DAY ONE: AMAZON WEB SERVICES with VSRX COOKBOOK Patel, Bidabadi, Et.Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -
Securebox Azure
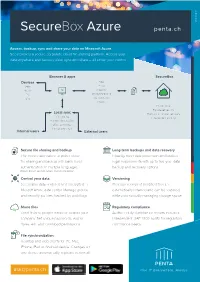
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Wandisco Fusion® Microsoft Azure Data Box
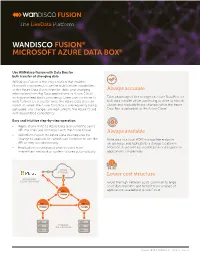
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Lock-Free Collaboration Support for Cloud Storage Services With
Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation Jian Chen, Minghao Zhao, and Zhenhua Li, Tsinghua University; Ennan Zhai, Alibaba Group Inc.; Feng Qian, University of Minnesota - Twin Cities; Hongyi Chen, Tsinghua University; Yunhao Liu, Michigan State University & Tsinghua University; Tianyin Xu, University of Illinois Urbana-Champaign https://www.usenix.org/conference/fast20/presentation/chen This paper is included in the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) February 25–27, 2020 • Santa Clara, CA, USA 978-1-939133-12-0 Open access to the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) is sponsored by Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation ⇤ 1 1 1 2 Jian Chen ⇤, Minghao Zhao ⇤, Zhenhua Li , Ennan Zhai Feng Qian3, Hongyi Chen1, Yunhao Liu1,4, Tianyin Xu5 1Tsinghua University, 2Alibaba Group, 3University of Minnesota, 4Michigan State University, 5UIUC Abstract Pattern 1: Losing updates Alice is editing a file. Suddenly, her file is overwritten All studied This paper studies how today’s cloud storage services support by a new version from her collaborator, Bob. Sometimes, cloud storage collaborative file editing. As a tradeoff for transparency/user- Alice can even lose her edits on the older version. services friendliness, they do not ask collaborators to use version con- Pattern 2: Conflicts despite coordination trol systems but instead implement their own heuristics for Alice coordinates her edits with Bob through emails to All studied handling conflicts, which however often lead to unexpected avoid conflicts by enforcing a sequential order. -
Wandisco Fusion® Microsoft Azure Data Box®
FUSION WANDISCO FUSION® MICROSOFT AZURE DATA BOX® Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Always accurate information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. Always available • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the Write data to a local HDFS-compatible endpoint API as they would normally. on-premises and replicate to a storage location in • Replication is continuous and recovers from Microsoft Azure with no modification or disruption to intermittent network or system failures automatically. applications on-premises. AZURE 2 STORAGE Lower cost structure MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of applications available in Azure Cloud. FUSION FUSION FUSION HADOOP ON-PREMISES Copyright © 2018 WANdisco, Inc. -

Igneous Backup with Microsoft Azure Data Box Executive Overview the Benefits of Cloud Backup, Including Scalability, Accessibility, and Agility, Are Immense
SOLUTION GUIDE Igneous Backup with Microsoft Azure Data Box Executive Overview The benefits of cloud backup, including scalability, accessibility, and agility, are immense. However, significant challenges lie in effectively deploying cloud backups for enterprise. To help enterprises harness the value of cloud backup while overcoming the challenges of massive scale, Igneous Unstructured Data Management as-a-Service and Microsoft Azure Data Box combine to offer an integrated solution that accelerates data migration from network attached storage (NAS) to Microsoft Azure Storage, and manages ongoing replication and tiering to cloud. With backup environments, the challenge of using public cloud is often seeding the initial backup before doing incrementals. Azure Data Box provides an economical way to transport those initial backups (often called “level- 0’s”) into Azure Storage without worrying about network bandwidth between your on-premises environment and Azure Storage. Igneous Unstructured Data Management as-a-Service solution, built for managing file-based backups, provides native integration with Azure Storage, including the Azure Data Box. Together, Igneous and Azure allow you to backup unstructured data stored on your primary network attached storage (NAS) file systems, efficiently move large amounts of data to Azure Storage, and protect and manage your data with tiering and replication to cloud. Microsoft Azure Data Box provides a secure, tamper-resistant method for quick and simple transfer of your data to Azure. Use Azure Data Box service when you want to transfer large amounts of data to Azure but are limited by time, network availability, or costs. Azure Data Box is supported by Igneous as a method to support transfers or initial sync to Azure Storage. -

Getting Started with Google Cloud Platform
Harvard AP275 Computational Design of Materials Spring 2018 Boris Kozinsky Getting started with Google Cloud Platform A virtual machine image containing Python3 and compiled LAMMPS and Quantum Espresso codes are available for our course on the Google Cloud Platform (GCP). Below are instructions on how to get access and start using these resources. Request a coupon code: Google has generously granted a number of free credits for using GCP Compute Engines. Here is the URL you will need to access in order to request a Google Cloud Platform coupon. You will be asked to provide your school email address and name. An email will be sent to you to confirm these details before a coupon code is sent to you. Student Coupon Retrieval Link • You will be asked for a name and email address, which needs to match the domain (@harvard.edu or @mit.edu). A confirmation email will be sent to you with a coupon code. • You can only request ONE code per unique email address. If you run out of computational resources, Google will grant more coupons! If you don’t have a Gmail account, please get one. Harvard is a subscriber to G Suite, so access should work with your @g.harvard.edu email and these were added already to the GCP project. If you prefer to use your personal Gmail login, send it to me. Once you have your google account, you can log in and go to the website below to redeem the coupon. This will allow you to set up your GCP billing account. -

