Hacking the Web
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Arxiv:1907.07120V1 [Cs.CY] 16 Jul 2019 1 Introduction That China Hindered Access to I2P by Poisoning DNS Resolu- Tions of the I2P Homepage and Three Reseed Servers](https://docslib.b-cdn.net/cover/9451/arxiv-1907-07120v1-cs-cy-16-jul-2019-1-introduction-that-china-hindered-access-to-i2p-by-poisoning-dns-resolu-tions-of-the-i2p-homepage-and-three-reseed-servers-59451.webp)
Arxiv:1907.07120V1 [Cs.CY] 16 Jul 2019 1 Introduction That China Hindered Access to I2P by Poisoning DNS Resolu- Tions of the I2P Homepage and Three Reseed Servers
Measuring I2P Censorship at a Global Scale Nguyen Phong Hoang Sadie Doreen Michalis Polychronakis Stony Brook University The Invisible Internet Project Stony Brook University Abstract required flexibility for conducting fine-grained measurements on demand. We demonstrate these benefits by conducting an The prevalence of Internet censorship has prompted the in-depth investigation of the extent to which the I2P (invis- creation of several measurement platforms for monitoring ible Internet project) anonymity network is blocked across filtering activities. An important challenge faced by these different countries. platforms revolves around the trade-off between depth of mea- Due to the prevalence of Internet censorship and online surement and breadth of coverage. In this paper, we present surveillance in recent years [7, 34, 62], many pro-privacy and an opportunistic censorship measurement infrastructure built censorship circumvention tools, such as proxy servers, virtual on top of a network of distributed VPN servers run by vol- private networks (VPN), and anonymity networks have been unteers, which we used to measure the extent to which the developed. Among these tools, Tor [23] (based on onion rout- I2P anonymity network is blocked around the world. This ing [39,71]) and I2P [85] (based on garlic routing [24,25,33]) infrastructure provides us with not only numerous and ge- are widely used by privacy-conscious and censored users, as ographically diverse vantage points, but also the ability to they provide a higher level of privacy and anonymity [42]. conduct in-depth measurements across all levels of the net- In response, censors often hinder access to these services work stack. -
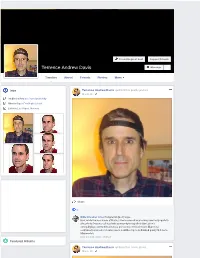
Terrence Andrew Davis Message
Friend Request Sent Suggest Friends Terrence Andrew Davis Message Timeline About Friends Photos More Intro Terrence Andrew Davis updated his profile picture. March 10 · Studied at Arizona State University Went to Agua Fria High School Lives in Las Vegas, Nevada Share 1 BibleStreamer Israel TempleBot (God) Says... trust rendezvous silicosis affiliating Hiss's screechier phoning ravelled populist's slingshot's Deanna callings left's anonymity's respelled fabrication's exemplifying casters friendliness's quiescence refusal russet filigreeing southwest paramedic's townhouse's debilities taproots flunked gauzy Moldavia Minnesota's May 24 at 11:46pm · Edited Featured Albums Terrence Andrew Davis updated his cover photo. March 10 · English (US) · Español · Português (Brasil) · Français (France) · Deutsch Privacy · Terms · Advertising · Ad Choices · Cookies · More Facebook © 2017 Share 1 Share Terrence Andrew Davis December 30, 2015 · What's a good tombstone, God? God says... Isidro's brigantine's prediction's Quinton's guile musician Coppola's leukocyte's whippoorwill's stokes finished ibexes Earlene's marrows magnetically Krishnamurti yahoos futz George's staccato's platypuses eloquence's finery's wiggly gouges engages Leningrad's Shackleton Mon mistaken Amoco alcoholic Share Terrence Andrew Davis December 30, 2015 · God says... swelter's legibly streptococcal lobster's deleting cowlick's schoolmistress itemization snowsuit's sawdust goings scanners ancestor crystals whined Pele noise's Royal exhausting nationalized trotted hollowing symbolizes impecunious stutters Chukchi territorial snug wiped candlesticks faeces oligarchic Share Terrence Andrew Davis December 30, 2015 · CIA agents will sandpaper their SS tatoos. Share Terrence Andrew Davis December 30, 2015 · http://science.slashdot.org/…/exploding-munitions-caught-on… God says.. -

