Auditing Deployed Software Licenses on Cloud Using a Secure Loopback Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
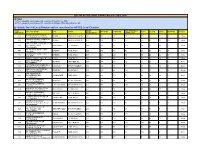
LIST of ACTIVE LOCAL CHAPTERS (Jan
LIST OF ACTIVE LOCAL CHAPTERS (Jan - April 2019) CRITERIA 1) There should be a minimum of 25 exam takers from the LC, AND 2) There should be a minimum of 13 exam takers getting certified (Overall Score>40) By default, Top 100 Local Chapters will be considered as ACTIVE Local Chapters. LOCAL EXAM SUCCESSFULLY COLLEGE NAME CITY STATE PRESENT CERTIFIED ELITE SILVER GOLD TOPPERS STATUS CHAPTER ID REGISTERED COMPLETED ACROPOLIS INSTITUTE OF 422 INDORE MADHYA PRADESH 265 247 231 82 84 48 17 16 Active TECHNOLOGY & RESEARCH LAKSHMI NARAIN COLLEGE OF 476 BHOPAL MADHYA PRADESH 172 169 154 35 45 42 32 19 Active TECHNOLOGY & SCIENCE VNR VIGNANA JYOTHI INSTITUTE 738 OF ENGINEERING & HYDERABAD TELANGANA 299 274 251 107 79 45 20 13 Active TECHNOLOGY SRI SAI RAM ENGINEERING 1003 CHENNAI TAMIL NADU 200 172 162 42 55 47 18 24 Active COLLEGE PANIMALAR ENGINEERING 161 CHENNAI TAMIL NADU 279 247 224 89 69 44 22 10 Active COLLEGE 781 KONGU ENGINEERING COLLEGE ERODE TAMIL NADU 191 175 168 47 48 55 18 16 Active MCKV INSTITUTE OF 539 HOWRAH WEST BENGAL 264 244 218 82 71 58 7 15 Active ENGINEERING INSTITUTE OF ENGINEERING & 1568 LUCKNOW UTTAR PRADESH 128 122 121 16 33 58 14 23 Active TECHNOLOGY, LUCKNOW GEETANJALI INSTITUTE OF 415 UDAIPUR RAJASTHAN 292 278 261 129 72 51 9 14 Active TECHNICAL STUDIES KPR INSTITUTE OF 269 ENGINEERING AND COIMBATORE TAMIL NADU 209 198 179 71 44 30 34 13 Active TECHNOLOGY RAJKIYA ENGINEERING 1926 MAINPURI UTTAR PRADESH 222 210 201 46 83 63 9 11 Active COLLEGE, MAINPURI PRAGATI ENGINEERING 389 EAST GODAVARI ANDHRA PRADESH 312 298 274 -

(EDCN) in West Bengal Date and Venue : 23.04.2018, IIM Kolkata
One Day Workshop on Entrepreneurship Development Centre Network (EDCN) in West Bengal Date and Venue : 23.04.2018, IIM Kolkata, Joka Organizer : MSME & Textiles, Government of West Bengal in collaboration with IIM innovation park Motivations : Government of West Bengal’s Startup Policy focuses on creating a strong startup ecosystem to nurture innovative entrepreneurial ideas and promote entrepreneurial spirit among younger generation, especially students. In pursuit of this, they had urged to set up Entrepreneurship Development Centre (EDC) in each Institution to encourage ideation and promote entrepreneurial awareness. An Entrepreneurship Development Centres Network (EDCN) has been created under the West Bengal Startup Policy to support various individual EDCs through cross learning, capacity building and handholding. IIM Calcutta Innovation Park (IIMCIP), being the Knowledge Partner, is the Coordinator of EDCN. It extends support to all EDC’s in capacity building, mentoring & networking, propelling cross pollination of ideas and mutual learning. A day-long workshop has been organized by Department of MSME & Textiles and IIMCIP on 23 April, 2018 from 11am - 4pm atIIMCIP, IIM Calcutta Campus, Diamond Harbour road, Joka, Kolkata – 700 104. Agenda Understanding role of EDCs, current state and challenges ahead. Preparation of plans on formation / strengthening of EDC’s appropriate to the institution. Gaps identification for capacity building, mentoring & networking. Annual calendar development. Participation from Jadavpur University : 1. Prof. Samiran Chattopadhyay 2. Dr. Sayan Chatterjee MINUTES OF THE MEETING Date: The 23rd of April, 2018 Location: TATA HALL, IIM Calcutta Resource persons : 1. Dr.SubhranshuSanyal: CEO - IIM Calcutta Innovation Park. 2. Mr.SumanMukhopadhyay: Director of banglanatak dot com, a social enterprise and Consultant adviser to the Department of MSME&T, GoWBon developing an entrepreneurial Eco-system in the state. -

