POWERLINK Safety
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Industrial Ethernet Technologies Page 1 © Ethercat Technology Group, January 2011
Industrial Ethernet Technologies Page 1 © EtherCAT Technology Group, January 2011 Industrial Ethernet Technologies: Overview Approaches Modbus/TCP Ethernet/IP Powerlink PROFINET SERCOS III EtherCAT Summary © EtherCAT Technology Group Industrial Ethernet Technologies Editorial Preface: This presentation intends to provide an overview over the most important Industrial Ethernet Technologies. Based on published material it shows the technical principles of the various approaches and tries to put these into perspective. The content given represents my best knowledge of the systems introduced. Since the company I work for is member of all relevant fieldbus organizations and supports all important open fieldbus and Ethernet standards, you can assume a certain level of background information, too. The slides were shown on ETG Industrial Ethernet Seminar Series in Europe, Asia and North America as well as on several other occasions, altogether attended by several thousand people. Among those were project engineers and developers that have implemented and/or applied Industrial Ethernet technologies as well as key representatives of some of the supporting vendor organizations. All of them have been encouraged and invited to provide feedback in case they disagree with statements given or have better, newer or more precise information about the systems introduced. All the feedback received so far was included in the slides. You are invited to do the same: provide feedback and – if necessary – correction. Please help to serve the purpose of this slide set: a fair and technology driven comparison of Industrial Ethernet Technologies. Nuremberg, January 2011 Martin Rostan, [email protected] Industrial Ethernet Technologies Page 2 © EtherCAT Technology Group, January 2011 Industrial Ethernet Technologies: Overview Approaches Modbus/TCP Ethernet/IP Powerlink PROFINET SERCOS III EtherCAT Summary © EtherCAT Technology Group Industrial Ethernet Technologies All Industrial Ethernet Technologies introduced in this presentation are supported by user and vendor organizations. -

Opensafety Basics 2013
openSAFETY The open safety standard for all communication protocols What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Safety Relays What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Additional DI/DO module Safety Relays What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Additional DI/DO module Extra wiring of safe sensors Safety Relays What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Additional DI/DO module Extra wiring of safe sensors Safety Extra wiring required to Relays control safe actuators What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Additional DI/DO module Speed Monitor Extra wiring of safe sensors Safety Extra wiring required to Relays control safe actuators Extra speed monitor for safe motion control functions What does Safety normally look like? • Safety Relays within the cabinet • Safety application by discrete wiring PLC I/O Servo Additional DI/DO module Speed Monitor Extra wiring of safe sensors Safety Timer Extra wiring required to Relays Relays control safe actuators Extra speed monitor for safe motion control functions Timer Relays for synchronous shutdown What Safety should look like! • Integrated • Flexible PLC -

Basics Why Real-Time Industrial Ethernet?
System Overview POWERLINK Basics Why Real-time Industrial Ethernet? Over the course of the last two decades, it has combination with an Internet protocol like TCP/IP is become hard to keep track of the numerous field- unsuitable for data transmission in hard real-time. bus systems that have been developed in the auto- Data traffic can be delayed in unforeseeable ways mation industry specifically for purposes of process due to the CSMA/CD mechanism (Carrier Sense and factory production control. Yet there remain Multiple Access/Collision Detection). An integral various restraints that are impeding their perform- part of the Ethernet standard IEEE 802.3, that ance. Demand has therefore become more mechanism helps prevent data collisions on the pressing for a reliable communication system that bus that can occur in Ethernet environments due would offer high flexibility and across-the-board to the particular nature of Ethernet transmissions. compatibility. A new solution in this vein was also In order to develop Ethernet-based, but real-time expected to allow for ongoing improvements and capable fieldbuses, manufacturers have pursued future upgrades. Ethernet first rose to that chal- various approaches in their efforts to eliminate such lenge: it was a tried and tested technology that delays. These solutions are commonly referred to as was free of patents and was widely standardized. “Real-time Industrial Ethernet” technologies. This Moreover, it had great potential to serve as a booklet will introduce you to POWERLINK, which consistent, integrated communication solution, i.e. has become one of the most successful Real-time allow for an interconnection of the control, process, Industrial Ethernet systems in the world today. -

POWERLINK Basics Why Real-Time Industrial Ethernet?