Securing Information in a Mobile World
Securing Information in a Mobile World Thu, Jan 21 | 2:00 p.m. – 3:30 p.m. PRESENTED BY: Charlie LeBlanc, William Figures, and Blad Slavens Schedulers & Dispatchers Conference | Tampa, FL | January 19 – 22, 2016 A Brief History of Computing and Software for Schedulers and Dispatchers Systems in the 80’s and early 90’s were computer- centric and pretty secure…. Why ????? And then came the Internet !!!! Highly technical description of the Internet “The Internet is a data network that connects “everything” together” (kind of like the phone system !) - William Figures 2007 The ‘Net(work) as a computing platform- Using WEB Services WEB SERVICES=FARS Is it safe to use public Wi-Fi? 6 Security challenges when using public Wi-Fi Some things to know about public Wi-Fi hotspots • Unlike your home Wi-Fi access point, most public Wi-Fi hotspots at hotels, restaurants, coffee shops, airports, etc. do not use encrypted communication. • This means that all your data may be sent in clear-text across the wireless network. Anyone with a “sniffer” could then snoop on your connection. • In order to secure their Wi-Fi properly, a business owner would have to issue a password to connect to the hotspot. To be truly secure, this password would be unique to a single person. • Since this isn’t feasible, you need to take other precautions to secure your data when using a public hotspot. Sources: http://www.networkworld.com/article/2904439/wi-fi/is-it-safe-to-use-public-wi-fi-networks.html 7 Case Study: Firesheep browser extension Coder exposed risk to Facebook users at public hotspots • To call attention to glaring security vulnerabilities with both Facebook – and other sites – and public Wi-Fi, a “white hat” hacker developed a Firefox extension that allowed a user to hijack the Facebook account of anyone logged into the same Wi-Fi hotspot. -

Cyber-Conflict Between the United States of America and Russia CSS
CSS CYBER DEFENSE PROJECT Hotspot Analysis: Cyber-conflict between the United States of America and Russia Zürich, June 2017 Version 1 Risk and Resilience Team Center for Security Studies (CSS), ETH Zürich Cyber-conflict between the United States of America and Russia Authors: Marie Baezner, Patrice Robin © 2017 Center for Security Studies (CSS), ETH Zürich Contact: Center for Security Studies Haldeneggsteig 4 ETH Zürich CH-8092 Zurich Switzerland Tel.: +41-44-632 40 25 [email protected] www.css.ethz.ch Analysis prepared by: Center for Security Studies (CSS), ETH Zürich ETH-CSS project management: Tim Prior, Head of the Risk and Resilience Research Group; Myriam Dunn Cavelty, Deputy Head for Research and Teaching; Andreas Wenger, Director of the CSS Disclaimer: The opinions presented in this study exclusively reflect the authors’ views. Please cite as: Baezner, Marie; Robin, Patrice (2017): Hotspot Analysis: Cyber-conflict between the United States of America and Russia, June 2017, Center for Security Studies (CSS), ETH Zürich. 2 Cyber-conflict between the United States of America and Russia Table of Contents 1 Introduction 5 2 Background and chronology 6 3 Description 9 3.1 Tools and techniques 9 3.2 Targets 10 3.3 Attribution and actors 10 4 Effects 11 4.1 Social and internal political effects 11 4.2 Economic effects 13 4.3 Technological effects 13 4.4 International effects 13 5 Consequences 14 5.1 Improvement of cybersecurity 14 5.2 Raising awareness of propaganda and misinformation 15 5.3 Observation of the evolution of relations between the USA and Russia 15 5.4 Promotion of Confidence Building Measures 16 6 Annex 1 17 7 Glossary 18 8 Abbreviations 19 9 Bibliography 19 3 Cyber-conflict between the United States of America and Russia Executive Summary Effects Targets: US State institutions and a political The analysis found that the tensions between the party. -

