A Survey on Ethereum Systems Security: Vulnerabilities, Attacks and Defenses Huashan Chen, Marcus Pendleton, Laurent Njilla, and Shouhuai Xu
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examining the Lightning Network on a Protocol Level
Examining the Lightning network on a protocol level Rene Pickhardt (Data Science Consultant) https://www.rene-pickhardt.de & https://twitter.com/renepickhardt München 19.7.2018 I've been told I should start any talk with something everybody in the audience should know A standard Bitcoin Transaction has 6 data fields ( The following is a brief summary of https://en.bitcoin.it/wiki/Transaction#Input ) ● Version number (4 Bytes) ● In-Counter (1-9 Bytes) ● List of inputs (depending on the Value of <In-Counter>) ● Out-Counter (1-9 Bytes) ● List of Outputs (depending on the Value of <Out-Counter>) ● Lock_time (4 Bytes) ( Bitcoin Transaction with 3 inputs and 2 outputs Data consists mainly of executable scripts! A chain of Bitcoin Transactions with 3 UTXO ● Outputs are references by the inputs ● The Script in the output defines how the transaction can be spent ● Owning Bitcoins means being able to spend the output of an unspent transaction ○ Provide an input script ○ Concatenate it with with some outputscript of an unspent transaction ○ The combined Script needs to evaluate to True Spending a Pay-to-PubkeyHash (standard TX) ● ScriptPubKey (aka the Output Script) ○ OP_DUP OP_HASH160 <pubKeyHash> OP_EQUALVERIFY OP_CHECKSIG ● ScriptSig: (aka the Input Script) ○ <sig> <pubKey> ● Explainations ○ OP_CODES are the instructions of the script language within Bitcoin ○ <data> is depicted like html tags with lesser than and greater than signs ○ The complete script is concatenated as Input || Output and then being executed on a Stack machine <sig> <pubKey> -

Pdp11-40.Pdf
processor handbook digital equipment corporation Copyright© 1972, by Digital Equipment Corporation DEC, PDP, UNIBUS are registered trademarks of Digital Equipment Corporation. ii TABLE OF CONTENTS CHAPTER 1 INTRODUCTION 1·1 1.1 GENERAL ............................................. 1·1 1.2 GENERAL CHARACTERISTICS . 1·2 1.2.1 The UNIBUS ..... 1·2 1.2.2 Central Processor 1·3 1.2.3 Memories ........... 1·5 1.2.4 Floating Point ... 1·5 1.2.5 Memory Management .............................. .. 1·5 1.3 PERIPHERALS/OPTIONS ......................................... 1·5 1.3.1 1/0 Devices .......... .................................. 1·6 1.3.2 Storage Devices ...................................... .. 1·6 1.3.3 Bus Options .............................................. 1·6 1.4 SOFTWARE ..... .... ........................................... ............. 1·6 1.4.1 Paper Tape Software .......................................... 1·7 1.4.2 Disk Operating System Software ........................ 1·7 1.4.3 Higher Level Languages ................................... .. 1·7 1.5 NUMBER SYSTEMS ..................................... 1-7 CHAPTER 2 SYSTEM ARCHITECTURE. 2-1 2.1 SYSTEM DEFINITION .............. 2·1 2.2 UNIBUS ......................................... 2-1 2.2.1 Bidirectional Lines ...... 2-1 2.2.2 Master-Slave Relation .. 2-2 2.2.3 Interlocked Communication 2-2 2.3 CENTRAL PROCESSOR .......... 2-2 2.3.1 General Registers ... 2-3 2.3.2 Processor Status Word ....... 2-4 2.3.3 Stack Limit Register 2-5 2.4 EXTENDED INSTRUCTION SET & FLOATING POINT .. 2-5 2.5 CORE MEMORY . .... 2-6 2.6 AUTOMATIC PRIORITY INTERRUPTS .... 2-7 2.6.1 Using the Interrupts . 2-9 2.6.2 Interrupt Procedure 2-9 2.6.3 Interrupt Servicing ............ .. 2-10 2.7 PROCESSOR TRAPS ............ 2-10 2.7.1 Power Failure .............. -