System Overview POWERLINK Basics Why Real-time Industrial Ethernet? Over the course of the last two decades, it has combination with an Internet protocol like TCP/IP is become hard to keep track of the numerous field- unsuitable for data transmission in hard real-time. bus systems that have been developed in the auto- Data traffic can be delayed in unforeseeable ways mation industry specifically for purposes of process due to the CSMA/CD mechanism (Carrier Sense and factory production control. Yet there remain Multiple Access/Collision Detection). An integral various restraints that are impeding their perform- part of the Ethernet standard IEEE 802.3, that ance. Demand has therefore become more mechanism helps prevent data collisions on the pressing for a reliable communication system that bus that can occur in Ethernet environments due would offer high flexibility and across-the-board to the particular nature of Ethernet transmissions. compatibility. A new solution in this vein was also In order to develop Ethernet-based, but real-time expected to allow for ongoing improvements and capable fieldbuses, manufacturers have pursued future upgrades. Ethernet first rose to that chal- various approaches in their efforts to eliminate such lenge: it was a tried and tested technology that delays. These solutions are commonly referred to as was free of patents and was widely standardized. “Real-time Industrial Ethernet” technologies. This Moreover, it had great potential to serve as a booklet will introduce you to POWERLINK, which consistent, integrated communication solution, i.e. has become one of the most successful Real-time allow for an interconnection of the control, process, Industrial Ethernet systems in the world today. -

Opensafety – the Open Source Safety Solution
MMC 2013 CAN in Automation Opensafety – the open source safety solution Miodrag Veselic (Bernecker & Rainer) The safety requirements for mobile machinery have increased considerably since the introduction of the new Machinery Directive (2006/42/EC). The new standards have resulted in new approaches to the design of safety technology. Integrated safety solutions allow safety signals to be used for automation as well. New features increase machine availability, reduce the number of required sensors and decrease the overall complexity of safety solutions. Opensafety is the world’s only open-source safety protocol that enables safety communication via any protocol available on the market. In addition, the Opensafety stack is pre-certified for SIL3 by TÜV-SÜD and TÜV-Rheinland. With no licensing costs and a free, pre-certified software stack, users benefit from greatly accelerated time-to-market. Basic safety requirements The procedure for reducing risk to an acceptable minimum is defined in EN ISO The failure of components – in vehicles for 12100 - Risk assessment and risk example – can be minimized through well- reduction - see also Figure 1. defined rules and regulations. The In the first step, hazards and hazardous transformation of the Machinery Directive situations are evaluated on the bare into the Product Safety Act (ProdSG) machine. The assessment must be carried provides a solid technical basis and, in out throughout the entire life cycle of the Germany, a legal framework as well. machine (manufacture, transport, commissioning, etc.). In the second step, risk is estimated by determining the likely extent of damage and its probability of occurrence. The last step, risk evaluation, involves an assessment of whether objectives for risk reduction have been achieved. -
The 5 Major Technologies