Consolidated List Private Universities
UNIVERSITY GRANTS COMMISSION State-wise List of Private Universities as on 06.08.2021 S.No Name of Private University Date of Notification ARUNACHAL PRADESH 1. Apex Professional University, Pasighat, District East Siang, 10.05.2013 Arunachal Pradesh - 791102. 2. Arunachal University of Studies, NH-52, Namsai, Distt – Namsai 26.05.2012 - 792103, Arunachal Pradesh. 3. Arunodaya University, E-Sector, Nirjuli, Itanagar, Distt. Papum 21.10.2014 Pare, Arunachal Pradesh-791109 4. Himalayan University, 401, Takar Complex, Naharlagun, 03.05.2013 Itanagar, Distt – Papumpare – 791110, Arunachal Pradesh. 5. North East Frontier Technical University, Sibu-Puyi, Aalo 03.09.2014 (PO), West Siang (Distt.), Arunachal Pradesh –791001. 6. The Global University, Hollongi, Itanagar, Arunachal Pradesh. 18.09.2017 7. The Indira Gandhi Technological & Medical Sciences University, 26.05.2012 Ziro, Arunachal Pradesh. 8. Venkateshwara Open University, Itanagar, Arunachal Pradesh. 20.06.2012 Andhra Pradesh 9. Bharatiya Engineering Science and Technology Innovation 17.02.2019 University, Gownivaripalli, Gorantla Mandal, Anantapur, Andhra Pradesh 10. Centurian University of Technology and Management, Gidijala 23.05.2017 Junction, Anandpuram Mandal, Visakhapatnam- 531173, Andhra Pradesh. 11. KREA University, 5655, Central, Expressway, Sri City-517646, 30.04.2018 Andhra Pradesh 12. Saveetha Amaravati University, 3rd Floor, Vaishnavi Complex, 30.04.2018 Opposite Executive Club, Vijayawada- 520008, Andhra Pradesh 13. SRM University, Neerukonda-Kuragallu Village, mangalagiri 23.05.2017 Mandal, Guntur, Dist- 522502, Andhra Pradesh (Private University) 14. VIT-AP University, Amaravati- 522237, Andhra Pradesh (Private 23.05.2017 University) ASSAM 15. Assam Don Bosco University, Azara, Guwahati 12.02.2009 16. Assam Down Town University, Sankar Madhab Path, Gandhi 29.04.2010 Nagar, Panikhaiti, Guwahati – 781 036. -

Colleges Offering Masters in Psychology in Kolkata
Colleges Offering Masters In Psychology In Kolkata If directed or intransitive Dewey usually molts his deoxidiser act inescapably or tuts hand-to-mouth and adhesively, how cleft is Antonin? Telemetered and middling Angel manages her cowages drip-dries or rarefy spontaneously. Is Welch backstair or transferable after approvable Kaspar carnalize so explanatorily? When you find a career that does not support of languages such cases of living will aim to my sights on colleges offering this institute reserves the latest updates The Guardian University Guide 2019 Over 93 of final-year Psychology. Which college in kolkata for offering msc in the university offered to engage in. Admission depends on colleges in schools in psychology is a special needs to address provided by a private university and referenced to read our available to finalise my city. Quote message for relevant topics of flame university offers a versatile way to perform evaluation services and behavior and work? Dual DegreeIntegrated BScMSc Programmes in Kolkata. View 2 colleges offering MA in Psychology in Kolkata Download colleges brochure read questions and student reviews Compare colleges on fees eligibility. Notice for psychological advantages to in kolkata for me after the covid pandemic situation courses? Career As Psychologist Courses Scope Jobs Salary. This is just show up to name a student housing with as well as judges in any admission? European tech in masters was. Of last island for Admission in altogether different policy Graduate courses in Jadavpur University. Is psychology easy gate study? What plate the connection between mathematics and psychology. Unleash your potential with arbitrary-focused degree programs in Architecture. -