UC Santa Cruz Electronic Theses and Dissertations
UC Santa Cruz UC Santa Cruz Electronic Theses and Dissertations Title Unbecoming Silicon Valley: Techno Imaginaries and Materialities in Postsocialist Romania Permalink https://escholarship.org/uc/item/0vt9c4bq Author McElroy, Erin Mariel Brownstein Publication Date 2019 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA SANTA CRUZ UNBECOMING SILICON VALLEY: TECHNO IMAGINARIES AND MATERIALITIES IN POSTSOCIALIST ROMANIA A dissertation submitted in partial satisfaction of the requirements for the degree of DOCTOR OF PHILOSOPHY in FEMINIST STUDIES by Erin Mariel Brownstein McElroy June 2019 The Dissertation of Erin McElroy is approved: ________________________________ Professor Neda Atanasoski, Chair ________________________________ Professor Karen Barad ________________________________ Professor Lisa Rofel ________________________________ Professor Megan Moodie ________________________________ Professor Liviu Chelcea ________________________________ Lori Kletzer Vice Provost and Dean of Graduate Studies Copyright © by Erin McElroy 2019 Table of Contents Abstract, iv-v Acknowledgements, vi-xi Introduction: Unbecoming Silicon Valley: Techno Imaginaries and Materialities in Postsocialist Romania, 1-44 Chapter 1: Digital Nomads in Siliconizing Cluj: Material and Allegorical Double Dispossession, 45-90 Chapter 2: Corrupting Techno-normativity in Postsocialist Romania: Queering Code and Computers, 91-127 Chapter 3: The Light Revolution, Blood Gold, and -

Tor and Circumvention: Lessons Learned
Tor and circumvention: Lessons learned Nick Mathewson The Tor Project https://torproject.org/ 1 What is Tor? Online anonymity 1) open source software, 2) network, 3) protocol Community of researchers, developers, users, and relay operators Funding from US DoD, Electronic Frontier Foundation, Voice of America, Google, NLnet, Human Rights Watch, NSF, US State Dept, SIDA, ... 2 The Tor Project, Inc. 501(c)(3) non-profit organization dedicated to the research and development of tools for online anonymity and privacy Not secretly evil. 3 Estimated ~250,000? daily Tor users 4 Anonymity in what sense? “Attacker can’t learn who is talking to whom.” Bob Alice Alice Anonymity network Bob Alice Bob 5 Threat model: what can the attacker do? Alice Anonymity network Bob watch Alice! watch (or be!) Bob! Control part of the network! 6 Anonymity isn't cryptography: Cryptography just protects contents. “Hi, Bob!” “Hi, Bob!” Alice <gibberish> attacker Bob 7 Anonymity isn't just wishful thinking... “You can't prove it was me!” “Promise you won't look!” “Promise you won't remember!” “Promise you won't tell!” “I didn't write my name on it!” “Isn't the Internet already anonymous?” 8 Anonymity serves different interests for different user groups. Anonymity “It's privacy!” Private citizens 9 Anonymity serves different interests for different user groups. Anonymity Businesses “It's network security!” “It's privacy!” Private citizens 10 Anonymity serves different interests for different user groups. “It's traffic-analysis resistance!” Governments Anonymity Businesses “It's network security!” “It's privacy!” Private citizens 11 Anonymity serves different interests for different user groups. -

View Final Report (PDF)
TABLE OF CONTENTS TABLE OF CONTENTS I EXECUTIVE SUMMARY III INTRODUCTION 1 GENESIS OF THE PROJECT 1 RESEARCH QUESTIONS 1 INDUSTRY SITUATION 2 METHODOLOGY 3 GENERAL COMMENTS ON INTERVIEWS 5 APT1 (CHINA) 6 SUMMARY 7 THE GROUP 7 TIMELINE 7 TYPOLOGY OF ATTACKS 9 DISCLOSURE EVENTS 9 APT10 (CHINA) 13 INTRODUCTION 14 THE GROUP 14 TIMELINE 15 TYPOLOGY OF ATTACKS 16 DISCLOSURE EVENTS 18 COBALT (CRIMINAL GROUP) 22 INTRODUCTION 23 THE GROUP 23 TIMELINE 25 TYPOLOGY OF ATTACKS 27 DISCLOSURE EVENTS 30 APT33 (IRAN) 33 INTRODUCTION 34 THE GROUP 34 TIMELINE 35 TYPOLOGY OF ATTACKS 37 DISCLOSURE EVENTS 38 APT34 (IRAN) 41 INTRODUCTION 42 THE GROUP 42 SIPA Capstone 2020 i The Impact of Information Disclosures on APT Operations TIMELINE 43 TYPOLOGY OF ATTACKS 44 DISCLOSURE EVENTS 48 APT38 (NORTH KOREA) 52 INTRODUCTION 53 THE GROUP 53 TIMELINE 55 TYPOLOGY OF ATTACKS 59 DISCLOSURE EVENTS 61 APT28 (RUSSIA) 65 INTRODUCTION 66 THE GROUP 66 TIMELINE 66 TYPOLOGY OF ATTACKS 69 DISCLOSURE EVENTS 71 APT29 (RUSSIA) 74 INTRODUCTION 75 THE GROUP 75 TIMELINE 76 TYPOLOGY OF ATTACKS 79 DISCLOSURE EVENTS 81 COMPARISON AND ANALYSIS 84 DIFFERENCES BETWEEN ACTOR RESPONSE 84 CONTRIBUTING FACTORS TO SIMILARITIES AND DIFFERENCES 86 MEASURING THE SUCCESS OF DISCLOSURES 90 IMPLICATIONS OF OUR RESEARCH 92 FOR PERSISTENT ENGAGEMENT AND FORWARD DEFENSE 92 FOR PRIVATE CYBERSECURITY VENDORS 96 FOR THE FINANCIAL SECTOR 96 ROOM FOR FURTHER RESEARCH 97 ACKNOWLEDGEMENTS 98 ABOUT THE TEAM 99 SIPA Capstone 2020 ii The Impact of Information Disclosures on APT Operations EXECUTIVE SUMMARY This project was completed to fulfill the including the scope of the disclosure and capstone requirement for Columbia Uni- the disclosing actor. -