The Effect of Film Sharing on P2P Networks on Box Office Sales
The effect of film sharing on P2P networks on box office sales Kęstutis Černiauskas Faculty of Computing Blekinge Institute of Technology SE-371 79 Karlskrona Sweden i This thesis is submitted to the Faculty of Computing at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of Master in Informatics (120 credits). Contact Information: Author(s): Kęstutis Černiauskas E-mail: [email protected] University advisor: Sara Eriksén Department Faculty of Computing Internet : www.bth.se Blekinge Institute of Technology Phone : +46 455 38 50 00 SE-371 79 Karlskrona, Sweden Fax : +46 455 38 50 57 ii ABSTRACT Context. Online piracy is widespread, controversial and poorly understood social phenomena that affects content creators, owners, and consumers. Online piracy, born from recent, rapid ITC changes, raises legal, ethical, and business challenges. Content owners, authors and content consumers should benefit from better understanding of online piracy. Improved, better adapted to marketplace and ITC changes content distribution models should benefit content owners and audiences. Objectives. Investigate online piracy effect on pirated product sales. Improve understanding of online piracy behaviors and process scale. Methods. This observational study investigated movie-sharing effect on U.S. box office. Movie sharing was observed over BitTorrent network, the most popular peer-to-peer file-sharing network. Relationship between piracy and sales was analyzed using linear regression model. Results. File sharing was found to have a slightly positive correlation with U.S. box office sales during first few weeks after film release, and no effect afterwards. Most of newly released movies are shared over BitTorrent network. -

Migrate-To-WVD-And-Beyond-By-Marius-Sandbu
Migrate to WVD and Beyond Published by Marius Sandbu on December 11, 2020 This blog post is split into different sections. Plan Assess Foundation Migrate/Rebuild/Extend Operate and Govern 1. Plan So if you want to move from an existing VDI platform to Windows Virtual Desktop (WVD) there are a lot of requirements that you need to understand (and not just the technical requirements). You are essentially moving to a cloud based ecosystem where WVD might be one of the workloads that is part of the big puzzle. And of course when hosting a VDI platform you need to have the applications and the data close together to ensure that you have an optimized end-user experience. In most organizations you have already invested time and money into training and processes to manage and operate the existing VDI platform. Also you might have 3.party management tools which are used to manage your VDI Service. Understand the state you are coming from: Existing VDI Solution – Technology Management & Operations – Process Knowledge and Expertise – People These will of course change when you migrate to WVD and you would need to ensure that you have the right skill and competency in place to manage a WVD enviroment ( in addition to the other workloads in Azure as well) Just to showcase how the difference might be from a technology perspective. Other standing the VDI workloads and requirements End-user requirements – Devices, Peripherals and Working Patterns End-user endpoints – Domain Join or Azure AD Based Workloads – Power Users or Office Workers Supporting -

Infrastructure As Code with Oracle Linux & Terraform Running On
Infrastructure as Code with Oracle Linux & Terraform Running on Oracle Public & Private Cloud UKOUG Midlands Summit Simon Hayler Technical Product Manager 28th February 2019 Copyright © 2019, Oracle and/or its affiliates. All rights reserved. | Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle. Copyright © 2019, Oracle and/or its affiliates. All rights reserved. | 2 Oracle Linux for Oracle Cloud Infrastructure Enhanced Developer Cloud-Ready, Integrated Cost Effective Compute Platform • Access to frequent and latest Oracle • Oracle Cloud developer tools such as • Oracle Linux Support is provided at Linux image updates Terraform, SDK's, and CLI are no additional cost on OCI deployed faster and easier via local • • Faster downloads from mirrored yum server Take advantage of its 24 x7 best-in- Oracle Container Registry and OL class support services and tools yum server within OCI • Easy access to Linux developer and preview software channels in local • No need to budget for OS support • Zero-downtime OS kernel and user OL yum server fees on OCI space updates with Ksplice pre- • installed in OCI • Thousands of EPEL packages built Use Oracle Linux as part of a fully and signed by Oracle for security and and extensively tested cloud • Comprehensive containers and compliance infrastructure stack container management support • Software Collection Library support • Oracle Linux Storage Appliance included to install recent versions of offers an easy way to build NFS and Python, PHP, NodeJS, nginx, and Samba shared storage in OCI more Copyright © 2019, Oracle and/or its affiliates. -

IBM Storage Suite for IBM Cloud Paks Data Sheet
IBM Storage Suite for IBM Cloud Paks Data Sheet IBM Storage Suite for IBM Cloud Paks IBM Storage Suite for Cloud Paks offers Highlights a faster, more reliable way to modernize and move to the cloud • Flexible sofware-defined data resources for easy Today, 85% of enterprises around the world are already container deployments operating in a hybrid cloud environment.1 At the same time, • Reduce risk and complexity more than three-quarters of all business-critical workloads when moving mission- have yet to make the transition to the cloud.2 These metrics critical apps to the cloud suggest that for all the benefits conveyed by cloud • Market-leading Red Hat and computing, many organizations still face plenty of challenges award-winning IBM ahead to fully incorporate cloud-native solutions into their Spectrum Storage software core business environments. Containerization is a key enabling technology for flexibly delivering workloads to private and public clouds and DevOps. Among their many benefits, containers allow legacy applications to run in almost any host environment without being rewritten – an enormous advantage for enterprises with numerous applications, each composed of thousands of lines of code. To facilitate deployment of containerized workloads and development of new cloud-native applications, companies large and small are modernizing around platforms such as Red Hat OpenShift. IBM has developed a series of middleware tools called IBM Cloud Pak solutions designed to enhance and extend the functionality and capabilities of Red Hat OpenShift. The solutions include Cloud Pak for Data, Business Automation, Watson AIOps, Integration, Network Application, and Security, and give enterprises the fully modular and easy-to- consume capabilities they need to bring the next 80% of their workloads into modern, cloud-based environments.