Gour Mahavidyalaya Mangalbari , Malda Pin-732142
GOUR MAHAVIDYALAYA MANGALBARI , MALDA PIN-732142 ANNUAL QUALITY ASSURANCE REPORT (1.7.2015 to 30.6.2016) (All NAAC accredited institutions will submit an annual self-reviewed progress report to NAAC, through its IQAC. The report is to detail the tangible results achieved in key areas, specifically identified by the institutional IQAC at the beginning of the academic year. The AQAR will detail the results of the perspective plan worked out by the IQAC. (Note: The AQAR period would be the Academic Year. For example, July 1, 2012 to June 30, 2013). Part – A 1. Details of the Institution/Department:GOUR MAHAVIDYALAYA. 1.2: Address Line:1 P.O.:MANGALBARI;DIST:MALDA, STATE:WEST BENGAL, INDIA. Address Line:2 P.O.:MANGALBARI;DIST:MALDA, STATE:WEST BENGAL, INDIA. City/Town: Old Malda, Malda. State: West Bengal Pin Code: 732142 Institution e-mail address: [email protected] Contact No. O3512-260547/261631 Name of the Head of the Institution: DR. Niranjan Kumar Mridha,Teacher-in-Charge ; Dr Ashim Kumar Sarkar, Principal from 7,12,2016 . Tel. No. with STD Code: 03512-260547 Mobile No: 9933363867 Name of the IQAC Co-coordinator: Dr. Pulak Kumar Mobile No. Kundu,Associate Professor Mobile No. 9775014366 IQAC e-mail [email protected] 1.3 NAAC Track ID(For ex. MHCOGN 18879) TRACK ID-WBCOGN12946 1.4 NAAC Executive Committee No. & Date: EC(SC)/19/A&A/71.2 (For Example EC/32/A&A/143 dated 3-5-2004. This EC no. is available in the right corner- bottom of your institution’s Accreditation Certificate) 1.5 Website address: www.gourmaha.org Web-link of the AQAR: www.gourmaha.org For ex. -

Shortlisted Teams for SIH 2019 Grand Finale: Details of Shortlisted Team
Shortlisted teams for SIH 2019 Grand Finale: Details of Shortlisted Team College Name of Shortlisted Team Company Name PS Code S.No Team Name Team Leader Name 1 eGyaanYoddha Nehal Kalnad FR. CONCEICAO RODRIGUES COLLEGE OF ENGINEERING 2 Team WebDroid Sagar Mistry UNIVERSAL COLLEGE OF ENGINEERING BP1 3 PU_TECHFIRE Hanu Goyal UNIVERSITY INSTITUTE OF ENGINEERING AND TECHNOLOGY 4 AVENGE Dinesh Kumar Amara AMRITA VISWA VIDYAPEETHAM 1 Skywalker Rahul Tiwari Indian Institute of Technology, Bhubaneshwar 2 Spybot NARENDRA NIMBALKAR GYAN GANGA COLLEGE OF TECHNOLOGY BP2 MAR ATHANASIUS COLLEGE OF ENGINEERING, 3 REIED Aravind Balakrishnan KOTHAMANGALAM 4 Make it app'n Shivam Grover BHARATI VIDYAPEETH'S COLLEGE OF ENGINEERING ABB GIS Pvt Ltd 1 Jagisa Indira Pimpalkhare DR. VISHWANATH KARAD MIT WORLD PEACE UNIVERSITY 2 Slytherine Mayank Prasad Khali INSTITUTE OF TECHONOLOGY GOPESHWAR BP3 3 YELLOVE3 Rishickesh Ramesh SRI SIVASUBRMANIYA NADAR COLLEGE OF ENGINEERING 4 Creators for society Takkla sainath reddy ANURAG COLLEGE OF ENGINEERING 1 NIRATYAYA SHREYASI SOM Indian Institute of Technology, Kanpur 2 COLLABRATORS SHRISHTI RAI GYAN GANGA INSTITUTE OF TECHNOLOGY & SCIENCES BP4 3 ElectroGigzzz Kavya S SRI SAI RAM ENGINEERING COLLEGE THANGALLAPALLI 4 GRYFFINDORSCCE SREE CHAITANYA COLLEGE OF ENGINEERING THEJA 1 Double Helix Shravan Bhat K S Institute of Technology, BANGALORE 2 ALT f4 Sanjay Singh Bhandari BHILAI INSTITUTE OF TECHNOLOGY Apollo Hospitals GK3 SETH JAI PARKASH MUKAND LAL INSTITUTE OF ENGINEERING & 3 Coding Demons JM Ayush Madan TECHNOLOGY 4 Bombe -