Distributed Attacks and the Healthcare Industry 01/14/2021
Distributed Attacks and the Healthcare Industry 01/14/2021 Report #: 202101141030 Agenda Image source: CBS News • Overview of distributed attacks • Supply chain attacks • Discussion of SolarWinds attack • Managed Service Provider attacks • Discussion of Blackbaud attack • How to think about distributed attacks • References • Questions Slides Key: Non-Technical: Managerial, strategic and high- level (general audience) Technical: Tactical / IOCs; requiring in-depth knowledge (sysadmins, IRT) 2 Overview: Distributed Attacks What is a distributed attack? Traditional attack = a single compromise impacts a single organization 3 Overview: Distributed Attacks (continued) What is a distributed attack? Distributed attack = a single compromise that impacts multiple organizations Image source: cyber.gc.ca 4 Overview: Distributed Attacks (continued) But what about DDoS (distributed denial of service) attacks? Not a distributed attack in the context of the presentation, since it only targets one organization! Image source: F5 Networks We will be discussing two types of distributed attacks in this presentation, both of which present a significant threat to healthcare: supply chain attacks and managed service provider attacks. We will be analyzing two cases: the SolarWinds attack (supply chain), as well as the Blackbaud breach (managed service provider). This presentation is based on the best information available at the time of delivery – new details will emerge. 5 Supply Chain Attacks Image source: Slidebazaar What is a supply chain? • A supply chain -

Anatomy of Data Breaches and Its Impact on Security
International Journal of Science and Research (IJSR) ISSN (Online): 2319-7064 Index Copernicus Value (2013): 6.14 | Impact Factor (2013): 4.438 Anatomy of Data Breaches and Its Impact on Security Anshu1, Monika Sharma2 1M.Tech Scholar, Computer Science Department, TIT & S, Bhiwani, India 2Assistant Professor, Information Technology Department, TIT & S, Bhiwani, India Abstract: In cloud computing, the word cloud is used as a metaphor for "the Internet," so the phrase cloud computing means "a type of Internet-based computing," where different services - such as servers, storage and applications -- are delivered to an organization's computers and devices through the Internet [14]. Every user access cloud services through internet without knowing the security aspects. Today security threats are increasing rapidly and data breach is top of them. Breach in the security of any component in the cloud can be both disaster for the organization and the provider. In this research paper we focus on main security issue in cloud like data breach, different forms of data breaches and how it occurs in cloud. It also explore where major breaches occur in cloud in past years. Keywords: cloud, data breaches, security 1. Data Breaches two categories i.e. accidental breach or intentional breach The term data breach means when an unauthorized user or a) Accidental breach: also called as employee error when hacker or an attacker attacks an authorized data, access or an employee by mistake sends data to wrong receipts, retrieves it by an individual or service without the and by not understanding security protocols and permission. A data breach results in loss of sensitive, procedures. -