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

White Paper of Bitcoin Ultimatum Introduction
White Paper of Bitcoin Ultimatum Introduction 1. Problematic of the Blockchain 4. Bitcoin Ultimatum Architecture industry 4.1. Network working principle 1.1. Transactions Anonymity 4.1.1. Main Transaction Types 1.2. Insufficient Development of Key Aspects of the 4.1.1.1. Public transactions Technology 4.1.1.2. Private transactions 1.3. Centralization 4.1.2. Masternode Network 1.4. Mining pools and commission manipulation 4.2. How to become a validator or masternode in 1.5. Decrease in Transaction Speeds BTCU 4.3. Network Scaling Principle 2. BTCU main solutions and concepts 4.4. Masternodes and Validators Ranking System 4.5. Smart Contracts 2.1. Consensus algorithm basis 4.6. Anonymization principle 2.2. Leasing and Staking 4.7. Staking and Leasing 2.3. Projects tokenization and DeFi 4.7.1. Staking 2.4. Transactions Privacy 4.7.2. Leasing 2.5. Atomic Swaps 4.7.2 Multileasing 4.8. BTCU Technical Specifications 3. Executive Summary 4.8.1. Project Stack 4.8.2. Private key generation algorithm 5. Bitcoin Ultimatum Economy 5.1. Initial Supply and Airdrop 5.2. Leasing Economy 5.3. Masternodes and Validators Commission 5.4. Transactions Fee 6. Project Roadmap 7. Legal Introduction The cryptocurrency market is inextricably tied to the blockchain – its fundamental and underlying technology. The modern market is brimming with an abundance of blockchain protocols, algorithms, and concepts, all of which have fostered the development of a wide variety of services and applications. The modern blockchain market offers users an alternative to both established financial systems and ecosystems/infrastructures of applications and services. -

Embedded C Programming I (Ecprogrami)
To our customers, Old Company Name in Catalogs and Other Documents On April 1st, 2010, NEC Electronics Corporation merged with Renesas Technology Corporation, and Renesas Electronics Corporation took over all the business of both companies. Therefore, although the old company name remains in this document, it is a valid Renesas Electronics document. We appreciate your understanding. Renesas Electronics website: http://www.renesas.com April 1st, 2010 Renesas Electronics Corporation Issued by: Renesas Electronics Corporation (http://www.renesas.com) Send any inquiries to http://www.renesas.com/inquiry. Notice 1. All information included in this document is current as of the date this document is issued. Such information, however, is subject to change without any prior notice. Before purchasing or using any Renesas Electronics products listed herein, please confirm the latest product information with a Renesas Electronics sales office. Also, please pay regular and careful attention to additional and different information to be disclosed by Renesas Electronics such as that disclosed through our website. 2. Renesas Electronics does not assume any liability for infringement of patents, copyrights, or other intellectual property rights of third parties by or arising from the use of Renesas Electronics products or technical information described in this document. No license, express, implied or otherwise, is granted hereby under any patents, copyrights or other intellectual property rights of Renesas Electronics or others. 3. You should not alter, modify, copy, or otherwise misappropriate any Renesas Electronics product, whether in whole or in part. 4. Descriptions of circuits, software and other related information in this document are provided only to illustrate the operation of semiconductor products and application examples. -

Deviant Decentralized Exchange
DDEEVVXX Deviant Decentralized Exchange A hybrid exchange leveraging Smartcoins on the Bitshares (BTS) blockchain. CONTENTS 03 What is the current landscape for trading crypto assets? 05 Centralized Exchanges 08 Decentralized Exchanges 11 Hybrid Exchanges 13 DEVX Platform 14 Platform Overview 16 DEVX Smart Coin 17 DEVX off-chain engine - The DEVX Transient Protocol (DEVTP) 19 Trading Process 25 What is the status of development / roadmap for these innovations? 26 DEVX Team 03 Crypto assets are here to stay. According to Apple co-founder Steve Wozniak, Bitcoin and WHAT IS THE blockchain will be the next major IT revolution, and will achieve full CURRENT potential in a decade. According to LANDSCAPE FOR Paypal co-founder Peter Thiel, Bitcoin is the next Digital Gold. TRADING CRYPTO Since Bitcoin’s release in 2009, 1,622 altcoin variants have been issued. ASSETS? 2018 has already broken all records with 345 Initial Coin Offerings, and over US$ 7.7 billion of capital raised. DEVX the next revolution 04 Growth in the number of crypto assets has also driven an increase in crypto asset trading, in order to satisfy the requirements of the increasingly numerous universe of holders, investors, arbitrageurs, market makers, speculators and hedgers. There are presently more than 500 crypto asset exchanges to bring together buyers and sellers, where crypto assets are traded for either different digital currencies, or for other assets such as conventional fiat money. These exchanges operate mostly outside Western countries, and range from fully-online platforms to bricks-and-mortar businesses. Currently, almost two thirds of all daily global crypto asset trading volume results from activity on just ten of these exchanges. -

