSOCIALIST ROMANIA A dissertation submitted in partial satisfaction of the requirements for the degree of DOCTOR OF PHILOSOPHY in FEMINIST STUDIES by Erin Mariel Brownstein McElroy June 2019 The Dissertation of Erin McElroy is approved: ________________________________ Professor Neda Atanasoski, Chair ________________________________ Professor Karen Barad ________________________________ Professor Lisa Rofel ________________________________ Professor Megan Moodie ________________________________ Professor Liviu Chelcea ________________________________ Lori Kletzer Vice Provost and Dean of Graduate Studies Copyright © by Erin McElroy 2019 Table of Contents Abstract, iv-v Acknowledgements, vi-xi Introduction: Unbecoming Silicon Valley: Techno Imaginaries and Materialities in Postsocialist Romania, 1-44 Chapter 1: Digital Nomads in Siliconizing Cluj: Material and Allegorical Double Dispossession, 45-90 Chapter 2: Corrupting Techno-normativity in Postsocialist Romania: Queering Code and Computers, 91-127 Chapter 3: The Light Revolution, Blood Gold, and -

View Final Report (PDF)
TABLE OF CONTENTS TABLE OF CONTENTS I EXECUTIVE SUMMARY III INTRODUCTION 1 GENESIS OF THE PROJECT 1 RESEARCH QUESTIONS 1 INDUSTRY SITUATION 2 METHODOLOGY 3 GENERAL COMMENTS ON INTERVIEWS 5 APT1 (CHINA) 6 SUMMARY 7 THE GROUP 7 TIMELINE 7 TYPOLOGY OF ATTACKS 9 DISCLOSURE EVENTS 9 APT10 (CHINA) 13 INTRODUCTION 14 THE GROUP 14 TIMELINE 15 TYPOLOGY OF ATTACKS 16 DISCLOSURE EVENTS 18 COBALT (CRIMINAL GROUP) 22 INTRODUCTION 23 THE GROUP 23 TIMELINE 25 TYPOLOGY OF ATTACKS 27 DISCLOSURE EVENTS 30 APT33 (IRAN) 33 INTRODUCTION 34 THE GROUP 34 TIMELINE 35 TYPOLOGY OF ATTACKS 37 DISCLOSURE EVENTS 38 APT34 (IRAN) 41 INTRODUCTION 42 THE GROUP 42 SIPA Capstone 2020 i The Impact of Information Disclosures on APT Operations TIMELINE 43 TYPOLOGY OF ATTACKS 44 DISCLOSURE EVENTS 48 APT38 (NORTH KOREA) 52 INTRODUCTION 53 THE GROUP 53 TIMELINE 55 TYPOLOGY OF ATTACKS 59 DISCLOSURE EVENTS 61 APT28 (RUSSIA) 65 INTRODUCTION 66 THE GROUP 66 TIMELINE 66 TYPOLOGY OF ATTACKS 69 DISCLOSURE EVENTS 71 APT29 (RUSSIA) 74 INTRODUCTION 75 THE GROUP 75 TIMELINE 76 TYPOLOGY OF ATTACKS 79 DISCLOSURE EVENTS 81 COMPARISON AND ANALYSIS 84 DIFFERENCES BETWEEN ACTOR RESPONSE 84 CONTRIBUTING FACTORS TO SIMILARITIES AND DIFFERENCES 86 MEASURING THE SUCCESS OF DISCLOSURES 90 IMPLICATIONS OF OUR RESEARCH 92 FOR PERSISTENT ENGAGEMENT AND FORWARD DEFENSE 92 FOR PRIVATE CYBERSECURITY VENDORS 96 FOR THE FINANCIAL SECTOR 96 ROOM FOR FURTHER RESEARCH 97 ACKNOWLEDGEMENTS 98 ABOUT THE TEAM 99 SIPA Capstone 2020 ii The Impact of Information Disclosures on APT Operations EXECUTIVE SUMMARY This project was completed to fulfill the including the scope of the disclosure and capstone requirement for Columbia Uni- the disclosing actor. -