February2013 / Issue 2 SYSTEM COMPARISON The 5 Major Technologies PROFINET, nd POWERLINK, Edition EtherNet/IP, 2 EtherCAT, SERCOS III How the Systems Work The User Organizations A Look behind the Scenes Investment Viability and Performance Everything You Need to Know! Safety protocols Learn the basics! EPSG_IEF2ndEdition_en_140416.indd 1 16.04.14 16:02 Luca Lachello Peter Wratil Anton Meindl Stefan Schönegger Bhagath Singh Karunakaran Huazhen Song Stéphane Potier INTRODUCTION 4 · Selection of Systems for Review Preface Outsiders are not alone in finding the world of Industrial Ethernet somewhat confusing. Experts who examine the matter are similarly puzzled by a broad and intransparent line-up of competing HOW THE SYSTEMS WORK 6 · Approaches to Real-Time systems. Most manufacturers provide very little information of that rare sort that captures tech- · PROFINET Communication nical characteristics and specific functionalities of a certain standard in a way that is both com- · POWERLINK Communication prehensive and easy to comprehend. Users will find themselves even more out of luck if they are · EtherNet/IP Communication seeking material that clearly compares major systems to facilitate an objective assessment. · EtherCAT Communication · SERCOS III Communication We too have seen repeated inquiries asking for a general overview of the major systems and wondering “where the differences actually lie”. We have therefore decided to dedicate an issue ORGANIZATIONS 12 · User Organizations and Licensing Regimes of the Industrial Ethernet Facts to this very topic. In creating this, we have tried to remain as objective as a player in this market can be. Our roundup focuses on technical and economic as well as on strategic criteria, all of which are relevant for a consideration of the long-term viability CRITERIA FOR INVESTMENT VIABILITY 16 · Compatibility / Downward Compatibility · Electromagnetic Compatibility (EMC) · Electrical Contact Points of investments in Industrial Ethernet equipment. -

Flyer Opensafety "The Future Is Wide Open"
The safety standard The safety standard Ot Et her herCat 4% THE FUTURE IS WIDE OPEN. s 5% LEADING MANUFACTURERS IEC APPROVES openSAFETY POWERLINK PROFINET 11% 28% TRUST IN openSAFETY AS WORLDWIDE STANDARD | | Modbus TCP/IP 22% Market shares of The fieldbus-independent openSAFETY protocol was tested Ethernet/IP according to IEC 61784-3 FSCP 13 and approved by national 30% Industrial Ethernet (Source: IMS Research 3rd quarter 2009) IEC committees representing 27 countries including China, USA and Germany, and is therefore released for international standardization. Because openSAFETY is bus independent, n 91 % realised with openSAFETY it can be used with all fieldbus or industrial Ethernet systems. End customers have been requesting a uniform and manufacturer- independent standard for years, and openSAFETY is the response to those requests. It allows increases in productivity that are currently Highlights at a glance:| not possible with other safety protocols. n n o n e single,uniformstandardforallleadingfieldbuses n n maximumproductivityduetoefficientcross-communication n n reducedcommissioningandmaintenancetime BE ON THE SAFE SIDE! n n automaticsafeparameterization Automotive OEMs SIL3 certification by TÜV Rheinland and TÜV Süd n n perfectlysuitedtosafemodularmachineconcepts and suppliers EthernetPOWERLINKStandardizationGroup(EPSG) POWERLINK-Office n n Building Construction s o l e 100%opensafetysolution automation industry Bonsaiweg 6 · 15370 Fredersdorf · Germany n n f a s t e s t IEC61508SIL3communicationsolution Phone: +49 33439 539 -

5 Ways to Improve Safety & Profitability