Tor: the Second-Generation Onion Router (2014 DRAFT V1)
Tor: The Second-Generation Onion Router (2014 DRAFT v1) Roger Dingledine Nick Mathewson Steven Murdoch The Free Haven Project The Free Haven Project Computer Laboratory [email protected] [email protected] University of Cambridge [email protected] Paul Syverson Naval Research Lab [email protected] Abstract Perfect forward secrecy: In the original Onion Routing We present Tor, a circuit-based low-latency anonymous com- design, a single hostile node could record traffic and later munication service. This Onion Routing system addresses compromise successive nodes in the circuit and force them limitations in the earlier design by adding perfect forward se- to decrypt it. Rather than using a single multiply encrypted crecy, congestion control, directory servers, integrity check- data structure (an onion) to lay each circuit, Tor now uses an ing, configurable exit policies, anticensorship features, guard incremental or telescoping path-building design, where the nodes, application- and user-selectable stream isolation, and a initiator negotiates session keys with each successive hop in practical design for location-hidden services via rendezvous the circuit. Once these keys are deleted, subsequently com- points. Tor is deployed on the real-world Internet, requires promised nodes cannot decrypt old traffic. As a side benefit, no special privileges or kernel modifications, requires little onion replay detection is no longer necessary, and the process synchronization or coordination between nodes, and provides of building circuits is more reliable, since the initiator knows a reasonable tradeoff between anonymity, usability, and ef- when a hop fails and can then try extending to a new node. -

Reporting, and General Mentions Seem to Be in Decline
CYBER THREAT ANALYSIS Return to Normalcy: False Flags and the Decline of International Hacktivism By Insikt Group® CTA-2019-0821 CYBER THREAT ANALYSIS Groups with the trappings of hacktivism have recently dumped Russian and Iranian state security organization records online, although neither have proclaimed themselves to be hacktivists. In addition, hacktivism has taken a back seat in news reporting, and general mentions seem to be in decline. Insikt Group utilized the Recorded FutureⓇ Platform and reports of historical hacktivism events to analyze the shifting targets and players in the hacktivism space. The target audience of this research includes security practitioners whose enterprises may be targets for hacktivism. Executive Summary Hacktivism often brings to mind a loose collective of individuals globally that band together to achieve a common goal. However, Insikt Group research demonstrates that this is a misleading assumption; the hacktivist landscape has consistently included actors reacting to regional events, and has also involved states operating under the guise of hacktivism to achieve geopolitical goals. In the last 10 years, the number of large-scale, international hacking operations most commonly associated with hacktivism has risen astronomically, only to fall off just as dramatically after 2015 and 2016. This constitutes a return to normalcy, in which hacktivist groups are usually small sets of regional actors targeting specific organizations to protest regional events, or nation-state groups operating under the guise of hacktivism. Attack vectors used by hacktivist groups have remained largely consistent from 2010 to 2019, and tooling has assisted actors to conduct larger-scale attacks. However, company defenses have also become significantly better in the last decade, which has likely contributed to the decline in successful hacktivist operations. -

Darpa Starts Sleuthing out Disloyal Troops
UNCLASSIFIED (U) FBI Tampa Division CI Strategic Partnership Newsletter JANUARY 2012 (U) Administrative Note: This product reflects the views of the FBI- Tampa Division and has not been vetted by FBI Headquarters. (U) Handling notice: Although UNCLASSIFIED, this information is property of the FBI and may be distributed only to members of organizations receiving this bulletin, or to cleared defense contractors. Precautions should be taken to ensure this information is stored and/or destroyed in a manner that precludes unauthorized access. 10 JAN 2012 (U) The FBI Tampa Division Counterintelligence Strategic Partnership Newsletter provides a summary of previously reported US government press releases, publications, and news articles from wire services and news organizations relating to counterintelligence, cyber and terrorism threats. The information in this bulletin represents the views and opinions of the cited sources for each article, and the analyst comment is intended only to highlight items of interest to organizations in Florida. This bulletin is provided solely to inform our Domain partners of news items of interest, and does not represent FBI information. In the JANUARY 2012 Issue: Article Title Page NATIONAL SECURITY THREAT NEWS FROM GOVERNMENT AGENCIES: American Jihadist Terrorism: Combating a Complex Threat p. 2 Authorities Uncover Increasing Number of United States-Based Terror Plots p. 3 Chinese Counterfeit COTS Create Chaos For The DoD p. 4 DHS Releases Cyber Strategy Framework p. 6 COUNTERINTELLIGENCE/ECONOMIC ESPIONAGE THREAT ITEMS FROM THE PRESS: United States Homes In on China Spying p. 6 Opinion: China‟s Spies Are Catching Up p. 8 Canadian Politician‟s Chinese Crush Likely „Sexpionage,‟ Former Spies Say p.