List of Targets of Arrested Computer Hackers 6 March 2012
List of targets of arrested computer hackers 6 March 2012 The five computer hackers charged in New York Tribune and Los Angeles Times, using on Tuesday and a sixth who pleaded guilty are misappropriated login credentials. accused of involvement in some of the most notorious hacking incidents of the past 18 months. -- February 2011: A cyberattack on private computer security firm HBGary that involved the The following are some of the cyberattacks in theft of 60,000 emails from HBGary employees and which the two Britons, two Irishmen and two the HBGary chief executive, as well as defacing his Americans allegedly played a role as members of Twitter account. Anonymous, Lulz Security or associated groups: -- April-May 2011: A cyberattack on a Fox -- December 2010: Operation Payback. Distributed Broadcasting Company website that involved the denial of service (DDoS) attacks by members of theft of names, dates of birth, telephone numbers, Anonymous on the websites of MasterCard, email and residential addresses for more than PayPal and Visa in retaliation for their refusal to 70,000 potential contestants on the Fox television accept donations for WikiLeaks. In a DDoS attack, show the "X-Factor." a website is bombarded with traffic, slowing it down or knocking it offline completely. -- May 2011: A cyberattack on Sony Pictures Entertainment that revealed the passwords, email -- January 2011: Defacing a website of the Irish addresses, home addresses and dates of birth of political party Fine Gael after accessing computer 100,000 users of the www.sonypictures.com servers in Arizona used to maintain the website, website and a subsequent online attack against www.finegael2011.com. -

A PRACTICAL METHOD of IDENTIFYING CYBERATTACKS February 2018 INDEX
In Collaboration With A PRACTICAL METHOD OF IDENTIFYING CYBERATTACKS February 2018 INDEX TOPICS EXECUTIVE SUMMARY 4 OVERVIEW 5 THE RESPONSES TO A GROWING THREAT 7 DIFFERENT TYPES OF PERPETRATORS 10 THE SCOURGE OF CYBERCRIME 11 THE EVOLUTION OF CYBERWARFARE 12 CYBERACTIVISM: ACTIVE AS EVER 13 THE ATTRIBUTION PROBLEM 14 TRACKING THE ORIGINS OF CYBERATTACKS 17 CONCLUSION 20 APPENDIX: TIMELINE OF CYBERSECURITY 21 INCIDENTS 2 A Practical Method of Identifying Cyberattacks EXECUTIVE OVERVIEW SUMMARY The frequency and scope of cyberattacks Cyberattacks carried out by a range of entities are continue to grow, and yet despite the seriousness a growing threat to the security of governments of the problem, it remains extremely difficult to and their citizens. There are three main sources differentiate between the various sources of an of attacks; activists, criminals and governments, attack. This paper aims to shed light on the main and - based on the evidence - it is sometimes types of cyberattacks and provides examples hard to differentiate them. Indeed, they may of each. In particular, a high level framework sometimes work together when their interests for investigation is presented, aimed at helping are aligned. The increasing frequency and severity analysts in gaining a better understanding of the of the attacks makes it more important than ever origins of threats, the motive of the attacker, the to understand the source. Knowing who planned technical origin of the attack, the information an attack might make it easier to capture the contained in the coding of the malware and culprits or frame an appropriate response. the attacker’s modus operandi. -

Episode 230: Click Here to Kill Everybody
Episode 230: Click Here to Kill Everybody Stewart Baker: [00:00:03] Welcome to Episode 230 of The Cyberlaw Podcast brought to you by Steptoe & Johnson. We are back and full of energy. Thank you for joining us. We're lawyers talking about technology, security, privacy, and government. And if you want me to talk about hiking through the rain forest of Costa Rica and just how tough my six-year-old granddaughter is, I'm glad to do that too. But today I'm joined by our guest interviewee Bruce Schneier, an internationally renowned technologist, privacy and security guru, and the author of the new book, Click Here to Kill Everybody: Security and Survival in a Hyper-Connected World. We'll be talking to him shortly. For the News Roundup, we have Jamil Jaffer, who's the founder of the estimable and ever-growing National Security Institute. He's also an adjunct professor at George Mason University. Welcome, Jamil. Jamil Jaffer: [00:00:57] Thanks, Stewart. Good to be here. Stewart Baker: [00:00:58] And David Kris, formerly the assistant attorney general in charge of the Justice Department's National Security Division. David, welcome. David Kris: [00:01:07] Thank, you. Good to be here. Stewart Baker: [00:01:08] And he is with his partner in their latest venture, Nate Jones, veteran of the Justice Department, the National Security Council, and Microsoft where he was an assistant general counsel. Nate, welcome. Nate Jones: [00:01:23] Thank you. Stewart Baker: [00:01:25] I'm Stewart Baker, formerly with the NSA and DHS and the host of today's program. -

