Ascii Table for Keyboard Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Freestyle-Pro-Manual.Pdf
User Manual KB900 Mac/Windows/PC SmartSet™ Cherry Low-Force Switchable Programming Engine Mechanical Keyswitches 1 Kinesis Corporation 22030 20th Avenue SE, Suite 102 Bothell, Washington 98021 USA Keyboard models covered by this manual: [email protected], [email protected] KB900-brn www.kinesis.com April 20, 2018 Edition This manual covers features included through firmware version 1.0.0. To download the latest firmware and to access all support resources visit www.kinesis.com/support. To shop for accessories visit https://www.kinesis-ergo.com/products/: Palm Supports (AC903)- Detachable Palm Supports. VIP3 Pro (AC920)- Adjustable tenting accessory and Palm Supports (5°/10°/15°). Palm Supports required for tenting. V3 Pro (AC930)- Adjustable tenting accessory (5°/10°/15°) for use without Palm Supports. Palm Pads (AC700blk)- Cushioned palm pads for use with Palm Supports. © 2018 by Kinesis Corporation, all rights reserved. Kinesis and Freestyle are registered trademarks of Kinesis Corporation. Freestyle Pro, SmartSet, and v-Drive are trademarks of Kinesis Corporation. All other trademarks are property of their respective owners. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any commercial purpose, without the express written permission of Kinesis Corporation. FCC Radio Frequency Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a residential installation. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

DEC Text Processing Utility Reference Manual
DEC Text Processing Utility Reference Manual Order Number: AA–PWCCD–TE April 2001 This manual describes the elements of the DEC Text Processing Utility (DECTPU). It is intended as a reference manual for experienced programmers. Revision/Update Information: This manual supersedes the DEC Text Processing Utility Reference Manual, Version 3.1 for OpenVMS Version 7.2. Software Version: DEC Text Processing Utility Version 3.1 for OpenVMS Alpha Version 7.3 and OpenVMS VAX Version 7.3 The content of this document has not changed since OpenVMS Version 7.1. Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation COMPAQ, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS is a trademark of Compaq Information Technologies Group, L.P. Motif is a trademark of The Open Group. PostScript is a registered trademark of Adobe Systems Incorporated. All other product names mentioned herein may be the trademarks or registered trademarks of their respective companies. Confidential computer software. Valid license from Compaq or authorized sublicensor required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information in this document is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. -

The Hexadecimal Number System and Memory Addressing
C5537_App C_1107_03/16/2005 APPENDIX C The Hexadecimal Number System and Memory Addressing nderstanding the number system and the coding system that computers use to U store data and communicate with each other is fundamental to understanding how computers work. Early attempts to invent an electronic computing device met with disappointing results as long as inventors tried to use the decimal number sys- tem, with the digits 0–9. Then John Atanasoff proposed using a coding system that expressed everything in terms of different sequences of only two numerals: one repre- sented by the presence of a charge and one represented by the absence of a charge. The numbering system that can be supported by the expression of only two numerals is called base 2, or binary; it was invented by Ada Lovelace many years before, using the numerals 0 and 1. Under Atanasoff’s design, all numbers and other characters would be converted to this binary number system, and all storage, comparisons, and arithmetic would be done using it. Even today, this is one of the basic principles of computers. Every character or number entered into a computer is first converted into a series of 0s and 1s. Many coding schemes and techniques have been invented to manipulate these 0s and 1s, called bits for binary digits. The most widespread binary coding scheme for microcomputers, which is recog- nized as the microcomputer standard, is called ASCII (American Standard Code for Information Interchange). (Appendix B lists the binary code for the basic 127- character set.) In ASCII, each character is assigned an 8-bit code called a byte. -
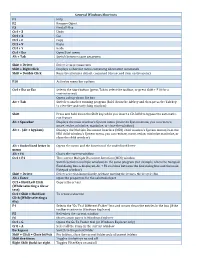
General Windows Shortcuts
General Windows Shortcuts F1 Help F2 Rename Object F3 Find all files Ctrl + Z Undo Ctrl + X Cut Ctrl + C Copy Ctrl + V Paste Ctrl + Y Redo Ctrl + Esc Open Start menu Alt + Tab Switch between open programs Alt + F4 Quit program Shift + Delete Delete item permanently Shift + Right Click Displays a shortcut menu containing alternative commands Shift + Double Click Runs the alternate default command ( the second item on the menu) Alt + Double Click Displays properties F10 Activates menu bar options Shift + F10 Opens a contex t menu ( same as righ t click) Ctrl + Esc or Esc Selects the Start button (press Tab to select the taskbar, or press Shift + F10 for a context menu) Alt + Down Arrow Opens a drop‐down list box Alt + Tab Switch to another running program (hold down the Alt key and then press the Tab key to view the task‐switching window) Alt + Shift + Tab Swit ch b ackward s b etween open appli cati ons Shift Press and hold down the Shift key while you insert a CD‐ROM to bypass the automatic‐ run feature Alt + Spacebar Displays the main window's System menu (from the System menu, you can restore, move, resize, minimize, maximize, or close the window) Alt + (Alt + hyphen) Displays the Multiple Document Interface (MDI) child window's System menu (from the MDI child window's System menu, you can restore, move, resize, minimize maximize, or close the child window) Ctrl + Tab Switch to t h e next child window o f a Multi ple D ocument Interf ace (MDI) pr ogram Alt + Underlined letter in Opens the menu and the function of the underlined letter -