VOL 08 | OCT-NOV 2015 www.AandD24.in AUTOMATIONAutomation & DRIVES & Drives UNLOCKING HIDDEN POTENTIAL 5 ways to improve safetyEfficient &Manufacturing profitability Also available in China, Taiwan, Singapore, Malaysia, Thailand & Hong Kong Malaysia, Singapore, Taiwan, Also available in China, FOCUS Semiconductor & Electronics P. 32 A&D - Interview A&D - Interview Dr Karl Tragl Hans Bangert President of the Executive Board Managing Director Bosch Rexroth AG Bosch Rexroth India (p.24) (p.24) In association with Advt Meistermacher. Made in Germany. Rainer Scholl, Master – Gripping System Components Jens Lehmann, German Goalkeeper legend, brand ambassador of SCHUNK, the family-owned company since 2012, represents precise gripping and concentrated, safe holding. German champion with Borussia Dortmund 2002 English champion with Arsenal London 2004 www.gb.schunk.com/robotaccessories SCHUNK Robot Accessories End-of-arm Competence with more than 1,200 Modules SCHUNK robot accessories. The unique standard line of modules for mechanical, sensor and power connections of handling modules and robots for every industry and handling task. 50% more moment load DDF 2 Rotary feed-through The latest standard for modern robots. Quick-change Collision and Compensation 6-axis force / moment system SWS. overload sensor OPR. unit AGE. sensor FT. 90% faster Protection class IP65. Compensation Measurement is effector changing. in 3 directions. possible in KG GmbH & Co. SCHUNK © 2015 6 degrees of freedom. INNOVATION INTELLIGENCE® Page 2_Igus.pdf 10/13/2014 5:06:37 -
Sercos News 01/2014
sercos Issue 01/2014 the automation bus magazine An existential Heinz Gall, Global Business Field Manager at TÜV Rheinland in conversation with Sercos International issue Cost efficient Optimized Transparent Cost reduction by one third, Reduction of machine down Ethernet communication reduction of energy requirements times while increasing with Sercos and Hilscher's by about 25 percent transmission rates in parallel netSWITCH sercos sercos Editorial News Events Technology Application Cover Story New Products Review & Outlook Editorial News Events Technology Application Cover Story New Products Review & Outlook Safety for Higher Economic Contents Efficiency and Flexibility News The requirements of operational safety for machinery 03 Sercos Webinar Series Available as Download are rising continuously. Automation solutions must not only protect people, machines and the en- 04 New Brochures for Users and Vendors Available vironment in a reliable manner but at the same time Webinar Recordings must fulfill high standards of economic efficiency and 05 Events flexibility. “Moving Forward with Tradition and Innovation” Technology “Sercos in Practice: Easy, Fast, Flexible” Bus systems, which not only transmit process data but also safety-relevant data, play an important role 06 Ethernet Connectivity with Sercos “Sercos in Practice: Efficient, Reliable and Economic” here. Enormous amounts are saved in installation and engineering, safe periphery components can be com- 08 Multi Vendor Solution: Plastic Electronics “CIP Safety on Sercos & EtherNet/IP” bined with standard components, and safe data can be used for diagnostic purposes at the standard level 10 Flexible Topologies with Sercos III “Benefits of a Common Sercos III and EtherNet/IP Infrastructure” as well. Application However, these advantages are countered by higher 12 Sercos Replaces Signalbus complexity both for device manufacturers and for engineers. -

New Lift Safety Architecture to Meet PESSRAL Requirements Ayoub Soury, Denis Genon-Catalot, Jean-Marc Thiriet
New lift safety architecture to meet PESSRAL requirements Ayoub Soury, Denis Genon-Catalot, Jean-Marc Thiriet To cite this version: Ayoub Soury, Denis Genon-Catalot, Jean-Marc Thiriet. New lift safety architecture to meet PESSRAL requirements. WSWAM 2015 - 2nd World Symposium on Web Applications and Networking, Mar 2015, Sousse, Tunisia. 5 p., 10.1109/WSWAN.2015.7210314. hal-01233766 HAL Id: hal-01233766 https://hal.univ-grenoble-alpes.fr/hal-01233766 Submitted on 2 Dec 2015 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. New lift safety architecture to meet PESSRAL requirements Ayoub Soury∗†, Denis Genon-Catalot† and Jean-Marc Thiriet∗‡ ∗Univ. Grenoble Alpes, Gipsa-lab, F-38000 Grenoble, France † Univ. Grenoble Alpes, LCIS, F-26000 Valence, France ‡ CNRS, Gipsa-lab, F-38000 Grenoble, France Email: {ayoub.soury, denis.genon-catalot}@lcis.grenoble-inp.fr; [email protected] Abstract — Industrial control and automation systems are The main contribution in this paper is an analysis case of evolving towards infrastructures more connected. Its the adopted standard IEC 61508 requirements specification component’s interconnection makes them more dependent targeting the development of a new safety chain for lift on the networks and communication protocols used. -