Operating Systems What Is an Operating System Real-Time
Operating Systems Babak Kia Adjunct Professor Boston University College of Engineering Email: bkia -at- bu.edu ENG SC757 - Advanced Microprocessor Design What is an Operating System z Operating System handles • Memory Addressing & Management • Interrupt & Exception Handling • Process & Task Management • File System • Timing • Process Scheduling & Synchronization z Examples of Operating Systems • RTOS – Real-Time Operating System • Single-user, Single-task: example PalmOS • Single-user, Multi-task: MS Windows and MacOS • Multi-user, Multi-task: UNIX 2 Real-Time Operating Systems z Operating systems come in two flavors, real-time versus non real-time z The difference between the two is characterized by the consequences which result if functional correctness and timing parameters are not met in the case of real-time operating systems z Real-time operating systems themselves have two varieties, soft real-time systems and hard real- time systems z Examples of real-time systems: • Food processing • Engine Controls • Anti-lock breaking systems 3 1 Soft versus Hard Real-Time z In a soft real-time system, tasks are completed as fast as possible without having to be completed within a specified timeframe z In a hard real-time operating system however, not only must tasks be completed within the specified timeframe, but they must also be completed correctly 4 Foreground/Background Systems z The simplest forms of a non real-time operating systems are comprised of super-loops and are called foreground/background systems z Essentially this is an application -

Blocksci: Design and Applications of a Blockchain Analysis Platform
BlockSci: Design and applications of a blockchain analysis platform Harry Kalodner Steven Goldfeder Alishah Chator [email protected] [email protected] [email protected] Princeton University Princeton University Johns Hopkins University Malte Möser Arvind Narayanan [email protected] [email protected] Princeton University Princeton University ABSTRACT to partition eectively. In fact, we conjecture that the use of a tra- Analysis of blockchain data is useful for both scientic research ditional, distributed transactional database for blockchain analysis and commercial applications. We present BlockSci, an open-source has innite COST [5], in the sense that no level of parallelism can software platform for blockchain analysis. BlockSci is versatile in outperform an optimized single-threaded implementation. its support for dierent blockchains and analysis tasks. It incorpo- BlockSci comes with batteries included. First, it is not limited rates an in-memory, analytical (rather than transactional) database, to Bitcoin: a parsing step converts a variety of blockchains into making it several hundred times faster than existing tools. We a common, compact format. Currently supported blockchains in- describe BlockSci’s design and present four analyses that illustrate clude Bitcoin, Litecoin, Namecoin, and Zcash (Section 2.1). Smart its capabilities. contract platforms such as Ethereum are outside our scope. Second, This is a working paper that accompanies the rst public release BlockSci includes a library of useful analytic and visualization tools, of BlockSci, available at github.com/citp/BlockSci. We seek input such as identifying special transactions (e.g., CoinJoin) and linking from the community to further develop the software and explore addresses to each other based on well-known heuristics (Section other potential applications. -