Reporting, and General Mentions Seem to Be in Decline
CYBER THREAT ANALYSIS Return to Normalcy: False Flags and the Decline of International Hacktivism By Insikt Group® CTA-2019-0821 CYBER THREAT ANALYSIS Groups with the trappings of hacktivism have recently dumped Russian and Iranian state security organization records online, although neither have proclaimed themselves to be hacktivists. In addition, hacktivism has taken a back seat in news reporting, and general mentions seem to be in decline. Insikt Group utilized the Recorded FutureⓇ Platform and reports of historical hacktivism events to analyze the shifting targets and players in the hacktivism space. The target audience of this research includes security practitioners whose enterprises may be targets for hacktivism. Executive Summary Hacktivism often brings to mind a loose collective of individuals globally that band together to achieve a common goal. However, Insikt Group research demonstrates that this is a misleading assumption; the hacktivist landscape has consistently included actors reacting to regional events, and has also involved states operating under the guise of hacktivism to achieve geopolitical goals. In the last 10 years, the number of large-scale, international hacking operations most commonly associated with hacktivism has risen astronomically, only to fall off just as dramatically after 2015 and 2016. This constitutes a return to normalcy, in which hacktivist groups are usually small sets of regional actors targeting specific organizations to protest regional events, or nation-state groups operating under the guise of hacktivism. Attack vectors used by hacktivist groups have remained largely consistent from 2010 to 2019, and tooling has assisted actors to conduct larger-scale attacks. However, company defenses have also become significantly better in the last decade, which has likely contributed to the decline in successful hacktivist operations. -

Positional Attacks
Positional Attacks Joel Johnson Edited by: Patrick Hammond © Joel Johnson, January 2014 All rights reserved. No part of this book may be reproduced, transmitted in any form by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission from Joel Johnson. Edited by: Patrick Hammond Cover Photography: Barry M. Evans Cover Design and Proofreading: Joel Johnson Game Searching: Joel Johnson, Richard J. Cowan, William Parker, Nick Desmarais Game Contributors: Brian Wall, Jack Young, Clyde Nakamura, James Rizzitano, Keith Hayward, Hal Terrie, Richard Cowan, Jesús Seoane, William Parker, Domingos Perego, Danielle Rice Linares Diagram and Linares Figurine fonts ©1993-2003 by Alpine Electronics, Steve Smith Alpine Electronics 703 Ivinson Ave. Laramie, WY 82070 Email: Alpine Chess Fonts ([email protected]) Website: http://www.partae.com/fonts/ Pressure Gauge graphic Image Copyright Araminta, 2012 Used under license from Shutterstock.com In Memoriam to my step dad and World War II Navy, Purple Heart Recipient, Theodore Kosiavelon, 12/22/1921 – 11/09/2012 CONTENTS Preface 7 Kudos 7 Brian Wall 8 Young Rising Stars 27 Daniil Dubov 27 Wei Yi 30 Section A – Pawn Roles 36 Pawn Structure 37 Ugliest Pawn Structure Ever? 38 Anchoring 41 Alien Pawn 48 Pawn Lever 63 Pawn Break 72 Center Pawn Mass 75 Isolated Pawn 94 Black Strategy 95 White Strategy 96 Eliminate the Isolated Pawn Weakness with d4-d5 96 Sacrifices on e6 & f7 , Often with f2-f4-f5 Played 99 Rook Lift Attack 104 Queenside Play 111 This Is Not Just