Openvms: an Introduction
The Operating System Handbook or, Fake Your Way Through Minis and Mainframes by Bob DuCharme VMS Table of Contents Chapter 7 OpenVMS: An Introduction.............................................................................. 7.1 History..........................................................................................................................2 7.1.1 Today........................................................................................................................3 7.1.1.1 Popular VMS Software..........................................................................................4 7.1.2 VMS, DCL................................................................................................................4 Chapter 8 Getting Started with OpenVMS........................................................................ 8.1 Starting Up...................................................................................................................7 8.1.1 Finishing Your VMS Session...................................................................................7 8.1.1.1 Reconnecting..........................................................................................................7 8.1.2 Entering Commands..................................................................................................8 8.1.2.1 Retrieving Previous Commands............................................................................9 8.1.2.2 Aborting Screen Output.........................................................................................9 -

Workspace Desktop Edition Developer's Guide
Workspace Desktop Edition Developer's Guide Best Practices for Views 10/3/2021 Contents • 1 Best Practices for Views • 1.1 Keyboard Navigation • 1.2 Branding • 1.3 Localization • 1.4 Parameterization • 1.5 Internationalization • 1.6 Screen Reader Compatibility • 1.7 Themes • 1.8 Loosely-coupled Application Library and Standard Controls • 1.9 Views Workspace Desktop Edition Developer's Guide 2 Best Practices for Views Best Practices for Views Purpose: To provide a set of recommendations that are required in order to implement a typical view within Workspace Desktop Edition. Workspace Desktop Edition Developer's Guide 3 Best Practices for Views Keyboard Navigation TAB Key--Every control in a window has the ability to have focus. Use the TAB key to move from one control to the next, or use SHIFT+TAB to move the previous control. The TAB order is determined by the order in which the controls are defined in the Extensible Application Markup Language (XAML) page. Access Keys--A labeled control can obtain focus by pressing the ALT key and then typing the control's associated letter (label). To add this functionality, include an underscore character (_) in the content of a control. See the following sample XAML file: [XAML] <Label Content="_AcctNumber" /> Focus can also be given to a specific GUI control by typing a single character. Use the WPF control AccessText (the counterpart of the TextBlock control) to modify your application for this functionality. For example, you can use the code in the following XAML sample to eliminate having to press the ALT key: [XAML] <AccessText Text="_AcctNumber" /> Shortcut Keys--Trigger a command by typing a key combination on the keyboard. -
Cisco Jabber for Windows 11.0 User Guide
Cisco Jabber for Windows 11.0 User Guide User Guide 2 New and Changed Information 2 Availability 2 Contacts 2 Chats 5 Calls 12 Meetings 14 Create Custom Tabs 17 Accessibility 17 Troubleshooting 21 Revised: September 11, 2015, User Guide New and Changed Information This document applies to Cisco Jabber for Windows Release 11.0.x and 11.1.x. Description of Change Date Where Documented New topic added for making a Jabber to September 11, 2015 Jabber to Jabber Call, on page 12 Jabber Call Availability Create Personal Status Messages You can create personal status messages to replace the default messages and tell your contacts what you are doing at a glance. Cisco Jabber saves the three most recent personal status messages for each state. You can select your status messages from the drop-down list on the main window. Procedure Step 1 Insert your cursor in the status message field on the main window. Step 2 Enter your personal status message. Step 3 Press the Enter key on your keyboard. Cisco Jabber displays your personal status message. Contacts Add Directory Groups Directory groups are maintained by your administrator for your enterprise. When you add a directory group to your Contacts list, then the list of people assigned to that directory group are automatically added to the group in your contacts. You don't have to maintain the list because it synchronizes automatically with the directory for your enterprise, meaning that people are added and removed from the group in your Contacts whenever the administrator adds or removes them from the enterprise directory. -

UTF-8-Plan9-Paper
Hello World or Kαληµε´ρα κο´σµε or Rob Pike Ken Thompson AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT Plan 9 from Bell Labs has recently been converted from ASCII to an ASCII- compatible variant of Unicode, a 16-bit character set. In this paper we explain the rea- sons for the change, describe the character set and representation we chose, and present the programming models and software changes that support the new text format. Although we stopped short of full internationalizationÐfor example, system error mes- sages are in Unixese, not JapaneseÐwe believe Plan 9 is the first system to treat the rep- resentation of all major languages on a uniform, equal footing throughout all its software. Introduction The world is multilingual but most computer systems are based on English and ASCII. The release of Plan 9 [Pike90], a new distributed operating system from Bell Laboratories, seemed a good occasion to correct this chauvinism. It is easier to make such deep changes when building new systems than by refit- ting old ones. The ANSI C standard [ANSIC] contains some guidance on the matter of ‘wide’ and ‘multi-byte’ characters but falls far short of solving the myriad associated problems. We could find no literature on how to convert a system to larger character sets, although some individual programs had been converted. This paper reports what we discovered as we explored the problem of representing multilingual text at all levels of an operating system, from the file system and kernel through the applications and up to the window sys- tem and display. -

