Jesper Johansson
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

Windows Poster 20-12-2013 V3
Microsoft® Discover the Open Specifications technical documents you need for your interoperability solutions. To obtain these technical documents, go to the Open Specifications Interactive Tiles: open specifications poster © 2012-2014 Microsoft Corporation. All rights reserved. http://msdn.microsoft.com/openspecifications/jj128107 Component Object Model (COM+) Technical Documentation Technical Documentation Presentation Layer Services Technical Documentation Component Object Model Plus (COM+) Event System Protocol Active Directory Protocols Overview Open Data Protocol (OData) Transport Layer Security (TLS) Profile Windows System Overview Component Object Model Plus (COM+) Protocol Active Directory Lightweight Directory Services Schema WCF-Based Encrypted Server Administration and Notification Protocol Session Layer Services Windows Protocols Overview Component Object Model Plus (COM+) Queued Components Protocol Active Directory Schema Attributes A-L Distributed Component Object Model (DCOM) Remote Protocol Windows Overview Application Component Object Model Plus (COM+) Remote Administration Protocol Directory Active Directory Schema Attributes M General HomeGroup Protocol Supplemental Shared Abstract Data Model Elements Component Object Model Plus (COM+) Tracker Service Protocol Active Directory Schema Attributes N-Z Peer Name Resolution Protocol (PNRP) Version 4.0 Windows Data Types Services General Application Services Services Active Directory Schema Classes Services Peer-to-Peer Graphing Protocol Documents Windows Error Codes ASP.NET -
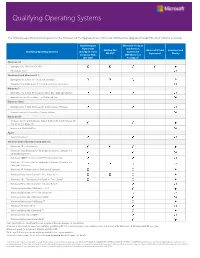
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

IT Security Principles: Windows Exploitation
IT Security Principles: Windows Exploitation IT 444 – Network Security Understanding LLMNR and NBNS • Windows systems go through several different steps to resolve a hostname to an IP address for us. • Windows will search the hosts or LMHosts file on the system to see if there’s an entry in that file. • If there isn’t, then the next step is to query DNS. Windows will send a DNS query to the default nameserver to see if it can find an entry. • In most cases, this will return an answer, and we’ll see the web page or target host we’re trying to connect to. • In situations where DNS fails, modern Windows systems use two protocols to try to resolve. LLMNR and NetBios Understanding LLMNR and NBNS o LLMNR: this protocol uses multicast in order to try to find the host on the network. Other Windows systems will subscribe to this multicast address, and when a request is sent out by a host, if anyone listening owns that name and can turn it into an IP address, a response is generated. Once the response is received, the system will take us to the host o If the host can’t be found using LLMNR, Windows use the NetBIOS protocol to try to discover the IP. It does this by sending out a broadcast request for the host to the local subnet, and then it waits for someone to respond to that request. If a host exists with that name, it can respond directly, and then our system knows that to get to that resource, it needs to go to that location Understanding LLMNR and NBNS o Both LLMNR and NBNS rely on trust o As a malicious actor, though, we can respond to any request sent out to LLMNR or NBNS and say that the host being searched for is owned by us. -

Windows 10 Download for Windows Vista Windows 10 Download for Windows Vista
windows 10 download for windows vista Windows 10 download for windows vista. Dummies has always stood for taking on complex concepts and making them easy to understand. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether it’s to pass that big test, qualify for that big promotion or even master that cooking technique; people who rely on dummies, rely on it to learn the critical skills and relevant information necessary for success. Learning Made Easy. Copyright © 2021 & Trademark by John Wiley & Sons, Inc. All rights reserved. Upgrade from Windows Vista to Windows 10 or 8.1? If you pay for 7 and then try for a free upgrade to 10 you may not get it as that offer expired in 2016. And 10 is cheaper than 7 to buy. But check everything first:: It depends on the hardware requirements of later operating systems and also whether the computer/laptop manufacturer supports and supplies drivers for the later operating systems as to whether it is possible or feasible to upgrade or not. There is no free upgrade from Vista to 7, 8.1 or 10. Follow these steps before you buy Windows 7; extended support Windows 7 SP1 until January 14, 2020 . Microsoft no longer sells 7; try amazon.com. Go to your Computer / Laptop Manufacturer's website and see if Windows 7 Drivers are available for your Make and Model Computer / Laptop. If not available, Windows 7 will not work correctly for you. Run the "Windows 7 Upgrade Advisor" Check to see if your System Specifications are compatible for Windows 7: "Windows 7 system requirements" Windows 7 Upgrade paths: Follow these steps before you buy and Upgrade (clean install) to Windows 8.1; extended support ends January 10, 2023 . -