Accounting for and Auditing of Digital Assets Digital Assets Working Group
Practice aid Accounting for and auditing of digital assets Digital Assets Working Group Accounting Subgroup Matthew Schell, Chair Kevin Jackson Mark Murray Crowe LLP PwC RSM US LLP Michael Bingham Jin Koo Amy Park US Government Accountability BDO USA LLP Deloitte & Touche LLP Office Corey McLaughlin Beth Paul Brian Fields Cohen & Company PwC KPMG LLP Lan Ming Aleks Zabreyko Rahul Gupta Ernst & Young LLP Connor Group Grant Thornton LLP Christopher Moore Crowe LLP Auditing Subgroup Amy Steele, Chair Angie Hipsher-Williams Shelby Murphy Deloitte & Touche LLP Crowe LLP Deloitte & Touche LLP Michael Bingham Michael Kornstein Christian Randall US Government Accountability Office Ernst & Young LLP Cohen & Company Jay Brodish Sara Krople Jay Schulman PwC Crowe LLP RSM US LLP Damon Busse Bryan Martin Robert Sledge Baker Tilly Virchow Krause, LLP BDO USA LLP KPMG LLP Mary Grace Davenport Dylan McDermott Jagruti Solanki PwC Coinbase Aprio Jeremy Goss Grant Thornton LLP AICPA Senior Committees Financial Reporting Executive Committee Angela Newell, Chair Mark Crowley Jeff Sisk Kelly Ardrey Jr. Sean Lager Dusty Stallings Michelle Avery Mark Northan Lynne Triplett Lee Campbell Bill Schneider Mike Winterscheidt Cathy Clarke Rachel Simons Aleks Zabreyko Assurance Services Executive Committee Jim Burton, Chair Mary Grace Davenport Brad Muniz Christine Anderson Chris Halterman Dyan Rohol Daniel Balla Elaine Howle Kimberly Ellison-Taylor Jennifer Burns Bryan Martin Miklos Vasarhelyi Auditing Standards Board Tracy Harding, Chair AICPA staff Diana Krupica, -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe. -
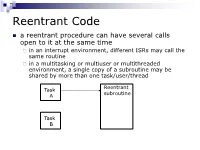
Reentrant Code
Reentrant Code a reentrant procedure can have several calls open to it at the same time in an interrupt environment, different ISRs may call the same routine in a multitasking or multiuser or multithreaded environment, a single copy of a subroutine may be shared by more than one task/user/thread Reentrant Task subroutine A Task B Reentrant Code Characteristics requirements: 1. any parameters or local variables must be on the stack frame 2. registers may be used for parameters and local variables but must be saved on or restored from the stack at beginning/end of the subroutine 3. guarantee that each call of the subroutine will create a separate stack frame to maintain data integrity 4. no self-modifying code Recursion recursive code must be reentrant recursive reentrant but reentrant recursive e.g. calculating 3! using recursion main move.w number,D0 pass the number jsr fact start recursive rtn move.w D0,result store the factorial stop #$2700 number dc.w 3 result ds.w 1 fact link A6,#-2 Stack structure move.w D0,-2(A6) subq.w #1,D0 bne push move.w -2(A6),D0 bra return push jsr fact mulu -2(A6),D0 return unlk A6 rts end main SP ->/////// A much more complex example: X: array [0..30] of words Y: longword Z, ALPHA, N: byte call order is S/R demo(X, Y, Z, ALPHA, N ) N is passed/returned by value, all others are passed by reference demo(X[w:31], Y[l], Z[b], ALPHA[b], N[b]) main CLR.W D2 zero entire word MOVE.B N,D2 N to low byte MOVE.W D2,-(SP) N on stack PEA ALPHA push arguments PEA Z in reverse order PEA Y PEA X JSR demo call -

On the Security of Electroneum Cloud Mining
This Selfie Does Not Exist: On the Security of Electroneum Cloud Mining Alexander Marsalek1, Edona Fasllija2 and Dominik Ziegler3 1Secure Information Technology Center Austria, Vienna, Austria 2Institute for Applied Information Processing and Communications (IAIK), Graz University of Technology, Graz, Austria 3Know-Center GmbH, Graz, Austria Keywords: Electroneum Cloud Mining, Cryptocurrency, Impersonation Attack, Image Manipulation. Abstract: The Electroneum cryptocurrency provides a novel mining experience called “cloud mining”, which enables iOS and Android users to regularly earn cryptocurrency tokens by simply interacting with the Electroneum app. Besides other security countermeasures against automated attacks, Electroneum requires the user to up- load selfies with a predefined gesture or a drawing of a symbol as a prerequisite for the activation of the mining process. In this paper, we show how a malicious user can circumvent all of these security features and thus create and maintain an arbitrary number of fake accounts. Our impersonation attack particularly focuses on creating non-existing selfies by relying on Generative Adversarial Network (GAN) techniques during account initialization. Furthermore, we employ reverse engineering to develop a bot that simulates the genuine Elec- troneum app and is capable of operating an arbitrary number of illegitimate accounts on one Android device, enabling the malicious user to obtain an unfairly large payout. 1 INTRODUCTION Rivet, 2019). Due to these effects, both Google and Apple prohibit cryptocurrency mining apps from their During 2017, the first and most popular cryptocurrency, application stores (Apple, 2019; Google, 2018), limiting Bitcoin, experienced an astonishing 13-fold increase in the accessibility of the average smartphone users to crypto mining. Despite this fact, several projects like value (Corcoran, 2017).