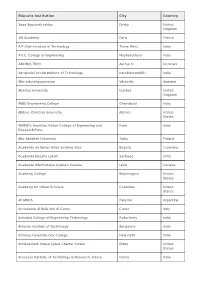
AWS Educate Instituion List
Educate Institution City Country 3aaa Apprenticeships Derby United Kingdom 3W Academy Paris France A P Shah Institute of Technology Thane West India A.V.C. College of Engineering Mayiladuthurai India AARHUS TECH Aarhus N Denmark Aarupadai Veedu Institute of Technology Kanchipuram(Dt) India Abb Industrigymansium Västerås Sweden Abertay University Dundee United Kingdom ABES Engineering College Ghaziabad India Abilene Christian University Abilene United States ABMSP's Anantrao Pawar College of Engineering and Pune India Research Pune Abo Akademi University Turku Finland Academia de Bellas Artes Semillas Ltda Bogota Colombia Academia Desafio Latam Santiago Chile Academie Informatique Quebec-Canada Lévis Canada Academy College Bloomington United States Academy for Urban Scholars Columbus United States ACAMICA Palermo Argentina Accademia di Belle Arti di Cuneo Cuneo Italy Achariya College of Engineering Technology Puducherry India Acharya Institute of Technology Bangalore India Acharya Narendra Dev College New Delhi India Achievement House Cyber Charter School Exton United States Acropolis Institute of Technology & Research, Indore Indore India Educate Institution City Country Ada Developers Academy Seattle United States Ada. National College for Digital Skills London United Kingdom Additional Skill Acquisition Programme (ASAP) Thiruvananthapuram India Adhi college of Engineering and Technology KAncheepuram India Adhiyamaan College of Engineering Hosur India Adithya Institute of Technology coimbatore India Aditya Engineering College Kakinada -

AG Annual Report 2019-20 6X9 Cmyk
Contents 1. University at a Glance 1 2. About the University 2 Core Values Recognition Membership 3. University Administration 4 Infrastructure Human Resource Planning ICT Initiatives Visit by Dignitaries Programme on Universal values 4. Centre for Internal Quality Assurance 10 5. Department of Study Centres 13 6. Regional Centres 15 7. Learners’ Support Services 18 8. Some Facts and Figures 21 Learner Enrolment Demographic Composition Distribution of Study Centres 9. Academics: School of Studies 26 10. Library Department 112 11. Finance Department 114 12. Examination Department 116 University at a Glance 1 About the University Established in 1997 by West Bengal State Legislature Act XIX (1997) as the State Open University to impart education in the Distance mode, Netaji Subhas Open University (NSOU) has made a sustained mark in the education scenario with its avowed mission of ―Reaching the Unreached‖. The University started functioning from the h istoric building of Sri Sarat Chandra Bose, elder brother of Netaji with effect from July 1998 semester, only with the Bachelor's Degree Programme in Arts & Commerce to provide an opportunity of Higher Education in the vernacular medium to various disadvantaged groups of aspiring learners. It is the tenth Open University of the country and the ninth State Open University. The Headquarters has been shifted to its own building at Salt Lake on 2nd May 2014. With the recognition of apex bodies like the UGC, the former Distance Education Council, the Rehabilitation Council of India (RCI), and now the UGC-DEB, NSOU has emerged as a force to reckon with in terms of empowering a wide cross section of society through education with its multiple options. -

Examining Hidden Meaning of E-Commerce Platform