Opensafety – Stejné Bezpečí Pro Všechny
téma OpenSafety – stejné bezpečí pro všechny Bezpečnostní komunikační protokol OpenSafety je první zcela otevřený protokol pro Výrobci strojů a zařízení ale profitují z in- přenos dat spjatých s funkční bezpečností vhodný pro všechny oblasti průmyslové au- tegrovaných a rychlých bezpečnostních systé- tomatizace. V článku jsou uvedeny důvody vzniku, základní vlastnosti a přednosti toho- mů i jinak. Rychle reagující systém umožňu- to univerzálního protokolu. je reagovat na nebezpečné situace později či používat větší provozní rychlosti. Zjednodu- Trend v systémech zajišťujících funkční výrobců strojů a zařízení je nuceno vybavo- šeně řečeno, rychlý systém pohyb bezpečně vat své výrobky řídicími systémy podle přání „ubrzdí“ z větší rychlosti za stejnou dobu jako bezpečnost svých odběratelů. Pokud jde jen o řídicí sys- pomalý systém z menší rychlosti. Ne proto, Asi před deseti lety se na trhu začaly ob- tém, znamená to programátorskou práci na- že by brzdil intenzivněji, ale proto, že zarea- funkční bezpečnostfunkční jevovat první systémy zajišťující funkční bez- víc. V případě bezpečnostních systémů však guje rychleji, vydá povel k brzdění dříve než pečnost strojů a strojních zařízení (bezpeč- nostní systémy), které pro bezpečný přenos zpráv mezi prvky systému používají komu- nikační sběrnice. Jejich přednosti oproti kon- venčním, „zadrátovaným“ bezpečnostním systémům jsou nepřehlédnutelné a přispíva- jí k rozvoji a upevnění pozice těchto nových systémů na trhu. K nesporným přednostem bezpečnostních systémů založených na ko- munikačních -
Newsletter October 2010
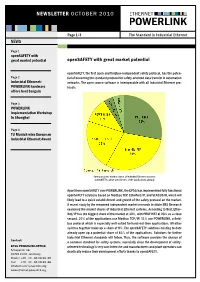
NEWSLETTER OCTOBER 2010 Page 1/4 The Standard in Industrial Ethernet NEWS Page 1 openSAFETY with great market potential openSAFETY with great market potential openSAFETY, the first open and fieldbus-independent safety protocol, has the poten- Page 2 tial of becoming the standard protocol for safety-oriented data transfer in automation Industrial Ethernet: networks. The open source software is interoperable with all Industrial Ethernet pro- POWERLINK hardware tocols. offers best bargain Page 3 POWERLINK Implementation Workshop in Shanghai Page 4 TU Munich wins European Industrial Ethernet Award Survey presents market shares of Industrial Ethernet systems: openSAFETY can be used in 63% of the applications already Apart from openSAFETY over POWERLINK, the EPSG has implemented fully functional openSAFETY solutions based on Modbus TCP, EtherNet/IP, and SERCOS III, which will likely lead to a quick establishment and growth of the safety protocol on the market. A recent study by the renowned independent market research institute IMS Research examined the market shares of Industrial Ethernet systems. According to that, Ether- Net/IP has the biggest share of the market at 30%, with PROFINET at 28% as a close second. 22% of the applications use Modbus TCP/IP. 11% use POWERLINK, a field- bus protocol which is especially well-suited for hard real-time applications. All other systems together make up a share of 9%. The openSAFETY solutions existing to date already open up a potential share of 63% of the applications. Solutions for further Industrial Ethernet standards will follow. Thus, the software provides the chance of Contact: a common standard for safety systems, especially since the development of safety- EPSG POWERLINK-OFFICE oriented technology is very cost-intensive and manufacturers and plant operators can Schaperstr.