Bits and Bytes
BITS AND BYTES To understand how a computer works, you need to understand the BINARY SYSTEM. The binary system is a numbering system that uses only two digits—0 and 1. Although this may seem strange to humans, it fits the computer perfectly! A computer chip is made up of circuits. For each circuit, there are two possibilities: An electric current flows through the circuit (ON), or An electric current does not flow through the circuit (OFF) The number 1 represents an “on” circuit. The number 0 represents an “off” circuit. The two digits, 0 and 1, are called bits. The word bit comes from binary digit: Binary digit = bit Every time the computer “reads” an instruction, it translates that instruction into a series of bits (0’s and 1’s). In most computers every letter, number, and symbol is translated into eight bits, a combination of eight 0’s and 1’s. For example the letter A is translated into 01000001. The letter B is 01000010. Every single keystroke on the keyboard translates into a different combination of eight bits. A group of eight bits is called a byte. Therefore, a byte is a combination of eight 0’s and 1’s. Eight bits = 1 byte Capacity of computer memory, storage such as USB devices, DVD’s are measured in bytes. For example a Word file might be 35 KB while a picture taken by a digital camera might be 4.5 MG. Hard drives normally are measured in GB or TB: Kilobyte (KB) approximately 1,000 bytes MegaByte (MB) approximately 1,000,000 (million) bytes Gigabtye (GB) approximately 1,000,000,000 (billion) bytes Terabyte (TB) approximately 1,000,000,000,000 (trillion) bytes The binary code that computers use is called the ASCII (American Standard Code for Information Interchange) code. -

Part 1: Introduction to The
PREVIEW OF THE IPA HANDBOOK Handbook of the International Phonetic Association: A guide to the use of the International Phonetic Alphabet PARTI Introduction to the IPA 1. What is the International Phonetic Alphabet? The aim of the International Phonetic Association is to promote the scientific study of phonetics and the various practical applications of that science. For both these it is necessary to have a consistent way of representing the sounds of language in written form. From its foundation in 1886 the Association has been concerned to develop a system of notation which would be convenient to use, but comprehensive enough to cope with the wide variety of sounds found in the languages of the world; and to encourage the use of thjs notation as widely as possible among those concerned with language. The system is generally known as the International Phonetic Alphabet. Both the Association and its Alphabet are widely referred to by the abbreviation IPA, but here 'IPA' will be used only for the Alphabet. The IPA is based on the Roman alphabet, which has the advantage of being widely familiar, but also includes letters and additional symbols from a variety of other sources. These additions are necessary because the variety of sounds in languages is much greater than the number of letters in the Roman alphabet. The use of sequences of phonetic symbols to represent speech is known as transcription. The IPA can be used for many different purposes. For instance, it can be used as a way to show pronunciation in a dictionary, to record a language in linguistic fieldwork, to form the basis of a writing system for a language, or to annotate acoustic and other displays in the analysis of speech. -

Binary Bracelets
10010011011000110 10010011011000110110000100010001000001000 1001001101100011011000010001000111000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000 001000 11000010 010000 010001010001000001000 100100110 010 010 110110000100010001000001000 1001001101 1000 110110000100010001000001000 1001001101 10001101100001000100010000 010 01000 10010011011000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000001000 11000010 010000 01000 010 010 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10000 01 000 11000 010 010000 010 010 010 010 010 0100010010011011000110 10010011011000110110000100010001000001000 10010011011000110110000100010001110001101 10 00010 001BINARY 1000001000 101000110110000100010001000001000 BRACELETS 10010011011000110110 00010 001 1000001000 100 10011 011 000110 110000 10001000001000 11000010 010000 01000 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10000 01 000 1110 1100011011000010001000100000 000110 110000 10001000001000 11000010 010000 01000 11000110110 00010 001 1000001000 100 10011 011 000110 110000 1000 10010011011000110110 00010 001 1000001000 100 10011 011 Binary Code We are often used to representing numbers using ten digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9. This is called a base-10, or decimal system. Binary code, however, uses only zeros and ones in a sequence of eight spots. We often to refer to these binary, or base-2, digits as “bits.” Binary code is used to communicate information between computers, communication devices, and many more modern technologies. It’s useful to build into electronic devices because it is a simple system that requires something turn on or off (where 1 is the on state and 0 is the off state). This activity will allow you to embed your own name or nickname in this secret code on a bracelet. The binary code for capital letters is found on the back of this page.