Windows Embedded Compact 7 · User Manual Windows CE7 10.1R442 · I.MX6Q Built on October 20, 2017 Manual Revision 451 Windows CE7 10.1R442 · I.MX6 · User Manual
Windows Embedded Compact 7 · User Manual Windows CE7 10.1r442 · i.MX6Q Built on October 20, 2017 Manual revision 451 Windows CE7 10.1r442 · i.MX6 · User Manual Important hints Thank you very much for purchasing a Garz & Fricke product. Our products are dedicated to professional use and therefore we suppose extended technical knowledge and practice in working with such products. The information in this manual is subject to technical changes, particularly as a result of continuous product upgrades. Thus this manual only reflects the technical status of the products at the time of printing. Before design-in the device into your or your customer’s product, please verify that this document and the therein described specification is the latest revision and matches to the PCB version. We highly recommend contacting our technical sales team priorto any activity of that kind. A good way getting the latest information is to check the release notes of each product and/or service. Please refer to the chapter[ I 10 Related documents and online support]. The attached documentation does not entail any guarantee on the part of Garz & Fricke GmbH with respect to technical processes described in the manual or any product characteristics set out in the manual. We do not accept any liability for any printing errors or other inaccuracies in the manual unless it can be proven that we are aware of such errors or inaccuracies or that we are unaware of these as a result of gross negligence and Garz & Fricke has failed to eliminate these errors or inaccuracies for this reason. -

Upgrading from Windows Vista to Windows 7
Upgrading from Windows Vista to Windows 7 Depending on your hardware and your current edition of Windows Vista, you can use the Upgrade option during Windows 7 installation to upgrade from Windows Vista to a corresponding or higher edition of Windows 7. Upgrading is the most convenient way to get Windows 7 on your computer, because it keeps your files, settings, and programs from Windows Vista in place. If you want to install Windows 7 on a netbook, purchasing Windows 7 online from the Microsoft Store (http://go.microsoft.com/fwlink/?LinkId=160999) is the easiest method. For more information, see Installing Windows 7 on a netbook (http://windows.microsoft.com/en-us/windows7/installing-windows- 7-on-a-netbook). Overview ....................................................................................................................................................... 2 Make sure that your programs and devices will work with Windows 7 ................................................... 2 Step 1: Which version of Windows 7 can I upgrade to? ............................................................................... 2 32-bit or 64-bit: Which version of Windows 7 to install? ......................................................................... 2 What if I can't choose the Upgrade option? ............................................................................................. 3 Step 2: Installing Windows 7 ........................................................................................................................ -

DMC2161 Installation Instructions on Microsoft Windows Vista Operating System
DMC2161 Installation instructions on Microsoft Windows Vista Operating System Lorex mCam software version 2.0.1 and above is compatible with Microsoft Windows Vista™ Operating System. The Video Driver for DMC2161 has been upgraded to work on Windows Vista and a dedicated driver directory “DVS Driver for Vista” is included on your installation CD and posted to the Lorex website (www.lorexcctv.com/support). While Lorex is continuing its efforts to upgrade the audio driver of the DMC2161 camera to work in a Windows Vista environment, mCam software does support audio using any external audio device (e.g. microphone) that is compatible with Windows Vista. Please note that both video and audio are fully supported in Windows XP. If during your installation on a Microsoft Windows Vista Operating System you get a message that your driver was not successfully installed OR Please follow the steps below to complete the installation: 1. Open the Device Manager: • Click Start / Settings / Control Panel / Device Manager • Click the ‘Continue’ Button on the ‘Microsoft Management Console’ window to continue. The Device Manager window will open. • A list of all System Devices will be displayed. Right Click on the “DVS Composite Device” listed under Universal Serial Bus Controls, and select “Update Driver Software” NOTE: If the device is not displayed, click on the ‘+’ beside the Universal Serial Bus Controllers option. 2. Browse for the Driver location www.lorexcctv.com Copyright © 2007 Lorex Technology Inc. 3. Click the ‘Browse’ button to select the Driver Location. This will typically be either the CD ROM drive, or the location where you saved the “DVS Driver for Vista” (.after downloading from the website) 4. -