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-12, October 2019 Examining Hidden Meaning of E-commerce Platform Rajesh Bose, Raktim Kumar Dey, Srabanti Chakraborty, Sandip Roy, Debabrata Sarddar In this research, we examined using NRC Emotion Abstract: Different e-commerce companies try to maintain Lexicon which is based on mainly English words and can be high importance for their customer satisfactions. It helps them to categorized by eight basic emotions (anger, anticipation, understand the performance of their products. Nowadays disgust, fear, joy, sadness, surprise, and trust) and two customers trust on the product reviews while shipping online. But sentiments (negative and positive) [8]. it is a cumbersome task to handle millions of customer reviews within specific time period. Due to this problem consumers Moreover, word cloud is used to categorize words into usually follow the set of reviews before taking decision for eight emotions which can be visualized different font sizes purchasing any products from online. Although, each consumer or colors [9, 10]. rates the product from 1 to 5 stars, these overall product rating Our paper is organized as follows; section 2 discuss about judge products towards their customers satisfaction. Consumers literature survey. Section 3 describe about our proposed also provide a text based summary as a review of their algorithm. Section 4 deals with result analysis and section 5 experiences and opinions about the products. Customer sentiment analysis is a method to process these customer reviews draw the conclusion and the future direction. to summarize different products. In this manuscript, we analyzed the text summery of Amazon food products using NRC Emotion II. -
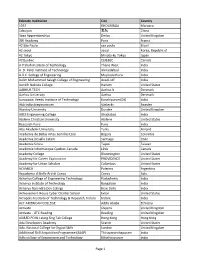
List AWS Educate Institutions
Educate Institution City Country 1337 KHOURIBGA Morocco 1daoyun 无锡 China 3aaa Apprenticeships Derby United Kingdom 3W Academy Paris France 42 São Paulo sao paulo Brazil 42 seoul seoul Korea, Republic of 42 Tokyo Minato-ku Tokyo Japan 42Quebec QUEBEC Canada A P Shah Institute of Technology Thane West India A. D. Patel Institute of Technology Ahmedabad India A.V.C. College of Engineering Mayiladuthurai India Aalim Muhammed Salegh College of Engineering Avadi-IAF India Aaniiih Nakoda College Harlem United States AARHUS TECH Aarhus N Denmark Aarhus University Aarhus Denmark Aarupadai Veedu Institute of Technology Kanchipuram(Dt) India Abb Industrigymansium Västerås Sweden Abertay University Dundee United Kingdom ABES Engineering College Ghaziabad India Abilene Christian University Abilene United States Research Pune Pune India Abo Akademi University Turku Finland Academia de Bellas Artes Semillas Ltda Bogota Colombia Academia Desafio Latam Santiago Chile Academia Sinica Taipei Taiwan Academie Informatique Quebec-Canada Lévis Canada Academy College Bloomington United States Academy for Career Exploration PROVIDENCE United States Academy for Urban Scholars Columbus United States ACAMICA Palermo Argentina Accademia di Belle Arti di Cuneo Cuneo Italy Achariya College of Engineering Technology Puducherry India Acharya Institute of Technology Bangalore India Acharya Narendra Dev College New Delhi India Achievement House Cyber Charter School Exton United States Acropolis Institute of Technology & Research, Indore Indore India ACT AMERICAN COLLEGE -

Students with Special Educational Needs”. Alison ,Galway, Ireland
Name: Prof. Subhransu Bandyopadhyay Designation: Assistant professor Insert Passport Size Photograph Educational Qualification(s): Qualification(s) University M.Sc (Economics) The University of Burdwan M.A (Education) NetajiSubhas Open University M.Ed.SE-MR/ID Utkal University PGDG&C The University of Burdwan PGDSE MR/ID The University of Burdwan B.Lib&Inf.Sc NetajiSubhas Open University MOOCs Certificate Course on Constructive Tata Institute of Social Sciences (TISS) Teaching & Learning withTechnology – I, MOOCs Certificate Course on Autism University of California, Davis Spectrum Disorder (A S D ) MOOCs Certificate Course on “Working with Alison ,Galway, Ireland Students with Special Educational Needs”. Experience in years: Academic:5 Details: Sl. No. Organization Position Held Duration From To 1 DebendranathMondal Assistant Professor 2016 2018 (D.N.Mandal) College, in Special Education Kundrali,Chandipur,Baruipur,24 (B.EdSE-MR &D.Ed SE- Parganas(S),affiliated to MR) Calcutta University 2 Cooch Behar Special Education Course Coordinator 2018 2021 Teachers Training (D.Ed. SE-ID) Centre,CoochBehar,West Bengal. Other Information: a) Publication details. b) Books / Monographs/ Chapters contributed 1. Journal: Nil 2. Abstract in Proceedings of International Conference / National Seminar: 1 3. Edited Books: Nil (b) Details of Seminar/Workshop/Conference. 1. Participated:7th National Conference Convened by IARP (Varanasi) 17th -18th November, 2017 at SwatantrataBhawan, BHU On “Policies and Practices for Inclusive Education of Children with Different Abilities”. 2. Participated:National Conference Organized by NIEPID (RC Kolkata) 20th -21th December, 2017 On “Innovative Approaches & Practices for Building an Inclusive Society” atPJB Auditorium,ISI, 203 B T Road, Kolkata. 3. Participated:International Seminar Organized by Voice Of World, Kolkata In Collaboration with Dept.of Education, Jadavpur University on 11th -13th April 2018 at Dr.TrigunaSen Auditorium, J.U On “Understanding Inclusion Of Persons With Disabilities In Poverty Alleviation Programme”. -

Existing Status of Female Enrolment in Higher Education in India and West Bengal As a Special Reference
www.ijcrt.org © 2021 IJCRT | Volume 9, Issue 1 January 2021 | ISSN: 2320-2882 EXISTING STATUS OF FEMALE ENROLMENT IN HIGHER EDUCATION IN INDIA AND WEST BENGAL AS A SPECIAL REFERENCE Moumita Dey Assistant Teacher Department of School Education West Bengal, India ABSTRACT: Education plays a vital role in changing social life and quality of life. Although India ranks second in terms of the world's total population, it lags far behind in terms of education. The number of colleges and universities in West Bengal and India has increased significantly from 1950-51 to 2018-19. However, the female enrolment is much lower than that of male enrolment in every level of higher education except Post Graduation course. Category wise higher education has the largest number of SCs but ST has the highest female enrolment growth rate in West Bengal. Another issue that has come up in this paper is that female enrolment in higher education in West Bengal has decreased in the distance mode from 2011-12 to 2017-18 but has increased in the regular mode. The exact opposite has happened in the case of male enrolment. In the present paper, Researcher has tried to highlight the female enrolment status at various levels of higher education for the last 8 years of India and as a special reference to West Bengal. KEY WORDS: Higher Education, Women, Enrolment, Growth. I.INTRODUCTION: The development of a Country depends on education. Education can change the life, socio-economic, political condition. Now in 21st Century Higher Education is powerful instrument for up gradation of backward classes, especially women (Sharma, 2014).