Information Protection Personal Computers Local Area Networks
A Short Course on Information Protection in Personal Computers and Local Area Networks by Dr. Frederick B. Cohen ASP Press FAX:412-422-4135 PO Box 81270 TEL:412-422-4134 Pittsburgh, PA 15217 USA ISBN#1-878109-14-6 Copyright c 1991, ASP ALL RIGHTS RESERVED Made in the USA by ASP Contents i 1 Introduction The proliferation of Personal Computers (PCs) and Local Area Networks (LANs) has brought about a resurgence in computer security problems that were largely solved for main- frames, and a wide variety of new problems that are specific to PC and LAN technologies. In most PCs, there are no access controls, backups are poorly managed if they are kept at all, the operating system can be accidentally corrupted, and denial of service is commonplace. In most LANs, the access controls in place can be easily violated, there is no protection against any user examining or modifying most of the network traffic, and existing controls are not adequately used. Subtle interactions between different machines on LANs can extend security problems, sometimes making even seemingly secure environments open to simplistic attacks. The purpose of this book is to explain the nature and scope of PC and LAN protection problems, describe the defenses available today and the tradeoffs in their use, and to discuss available tools for understanding the technology. 1 About the author: Dr. Cohen is widely known in computer security circles, where he has developed basic the- ory, performed ground-breaking experiments, prototyped practical solutions in widespread use, developed commercial security products for over 15 years, and provided security prod- ucts and services to organizations worldwide. -

Windows Powershell 1.0 Essentials
Windows PowerShell Essentials Windows PowerShell Essentials Windows PowerShell Essentials – Edition 1.0 © 2009 Payload Media. This eBook is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved. The content of this book is provided for informational purposes only. Neither the publisher nor the author offers any warranties or representation, express or implied, with regard to the accuracy of information contained in this book, nor do they accept any liability for any loss or damage arising from any errors or omissions. Find more eBooks at www.ebookfrenzy.com 2 © 2009 Payload Media Windows PowerShell Essentials Table of Contents Chapter 1. Installing Windows PowerShell ............................................................................... 10 1.1 Installing Windows PowerShell on Windows Server 2008 ............................................ 10 1.2 Performing a Windows Server 2008 PowerShell Command Line Installation ............... 10 1.3 Installing PowerShell on Windows Server 2003, XP and Vista Systems ........................ 11 Chapter 2. The Basics of the Windows PowerShell Interactive Shell ....................................... 13 2.1 The Windows PowerShell Command Prompt ................................................................ 13 2.2 PowerShell Command Line Editing Keys ........................................................................ 14 2.3 PowerShell Command Completion ............................................................................... -
Skype Old Version Download for Windows Vista Skype for Windows Vista
skype old version download for windows vista Skype for Windows Vista. Below there is a list of all versions of Skype for Windows Vista. Click on the version number to find out the details and download the full installer for free (note that only version 7.31 and higher are officially supported). Versions for 2017 Operating system Skype version Release date Windows Vista 7.36.0.150 9 may 2017 Windows Vista 7.35.0.103 5 may 2017 Windows Vista 7.35.0.102 2 may 2017 Windows Vista 7.35.0.101 11 april 2017 Windows Vista 7.34.0.103 3 april 2017 Windows Vista 7.34.0.102 22 march 2017 Windows Vista 7.33.0.105 14 march 2017 Windows Vista 7.33.0.104 20 february 2017 Windows Vista 7.32.0.104 9 february 2017 Windows Vista 7.32.0.103 30 january 2017 Windows Vista 7.31.0.104 10 january 2017. Versions for 2016 Operating system Skype version Release date Windows Vista 7.30.0.105 21 november 2016 Windows Vista 7.30.0.103 9 november 2016 Windows Vista 7.29.0.102 20 october 2016 Windows Vista 7.29.0.101 13 october 2016 Windows Vista 7.28.0.101 19 september 2016 Windows Vista 7.27.0.101 24 august 2016 Windows Vista 7.26.0.101 26 july 2016 Windows Vista 7.25.0.106 1 july 2016 Windows Vista 7.25.0.103 16 june 2016 Windows Vista 7.24.0.104 20 may 2016 Windows Vista 7.23.0.105 29 april 2016 Windows Vista 7.23.0.104 28 april 2016 Windows Vista 7.22.0.109 16 april 2016 Windows Vista 7.22.0.108 5 april 2016 Windows Vista 7.22.0.107 30 march 2016 Windows Vista 7.22.0.104 24 march 2016 Windows Vista 7.21.0.100 10 march 2016 Windows Vista 7.18.0.112 11 february 2016 Windows Vista 7.18.0.111 3 february 2016 Windows Vista 7.18.0.109 19 january 2016 Windows Vista 7.18.0.103 11 january 2016.